How to stop logging out of state packets from bad clients (Roku)
-
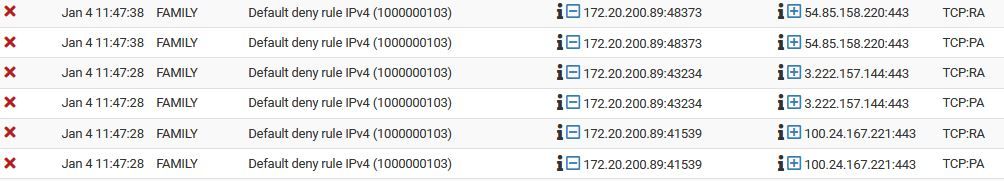
I have a few clients, some wired, some wireless which consistently flood my logs with out of state packets. I do not think I have an asymetric routing problem but I may since I have multiwan. It is only my rokus and pixel phone.
Aside from disabling logging of all packets blocked by the default rule, is there a way to construct a rule to block and not log out of state packets? I don't really understand the TCP flag set and out of set options in the firewall rule advanced page.
Thanks
Devan
-
@ddbnj yeah its common to see those on cell phones, they are horrible at switch from cell to wifi, or trying to reuse connections that have long timed out, etc.
If you don't want to see such blocks, you could turn off the logging of the default deny, and then just create your own rule that only logs syn traffic.
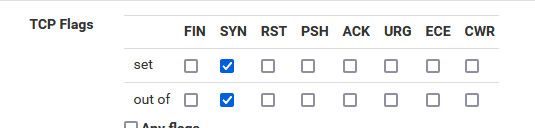
Put this rule at the bottom of your rules, set to log.. Now you only see stuff that was syn and not allowed by your rules.
edit: I do this on my wan rules
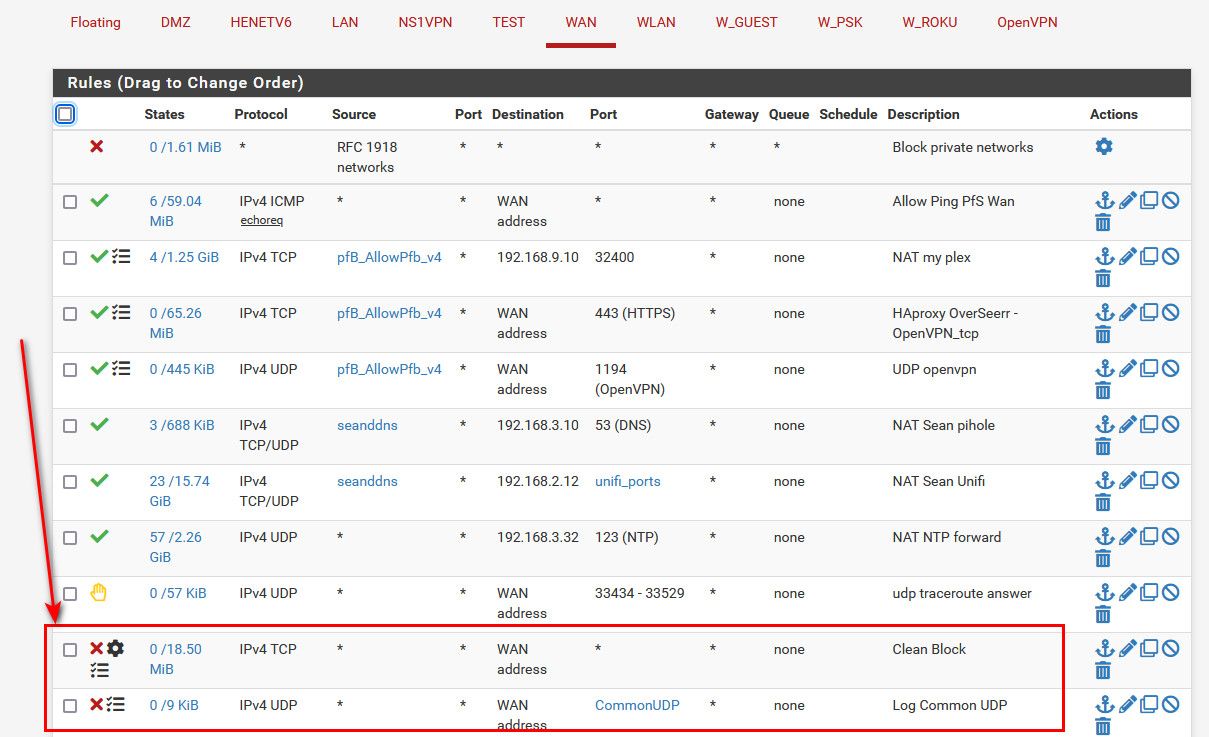
And then I log only udp that is of interest of me.. Common ports - have no desire to see all the other noise.
SYN are what can start a connection.. So if you want to see traffic that is trying to actually open a state that is blocked, you only need to log those.
-
Thank you.
Do you have similar rules on your local networks? I have teenagers which questionable personal device security practices.
-Devan
-
@ddbnj I personally do not have such rules on my lan side interfaces currently. I do have some log rules for some specific blocks and specific allows. But my sons haven't been teenagers in like 20 years (both in their 30s) and long gone from the home.. But I get your reasoning ;)
If I was needing to troubleshoot something where I need to see all blocks for sure, I would just toggle the default logging back on.. But sure you could do the same sort of rules on your lan side interfaces.
I personally am more interested in unsolicited inbound into the wan that is interesting.. Gives me an idea what major noise is going on right now - remember back awhile when those modems got compromised and were generating tons of traffic globally - that popped up to the top of my block list in the report.. Then there is always the common 80,443,22,21,3389, etc.