Unknown IPs attempting to connect?
-
I have 3 users that are VPN'd pretty much all day long. Recently they have started to complain their RDP sessions are disconnecting. Sometimes it is very sporadic and other times it is pretty much unusable. I'm looking at the logs and I see a lot of attempts from unknown IPs. Ho can I stop this from happening? I do have a rule I set up to block specific IPs for OpenVPN but the unknown IPs are constantly changing so that really isn't a viable solution.
Here is a snippet of the log. Note that none of the IPs are for anyone that has VPN capability to this firewall:
https://pastebin.com/embed_js/5CGCG3V7
-
@dennis100 So they are connecting to OpenVPN and trying to authenticate? Some thoughts/options:
- generate geo IP aliases in pfBlockerNG-devel and limit OpenVPN listening/server ports to just your country
- have the remote staff set up dynamic DNS hostnames and limit access to those hostnames
Otherwise, it's the Internet and you'll likely see connection attempts 24x7.
-
@steveits
I'm seeing the same IPs on another pfsense install at another location. I strongly suspect this is some type of attempt to hack a VPN connection. -
@dennis100 I agree, but I doubt it’s specific to you…we see connection attempts for various things all the time across our clients. Just bots scanning for things to hack into.
-
@dennis100 said in Unknown IPs attempting to connect?:
https://pastebin.com/embed_js/5CGCG3V7
Well there is going to be noise, is this is what you think is causing you problem?
MULTI: new incoming connection would exceed maximum number of clients (10)Did you try increasing this number?
Couple things you could do to reduce noise and connection attempts - change port, limit what IPs could talk to you.. Are all your users in the US for example, if so use pfblocker to only allow US IPs to talk to your vpn. I do this for my vpn connection as well as my plex connection.
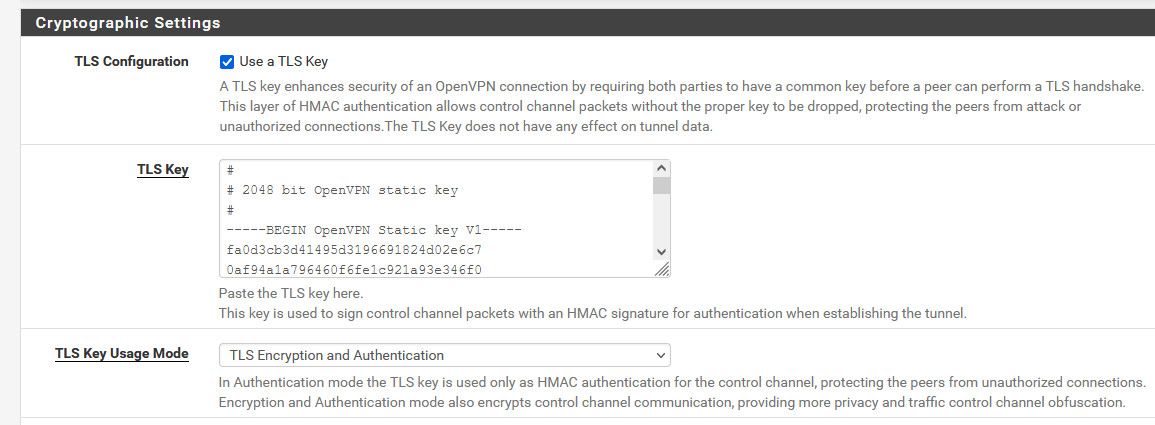
Are you using tls-auth? This should drop connections right away
https://openvpn.net/community-resources/hardening-openvpn-security/
The tls-auth directive adds an additional HMAC signature to all SSL/TLS handshake packets for integrity verification. Any UDP packet not bearing the correct HMAC signature can be dropped without further processing.
-
@johnpoz
I do suspect exceed the max number of clients is causing the problem. It was 5 and I bumped it to 10, but the problem persists. Should I just bump it to something high, say 100?
I've added implementing pfblocker to restrict to the US to my project list. I'll also take a look at the link you posted. -
@dennis100 I would think that tls-auth is default, so that really should be in place, unless your using say username/password type vpn only?
But if that was in place, nothing should be even able to have open start to process a connection if the packet being sent does first pass that authentication.
BTW - that first IP is from GB.. so if that is where your at, geo blocking with pfblocker wouldn't help.
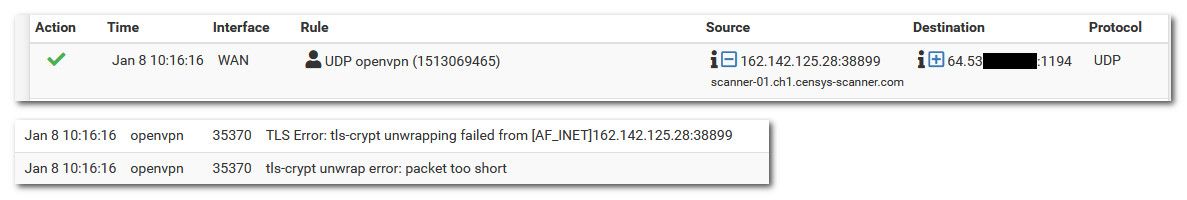
So for example - I don't get a lot of traffic that gets through because I only allow US IPs, but here is some outside scanner IP that tried check my 1194 vpn port.. You can see the firewall allowed it.. But openvpn dropped it right away because it didn't pass tls, I use crypt plus auth
do you not have this set in your vpn settings?
Here are hits in mine last couple of days.
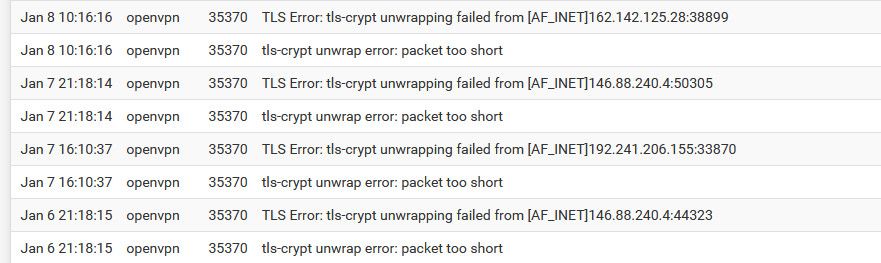
None of those got very far because the first udp packet didn't pass muster.
-
-
@dennis100 ah if your clients can not do it? Then you have a bit of a problem.. But that is something you would want to implement because it keeps noise away from your vpn.. Only authorized clients to actually even start a conversation with your vpn, etc.
But I find it hard to believe the viscosity client could not do that.. Its basic openvpn stuff.. Maybe not do tls-crypt, but they should be able to do at min tls-auth
edit: so quick google found this, so there might of been a problem with older client, but looks like from that that the viscosity client should for sure support tls-crypt
https://www.sparklabs.com/forum/viewtopic.php?t=2647
Here is tls-auth I found on their site. So clearly they support it, you would just need to set it up
https://www.sparklabs.com/support/kb/article/advanced-configuration-commands/#tls-authAdd an additional layer of HMAC authentication on top of the TLS control channel to mitigate DoS attacks and attacks on the TLS stack.
In a nutshell, tls-auth enables a kind of "HMAC firewall" on OpenVPN's TCP/UDP port, where TLS control channel packets bearing an incorrect HMAC signature can be dropped immediately without response.