NGNIX Errors?
-
Well this is new.....
nginx 2021/12/23 12:05:18 [error] 91181#100155: *526 open() "/usr/local/www/ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application" failed (2: No such file or directory), client:, server: , request: "GET /ecp/Current/exporttool/microsoft.exchange.ediscovery.exporttool.application HTTP/1.1"
Log entry.
Ignore? Some tweak I need to do?
-
Something tried to open that page on the pfSense gui which obviously doesn't exist.
It should show you the requesting IP. If that's something external then you need to lock down the WAN to prevent it. The webgui should never be open to WAN without restrictions.
Steve
-
Obviously I've been banging on stuff. I'm sure I've clicked on options that went nowhere. Like the VPN tab. I don't have a VPN setup. Family who works from home log into a VPN but we don't have one locally.
I cleared the syslog and will see if it returns.
-
I don't have any errors in my log to reference but those entries should show the client IP that requested that page. If it's an IP on your LAN it's nothing to worry about IMO.
Steve
-
Its back....
2021/12/23 14:15:01 [error] 91181#100155: *728 "/usr/local/www/solr/index.php" is not found (2: No such file or directory), client: 128.14.209.170, server: , request: "GET /solr/ HTTP/1.1", host: "xxxxxxxxxxxx", referrer: "http://xxxxxxxx/solr/#/"
Nothing on my network is 128.14.209.170. I can't check anything about the VPN. Folks are working.....
The referer and host addresses however is the IP my ISP assigns to my modem.
-
That traffic should not be hitting the pfSense webgui then. You should make sure you haven't accidentally opened the WAN to any external source.
-
The VPN provided IP's are not 129.......
Where would I have opened up the WAN? I've not touched any firewall rules. I have gateways for the multiple NIC's otherwise a client connected on one NIC couldn't talk to a client connected on the other. Like my networked printer. Only people that could print to it were folks hung off the same NIC the printer was on.
And they're all bridged. Which I though would allow them all to talk to each other.
As far as opening the WAN, not touched it.
-
This is showing in Sockets. It is the only thing assigned to the same IP listed in the NGNIX error.
root ntpd 92198 26 udp4
I DO have some WAN ports open. Sorry but just dawned on me.
Static ports for Nintendo game consoles to be able to play in friends on-line game "rooms".
-
You should only have gateways on WANs unless you have other internal routers with further subnets behind them.
Internal NICs should only be bridged if they're on the same subnet. They probably aren't.
If you have port forwards they should be to internal IPs so traffic hitting them could not hit the webgui.
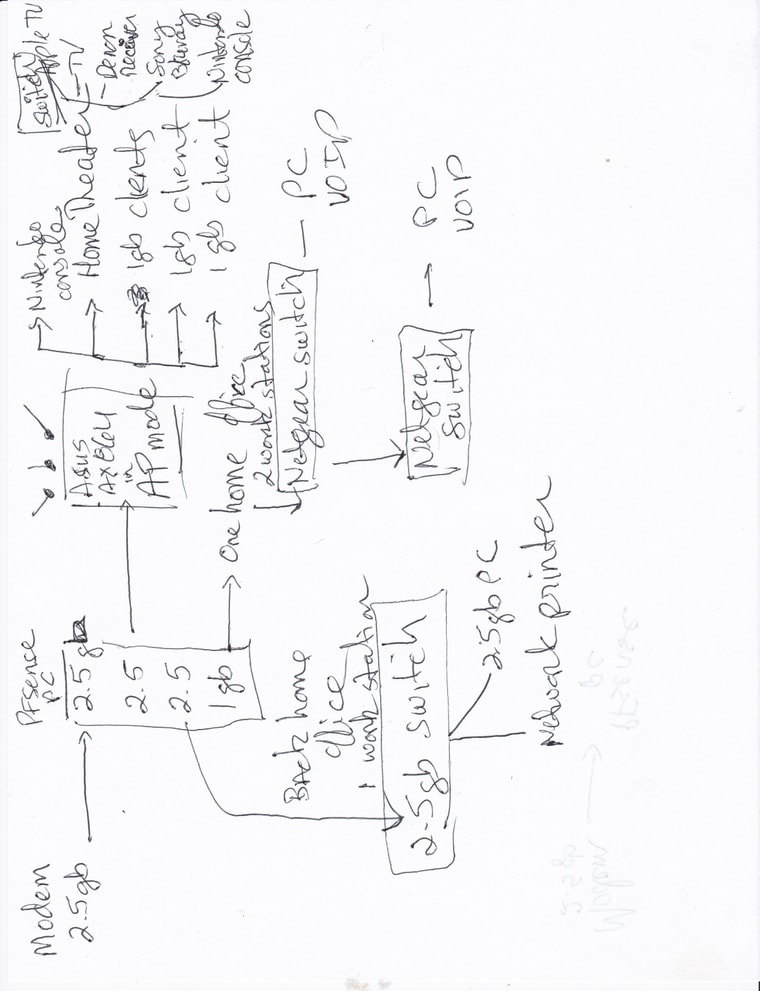
I think we will need to see a diagram here and probably some screen shots of your rules.
Steve
-
NIC's are on same subnet. I followed the steps on Netgate for making a bridge.
The rules for the Nintendo game consoles are assigned to static IP's.
By default the WAN gateway was there I thought. I don't recall making one but may have.
Just looked, I didn't make those 2 gateways for the WAN. One is for IPV4, one for IPV6.
I mispoke earlier. I made the Firewall rules not gateways for the LAN, the NIC's.
The IP's I'm seeing are assigned to Zenlayer Inc.
The rules are all the same.
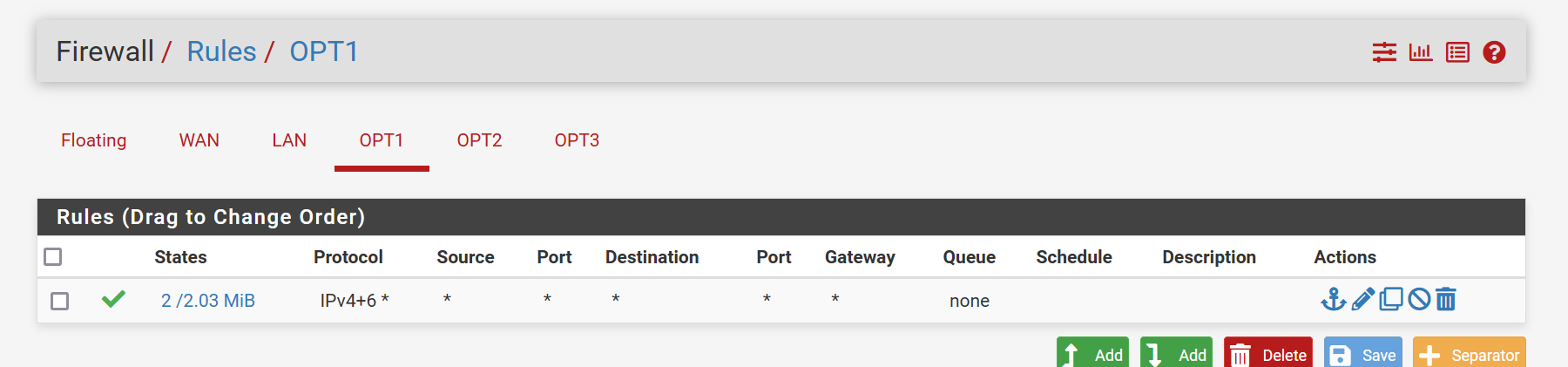
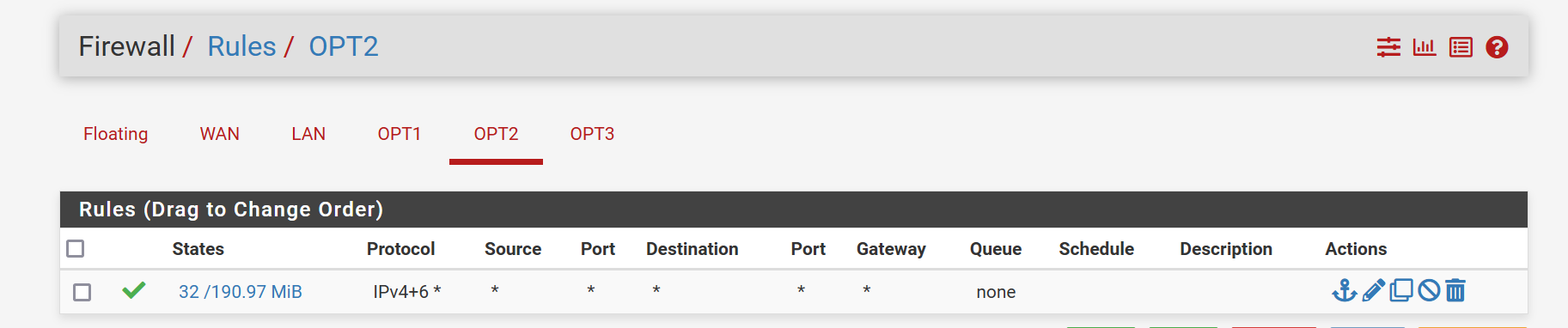
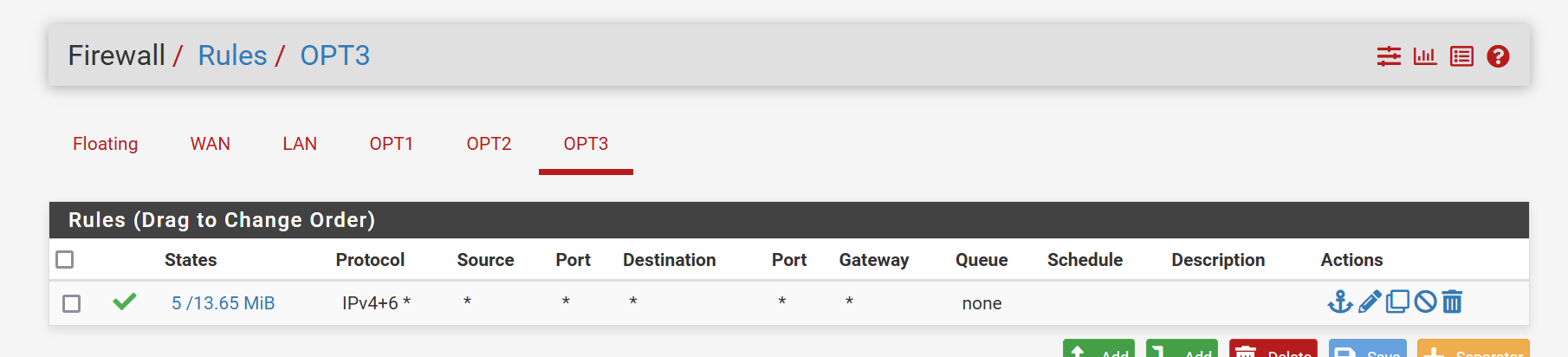
-
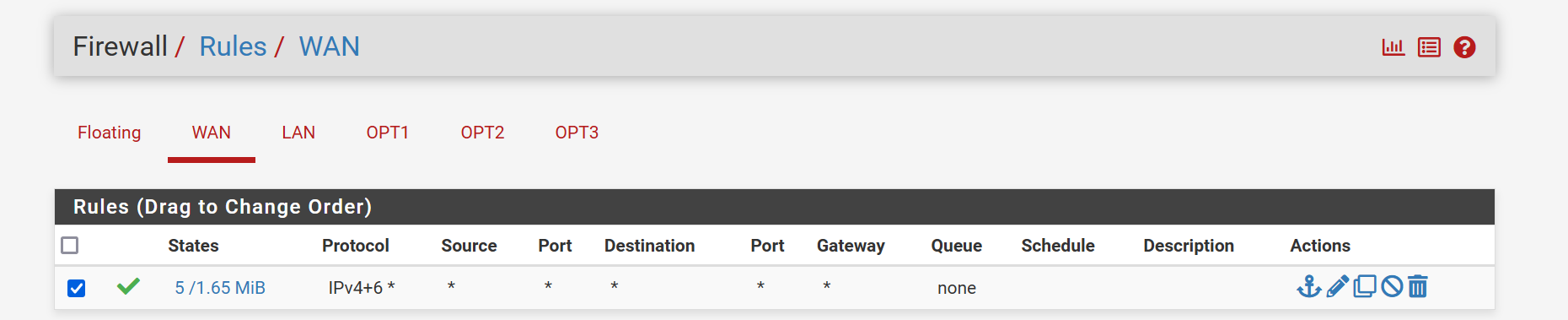
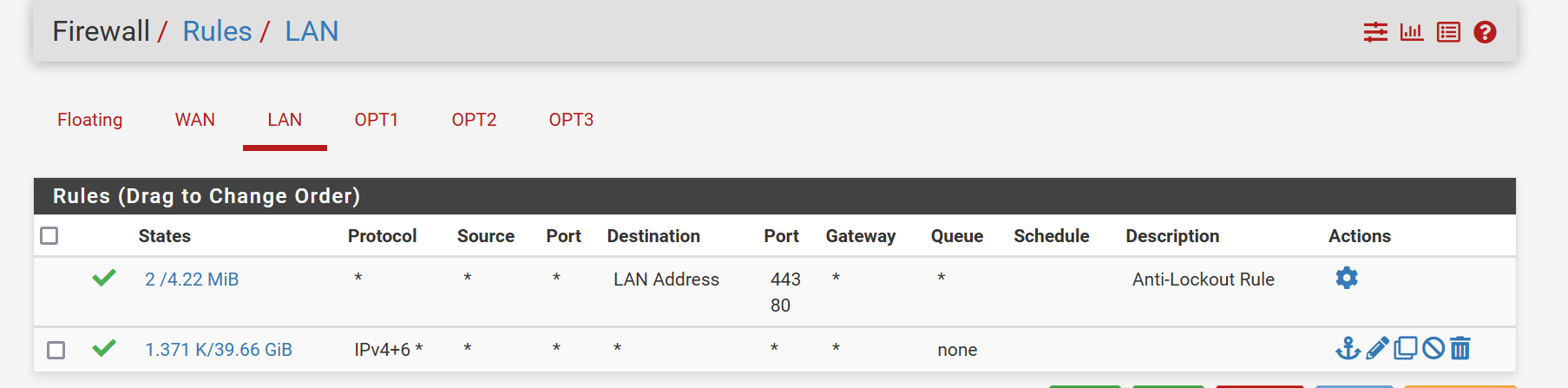
Ok, you have an allow all rule on the WAN there. You should disable or remove that immediately.
Currently all the services on the firewall are open to any external source.
I don't see any firewall rules created by port forwards and they usually would be by default. So I don't what the NAT rules are you added.
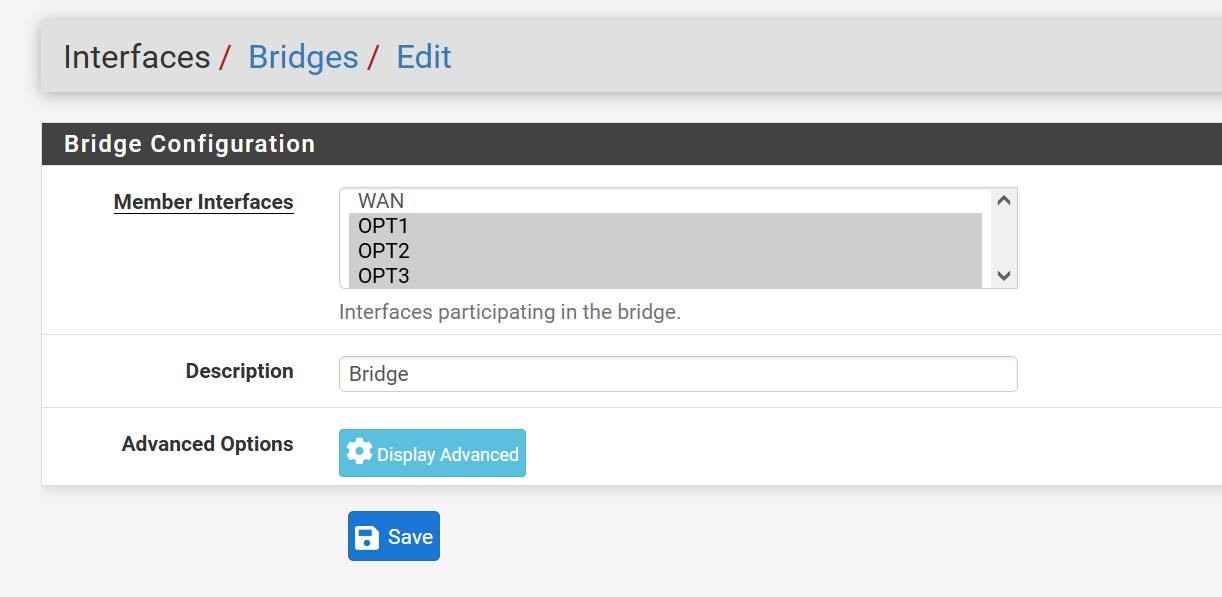
If you just want all of those internal interfaces bridged in the same subnet you should assign the bridge itself and put the IP address and DHCP server etc on that.
Steve
-
@stephenw10
That’s how I have the bridge setup.If I don’t have those NAT rules devices hung on different NIC’s can’t talk to devices on the other NIC’s.
I’m removing the WAN now.
Firewall rules created by port forwards.
As best as I can remember none were. Which is why I created those rules.
I’m on my iPAD connected wirelessly to the ASUS AX86U. If I try to access the network printer hung off the 2.5gb switch in the back office WITHOUT those rules, I can’t access it. I’m blocked from it.
If there’s a better way to do so I’m at the ready to change any rules. I obviously don’t know change to what though.
-
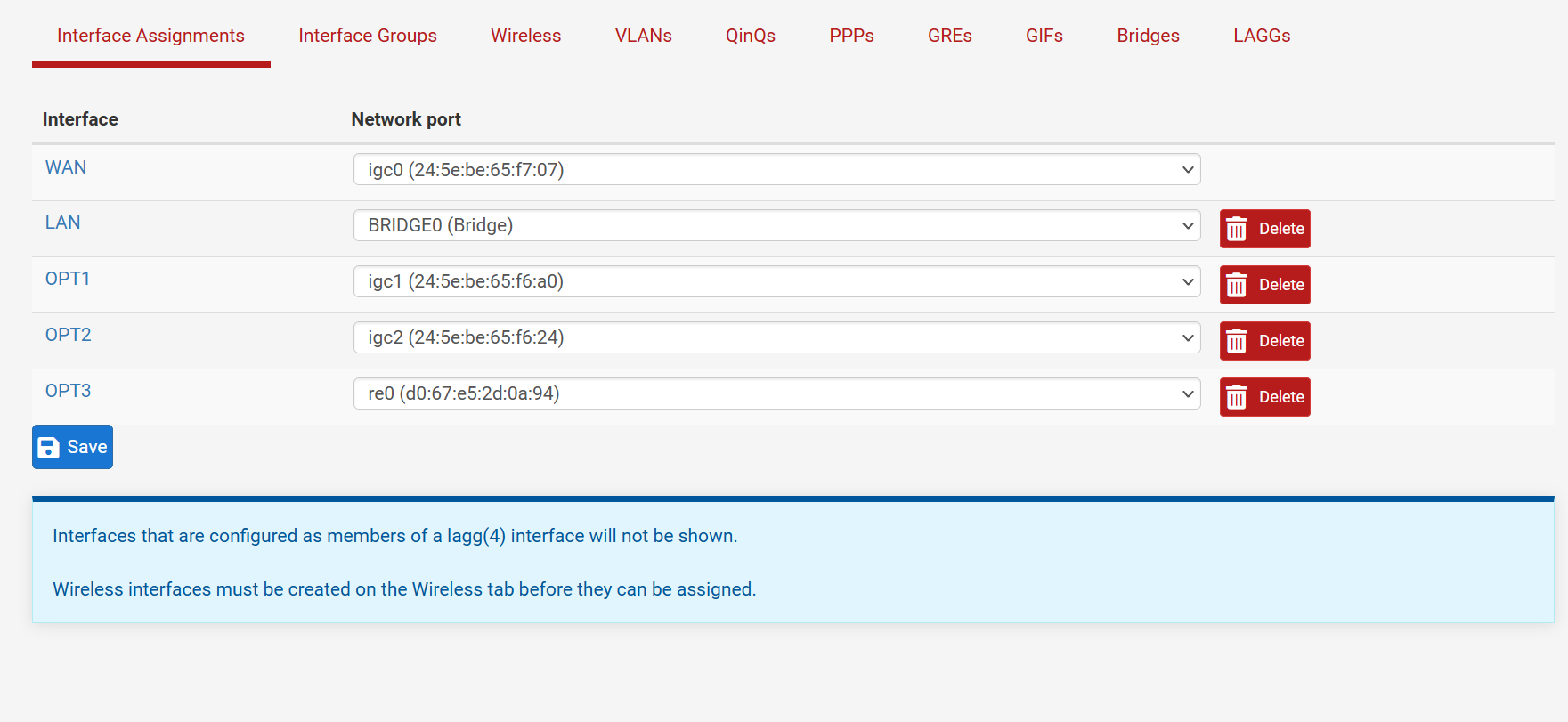
We'll need to see screenshots of those rules then. If it's in the same subnet you should not need any NAT rules.
Can we see the Interfaces > Assignments and Interfaces > Bridges screen.
Steve
-
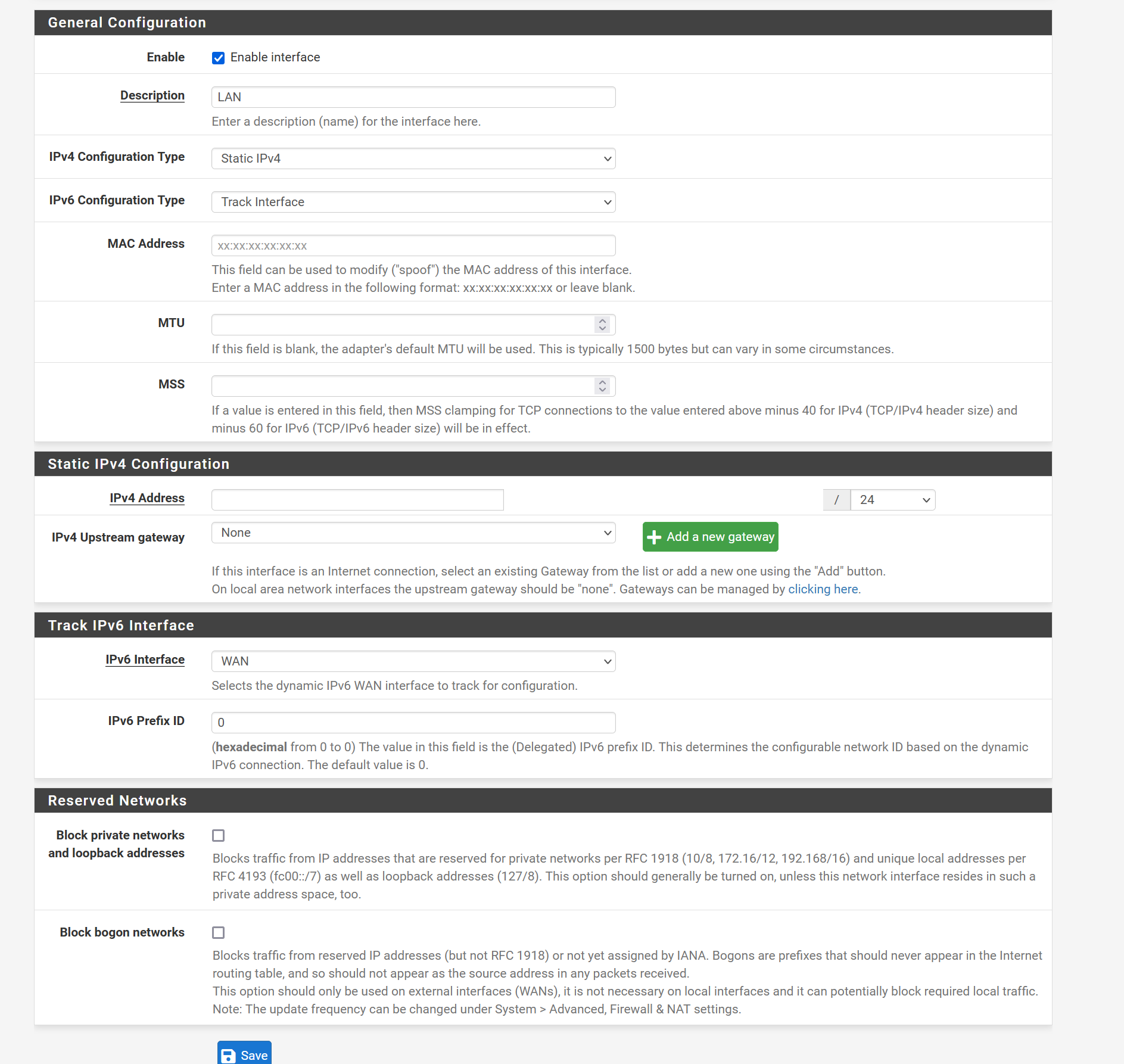
Bridge is configured for IPV4 and 6, NIC's are not.
The rules, glad to post screen shots but there's nothing beyond what I posted. That's why the "*" in most of the fields, its just "any".
"If it's in the same subnet you should not need any NAT rules"
The bridge has a static IPV4 address. Blanked it for the screen shot.
I've tested and retested. No rules, can't connect to devices with connect to different NIC's.
-
OK, the interface assignments and bridge config look good.
Since you have pass-all rules on the bridge and the members all traffic should pass between hosts on any of those.
Do you see anything blocked in the firewall log?
I meant the NAT rules you said you had to add.
Steve
-
I apologize if I'm getting terms crossed.
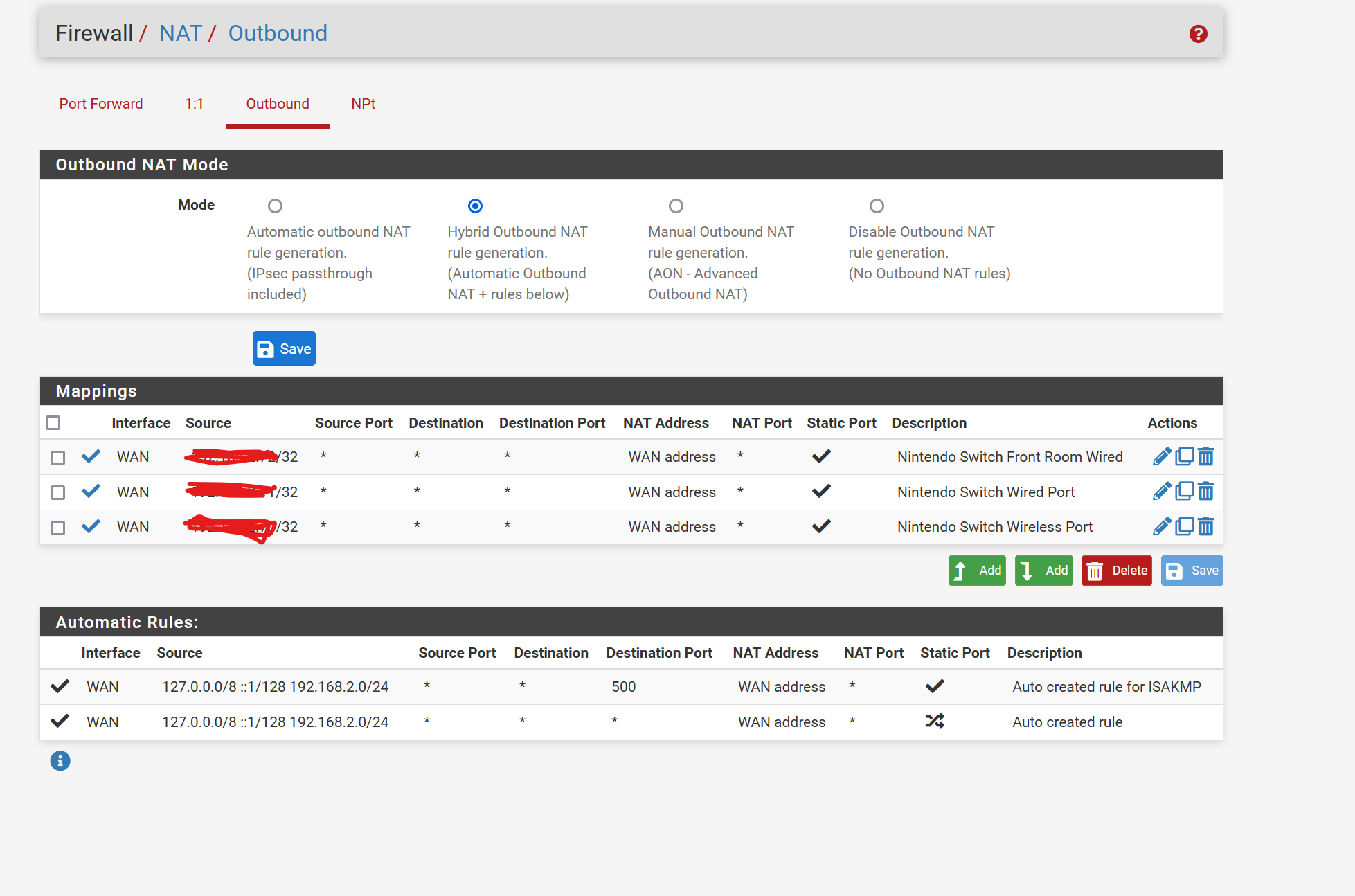
The only direct NAT rules I've made are the outbound rules for the Nintendo devices. Followed the Netgate document step by step for the static port, changed to Hybrid, etc.
I did not initially make those Firewall Rules for each NIC. I expected as you've said they're all one big happy "bridge", should talk to each other.
Didn't and won't.
I'm not saying that's the correct way to set it up. Just that's what I had to do.
My Port Forwarding information in the NAT tab is empty by the way.
Without those Firewall Rules the Firewall Log fills with blocked entries to the various devices.
Here's those outbound rules.
-
Ok, did you set the bridge sysctls to moved filtering the bridge interface?
https://docs.netgate.com/pfsense/en/latest/bridges/firewall.html#bridging-and-firewallingDid you reboot after doing that?
With those set you should only need rules on the bridge interface, LAN here. Otherwise, by default, the bridge filters on the member interfaces so you would need pass rules om all of them.
Steve
-
I don't recall doing so. I'll hit that document now.
-
The source in those outbound NAT rules should be internal private IPs. There's no real need to obscure those.
-
I did not do anything with System Tunables when making the bridge. Can do so now, booting might have to wait. Wife watching Thursday Night Football via streaming on Fubo.TV.......
These are the current entries:
net.link.bridge.pfil_onlyip Only pass IP packets when pfil is enabled 0
net.link.bridge.pfil_member Packet filter on the member interface 1
net.link.bridge.pfil_bridge Packet filter on the bridge interface 0"At least one of these must be set to 1"
One of them is set to 1 already????
All of them to "1"?