pfSense 2.5.2 OpenVPN Server - problems getting DNS working
-
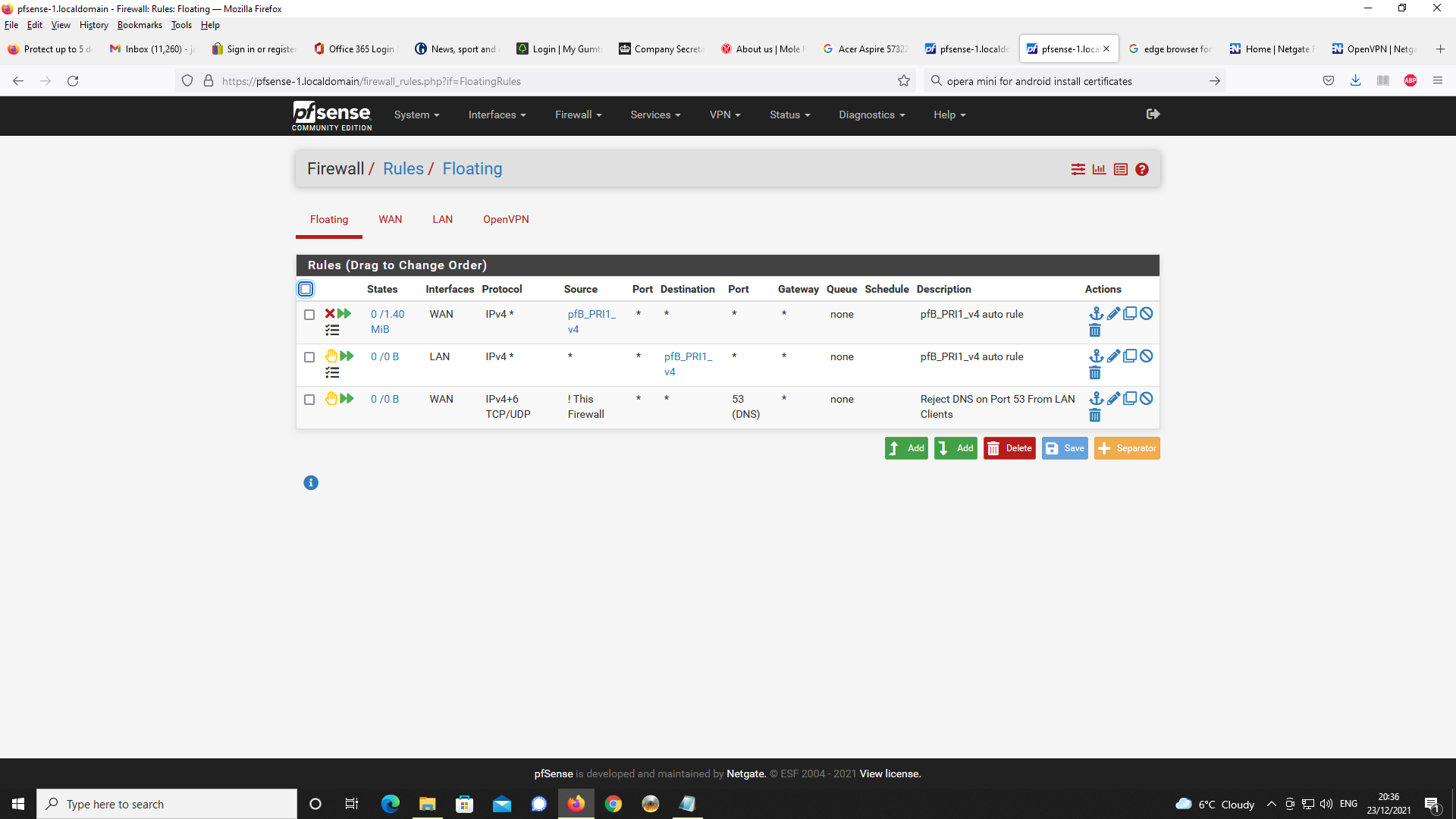
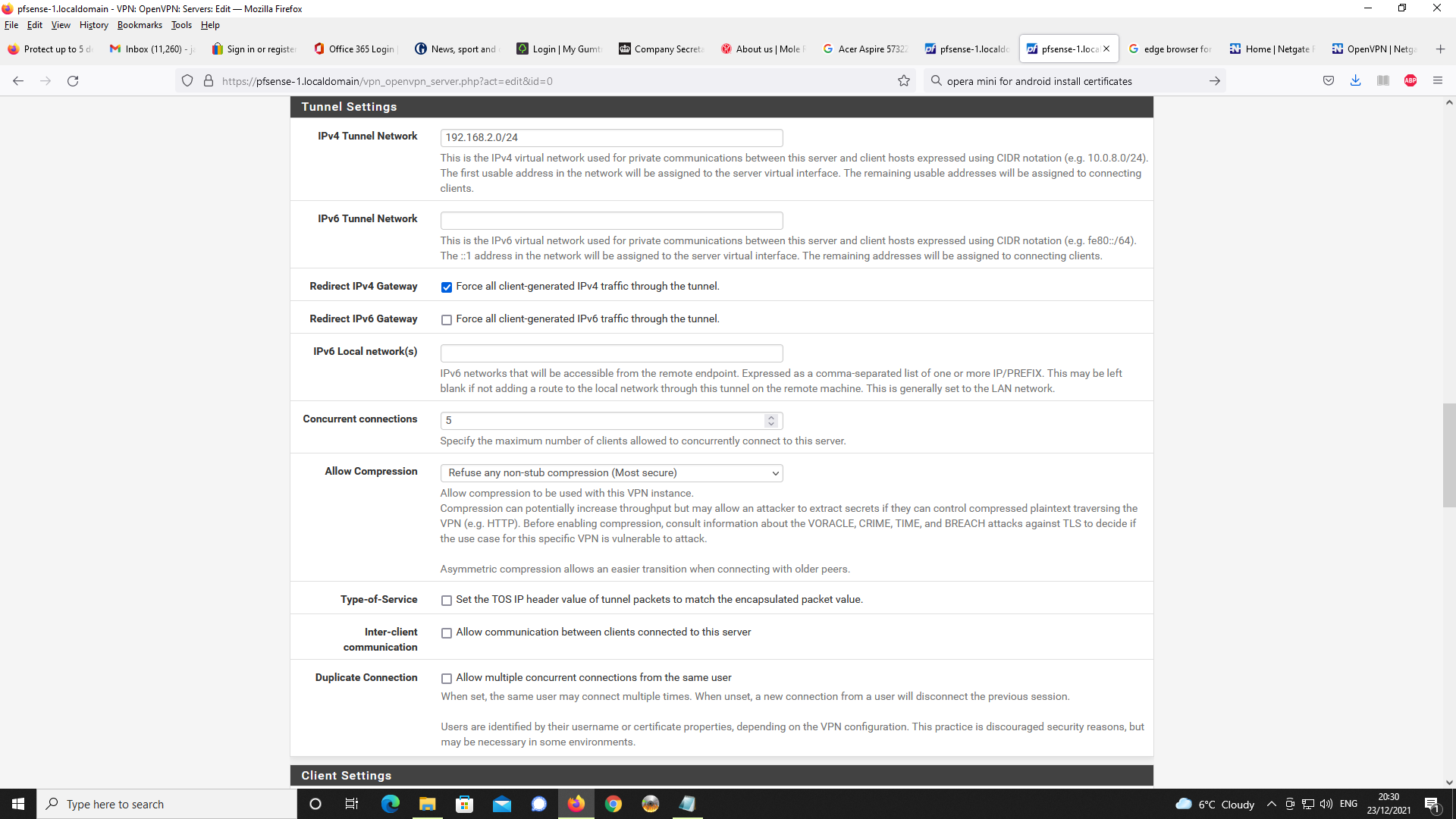
Y, device gets 192.168.2.0
Like I said strange -
I re checked your images / settings :
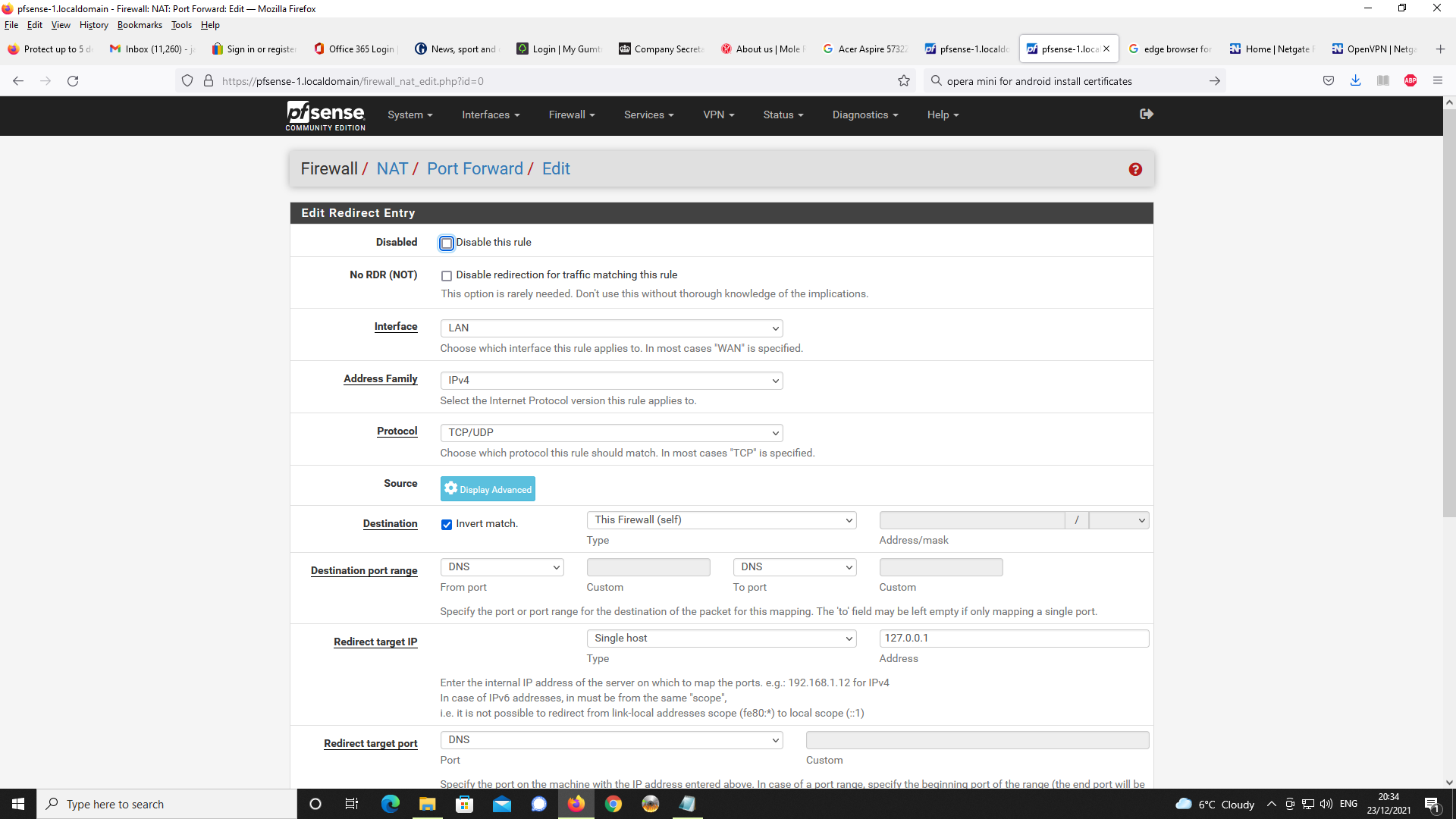
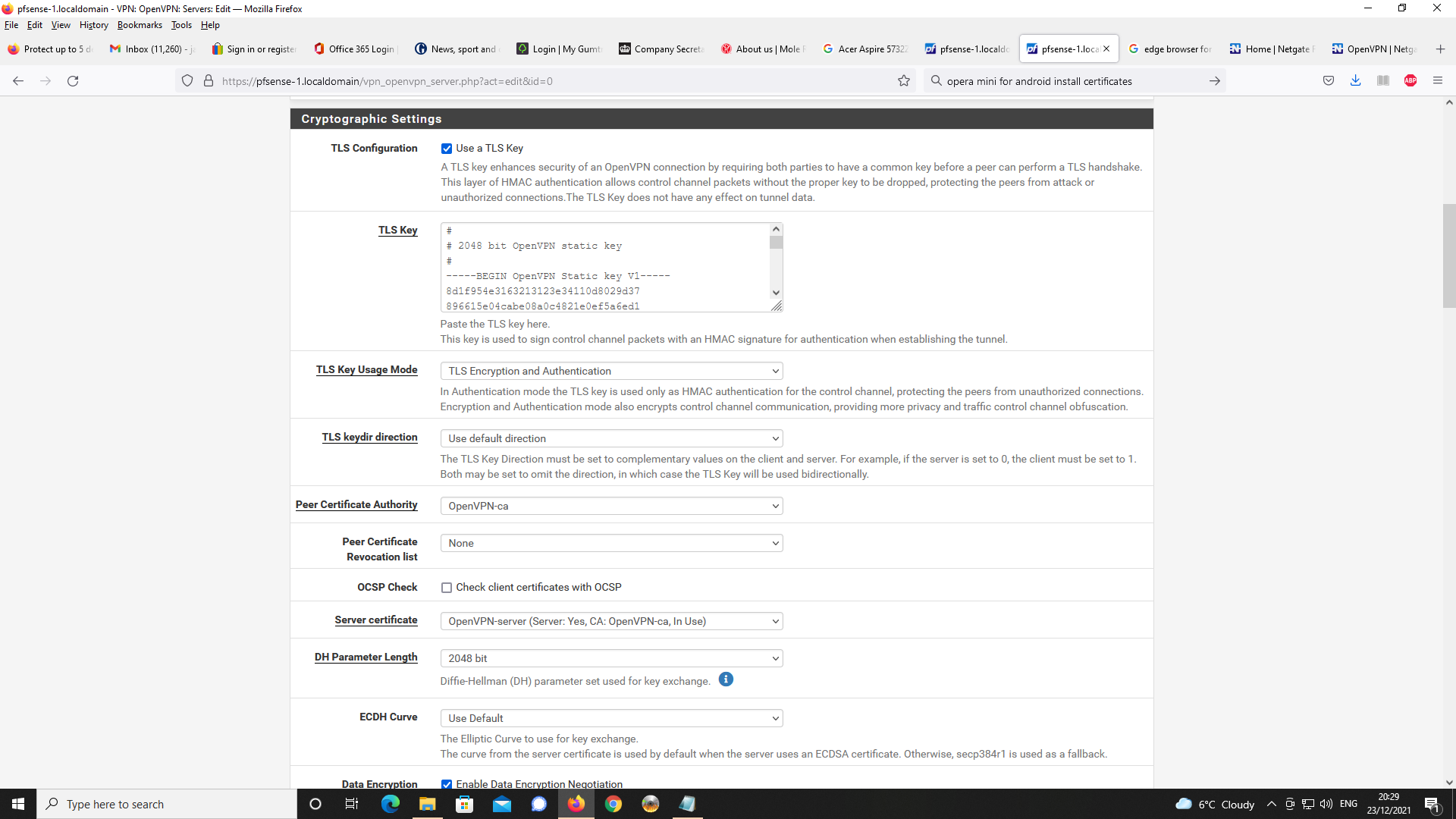
These https://forum.netgate.com/assets/uploads/files/1640291609199-img016.png are normally not needed : See here VPN > OpenVPN > Client Specific Overrides.
Remove it/them.
Re generate a opvn config file for your client. -
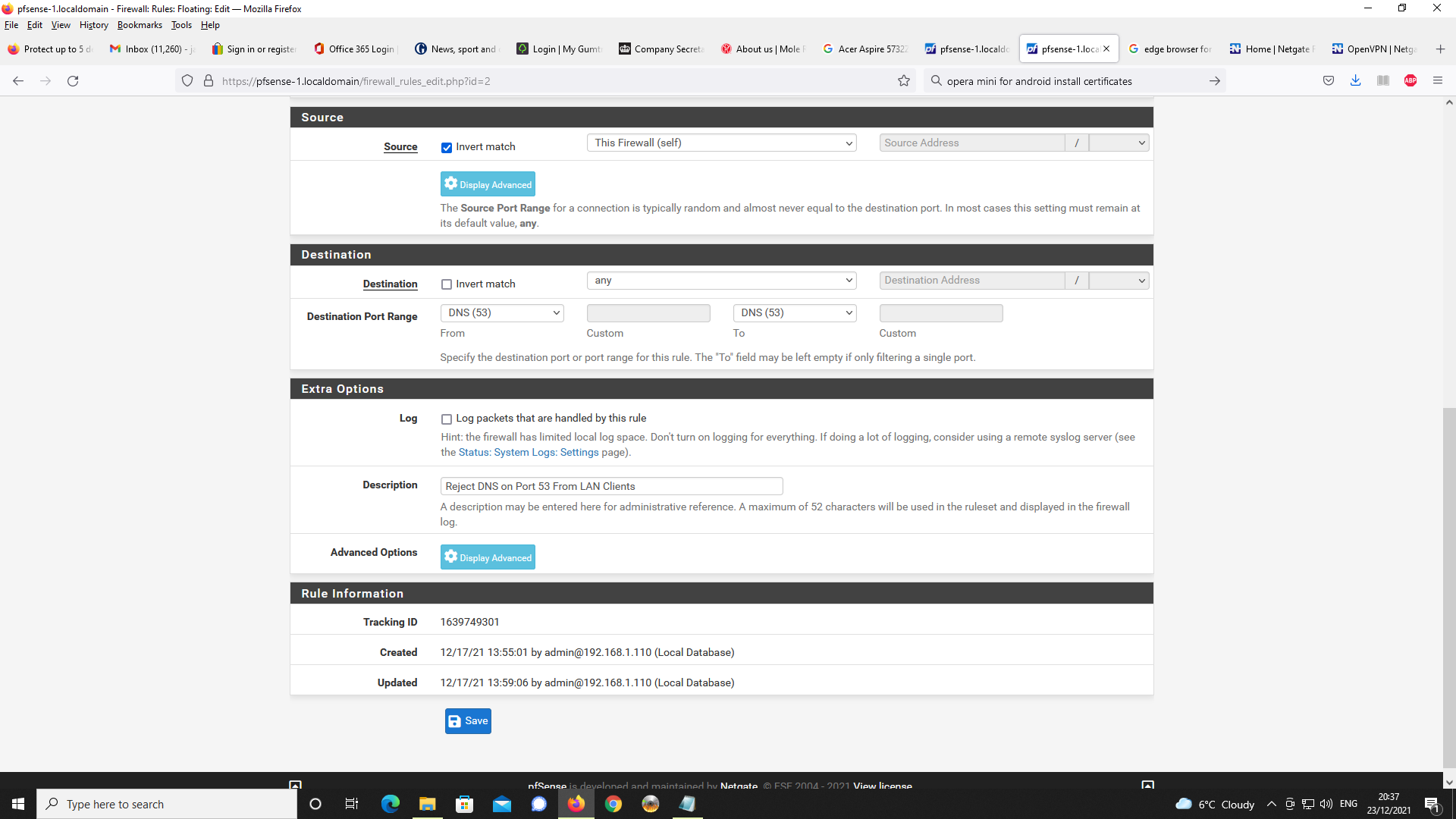
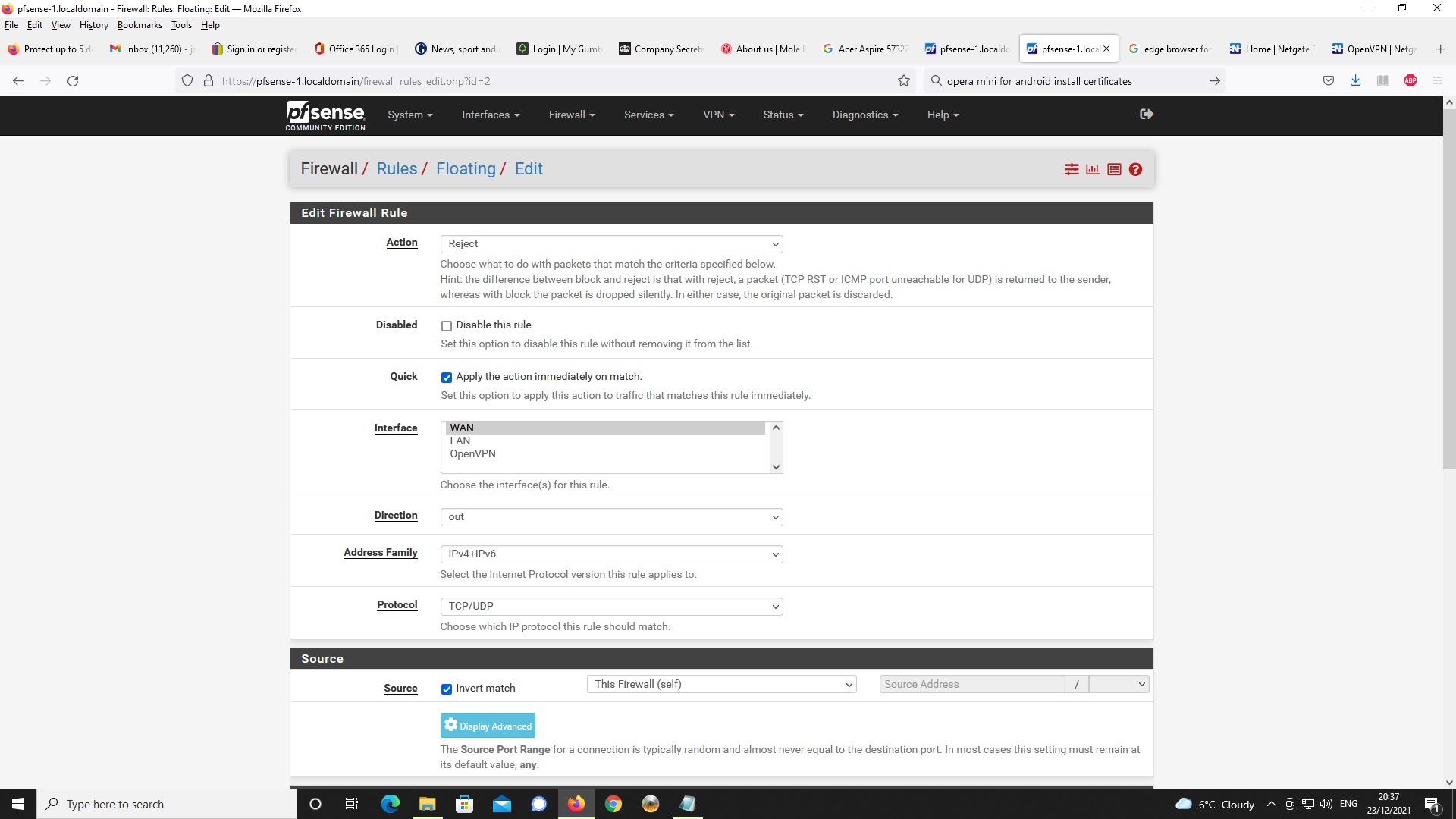
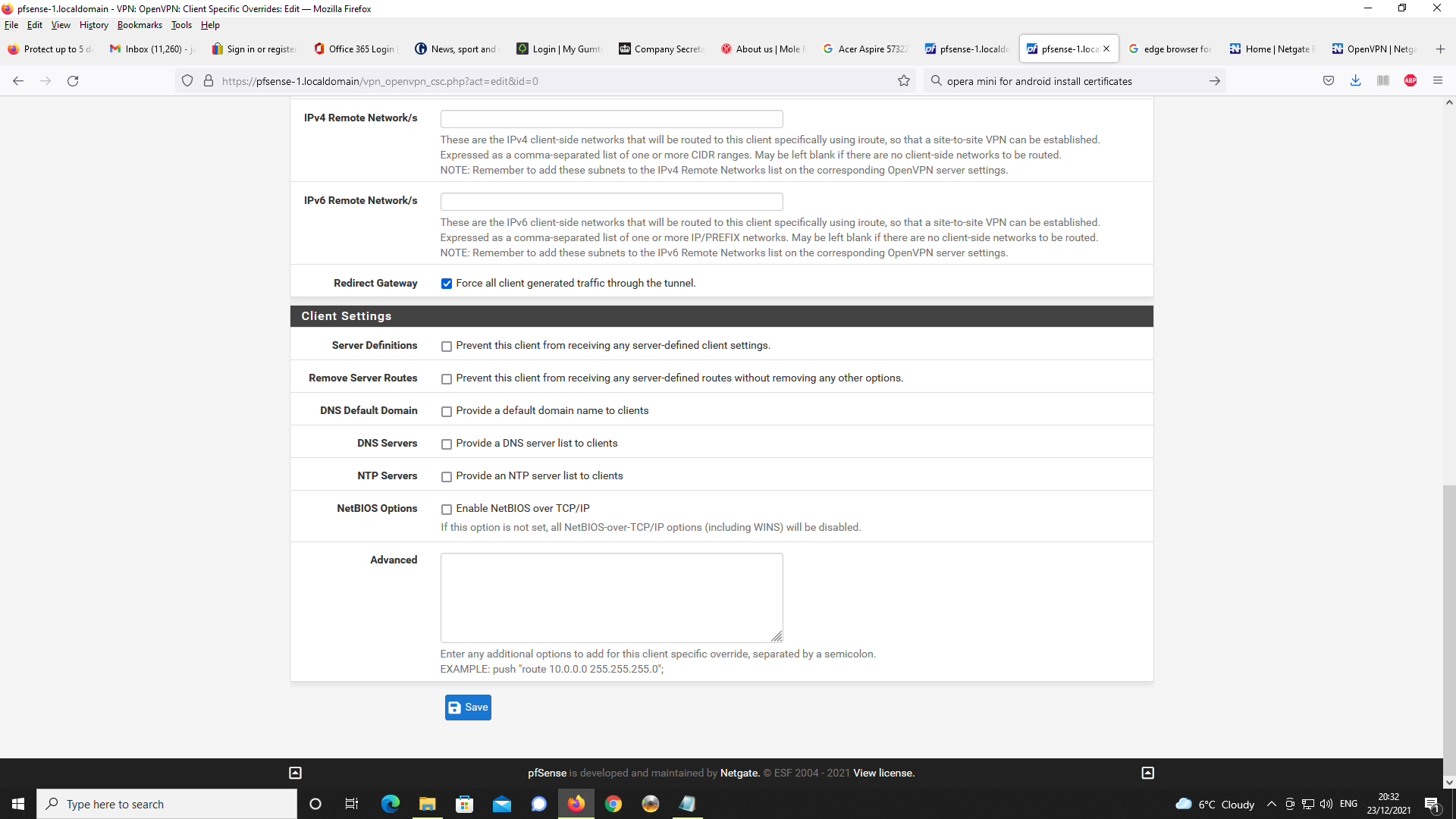
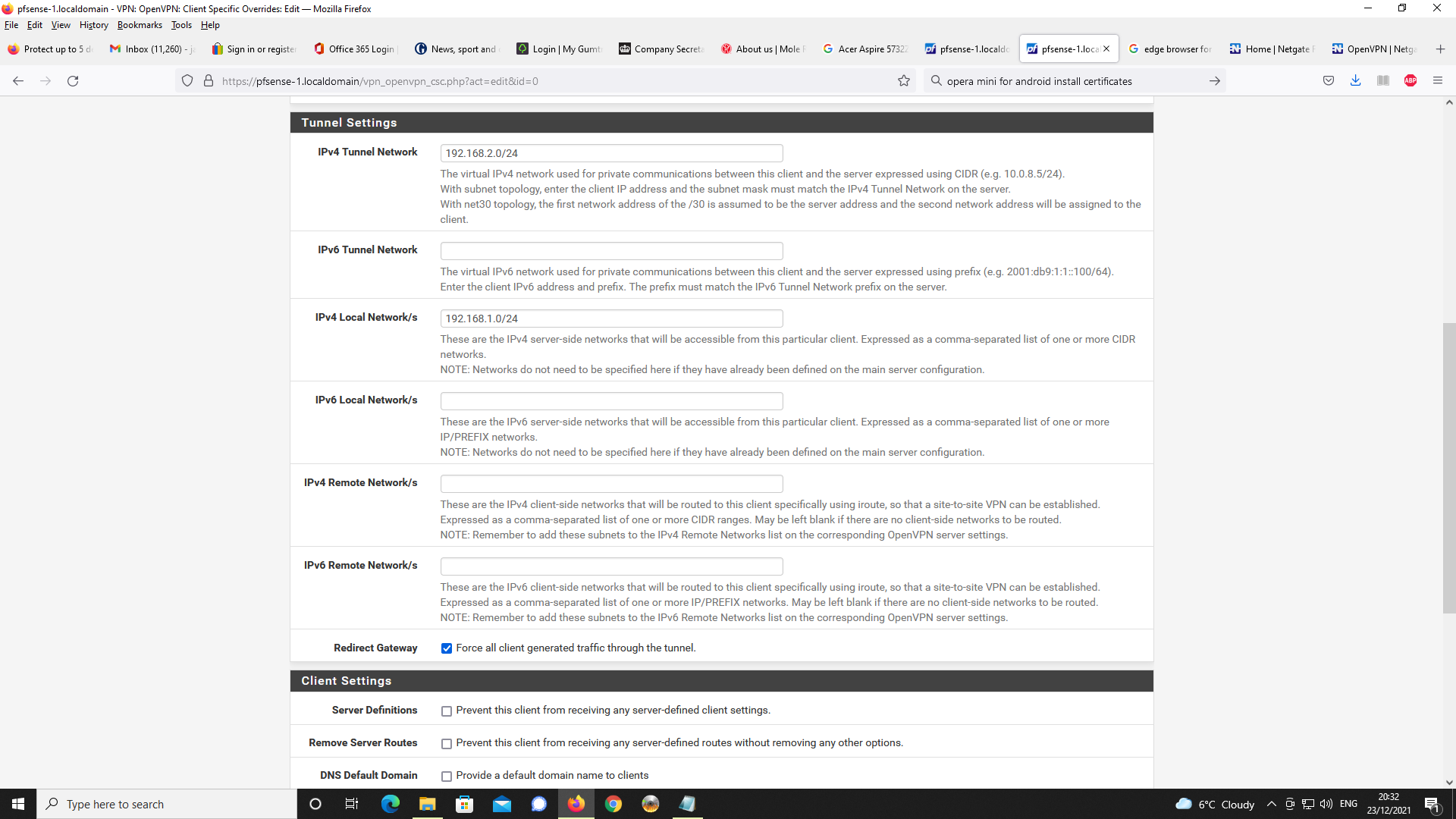
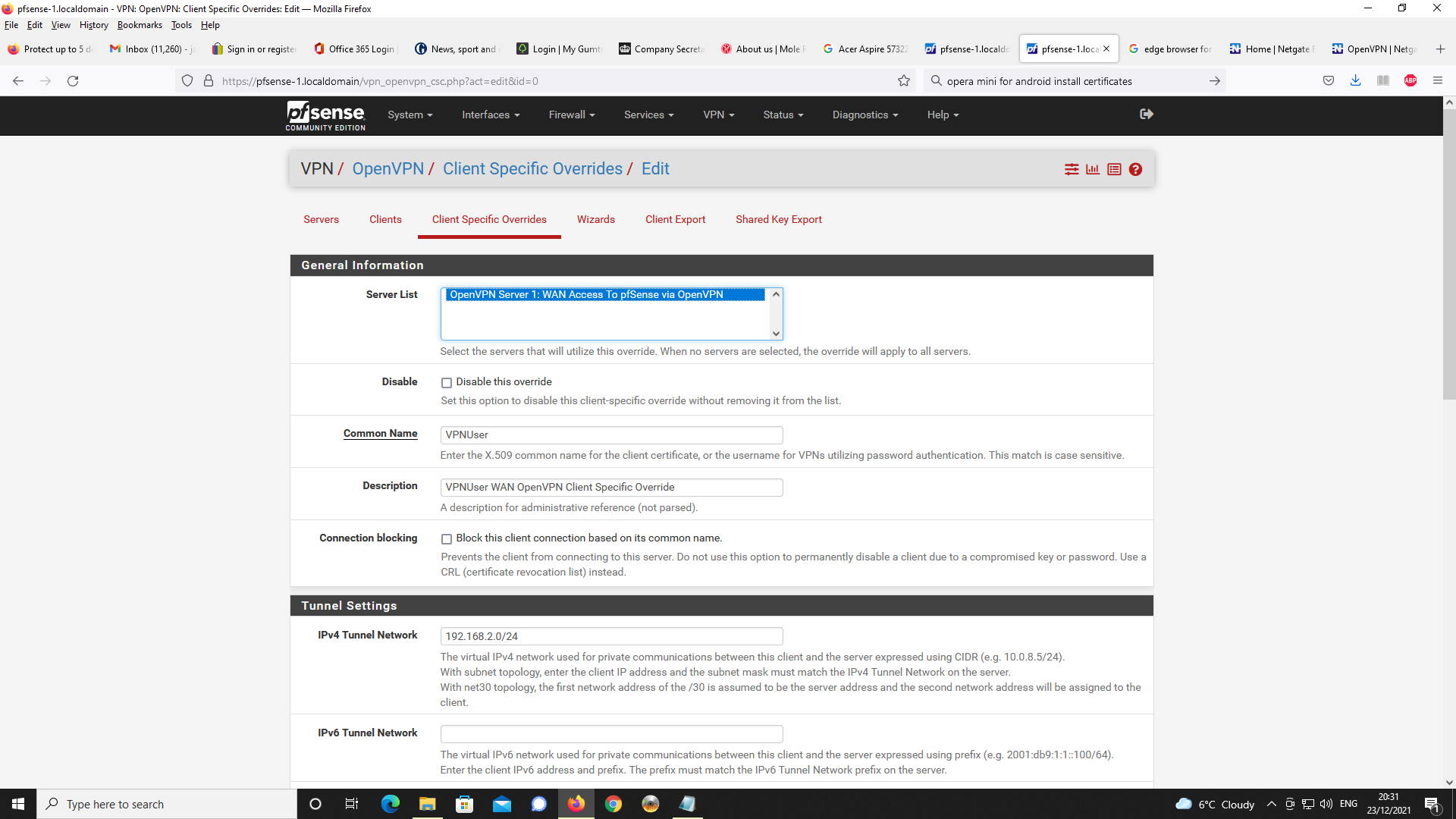
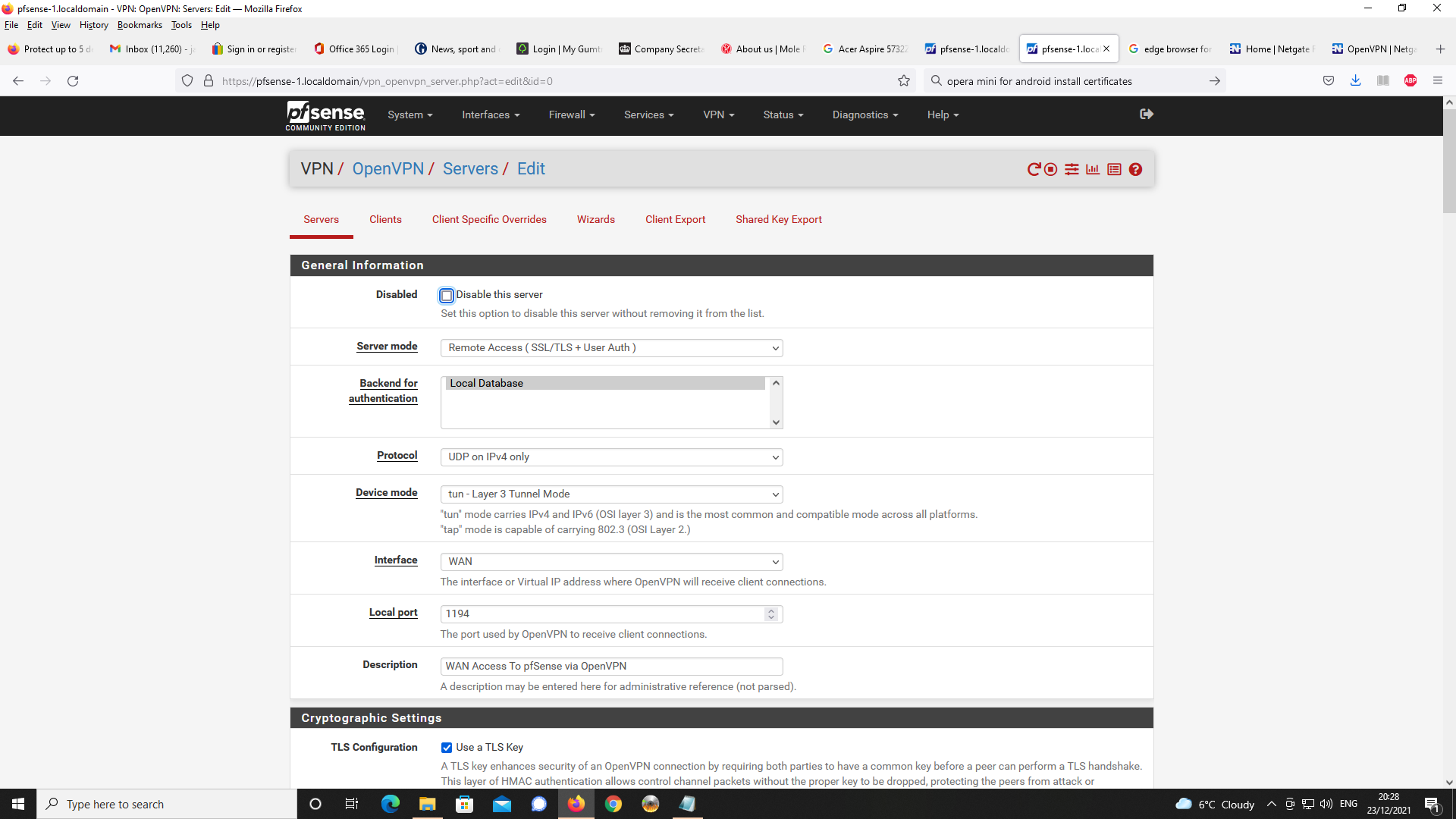
I am using client specific overrides in order to specify IPv4 LAN clients on pfsense
as 192.168.1.0/24 as you cannot specify these on the actual OpenVPN server config.
On my version of pfsense v2.5.2, it only allows you to specify IPv6 networks.I take the point, specifying 192.168.2.0/24 on the client specific override for the IPv4
tunnel network is unncessary as this is already specified on the OpenVPN server config settings. I will remove this on the client specific override and see if changes behaviour
on the VPN client being allocated 192.168.2.0.Additionally, if you look at the exported client OpenVPN Connect OVPN file, this only
provides server settings such as tun settings, the certificates et al. For example, my OVPN
file contains;persist-tun
persist-key
data-ciphers AES-256-CBC:AES-256-GCM
data-ciphers-fallback AES-256-CBC
auth SHA512
tls-client
client
remote 'public IP address for WAN' 1194 udp4
setenv opt block-outside-dns
verify-x509-name "OpenVPN-server" name
auth-user-pass
remote-cert-tls server
explicit-exit-notifyOf course for the above, I have replaced the actual IP address for my WAN with the stated
text string and the certs are omitted for clarity.This is all that is exported at least, that is, with my settings. This means in practice you can change the settings for the OpenVPN server below these settings in the OVPN file without requiring a new, export for the OpenVPN Connect client to your mobile handset or notebook etc.
Ditto the case for client specific overrides.In use, the OpenVPN Connect will connect to the server on pfsense, get the settings set out
in the client export, configure these and use the certificates to configure the VPN connection.
Additionally, the OpenVPN Connect client will obtain the relevant settings from the OpenVPN
server settings which are not specified in the OVPN export and enforce these as it builds
the VPN connection. This includes client specific overrides.If you look at the log on your OpenVPN Connect client once the connection has been
established, you can see this to be the case. The settings which are not specified in the
OVPN client export, are stated as OPTIONS in the OpenVPN Connect client log. You can
change these (at least in my case) without, as asserted, the need for a fresh OpenVPN
connect client export.Upon reflection, you may be able to use the advanced configuration custom settings on
the OpenVPN server config in order to specify the LAN network 192.168.1.0/24. I'm not
sure of this or don't know, rather, how to do this.
That being so, using the client specific override to specify the LAN network would be not
necessary and in my case, would preclude from having to specify this in that way.Thanks for your observations.
-
I made that change to the client specific override and now OpenVPN Connect is allocating 192.168.2.2 to the client and not 192.168.2.0.
Thanks for the help.