Firewall for DMZ
-
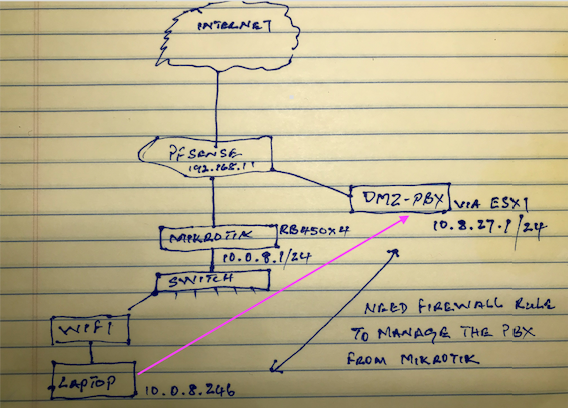
Here is a diagram of my setup below:
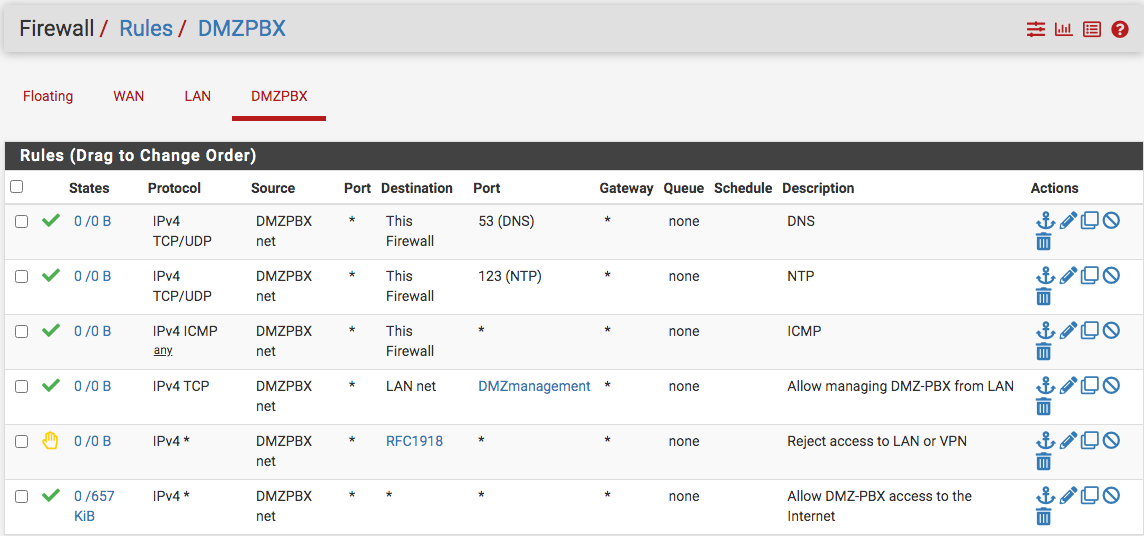
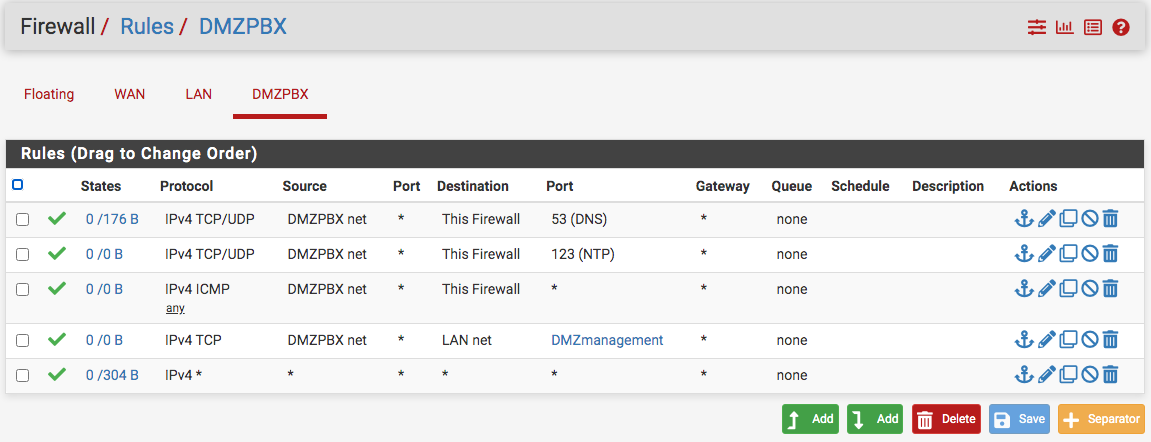
Here is my DMZ firewall rules and I have a firewall rule to forward management traffic to the DMZ from the Mikrotik yet I am getting timeout on ping...why? Firewall rules on pfSense correct so I can rule out pfSense?
-
@nollipfsense I'm having a hard time understanding your drawing..
You have 192.168.1 on pfsense, but then off of that you have this dmz in 10.8.27
And then some other router with 10.0.8, is it also doing nat? Do you have routing setup in pfsense? How is this pbx on esxi connected from a 10.8.27 to 192.168.1 - is it also doing nat?
your firewall rules make no sense.. you list this dmzpbx as 10.8.27, but then your blocking rfc1918? But then your wanting to allow to the firewall for 53 and 123, how would it get there if your blocking rfc1918..And bogon?
If you have network X off of pfsense, and you want network Y (also off pfsense) to get to X then those rules would go on the network Y interface..
-
@johnpoz said in Firewall for DMZ:
your firewall rules make no sense.. you list this dmzpbx as 10.8.27, but then your blocking rfc1918? But then your wanting to allow to the firewall for 53 and 123, how would it get there if your blocking rfc1918..And bogon?
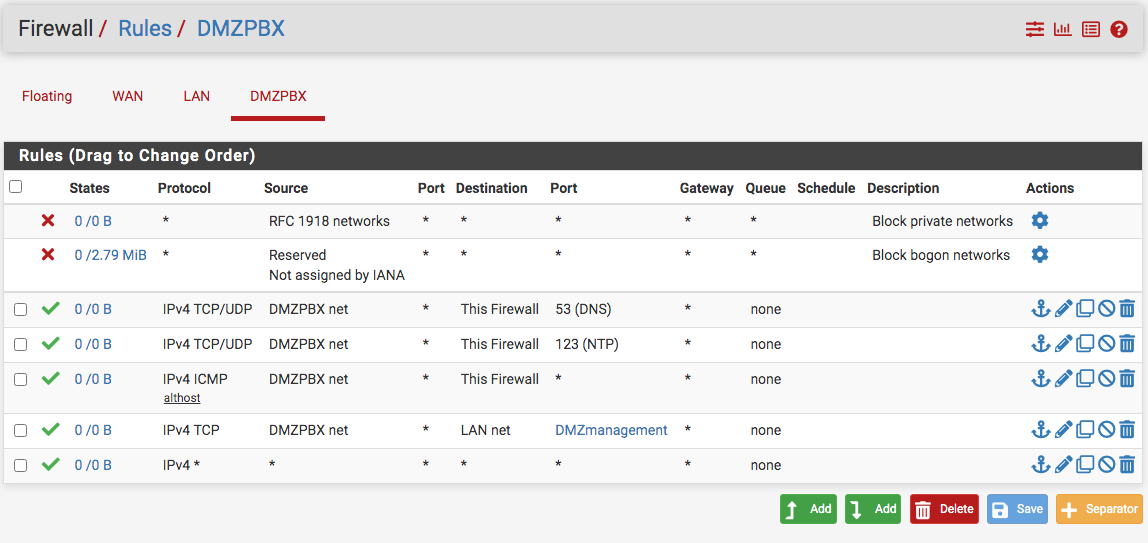
LOL, well John I just realize that and came to post when I saw your response and had a good laugh. I had watched Jimp's old video on DMZ (pfSense 2.3 days - https://www.youtube.com/watch?v=QFk5jX-oeSo&t=9s). However, things have changed so much and the DMZ interface has the button to automatically add to firewall when checked. So that what I did while not thinking of the consequences to the other rules.
So, I spend three or four hours scratching my head why I can ping the DMZ interface from the laptop but could not ping the EXSI from the laptop nor the DMZ interface from the ESXI or the switch it attaches to.
I'll see whether I can drag the rfc1918 rule down. Well, those rules cannot move so the choice was to just remove them. Now, I can ping the switch but not the ESXI and I loan out my monitor...need to wait a few days for it to return.
-
@nollipfsense those rules don't make a lot of sense either... Your last rule is any any, so all the allow rules that are more specific are just just filler..
They might make sense if you were going to log specifics..
Still didn't explain how anything gets anywhere because you only list pfsense 192.168.1.1, but then you have different 10 networks connected to it?
-
@johnpoz said in Firewall for DMZ:
Your last rule is any any, so all the allow rules that are more specific are just just filler..
They might make sense if you were going to log specifics..Again, I agree and was just following Jimp's presentation but realizing things have changed that I can do some of those on the interface menu itself. I'll have to reconsider the DMZ configuration. I had set this up previously when I was using the Mac Mini and was trying to remember what I had done before going to war with Cox ISP. Any recommendation?
@johnpoz said in Firewall for DMZ:
Still didn't explain how anything gets anywhere because you only list pfsense 192.168.1.1, but then you have different 10 networks connected to it?
One of the real cool feature of the Mikrotik firewall is connection state; so, since pfSense is gateway as well as DNS server to the Mikrotik and its devices through DHCP, they know the addresses associated with pfSense LAN net, such as the DMZ and the path.
-
@nollipfsense said in Firewall for DMZ:
One of the real cool feature of the Mikrotik firewall is connection state
Yeah stateful firewalls are cool ;) Why you have 2 have no idea.. So I take it your mikrotik is doing nat from the 10 address behind to this 192.168.1 network on pfsense. But what about your dmzpbx that you show on some esxi host, which looks like its connected only to a 192.168.1 network, but then lists 10.8.27 network.. How exactly is that suppose to work? Is that internal nat of esxi, do you have some vlan also going to this esxi host?
Just not sure your laptop is suppose to know how to get to this 10.8.27 network from that drawing.. Are you wanting to hit your esxi 192.168.1.x IP that is connected to pfsense and your mikrotik? And port forwarding via the nat on your esxi?
-
@johnpoz said in Firewall for DMZ:
Why you have 2 have no idea..
Before discovering pfSense, I had Mikrotik RB450G for over ten years and got to learn it and really liked it. Then, I met the fascinating pfSense and the IDS/IPS capabilities...fell in love and decided to keep the two since the Mikrotik is already sunk cost. Last year, I decided to upgrade my network to the Lenovo box for pfSense and get the new Mikrotik RB450x4...like why not, I like both in my network. It's grossly overkill but I only live once...have fun.
@johnpoz said in Firewall for DMZ:
But what about your dmzpbx that you show on some esxi host, which looks like its connected only to a 192.168.1 network, but then lists 10.8.27 network.
Yes, the DMZPBX is a different subnet to separate it completely instead of attaching it to the Mikrotik because the PBX (FreePBX) works better not having to deal with two firewalls. I have had set this up back in 2019 but had firewall issues in receiving calls. I could not complete the project...(ISP war). I am literally plugging things back together from what was set up then.
@johnpoz said in Firewall for DMZ:
Just not sure your laptop is suppose to know how to get to this 10.8.27 network from that drawing.. Are you wanting to hit your esxi 192.168.1.x IP that is connected to pfsense and your mikrotik? And port forwarding via the nat on your esxi?
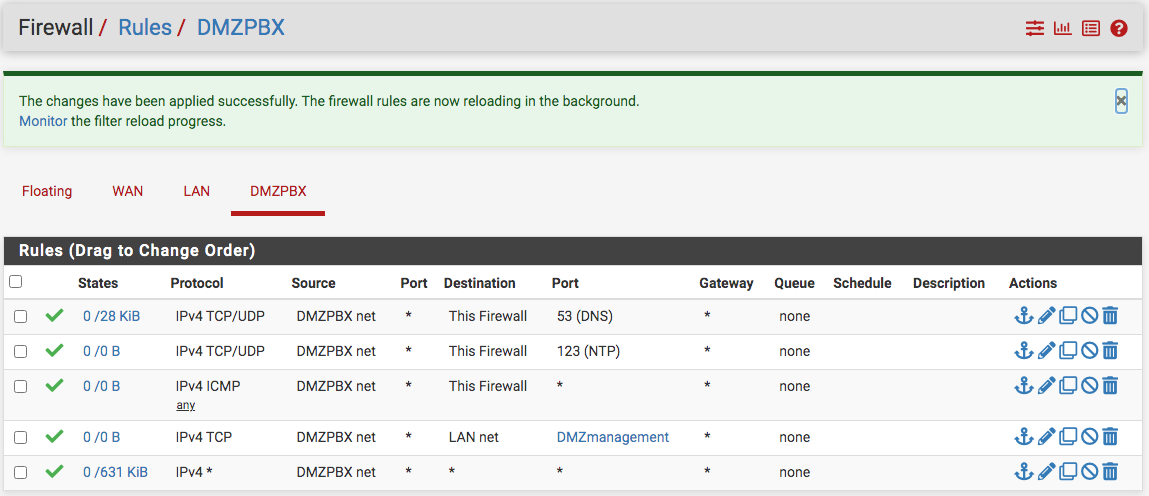
On the Mikrotik stateful firewall, I used a rule based on address list so that source address list 10.0.8.1/24 (where the laptop sits) to destination address list 10.8.27.1/24 (the DMZPBX) is allowed and accepted. Since, pfSense LAN.net know where the DMZPBX is by firewall rule, the traffic connects...I can ping the DMZ as well as the switch that connects the ESXI box (Lenovo SFF) and phone to the pfSense box from the laptop...no problem. However, I could not reach the ESXi box for some reason and will need to connect a monitor/keyboard directly to that Lenovo find out why. So, nothing was wrong with the firewall rules, except for some cleaning up...see below.
I see on the DHCP server menu for the DMZ has settings for DNS and NTP...don't know what the recommendation. Thanks John for catching the last rule wide opened any- any...fixed.
-
@nollipfsense Dude not talking about any firewall rules!! Talking about basic 101 networking
You have 2 natting devices from your drawing and your mik and esxi
This is just plain BORKED!
There is no freaking way your laptop could get to 10.8.27 behind a nat of 192.168.1
You could get to 192.168.1.x something that your esxi port forwards.. Look at your drawing - how does this make sense
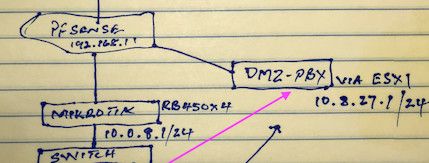
Your routing at esxi with something?? That would work - but you make zero mention of creating any routes on pfsense..
So your laptop wants to get to 10.8.27, he talks to his gateway the mik, which sends it to pfsense.. How does pfsense know how to get to 10.8.27???
You show 2 interfaces on pfsense.. But only 192.168.1.1 on your drawing..
What IPs do you have on lan and dmzpbx interface of pfsense??
-
@johnpoz said in Firewall for DMZ:
So your laptop wants to get to 10.8.27, he talks to his gateway the mik, which sends it to pfsense.. How does pfsense know how to get to 10.8.27???
You show 2 interfaces on pfsense.. But only 192.168.1.1 on your drawing..
What IPs do you have on lan and dmzpbx interface of pfsense??Yes, that's correct and only going through one natted device - the Mikrotik because it's only when leaving the pfSense through WAN would it get natted again. But, I am staying within pfSense.
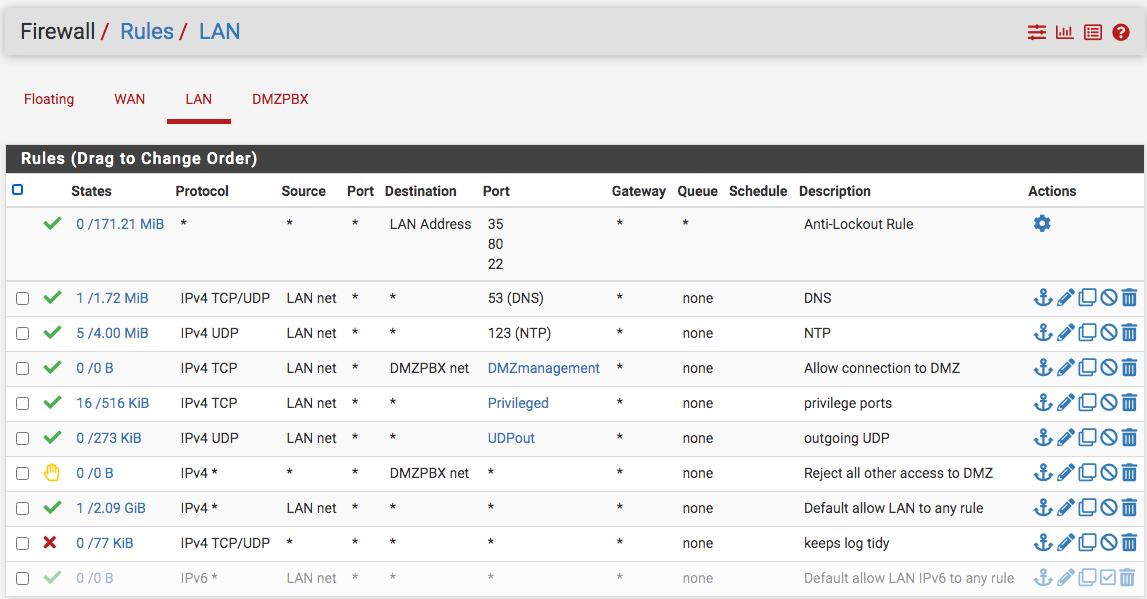
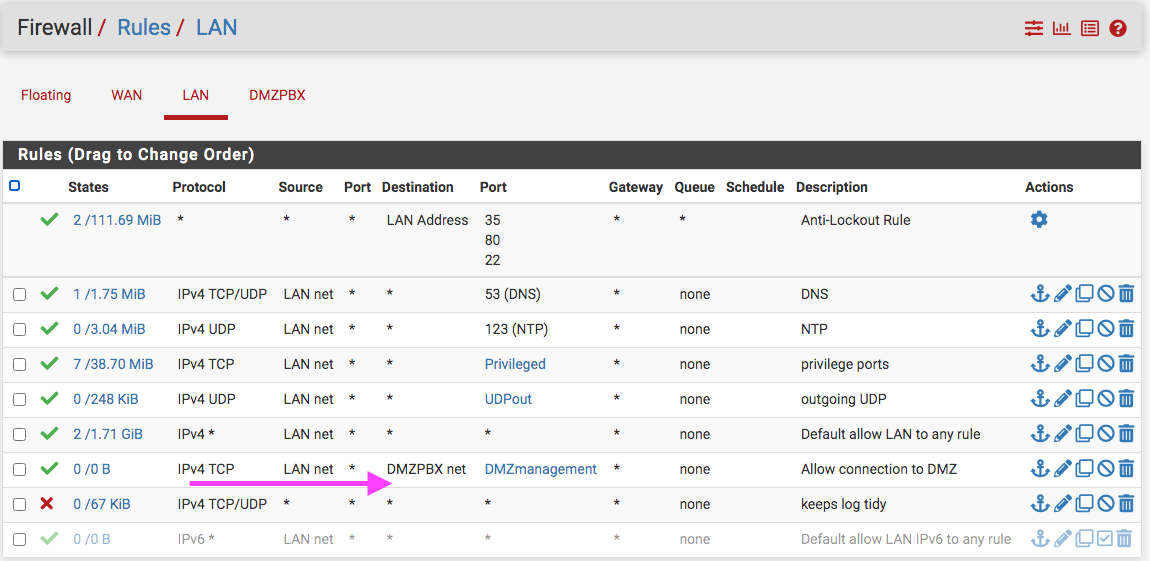
The IP for pfSense LAN is default 192.168.1.1/24 and the IP for the DMZPBX is 10.8.27.1/24. As they say, a picture is worth a thousand words; so, I took a screen shot of Terminal on my MacBook Pro with ifconfig and ping 10.8.27.2 -the switch connected to the DMZPBX Ethernet port on the pfSense box. The other pic is the pfSense LAN firewall rule.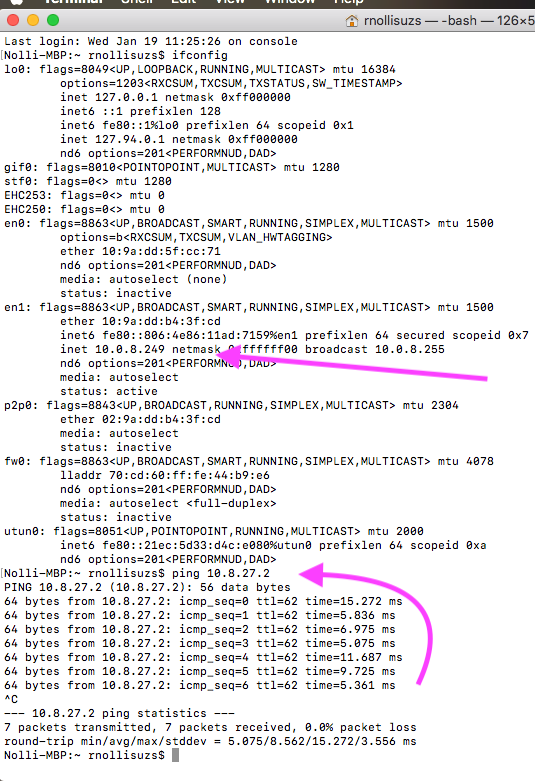
-
@nollipfsense said in Firewall for DMZ:
The IP for pfSense LAN is default 192.168.1.1/24 and the IP for the DMZPBX is 10.8.27.1/24.
So pfsense has 2 interfaces, that is not what you have drawn..
And you give no ip of this other device.. This other device is 10.8.27.2?
What is that ifconfig off of? I asked to see the IPs of pfsense..
This rules is pointless and will never be evaluated
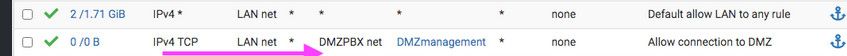
Its below a any any rule - just like all you rules above the any any make zero sense, since you have a any any rule.. Why do you think you need those other rules, your not logging them.. Your any any allows all of what those rules are doing..
Your placement of those rules don't even help us figure out if any traffic is being sent to pfsense trying to go where your allowing, because its below a rule that allows any and is never evaluated..
-
@johnpoz said in Firewall for DMZ:
So pfsense has 2 interfaces, that is not what you have drawn..
No, it has three interfaces, a WAN (Internet), a LAN (to the Mikrotik) and a DMZ which is the 10.8.27.1/24. The other device is a switch (10.8.27.2) that is connected to the pfSense so I can connect both the phone and the ESXI box (Lenovo) where FreePBX and Unbuntu server are installed, but I'll delete Ubuntu.
The ifconfig was to provide info that indeed it is the MacBook Pro and from said laptop I can ping the switch (10.8.27.2).
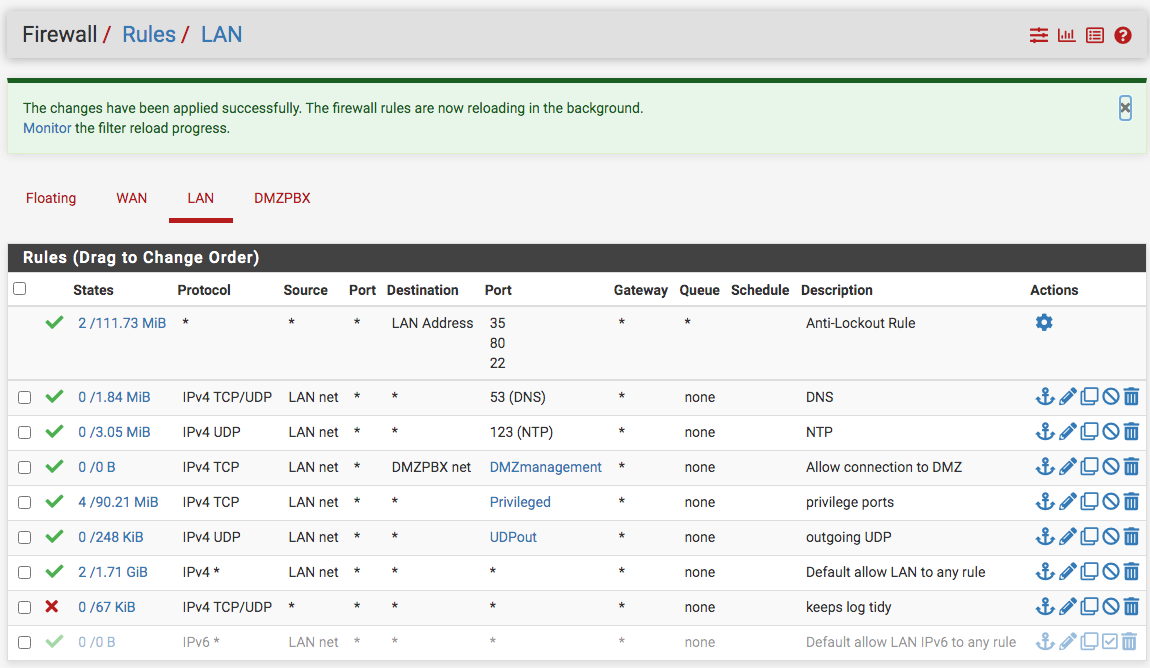
Thanks John for catching another firewall misstep...fixed!
-