VLAN configuration on Netgate 6100 for Hyper-V
-
Hello! I'm looking for some help/guidance around configuring VLANs for my environment. New to VLANs, particularly working with multiple ones on a single switch.
My setup consist of a Netgate 6100, EdgeSwitch, and Hyper-V Host.
How I think I'm setting up pfSense:
LAN: 10.0.0.1/24 (Management)
VLAN10: 10.0.10.1/24 (Web Servers)
VLAN20: 10.0.20.1/24 (App/MySQL Servers)Netgate 6100:
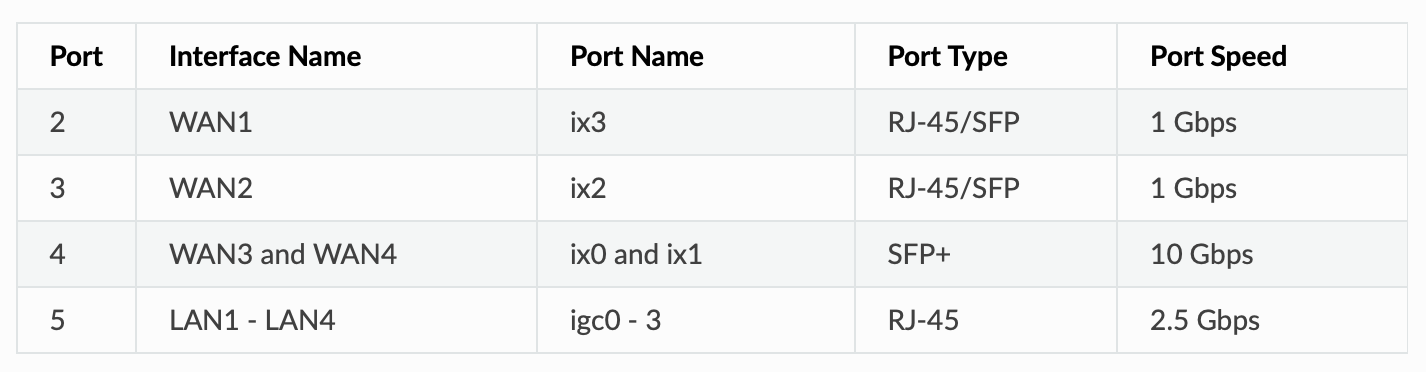
Hyper-V Host:
Single Port adapter associated with vSwitch.
vSwitch settings allow OS to share adapter.
OS vAdapter: 10.0.0.100 (VLAN1)
VM-WEB vAdapter: 10.0.10.2 (VLAN ID: 10)
VM-SQL vAdapter: 10.0.20.2 (VLAN ID :20)
VM-MAN vAdapter: 10.0.0.101 (VLAN ID: 1)In my test environment, I have this working and configured as such: VLAN10 and VLAN20 use (igc0) as parent interface...
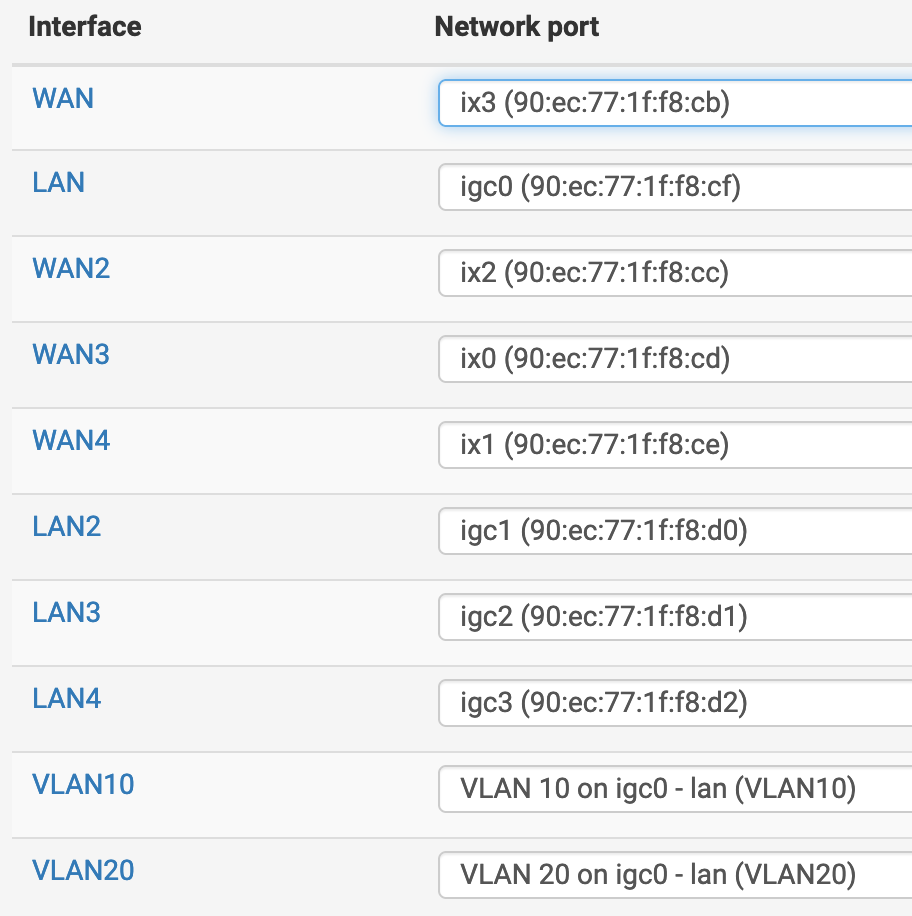
Finally, the EdgeSwitch:
All ports configured with default VLAN1 untagged, and VLAN10 and VLAN20 tagged.
Port 1: Connected to LAN (igc0) and selected as trunk port.
Port 3: Connected to my workstation; automatically gets a LAN address of 10.0.0.1/24 as expected.
Port 5: Connected to Hyper-V Host. OS gets a LAN address of 10.0.0.1/24 as expected. VM-WEB gets a VLAN10, VM-SQL get a VLAN20 address, and VM-MAN a LAN address.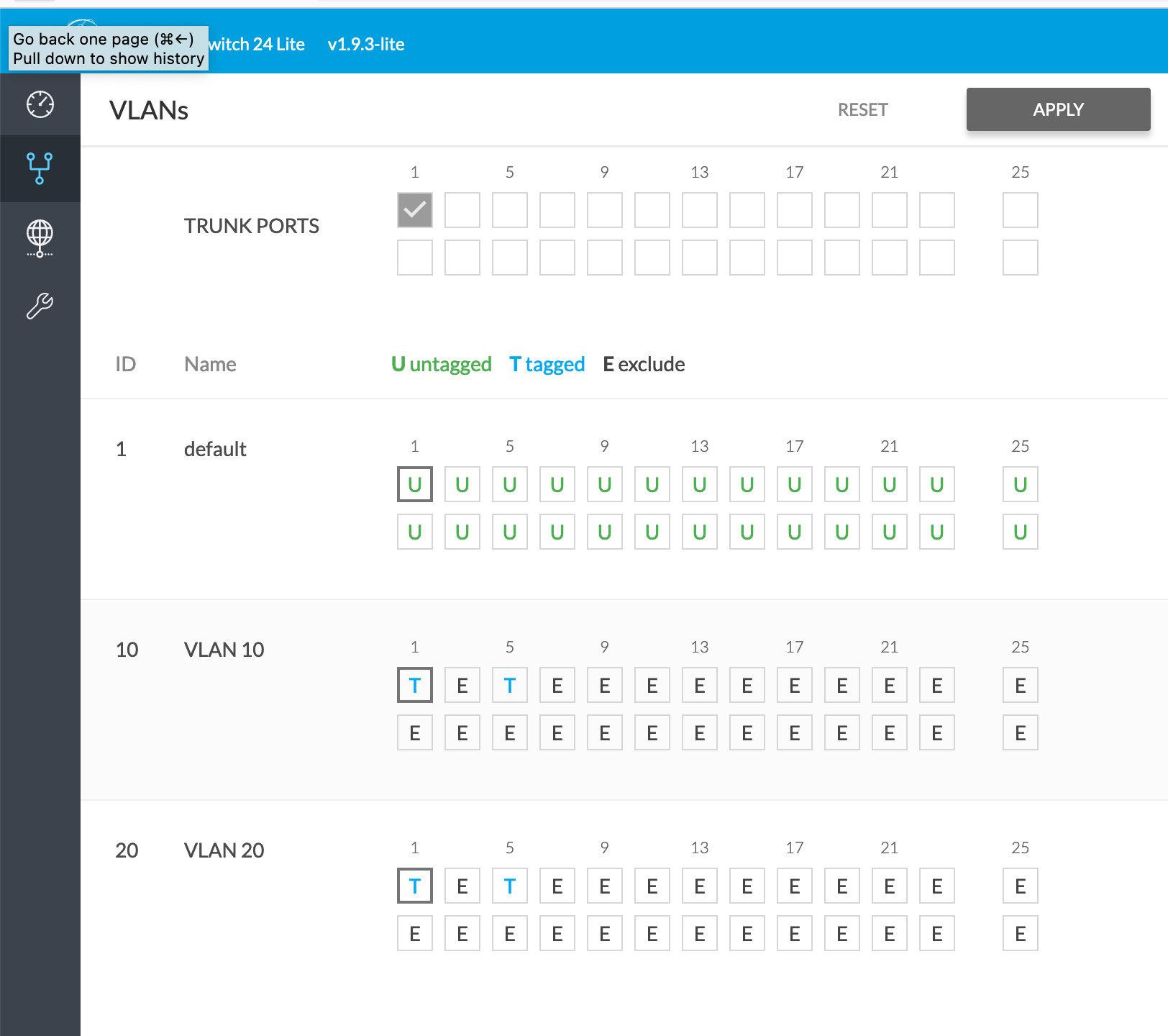
So, I guess I have a couple of questions
Is the a basically acceptable way of setting up VLANs using a pfSense and a single switch? Anything I'm missing there?For instance; if I add a backup server on Port 7, I'd leave the port untagged so that it would connect to the default (management) LAN.
As for the Hyper-V connection:
The production server has two dual-port NICs that will be teamed for bandwidth/failover. So it'll have four connections to the switch. Either way, even with a single port like in my test, that connection needs to support all VLANs as the VMs could need to join any one of them...
However, I thought I would need to trunk-port those ports? But it doesn't seem to matter whether I select trunk port or not there? Only on the one connected to the Netgate. Is that normal?Anything else I'm overlooking or can improve on (outside of adding physically separate switches)?