Scan for Containers, dormant VMs, and Kali's Docker Secure Containers with pfSense Security Software ?
-
Hello Netgate community,
how can I enable a scan for invasive containers and or dormant VMs that start running?
If we use a proxy "content accelerator" we can figuratively catch the container and take it "the proxy caught container" off line with transparent mode and dual use container duplication and air gap the container to test for container purity with a virus scan after or use a Data Loss Prevention (DLP) systems while its running in transparent mode. Now how can we scan that container or Virtual Machine we caught for instances of that invasive container use on non small office, company, and corporate non approved containers. I want to learn how to block out any reverse binds or egress use that are bypassing the access control lists with outgoing connections that are data marshaling the Network Interface Card. Keep in mind anything that will alert the container manager will trigger a sandboxed event of that container. We want hard evidence for cybersecurity GDPR, and California Privacy laws being broken with invasive use.
What pfSense or Netgate security tool can we use to scan for any and all Docker containers without installing Docker, or other container managers? Or what firewall rules can you put in place for new virtual sandbox container based issues.
Keep in mind any and all fresh installs will come from the Windows servers and push that same invasive non approved container down. It is no longer a DVD or CD one size fits all image that is downloaded. They are Ip and use based for systems with use of auto deployment and vendor drivers that are pushed on reimage. So if you wipe the system that same container is fault tolerant based on the system you are using and will eventually restore itself. How can we scan for them?
Example: Hypothetically can a old job you left that has a disgruntled manager still access and still push containers to a private home system that you used for access with Office 365 only or had linked to a personal Gmail account. Even after you left that job this manager wanted to do something invasive because he did not like that you put your three weeks in, and tries to break your personal system.This is all hypothetical however you can see the reasons for a need to scan for any and all instances of containers in a small office setting to a large corporate environment. NIST SP800-190 states a major container issue and I quote
*"1. Compromise of an image or container. This risk was evaluated using the data-centric 696 system threat modeling approach described in NIST SP 800-154 [17]. The primary “data” 697 to protect is the images and containers, which may hold application files, data files, etc. 698 The secondary data to protect is container data within shared host resources such as 699 memory, storage, and network interfaces.
- Misuse of a container to attack other containers, the host OS, other hosts, etc."*
With that being said what protections and compartmentalization is there for the end user in a personal setting and or small business that would utilize proxy duplication for virus scan and testing of what is being data marshaled within the shielded containers, as well as protections for the good known instances containers that are currently used for Cybersecurity.
When we have our phones linked with software like Microsoft's phone companion issues such as invasive unapproved illegal containers could cause issues, even blocking cell phone based messages. This is smartphone system with messages to my father last couple days. Everything says message expired or not available. Could a invasive container even take control of the "Your Phone application?"Do to this very vulnerable security lapse you now are starting to see Pen testing companies taking advantage of this. Kali now has a full instance of their standard tool kit now inside of a secure Docker container. How can the security teams start to block containers.
Inside of my firewall Squid is logging all tunnels some devices are going to tunneled URLs even when there is no one using the internet the system is logging URL tunneled activity.
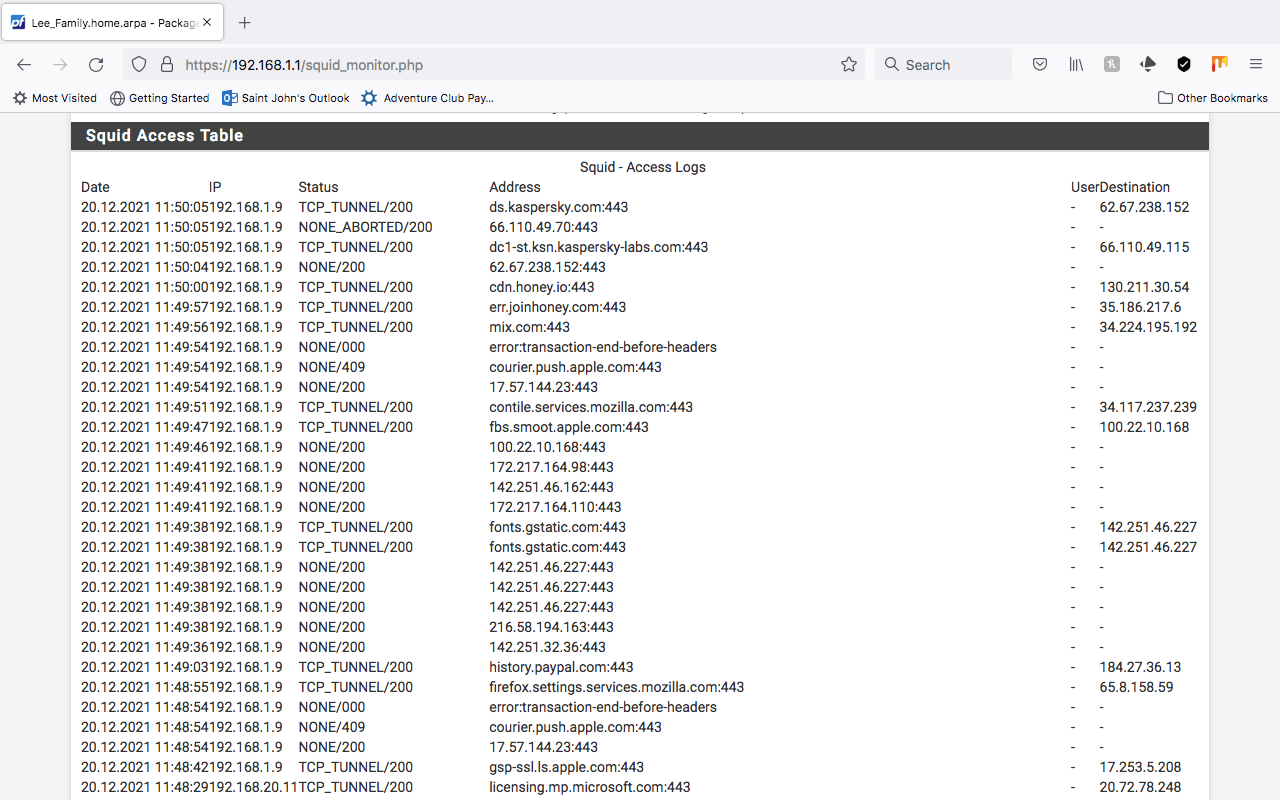
How can this be scanned ???Encrypted containers and unknown instances of virtual machines that are unknown to the users cause a cyber security concern.
history.paypal and I have seen sandbox pushes also. I have no Paypal account so this is concern who is using Paypal in a tunnel??
Again we need ways to scan for invasive containers.
-
Again, What tools does pfSense or Netgate have in its arsenal to combat cutting edge containers being used.
I feel heavy proxy improvement and use is key to dismantling such invasive actors.
-
What you are asking for is a bit unreasonable... a container is merely an OS nested inside of another. It's a bit like asking, "how can we detected these pesky 'virtual machines' hidden inside the hypervisors on my network?" Or to use a non-technical metaphor, "how can we detect malicious cardboard boxes hidden inside these shipping containers that are skulking around on our cargo ship?"
-
@garyd said in Scan for Containers, dormant VMs, and Kali's Docker Secure Containers with pfSense Security Software ?:
how can we detect malicious cardboard boxes hidden inside these shipping containers
Nice.
Adding to that : knowing the the transporter isn't even allowed to open the container - as the postal services are not allowed to open your letters.
=> pfSense will not and can not 'open' Ethernet packets and look inside it. Everything is TLS encrypted. What pfSense sees : see the definition of a Ethernet packet. The 'payload' will be 100 % accessible. So how can pfSense know that a packet is made by process X or device Y ??Ok, the set of these "Preamble / Start frame delimiter / MAC destination / MAC source 802.1Q tag (optional) / Ethertype (Ethernet II) or length (IEEE 802.3)" can be fingerprinted, and some conclusions can be drawn from them. But nothing will be 'sure'.
pfSense is a router firewall. It takes packets in, and throws them out according a routing list. Packets can be accepted or blocked according source and destination addresses, ports, type of protocol etc. Exactly like the info you find on the envelop - on the outside.
-
@gertjan I like when you said "Ok, the set of these "Preamble / Start frame delimiter / MAC destination / MAC source 802.1Q tag (optional) / Ethertype (Ethernet II) or length (IEEE 802.3)" can be fingerprinted, and some conclusions can be drawn from them. But nothing will be 'sure'."
There is also areas in pfSense's advanced settings that show options for OS detection inside of the firewall rules. The proxy package Squid can also intercept SSL traffic decrypt it and issue its own certificate as it sends the data. Much like the mailman inspector.
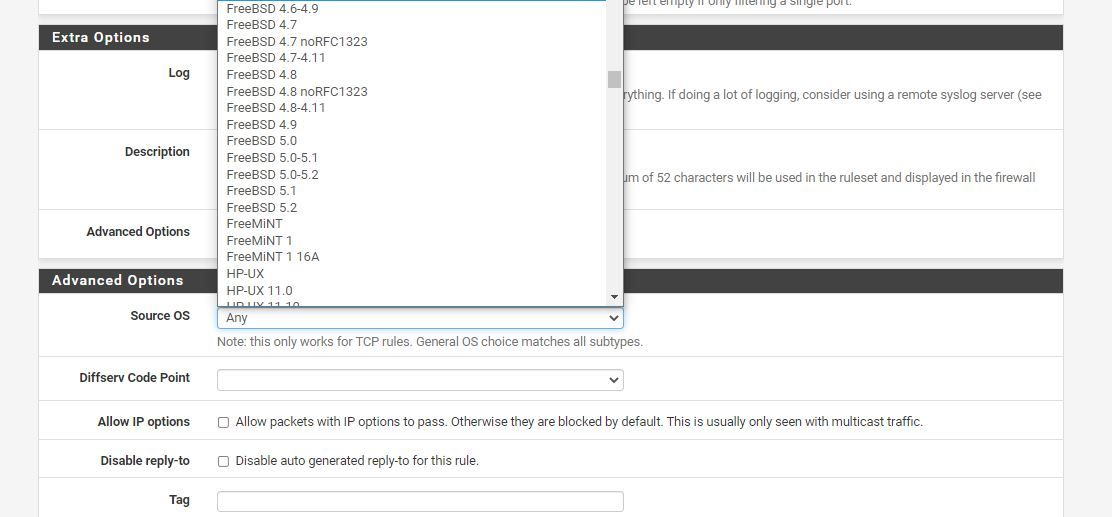
(Advanced Options: Source OS detections)Once again to quote the issues currently needing compartmentalization and in need of major solutions. NIST SP800-190 states a major container issue and I quote
"1. Compromise of an image or container. This risk was evaluated using the data-centric 696 system threat modeling approach described in NIST SP 800-154 [17]. The primary “data” 697 to protect is the images and containers, which may hold application files, data files, etc. 698 The secondary data to protect is container data within shared host resources such as 699 memory, storage, and network interfaces.
- Misuse of a container to attack other containers, the host OS, other hosts, etc."
When I can find containers issued from Facebook or Google running on a system that auto delete as soon as they are spotted one can wonder how can one inspect what is occuring with these "hidden packages, within packages. . ."
Even Linux Jails hide. This was my major takeaway:
Obscurity is of upmost importance when working with exploits. Antivirus software is finetuned daily to detect specific exploits within the signatures of files. Encoders play a key role in obfuscation for the security of the exploit and it's handlers. Use of encoders gives rise to polymorphism within code, code that is ever changing in its location and signature.
Good Firewall Software needs to change and find solid solutions to current trends within Cyber Security. Container decrypt and fingerprinting may be what is needed.
-
@jonathanlee we can do it if we think of a solution. In cyber security we don't make more problems we make solutions. We can find something to fix this.
To quote Michael W Lucas book Free BSD Mastery Jails . . .
"Virtualization is grand, but even with nested layers of virtual machines eventually you hit an operating system installed on physical hardware."
-
Cheers!! Merry Christmas Everyone!!
Please if anyone knows of a pfSense package or setting that can do this please reply.
I think the HTTP get may help as a solution with fingerprinting however it would require a database to help with where the GET requests are sent.
"The HTTP GET request method is used to request a resource from the server. The GET request should only receive data (the server must not change its state). If you want to change data on the server, use POST, PUT, PATCH or DELETE methods."
ReqBin, A. (2021, July 24). What is the HTTP get request method and how to use it? ReqBin. Retrieved December 24, 2021, from https://reqbin.com/Article/HttpGet
-
@jonathanlee said in Scan for Containers, dormant VMs, and Kali's Docker Secure Containers with pfSense Security Software ?:
"Virtualization is grand, but even with nested layers of virtual machines eventually you hit an operating system installed on physical hardware."
Authenticated scans with a vulnerability management tool will get a list of all software installed on a host. This is why number one & two of the CIS critical controls are inventory of hardware & software.
-
Yes!!! exactly,
However alot of them do not work with the scanning for containers and again require 3rd party scanners to find them so I was told by our Professor when I asked about this. He even said alot of the times they do not fully find them all.
Containers want to be hidden sometimes. That is fine when it is an approved instance of a container from an admin. Times are changing and currently even PaloAlto firewalls now have a new ability to have container identification. Here is a quote from Palo Alto "Containers, Kubernetes and containers as a service (CaaS) have become mainstream ways to package and orchestrate services at scale. At the same time, container users need to ensure they have purpose-built security to address vulnerability management, compliance, runtime protection and network security requirements for their containerized applications."
This leaves me wondering what package pFsense will soon have to address this situation. Virtualization on the scale of Mesosphere really paint the picture of the Cyber Security sector's new reality. One day I hope that Squid can find and label invasive containers as a virus inside Squid. Even if they try to self delete it Squid should have an ability secure them and block them for analysis.
All dreams on my end however real nightmares for cyber security programmers. This kind of solution requires teamwork.
-
I am a Palo Alto Networks customer and they have a huge development team and the PAN-OS system requirements are much higher than pfSense’s.
Snort’s Open App ID framework is probably the closest you’re going to get in being able to root out hidden containers in your environment — and even then it will likely require some development & testing on your part.
-
@garyd thank you for sharing this.
This will be the first one I try to work with for detection. Hotjar scripts interceptions and inspection.
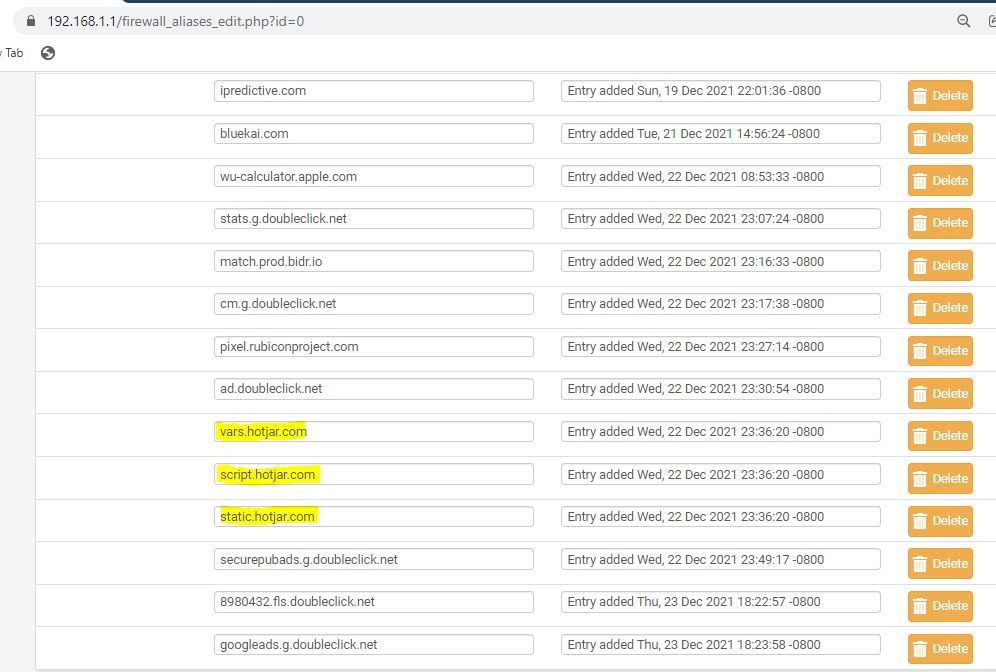
(Image: What I would like to code with first for detection)
My Smart TV was having some weird issues and I noticed this would run on the proxy.
-
@garyd I did eventually get Snort's Open App ID with full text rules running. My text rules I call the sorcerers code file, anyway it was able to show the applications that were running without any use over the network and pinpoint it to my Android smartphone. I got a new phone it stopped. Again, I knew it was there my goal was to find a way to stop it globally something I could report. Yes Snort's appID was the closest as you can detect the app use. Again, it does not list containers used.
I was researching this over summer break and found you can use pf to detect the OS in use in the tcp stack if you want to check this out. All for the goal of a more secure system. But it requires a OS container database much like a blacklist for this to function again this is similar to AppID with the text files.
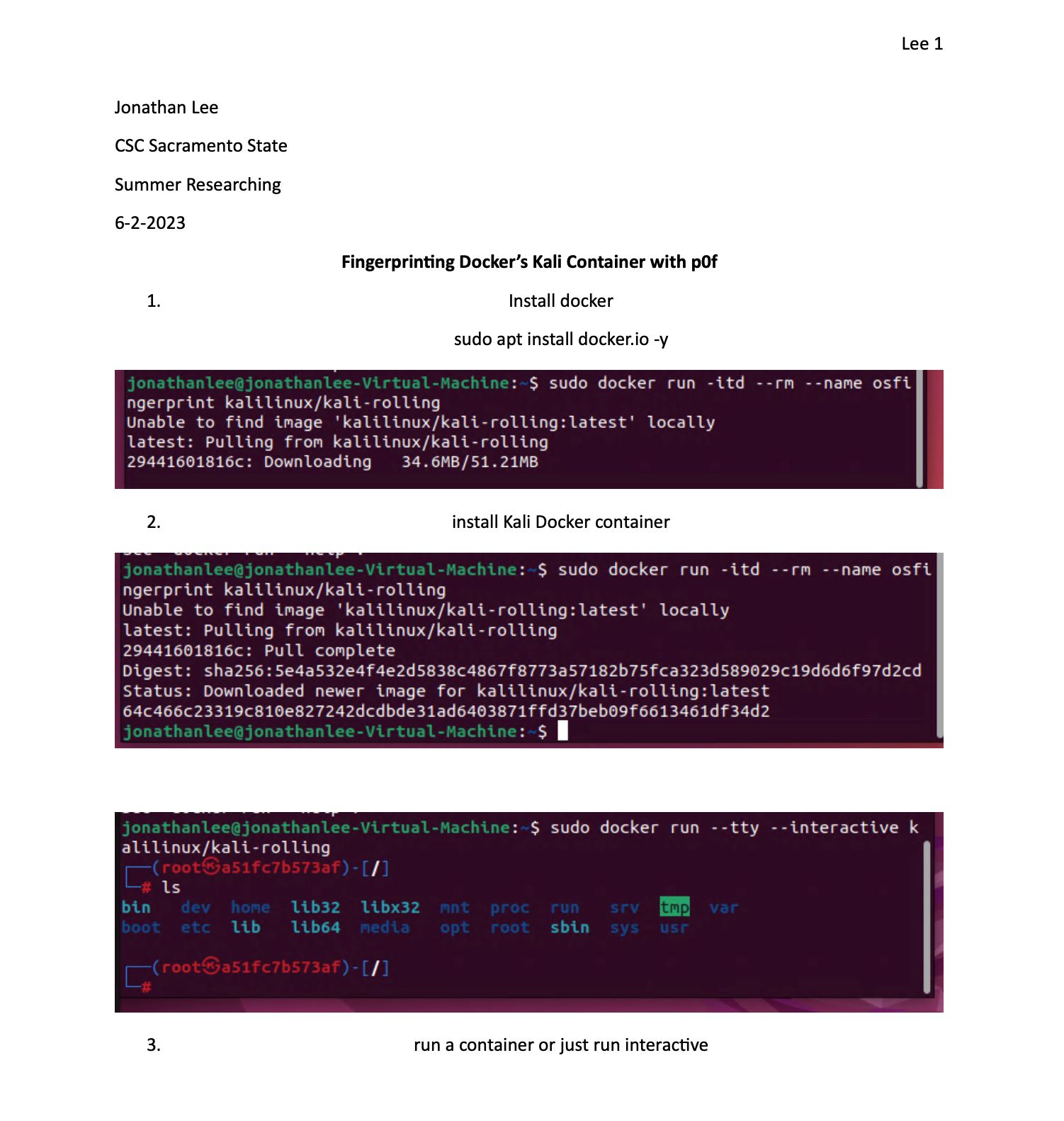
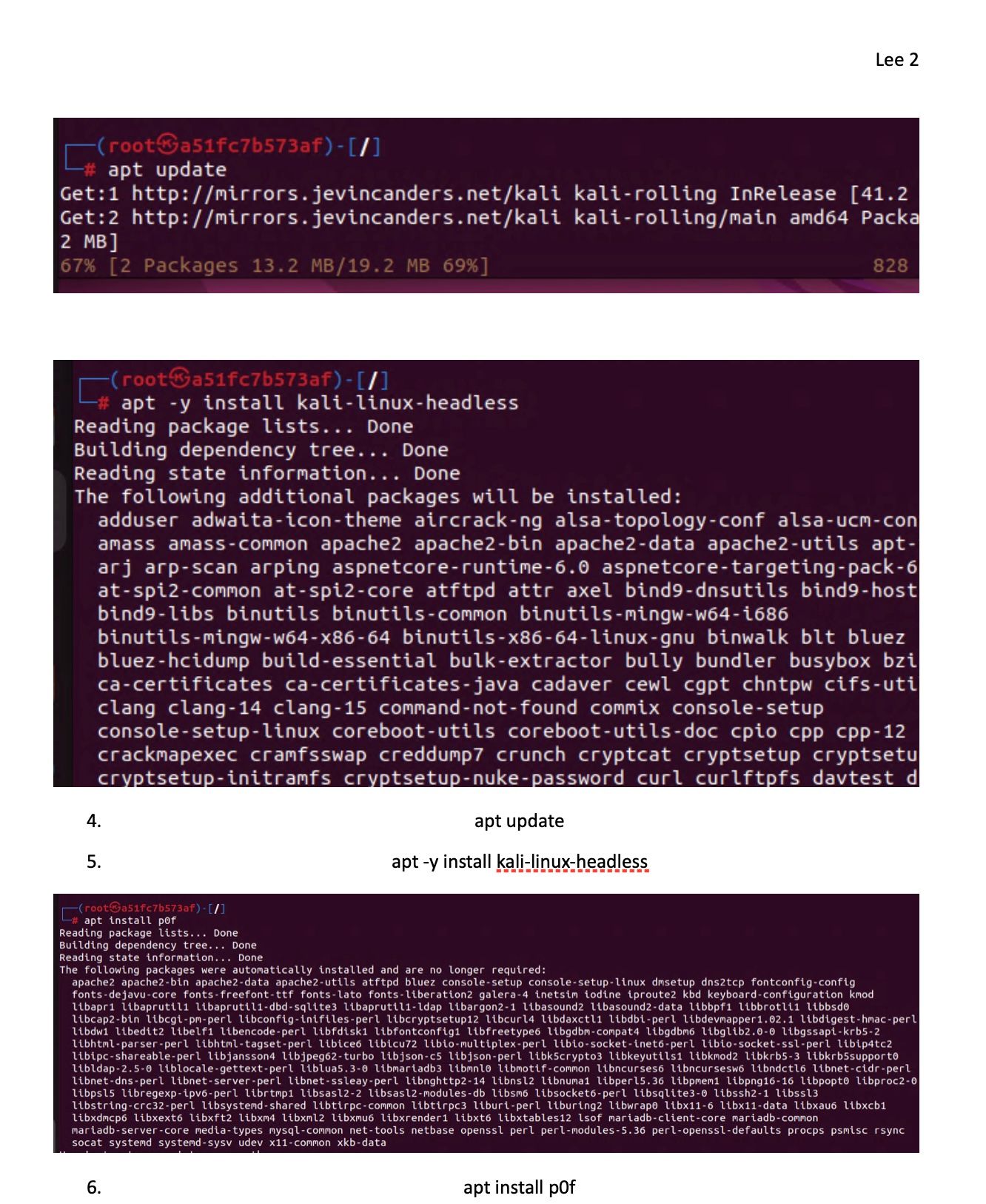
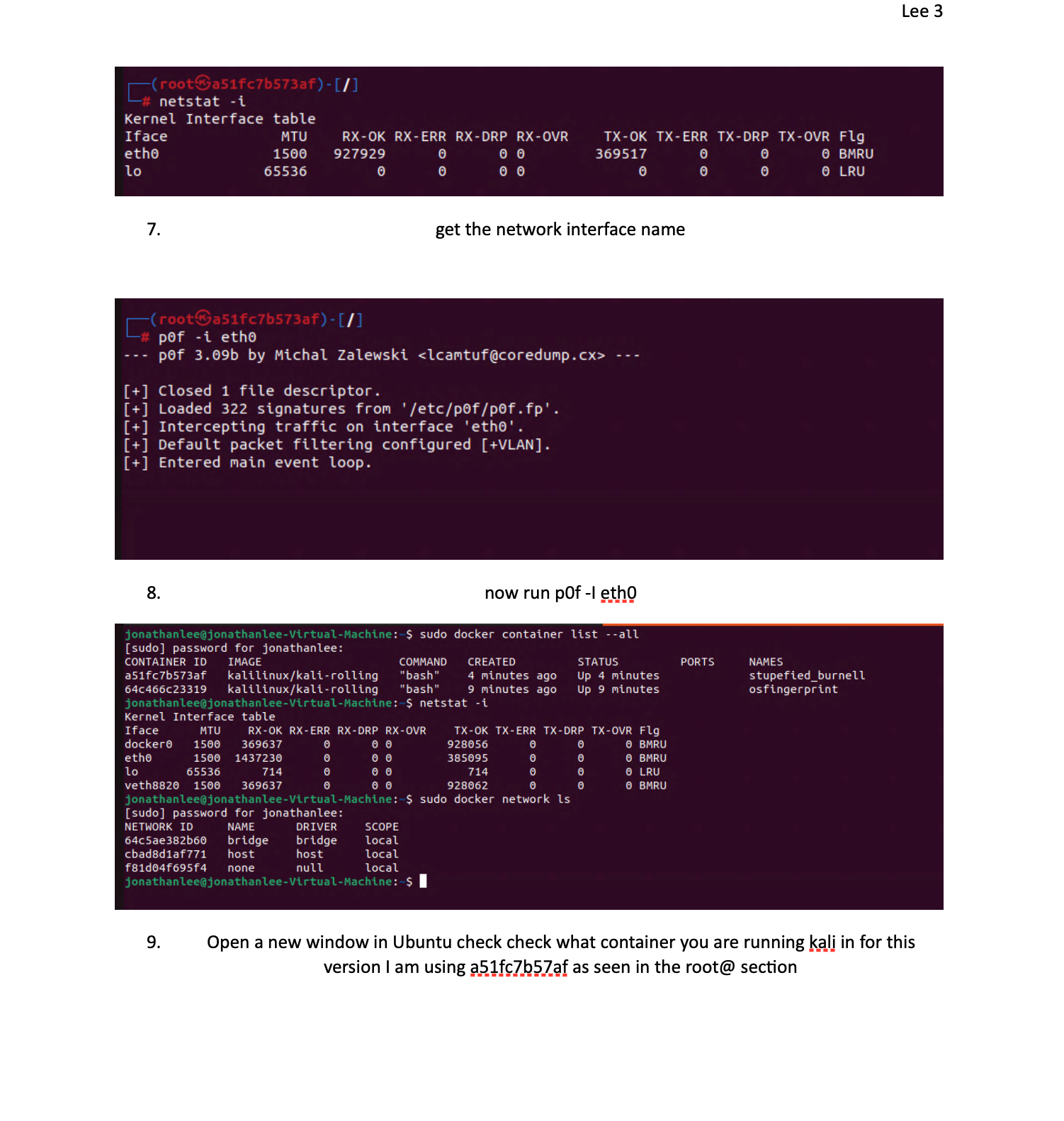
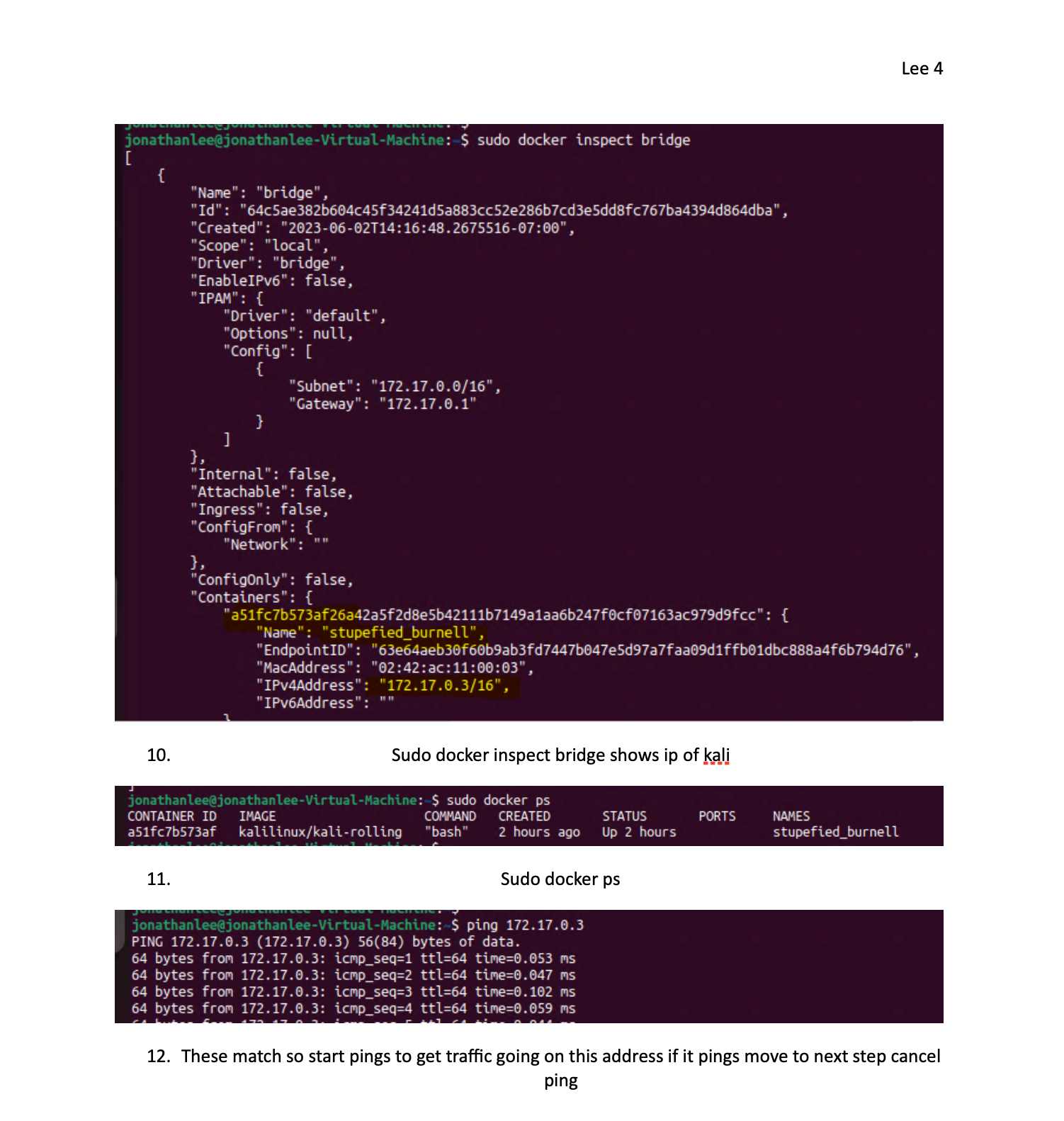
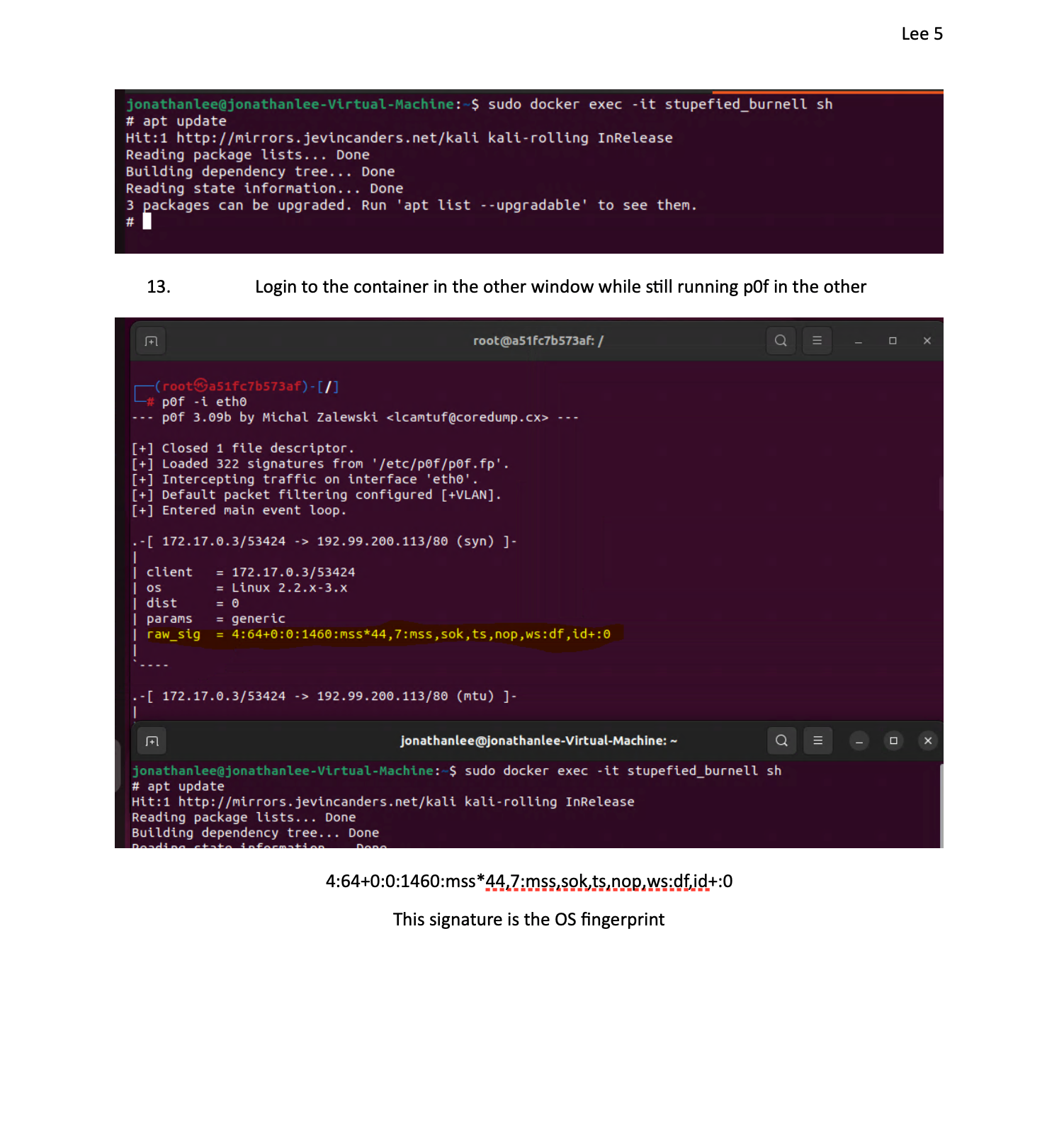
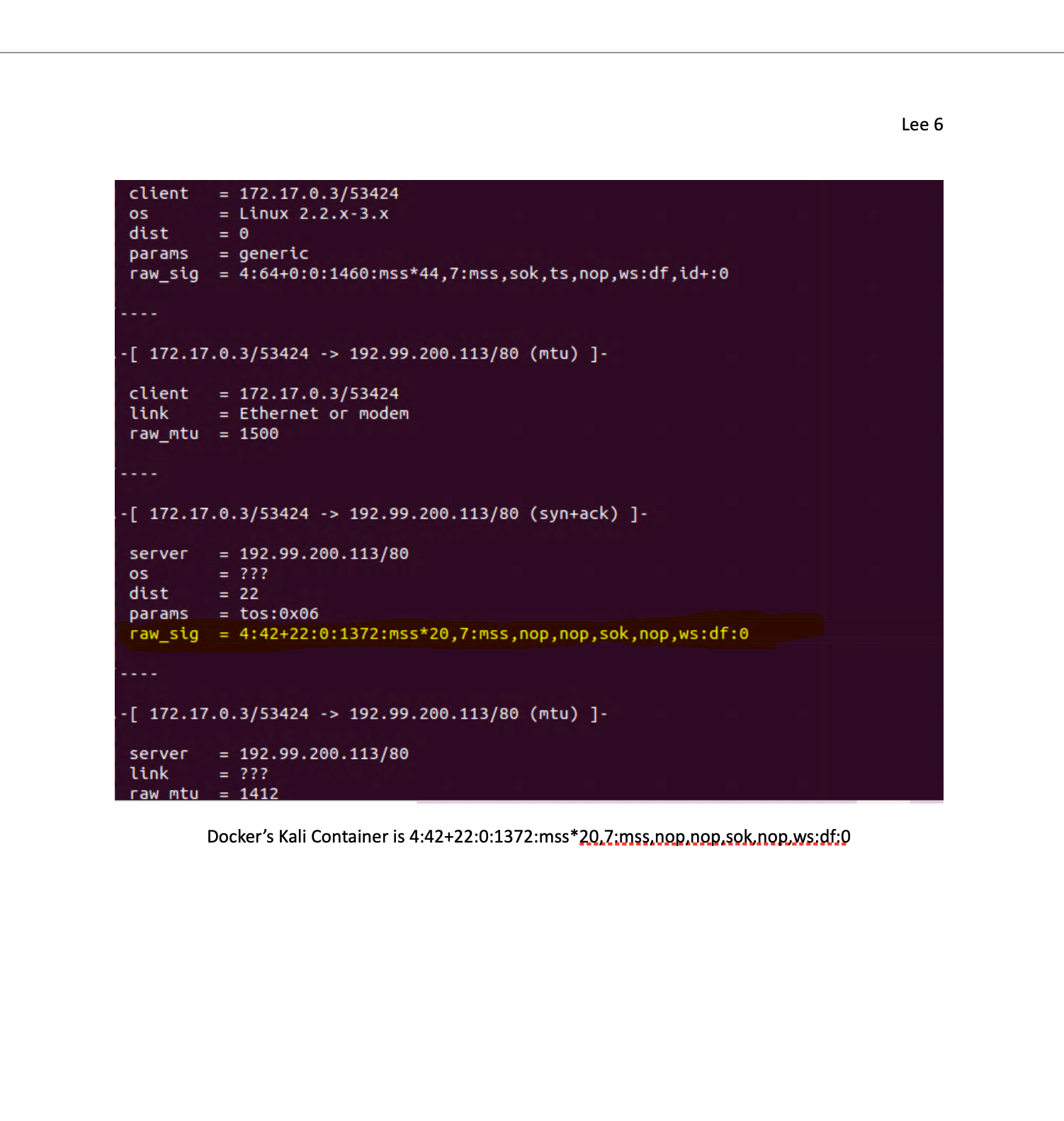
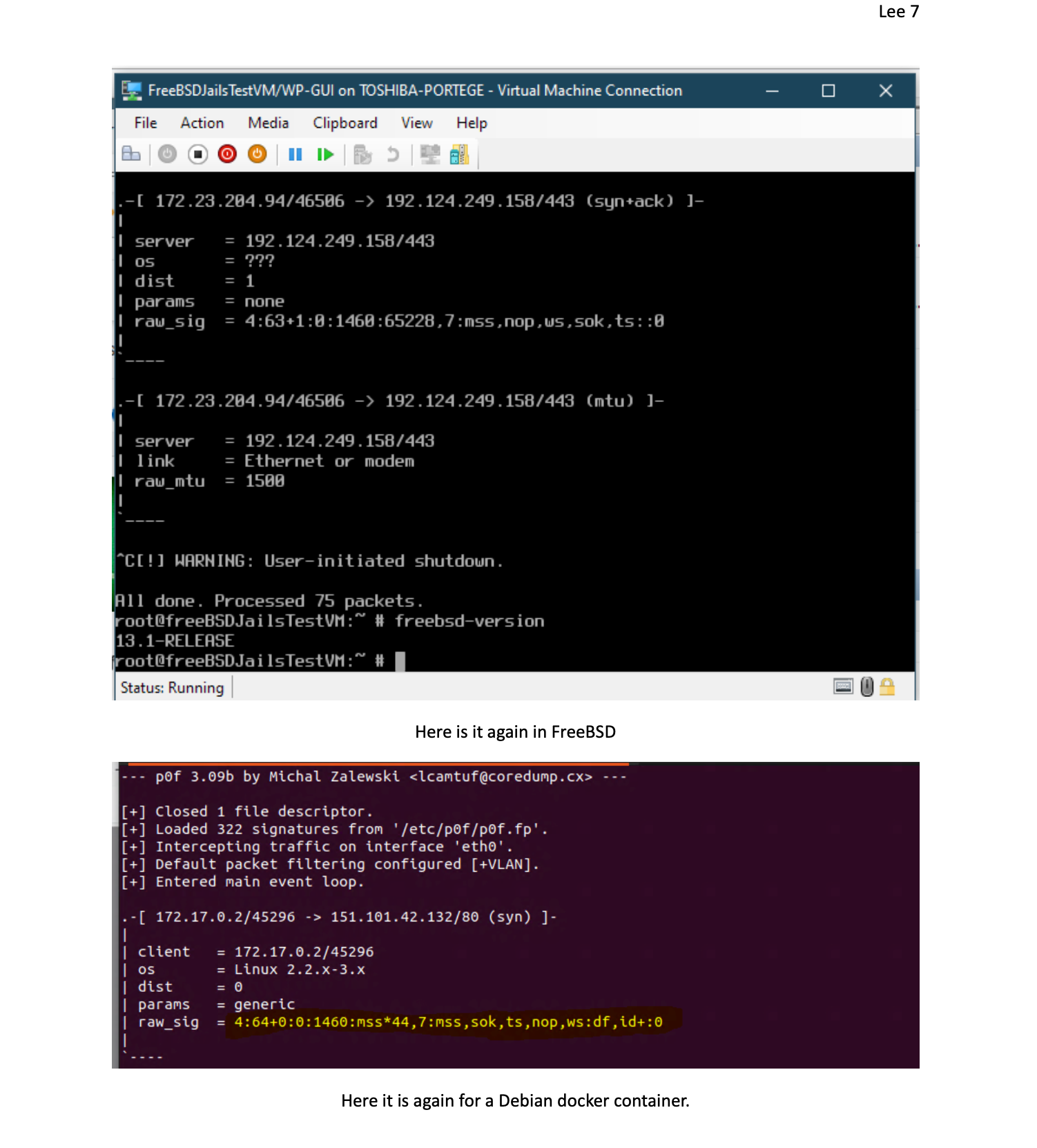

So any containers can be detected this way. What I want to do is set up a signature of what I use and start to block the bad ones. Least privilege approval. I am sure some are real and needed but some are unknown also.
I had a big one in my NAS that was found the other day also. Got that issue fixed.