Trying to setup OpenVPN to HotspotShield but won't connect
-
Hi, I'm trying to setup an OpenVPN connection with HotspotShield VPN but it won't connect.
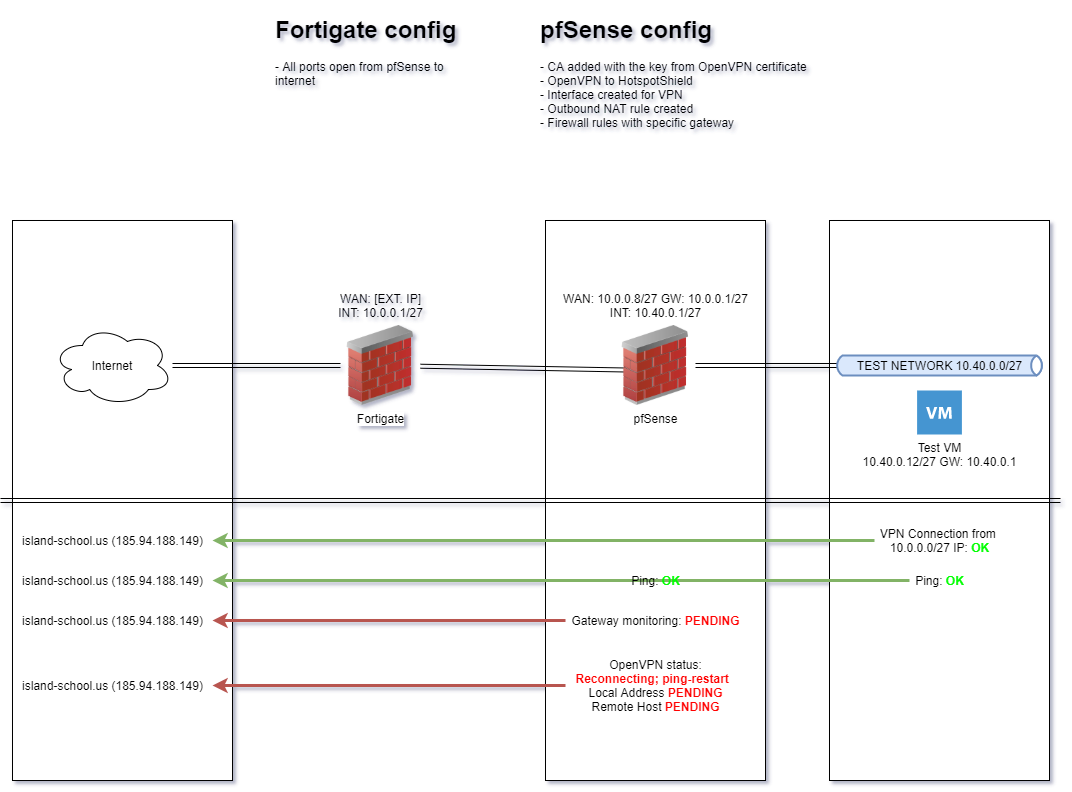
Below you'll find my network situation with an explaination what's working and what not in this topic. From pfsense I can ping to the VPN server from HotspotShield and I can setup a VPN connection from a test VM in the same network as pfsense.
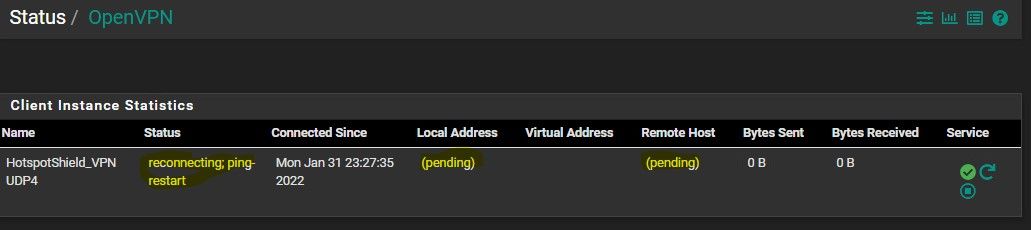
Below the logging:
Jan 31 20:59:57 openvpn 26641 Restart pause, 300 second(s)
Jan 31 20:59:57 openvpn 26641 SIGUSR1[soft,ping-restart] received, process restarting
Jan 31 20:59:57 openvpn 26641 TCP/UDP: Closing socket
Jan 31 20:59:57 openvpn 26641 [island-school.us] Inactivity timeout (--ping-restart), restarting
Jan 31 20:58:57 openvpn 26641 VERIFY OK: depth=0, CN=island-school.us
Jan 31 20:58:57 openvpn 26641 VERIFY EKU OK
Jan 31 20:58:57 openvpn 26641 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Jan 31 20:58:57 openvpn 26641 Validating certificate extended key usage
Jan 31 20:58:57 openvpn 26641 VERIFY KU OK
Jan 31 20:58:57 openvpn 26641 VERIFY OK: depth=1, C=US, O=Let's Encrypt, CN=R3
Jan 31 20:58:57 openvpn 26641 VERIFY OK: depth=2, C=US, O=Internet Security Research Group, CN=ISRG Root X1
Jan 31 20:58:57 openvpn 26641 VERIFY WARNING: depth=2, unable to get certificate CRL: C=US, O=Internet Security Research Group, CN=ISRG Root X1
Jan 31 20:58:57 openvpn 26641 VERIFY WARNING: depth=1, unable to get certificate CRL: C=US, O=Let's Encrypt, CN=R3
Jan 31 20:58:57 openvpn 26641 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=island-school.us
Jan 31 20:58:57 openvpn 26641 TLS: Initial packet from [AF_INET]185.94.188.148:8041, sid=e147d894 f36192da
Jan 31 20:58:57 openvpn 26641 UDPv4 link remote: [AF_INET]185.94.188.148:8041
Jan 31 20:58:57 openvpn 26641 UDPv4 link local (bound): [AF_INET]10.0.0.8:0
Jan 31 20:58:57 openvpn 26641 Socket Buffers: R=[42080->42080] S=[57344->57344]
Jan 31 20:58:57 openvpn 26641 TCP/UDP: Preserving recently used remote address: [AF_INET]185.94.188.148:8041
Jan 31 20:58:57 openvpn 26641 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-server'
Jan 31 20:58:57 openvpn 26641 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-client'
Jan 31 20:58:57 openvpn 26641 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
Jan 31 20:58:57 openvpn 26641 Control Channel MTU parms [ L:1621 D:1212 EF:38 EB:0 ET:0 EL:3 ]
Jan 31 20:58:57 openvpn 26641 Re-using SSL/TLS context
Jan 31 20:58:57 openvpn 26641 NOTE: the current --script-security setting may allow this configuration to call user-defined scriptsBelow added some screenshots from the firewall and NAT rules and the VPN settings.
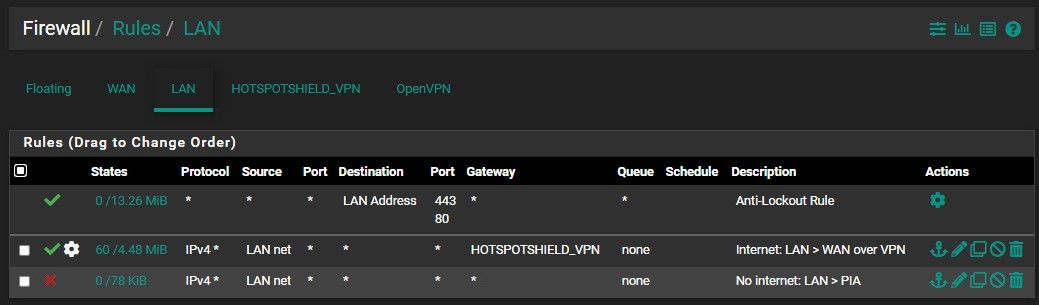
Firewall rules
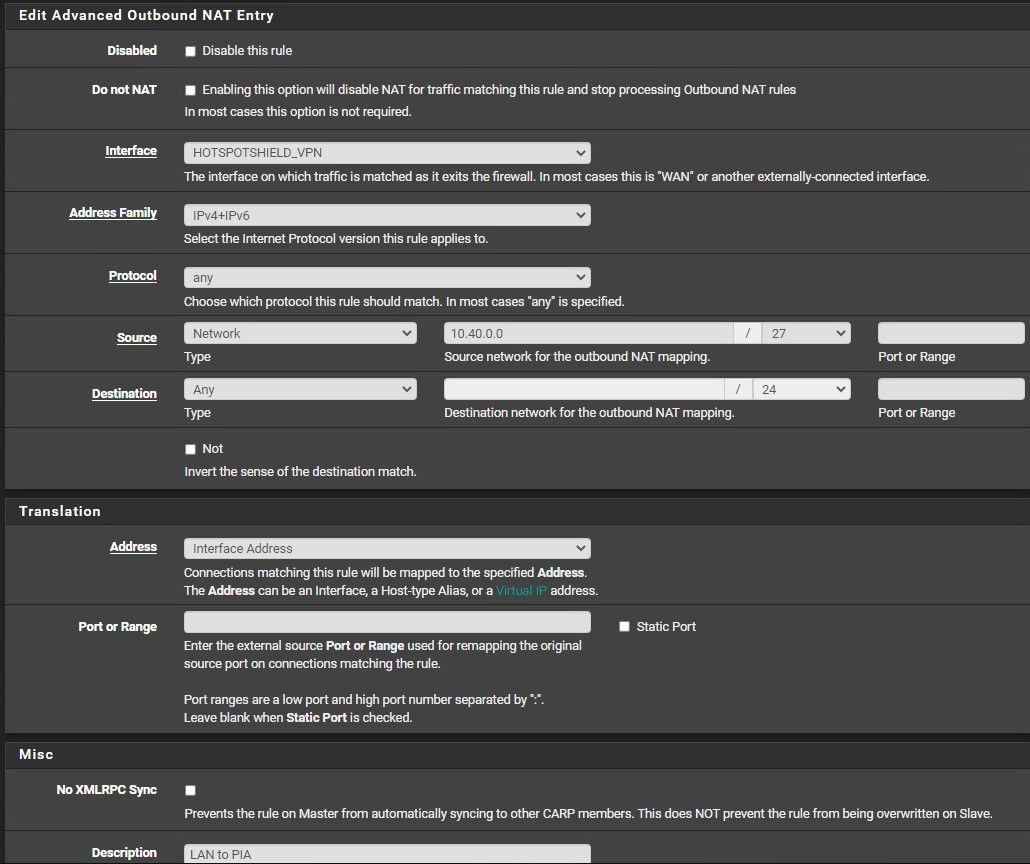
NAT rule
VPN config
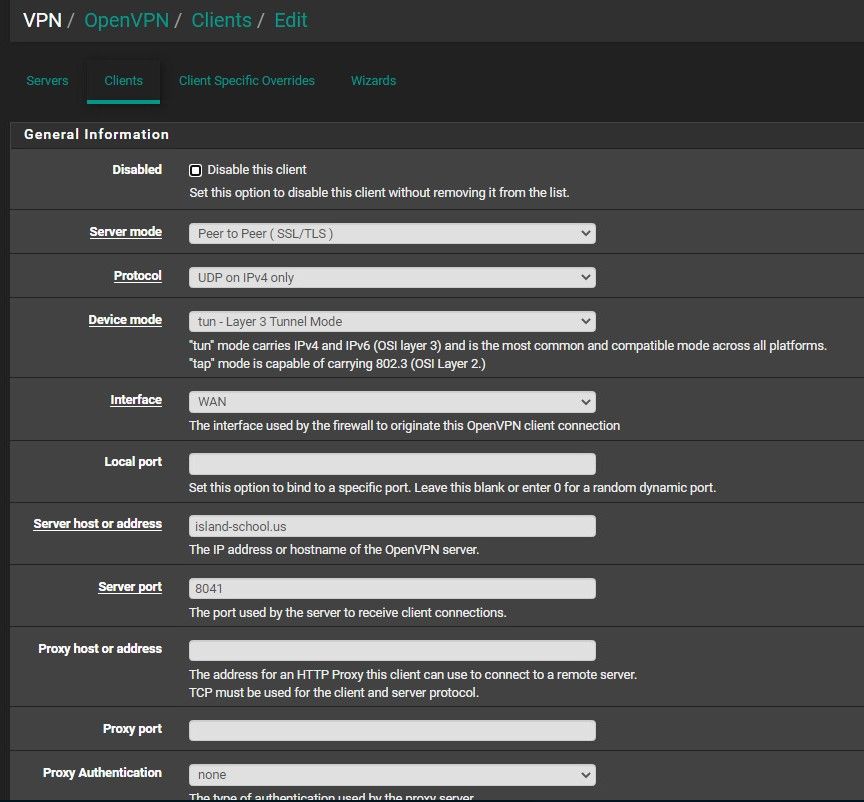
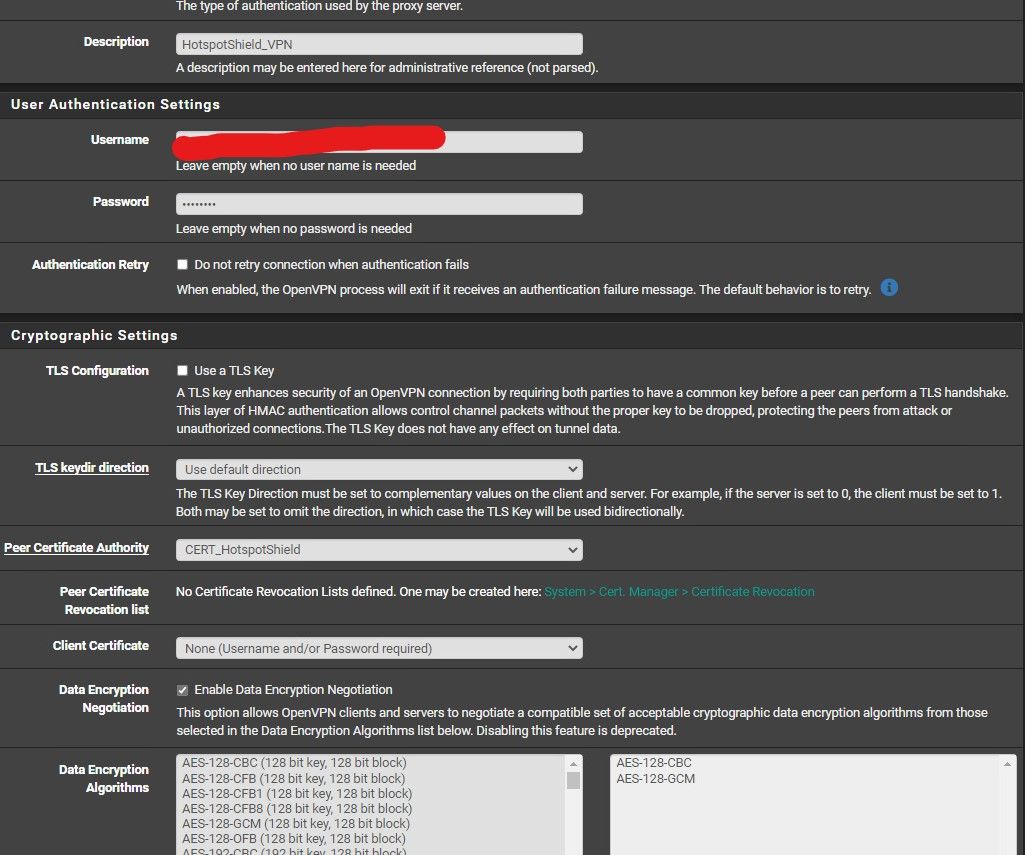
Offcourse I've checked much topics here at Netgate and other fora but I didn't found the solution.
-
@gerrit700
The log should show some more lines of the connection establishment.What is the goal of this VPN? Accessing the remote site or passing the upstream traffic over it?
What do you intend with the stated advanced options. "persist-key" and "persist-tun" are used by default anyway. Why "reneg-sec 0"?
Consider that you policy routing LAN rule does pass any traffic from LAN devices to the OpenVPN server. Hence accessing local addresses is not possible with this. Consider that if the LAN devices are set to use a local DNS, they will fail.
-
Hi @viragomann ,
Thanks for your answer.
"The log should show some more lines of the connection establishment."
I've the verbosity level at 4 so if you want more logging, I can set it higher and post that here.
What is the goal of this VPN? Accessing the remote site or passing the upstream traffic over it?
Passing the upstream traffic. It will be a test network for scambaiting and I want to prevent that they can see my own IP-address when they get me.
What do you intend with the stated advanced options. "persist-key" and "persist-tun" are used by default anyway. Why "reneg-sec 0"?
I've watched this video from NetworkChuck and here he is instructing how you set it up with PrivateInternetAccess. He copies this info from the .ovpn file into the VPN settings.
https://youtu.be/lUzSsX4T4WQ?t=1282I tried it also without these custom options but no luck.
Consider that you policy routing LAN rule does pass any traffic from LAN devices to the OpenVPN server. Hence accessing local addresses is not possible with this. Consider that if the LAN devices are set to use a local DNS, they will fail.
The local addresses can connect to eachother because they're in the same network. Only through internet the traffic goes through the VPN.
In pfSense I've set de DNS tot 1.1.1.1 and 8.8.8.8 and for the clients 10.40.0.1, pfSense itself.
-
Hi @viragomann ,
I've just removed the custom options but still no luck.
-
@gerrit700
No, don't need a higher log level. But the link connection seems not to have finished in the shown section.Doesn't the server require a client cert?
In pfSense I've set de DNS tot 1.1.1.1 and 8.8.8.8 and for the clients 10.40.0.1, pfSense itself.
So when the connection is up, the LAN devices won't be able to resolve host names.
-
the directions say to use 256cbc
you do not have that added to be utilizedcompression. you may have to try some of the less secure methods... they are not clear on that...
-
Doesn't the server require a client cert?
I don't know, I cannot find some usable info from HotspotShield. They provide only a .opvn file.
So when the connection is up, the LAN devices won't be able to resolve host names.
Okay, so I need to override 10.40.0.1 to 1.1.1.1 and 8.8.8.8 in de DHCP scope so the clients get these DNS servers?
-
Hi @bcruze,
the directions say to use 256cbc
you do not have that added to be utilizedI've added 256cbc
New logging after this change:
Feb 1 14:09:13 openvpn 38894 Restart pause, 40 second(s)
Feb 1 14:09:13 openvpn 38894 SIGUSR1[soft,ping-restart] received, process restarting
Feb 1 14:09:13 openvpn 38894 TCP/UDP: Closing socket
Feb 1 14:09:13 openvpn 38894 [island-school.us] Inactivity timeout (--ping-restart), restarting
Feb 1 14:08:44 openvpn 38894 UDPv4 WRITE [592] to [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=578
Feb 1 14:08:28 openvpn 38894 UDPv4 WRITE [592] to [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=578
Feb 1 14:08:19 openvpn 38894 UDPv4 WRITE [592] to [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=578
Feb 1 14:08:15 openvpn 38894 UDPv4 WRITE [592] to [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=578
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [604] to [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ 5 ] pid=2 DATA len=578
Feb 1 14:08:13 openvpn 38894 UDPv4 READ [19] from [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=5 DATA len=5
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [22] to [AF_INET]185.94.188.150:8041: P_ACK_V1 kid=0 [ 4 ]
Feb 1 14:08:13 openvpn 38894 VERIFY OK: depth=0, CN=island-school.us
Feb 1 14:08:13 openvpn 38894 VERIFY EKU OK
Feb 1 14:08:13 openvpn 38894 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Feb 1 14:08:13 openvpn 38894 Validating certificate extended key usage
Feb 1 14:08:13 openvpn 38894 VERIFY KU OK
Feb 1 14:08:13 openvpn 38894 VERIFY OK: depth=1, C=US, O=Let's Encrypt, CN=R3
Feb 1 14:08:13 openvpn 38894 VERIFY OK: depth=2, C=US, O=Internet Security Research Group, CN=ISRG Root X1
Feb 1 14:08:13 openvpn 38894 VERIFY WARNING: depth=2, unable to get certificate CRL: C=US, O=Internet Security Research Group, CN=ISRG Root X1
Feb 1 14:08:13 openvpn 38894 VERIFY WARNING: depth=1, unable to get certificate CRL: C=US, O=Let's Encrypt, CN=R3
Feb 1 14:08:13 openvpn 38894 VERIFY WARNING: depth=0, unable to get certificate CRL: CN=island-school.us
Feb 1 14:08:13 openvpn 38894 UDPv4 READ [1188] from [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=4 DATA len=1174
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [22] to [AF_INET]185.94.188.150:8041: P_ACK_V1 kid=0 [ 3 ]
Feb 1 14:08:13 openvpn 38894 UDPv4 READ [1188] from [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=3 DATA len=1174
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [22] to [AF_INET]185.94.188.150:8041: P_ACK_V1 kid=0 [ 2 ]
Feb 1 14:08:13 openvpn 38894 UDPv4 READ [1188] from [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=2 DATA len=1174
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [22] to [AF_INET]185.94.188.150:8041: P_ACK_V1 kid=0 [ 1 ]
Feb 1 14:08:13 openvpn 38894 UDPv4 READ [1200] from [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ 1 ] pid=1 DATA len=1174
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [291] to [AF_INET]185.94.188.150:8041: P_CONTROL_V1 kid=0 [ ] pid=1 DATA len=277
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [22] to [AF_INET]185.94.188.150:8041: P_ACK_V1 kid=0 [ 0 ]
Feb 1 14:08:13 openvpn 38894 TLS: Initial packet from [AF_INET]185.94.188.150:8041, sid=b9ae7b7b 1188b486
Feb 1 14:08:13 openvpn 38894 UDPv4 READ [26] from [AF_INET]185.94.188.150:8041: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ 0 ] pid=0 DATA len=0
Feb 1 14:08:13 openvpn 38894 UDPv4 WRITE [14] to [AF_INET]185.94.188.150:8041: P_CONTROL_HARD_RESET_CLIENT_V2 kid=0 [ ] pid=0 DATA len=0
Feb 1 14:08:13 openvpn 38894 UDPv4 link remote: [AF_INET]185.94.188.150:8041
Feb 1 14:08:13 openvpn 38894 UDPv4 link local (bound): [AF_INET]10.0.0.8:0
Feb 1 14:08:13 openvpn 38894 Socket Buffers: R=[42080->42080] S=[57344->57344]
Feb 1 14:08:13 openvpn 38894 TCP/UDP: Preserving recently used remote address: [AF_INET]185.94.188.150:8041
Feb 1 14:08:13 openvpn 38894 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-server'
Feb 1 14:08:13 openvpn 38894 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-client'
Feb 1 14:08:13 openvpn 38894 Data Channel MTU parms [ L:1621 D:1450 EF:121 EB:406 ET:0 EL:3 ]
Feb 1 14:08:13 openvpn 38894 Control Channel MTU parms [ L:1621 D:1212 EF:38 EB:0 ET:0 EL:3 ]
Feb 1 14:08:13 openvpn 38894 Re-using SSL/TLS context
Feb 1 14:08:13 openvpn 38894 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts -
@gerrit700 said in Trying to setup OpenVPN to HotspotShield but won't connect:
They provide only a .opvn file.
You should find all settings you need in this file.
If the server require a client cert, there will be a link in the file. -
Hi @viragomann,
You're my hero! I've added the certificate to the certificate manager and selected this certificate in de VPN config and that was the solution.
Thank for your help :-)