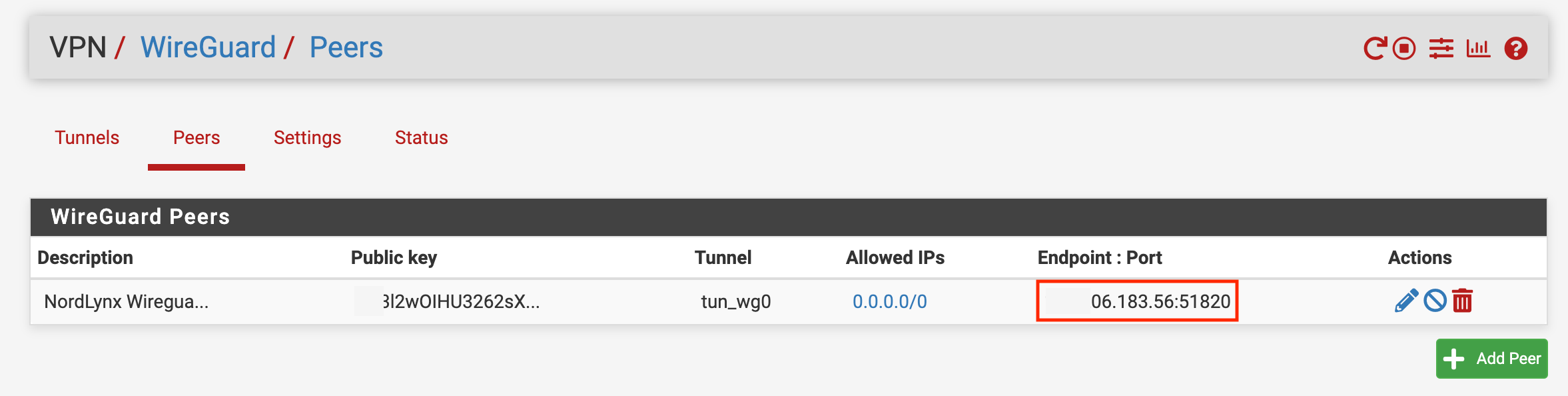
Endpoint IP - Peer vs WG vs Status
-
See the screenshots below.
The Endpoint IP address shown in the Peers List / Edit page does not match the Endpoint IP address actually being used by the wireguard service or the IP address that is displayed by the Peer in the Status tab:
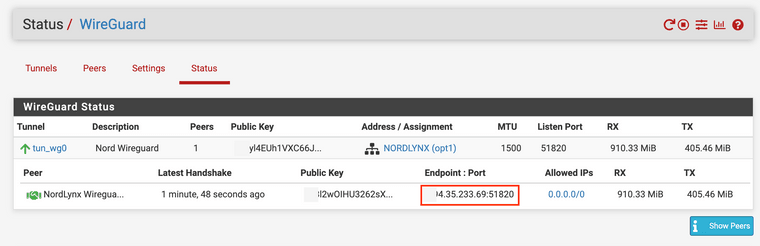
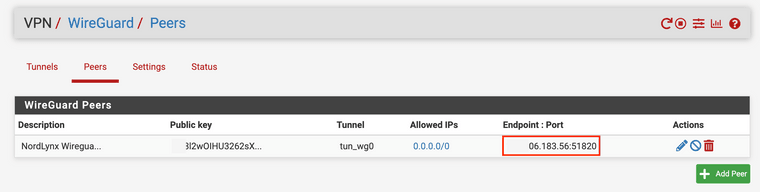
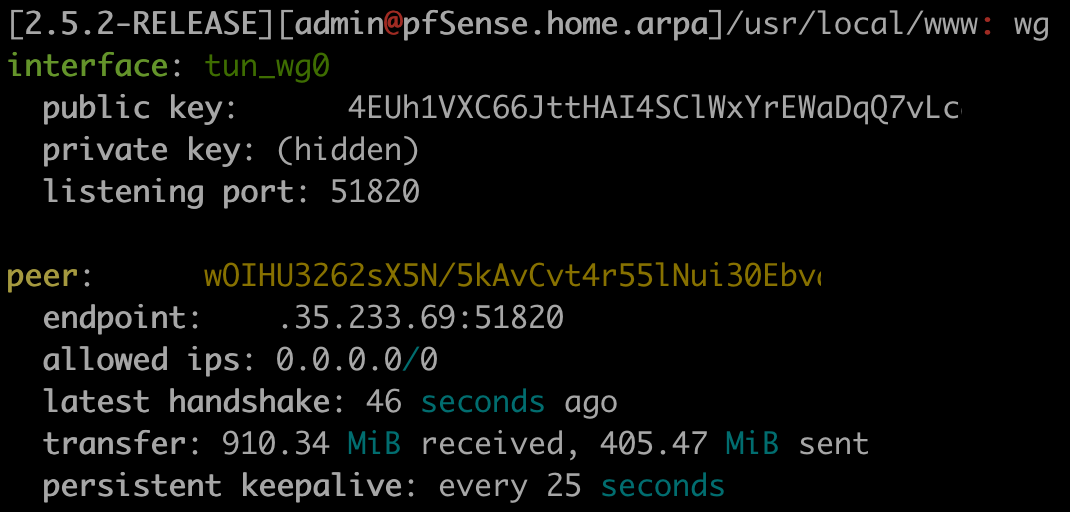
-
What is even stranger is that if I set a new Peer Endpoint, save and apply it, nothing happens.
If I then restart the service, the new IP gets applied to the wireguard service.
But if I continually query wg thru the console i.e.
wgevery few seconds, the endpoint that is being used will alternate between the old endpoint ip and the new one ! -
And in the system logs:
/rc.openvpn: OpenVPN: One or more OpenVPN tunnel endpoints may have changed its IP. Reloading endpoints that may use NORDLYNXGW.But NORDLYNXGW interface is not associated with OPENVPN, it appears that the openvpn service is restarting the wiregaurd endpoints.
-
It looks like when the wireguard endpoint is changed, the interface goes down and that triggers the Gateway Alarm.
Then rc.openvpn receives this alarm and assumes that the alarm came from openvpn and this then kicks off reloading of the wireguard interface
-
Amendment to above:
It looks like when the wireguard endpoint is changed, the interface goes down and that triggers the Gateway Alarm.
then rc.gateway_alarm reloads all services (except wireguard):
/usr/local/sbin/pfSctl \ -c "service reload dyndns ${GW}" \ -c "service reload ipsecdns" \ -c "service reload openvpn ${GW}" \ -c "filter reload" >/dev/null 2>&1And it seems that rc.openvpn does not check if the gateway that triggered the alert was actually an openvpn interface.
I can fix this with:
$if = $gateways_arr[$argument]["interface"]; if (strpos($if, 'ovpnc') !== 0) { $msg = "$argument gateway is not an OPENVPN interface ($if)"; log_error($msg); return; }But I'm not sure if that is really necessary as it does not prevent the toggling of the wireguard endpoint between the old and new ip address.
-
The easiest solution to prevent the openvpn reloads / restarts is just to disable the Gateway Alarm Actions.
But still unsure why the status > peers endpoint IP is not being displayed correctly, I think it is picking up the previous / old one.