Trouble actually hitting the correct applet from external connection
-
@menethoran read the thread I linked to @PiBa is the resident guru of guru's when it comes to HAproxy..
With my page of him, maybe he will drop by and smack some of his wisdom down..
BTW - going to move this to the proxy section..
-
 J johnpoz moved this topic from Firewalling on
J johnpoz moved this topic from Firewalling on
-
@johnpoz sounds good!
Yeah, im already using real certificates (which looks like that was part of the problem in the other thread...)
-
@menethoran take note of not being able to pass it thru really directly, etc.
None of the stuff I have hosted with haproxy used ssl on the backend, I always just did the ssl offloaded to the frontend..
-
@johnpoz
OK, maybe im making this WAY more complicated than i need to. Once the traffic hits my network, i dont "really" care how secure it is as long as its encrypted coming in and going out. Can I in theory, just drop the SSL handling of the backend and leave it on the frontend? Or do i need the backend to have SLL because I have it set for SSL offloading? -
@menethoran the only issue, is I think nextcloud is pretty strict on wanting to use ssl. But sure if you can get it to load locally without ssl just by going to http://IPaddress:port then you could do whatever offloading you want on the front in haproxy.
-
@johnpoz actually, thats just it... I CANT hit it locally with HTTP, only HTTPS...
-
@johnpoz
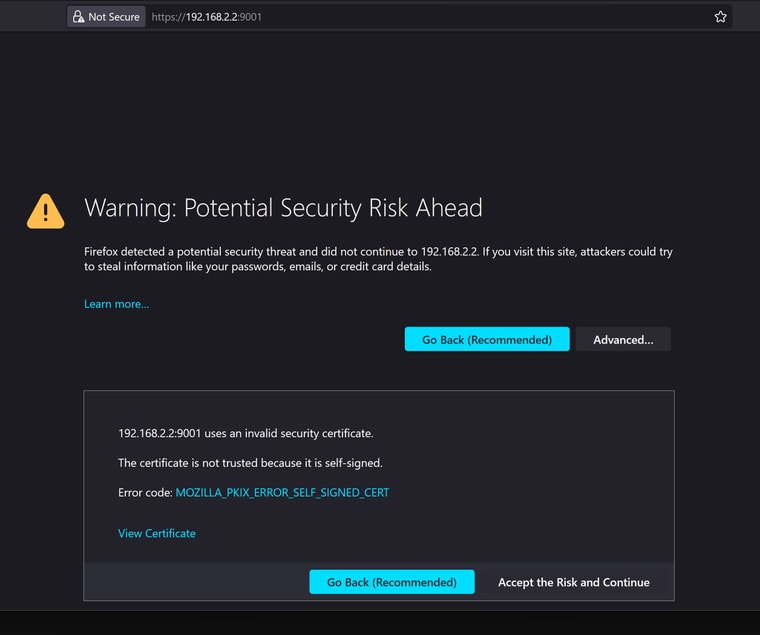  d.jpg)
d.jpg) -
@menethoran Then you have to setup haproxy frontent and backend using ssl, or you need to change nextcloud to only use http..
That is selfsigned cert, change it to use an acme cert on the nextcloud box.. Or I think there was a thread around here getting haproxy to use backend self signed certs?
-
@johnpoz honestly, im starting to think i need to go over to the TrueNAS guys and ask them why this whole thing is picking up their cert... I mean, i get that theres something wonky going on... and theres a good chance that part of it heavily involves PfSense, but i feel like maybe i dont understand (or we dont) how TrueNAS is handling the incoming traffic.
That make sense or am i grasping at straws here?
(And FYI: I refuse to run Nextcloud over a non-secured connection... not that you were telling me to go that direction, just letting you know where i stand)
-
@johnpoz also, i would prefer to avoid self-signed certs if at all possible...
-
@menethoran said in Trouble actually hitting the correct applet from external connection:
i would prefer to avoid self-signed certs if at all possible...
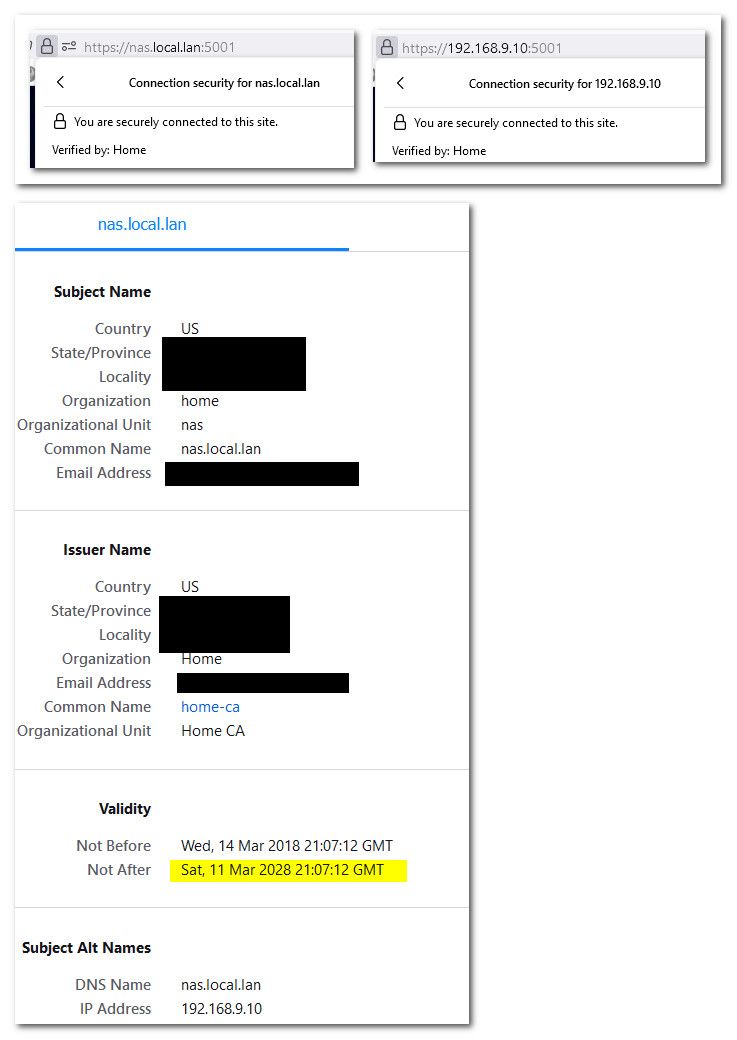
Completely agree - I wouldn't use them, especially when pfsense makes it so easy to create your own CA and create any certs you want and have your browsers trust them. All of my services that use ssl are signed by my home ca, and my browser trusts them. Printer gui, switches gui, my unifi controler, my nas, etc..
And they all have san entries for just the IPs they use, so can access them via fqdn (without having to be a public domain) or just their IP.
And since these were created before browsers when with like the year limits, these certs are good for 10 years ;)
-
@johnpoz So, strike my previous comment. It looks like the nginx message is actually created by PfSense (i get the same message if i try to connect PfSense with a forced HTTPS that originates as an HTTP connection
What I dont understand is why? SM i missing something in my settings (frontend/backend) that is causing PfSense to think im trying to connect with an insecure connection?