stretchoid.com IP list for use in blocking their port scans
-
In the last 24 hours, more than 150 separate IP addresses controlled by stretchoid.com have scanned numerous ports on two static IPs assigned to me.
The "opt-out" form at stretchoid.com is simply phishing. If you fill it out, the scans continue, but they have your name, email address, and CIDR block you asked them to stop scanning.
Stretchoid's website claims that "Stretchoid is a platform that helps identify an organization's online services." I see no way to access their findings and they don't seem to offer them for sale.
The vast majority of their scans seem to be aimed at finding vulnerable admin interfaces and services, not online services for public use. Given the ongoing cost of having more than 800 scanning IPs hosted on Digital Ocean, I wonder if "stretchoid.com" is being funded to identify targets for state-sponsored cybercrime, such as ransomware attacks.
For years, Digital Ocean, has allowed this to go on. I suspect that it may be an example of "bulletproof hosting" in which the owners of stretchoid.com have paid for a "no kill" clause in their contract with Digital Ocean.
Since all of the stretchoid.com IPs I've seen in recent times have been in the 192.241.128.0/17, I did a little one-liner on my iMac Pro to query for PTR records, dumping the results to a text file:
for N in {128..255}; do echo "Testing 192.241.$N.0 - 192.241.$N.255" >> stretchoid_ips.txt; for L in {0..255}; do host -t PTR "192.241.$N.$L" | grep -qF 'stretchoid.com.' && echo "192.241.$N.$L `host -t PTR \"192.241.$N.$L\"`" >> stretchoid_ips.txt; done; doneIt's ugly and crude, but the output is simple to edit into the IP address and PTR record you see at the file link below, which is sorted by PTR record.
Copy the list into your clipboard, go to Firewall --> Aliases in pfSense and then select "Import" (at the bottom right). Paste the clipboard contents into the Aliases To Import box and you can use the resulting IP alias to block stretchoid.com scans.
Notes:
- The list is based on public PTR records (reverse DNS), the accuracy of which I cannot verify.
- If there are stretchoid.com IPs outside of the 192.241.128.0/17 block that I queried, they are not included.
- I make no guarantees. The list may be wrong. My methodology may be flawed.
- If you choose to use the list, you do so at your own risk.
- I am not offering to maintain the list, update the list, or remove the list should IP addresses be reassigned.
- This isn't my list. It's public information as of January 10, 2022. I would welcome someone turning it into a maintained feed that others (including me) could use.
-- Sissy
-
@sissy said in stretchoid.com IP list for use in blocking their port scans:
IPs I've seen in recent times have been in the 192.241.128.0/17
Why would you need to parse anything? If you have the netblock they are coming from, just block the whole /17?
For that matter block all of digitalocean inbound.. What/who would be coming from some IP hosted at DO? Sure not going to be actual clients you would like to allow.. Block their whole freaking ASN, which you can easy setup with pfblocker.
Inbound block doesn't stop you from going there, but it would stop any inbound unsolicited traffic to your IP, like scanning for what ports you have open,etc... I show the ASN for that netblock to be AS14061 – DigitalOcean, LLC
-
@johnpoz said in stretchoid.com IP list for use in blocking their port scans:
@sissy said in stretchoid.com IP list for use in blocking their port scans:
IPs I've seen in recent times have been in the 192.241.128.0/17
Why would you need to parse anything? If you have the netblock they are coming from, just block the whole /17?
Because there are 32K IP addresses in that range and only 2.5% of them are assigned to stretchoid.com. Some of the others are assigned to legitimate small businesses and organizations, some of which could be clients of, or vendors to, someone for whom I provide services.
For that matter block all of digitalocean inbound.. What/who would be coming from some IP hosted at DO?
Email is one thing that comes to mind, and there are just shy of half a million mail servers hosted on Digital Ocean.
Sure not going to be actual clients you would like to allow.. Block their whole freaking ASN, which you can easy setup with pfblocker.
No one would want to do business with python.org, letsencrypt.org, or Alex Green Farms, which sells organic fruits and vegetables, right? I may not like that the National Eating Disorders Association (NEDA) chose Digital Ocean as their provider, but NEDA is the type of organization that might turn to my client for content creation.
Inbound block doesn't stop you from going there, but it would stop any inbound unsolicited traffic to your IP, like scanning for what ports you have open,etc... I show the ASN for that netblock to be AS14061 – DigitalOcean, LLC
My firewall is on a business Internet connection on which I host servers. It's not something through which I'm web surfing. I don't have the option of firewalling off 2.6 million U.S. IP addresses and then just hoping that everything works out.
There is another very good reason for parsing: I have a rule that is logging port scans by stretchoid.com so that I have a record of the activity.
-
@Sissy Thanks for this. Also, looks like they have an opt-out form on their website, FWIW. https://stretchoid.com/
-
@sprocktech said in stretchoid.com IP list for use in blocking their port scans:
Also, looks like they have an opt-out form on their website
In my opinion its strange to opt-out from something I never opt-in ... and btw - I dont like self proclaimed Internet Policemens ...

AS14061 is in my pfblocker and until now I never saw from there any legit connection ...
-
@johnpoz said in stretchoid.com IP list for use in blocking their port scans:
For that matter block all of digitalocean inbound
Also works with the IP-feed Cinsscore
in pfblockerNG-devel for all the strechoids ...
-
@fireodo yeah a home user would have zero need for anything coming from DO at all.. But as mentioned you might if your hosting email services, etc.
I found this parsed listed of the stretchoid IPs
https://github.com/SilvrrGIT/IP-Lists/blob/master/stretchoidLooks like last updated 21 days..
As the OP stated that opt-out thing could just be way to get more info - who knows.. I see their IPs hitting my wan... To me its just one of the many other bots, scripts, whatever - who cares.. If they find my open ports... Can't lock down the ports from every single IP - have them locked down to country already..
What does it get you blocking them - still traffic hitting your wan.. So what if they find out your running smtp server.. You are running a smtp server open to the planet anyway ;)
If anything I could see just blocking and not logging the traffic maybe if its filling up your logs with stuff you don't care to see.
-
@johnpoz Doh, I skipped over the part in the OP about the opt-out. Oh well, I at least wanted to say thanks for the contribution. Everyone has a different way of doing things.
-
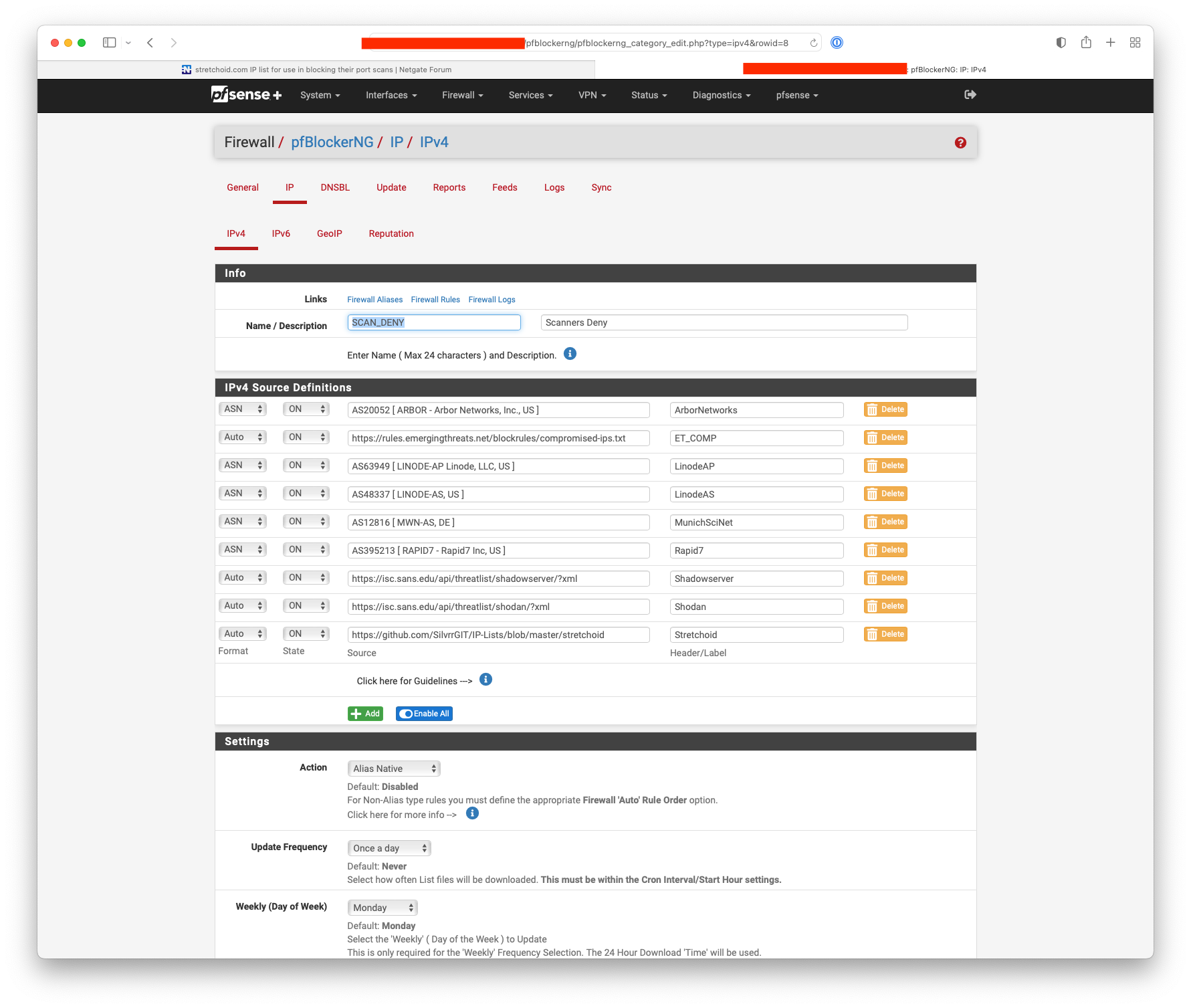
https://isc.sans.edu/api/threatlist/shodan/?xml
https://isc.sans.edu/api/threatlist/shadowserver/?xml
Handy for pfBlocker:-
-
Hi all,
This is an old subject but has good SEO.
There is lists of stretchoid IPs: https://github.com/SilvrrGIT/IP-Lists/issues/85I built a much more complete one, you can find it here: https://github.com/SilvrrGIT/IP-Lists/issues/85#issuecomment-1657267386
I currently use this with my pfSense/OPNsense setup as a firewall alias.
-
@williamdes said in stretchoid.com IP list for use in blocking their port scans:
I built a much more complete one, you can find it here: https://github.com/SilvrrGIT/IP-Lists/issues/85#issuecomment-1657267386
I currently use this with my pfSense/OPNsense setup as a firewall alias.
Thanks, today I encountered some stretchoid hits from your list, which were not in the PRI group feeds.
-
@Bob-Dig what were the ips?
-
@johnpoz said in stretchoid.com IP list for use in blocking their port scans:
@Bob-Dig what were the ips?
I already deleted the log file so I can't tell. But when I looked, they were almost identical to ones, which were already in PRI1.