Routing between openvpn client and subnets accessible from openvpn server via wireguard site-to-site tunnel
-
Hi all
I have 2 sites each with a pfsense edge. I've recently changed the site-to-site vpn between them form an IPSEC tunnel to a wireguard tunnel. @CMCDONALD - many thanks for your recent video guide on this (https://www.youtube.com/watch?v=2oe7rTMFmqc) - my site-to-site setup essentially follows this example.
I sometimes connect to site 1 via an OpenVPN connection and before changing to wireguard I could reach the LAN on sites 1 and 2 from the OpenVPN connection to the site 1 pfsense box. Since the change, my OpenVPN connection to site 1 can only access the site 1 LAN (but not the site 2 LAN that is on the otherside of the WireGuard tunnel). The site 1 LAN can access the site 2 LAN just fine (and vice versa), but I can't figure out how to do the routing to access the site 2 LAN via the OpenVPN connection to site 1?
I've checked the firewall connections and these make sense and the traffic from OpenVPN enters the WireGuard tunnel on site 1 but is never seen at site 2. I think this is a routing issue, so wondered it someone could give me a pointer on the routing config required? Previously IPSEC SPD handled this.
My network layout and routes are per the following diagram:
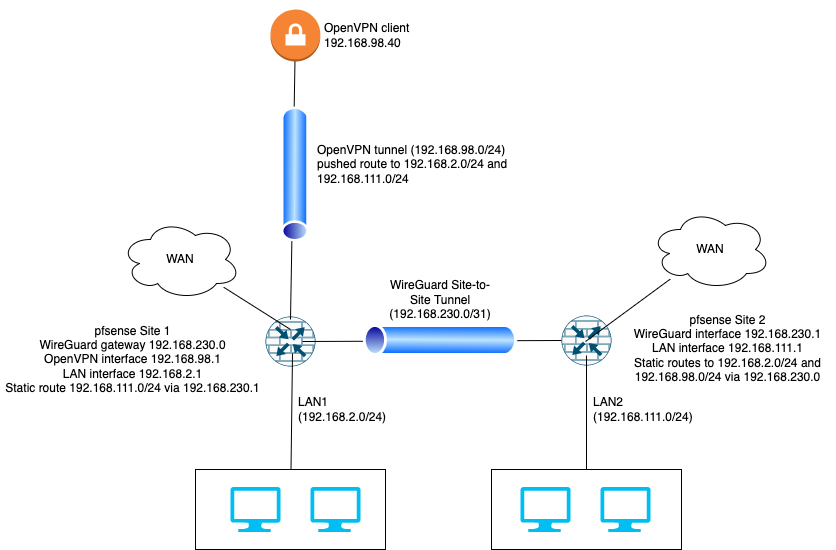
Thanks
-
Pushing routes is not enough.
You also need to tell the openvpn tunnel what are the "local" lans.
As far as openvpn is concerned
192.168.111.0 is "local"
This is configured at the openvpn server
You can look openvpn iroute command for more info.
add 192.168.111.0 (and 98 too) and test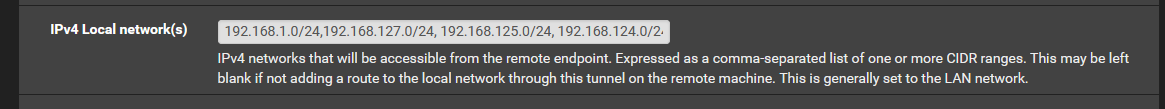
-
@netblues Thanks for the suggestion. As it happens I already had that bit right, but I stupidly overlooked including the 98 subnet as an allowed IP for the WireGuard tunnel - so problem solved! Thanks again.