Using Haproxy to Redirects Calls to FreePBX
-
I am new to Haproxy and want to use this package to redirect voip calls securely to FreePBX server. The goal is to make security airtight. So, I have been using pfSense 2.7-devel and Haproxy-devel on a VM to be familiar with the package and develop a configuration. I found that I cannot incorporate the test domain certificate because it would bind the actual WAN. So, I'll share what I draft screen shots to get feedback before I move to configuring the actual production box. Note: I already use a different port for webcconfig interface long before so no problem when ready to setup Haproxy on the production box.
So, first is the certificate for the fictitious domain: bignolli.net to show this step was completed and the cron job checked.
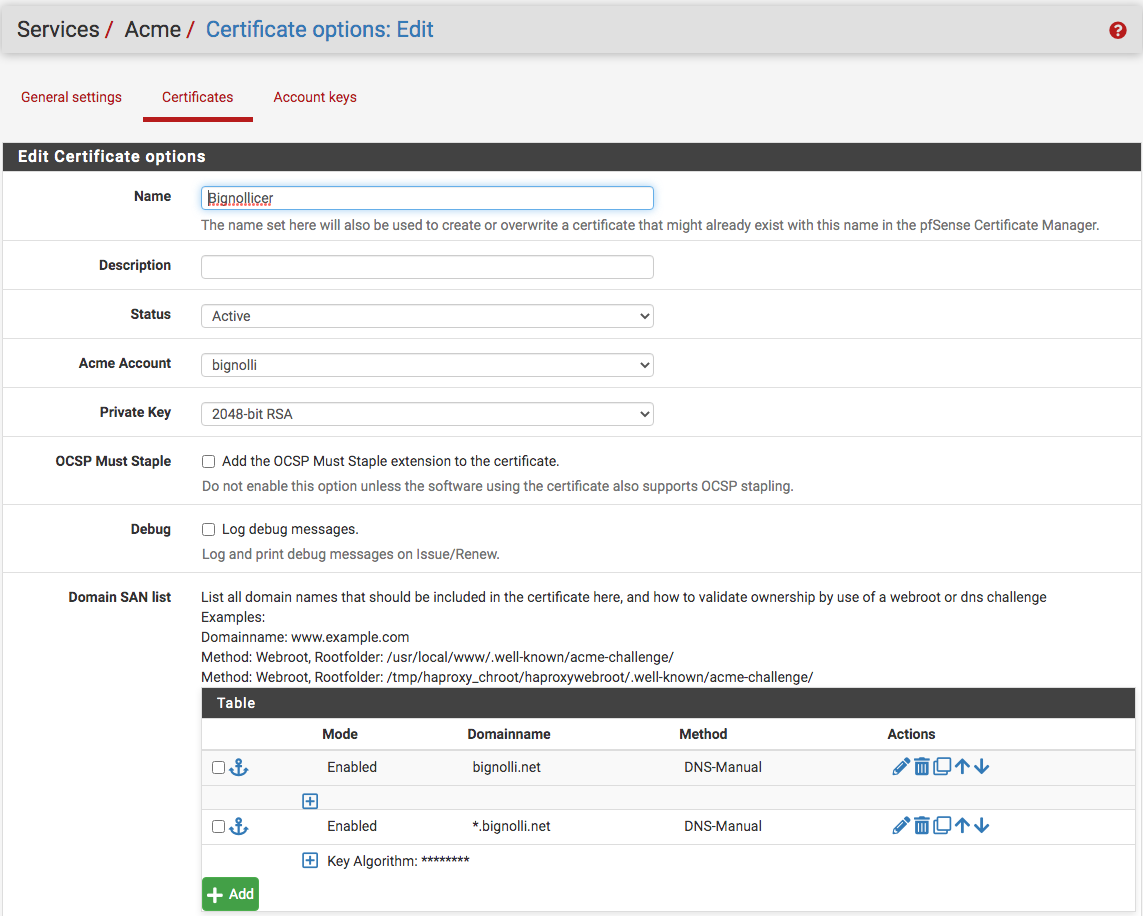
Then, launch and enable the package, then create the backend.
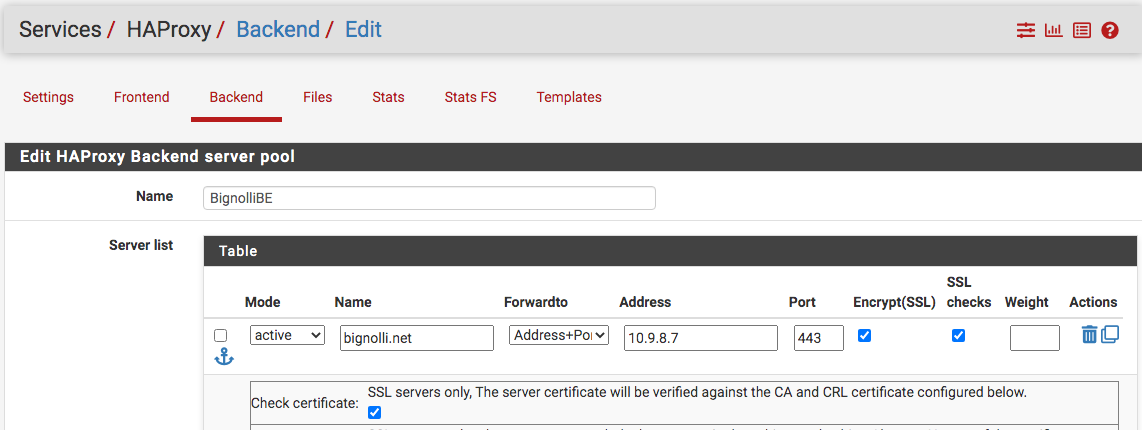
Then, create the frontend...question here: could I have created just two frontends with the first one the redirect?
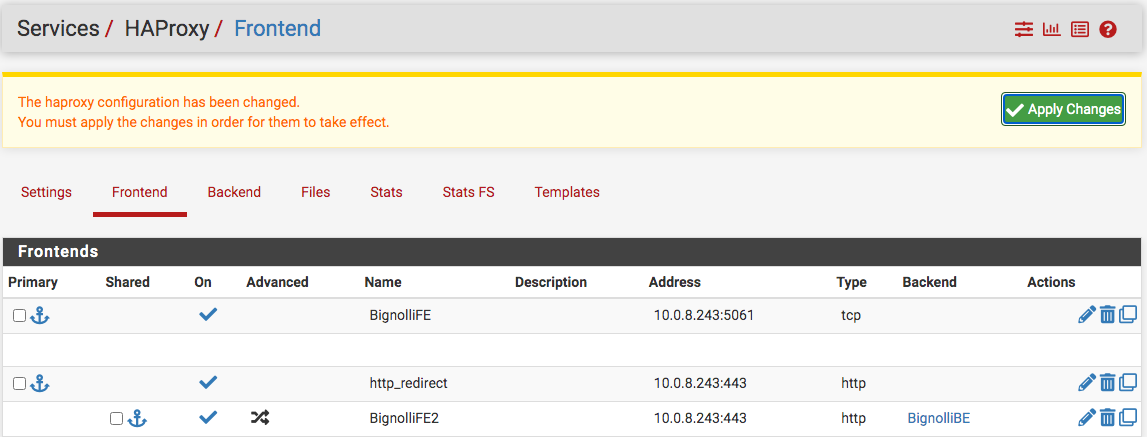
First frontend...
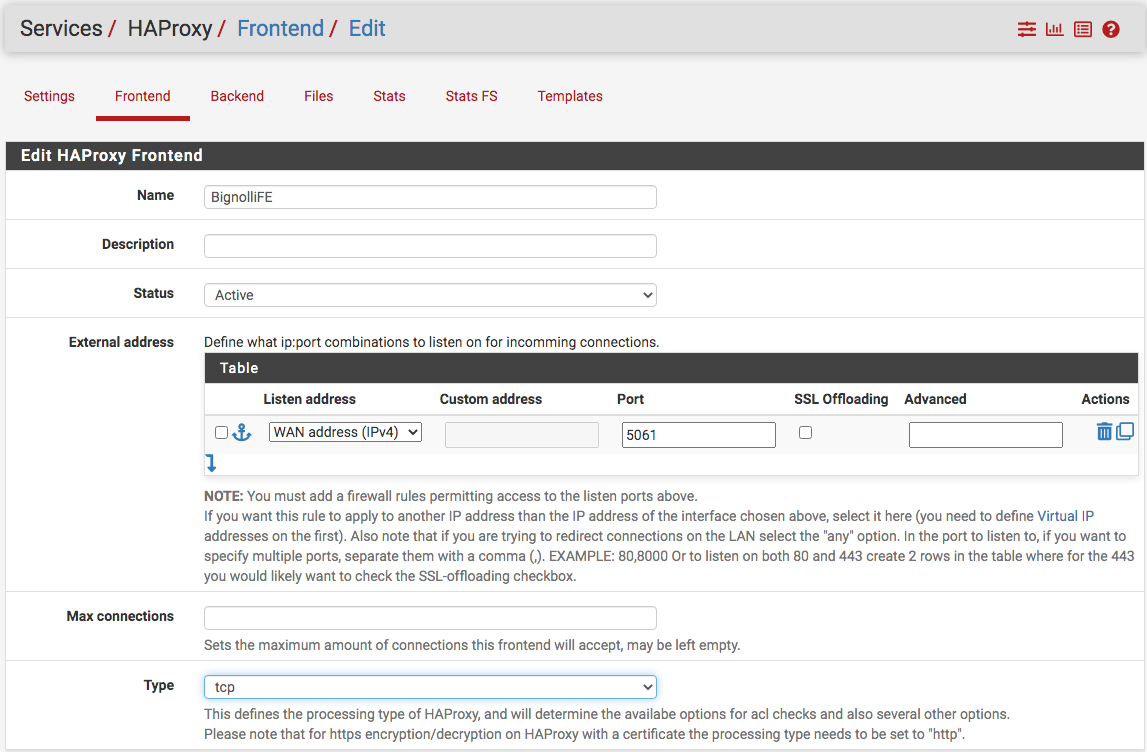
Second frontend...this is the redirect from WAN with an action and a certificate in the real production mode...cannot include the certificate here since pfSense is a VM.
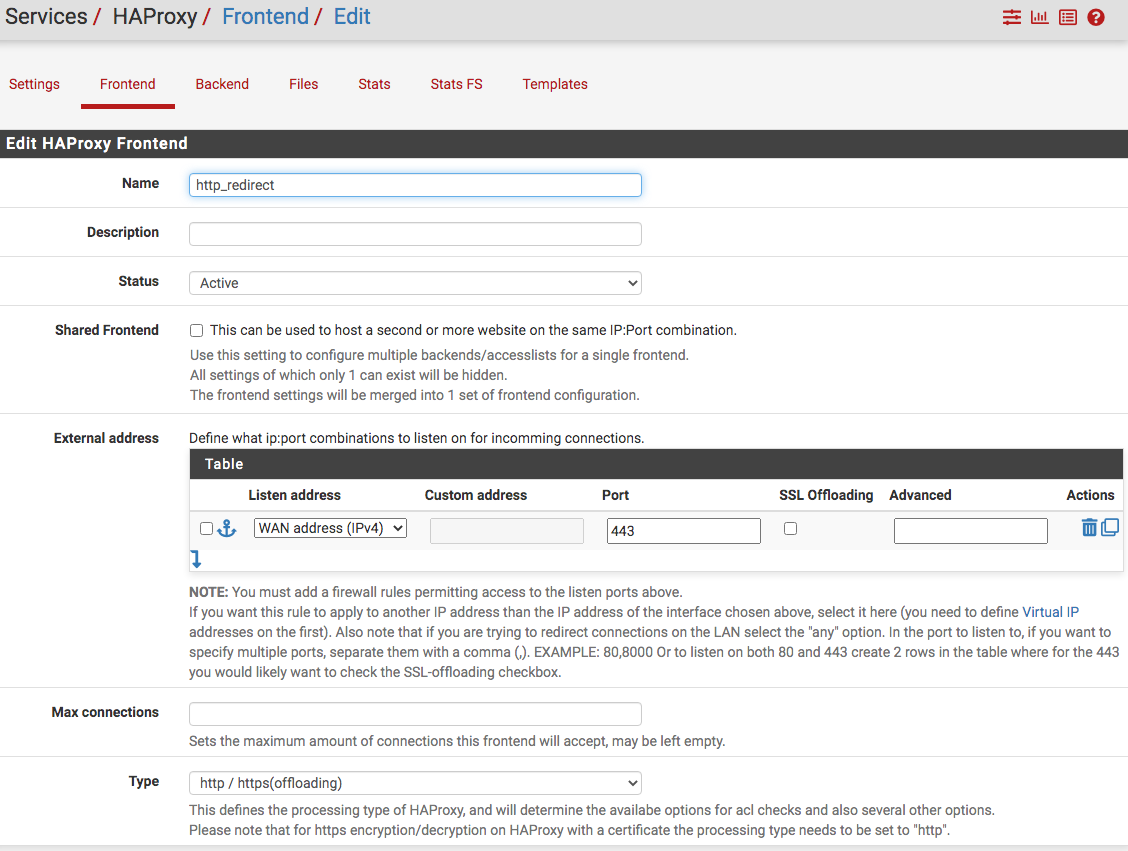
Followed by the action...
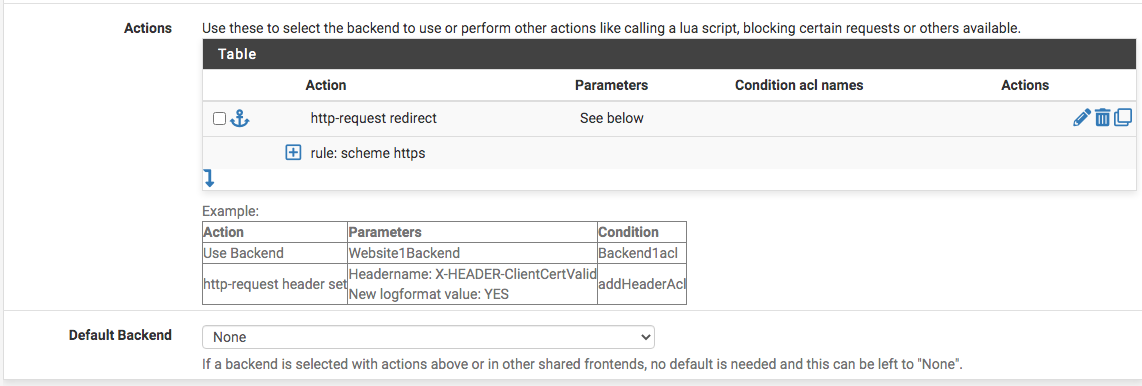
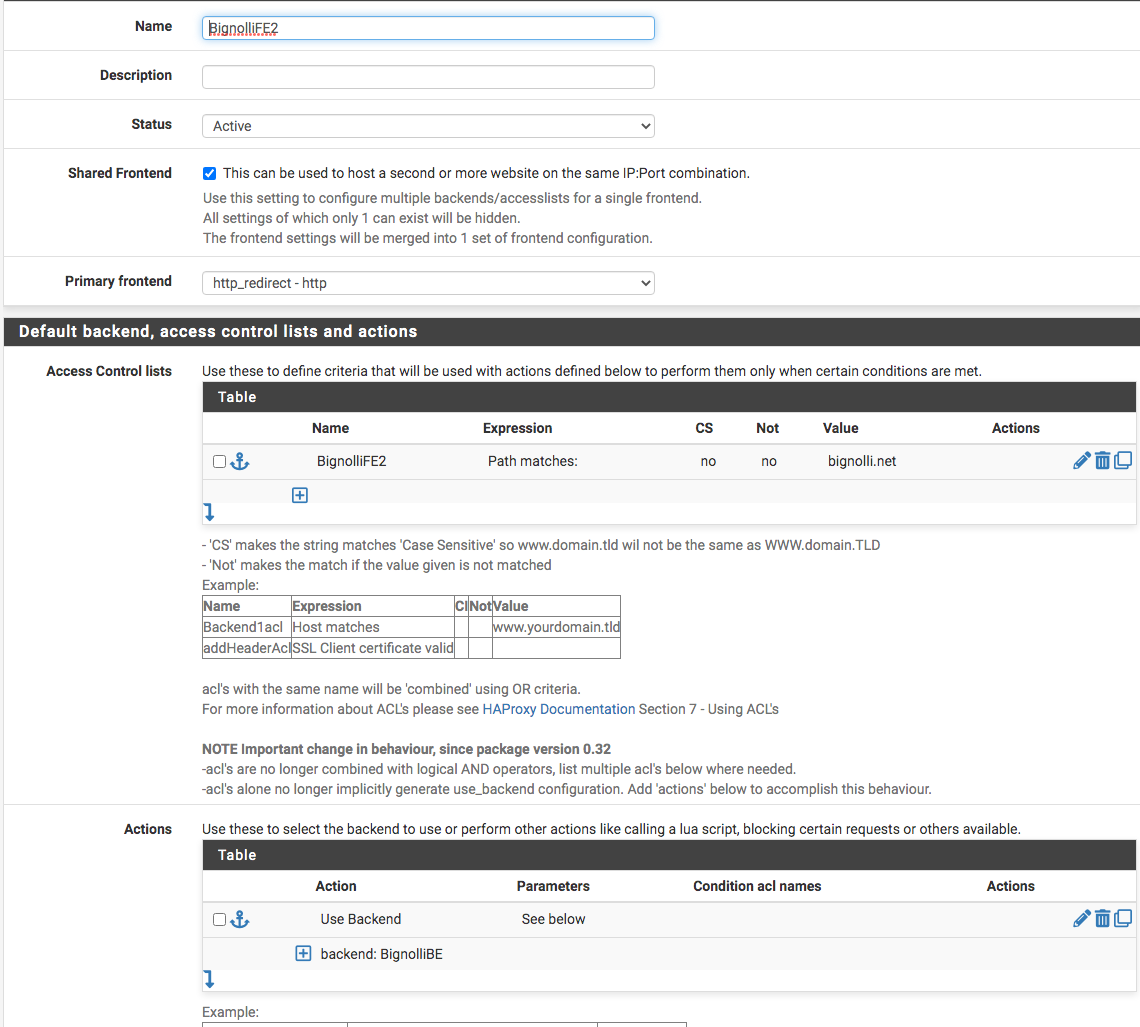
Then, the final frontend that ties the two above...
Now, for the whole Haproxy setup to work, I would need to include firewall port forward to forward calls to Haproxy so phone calls can be routed to the FreePBX server...
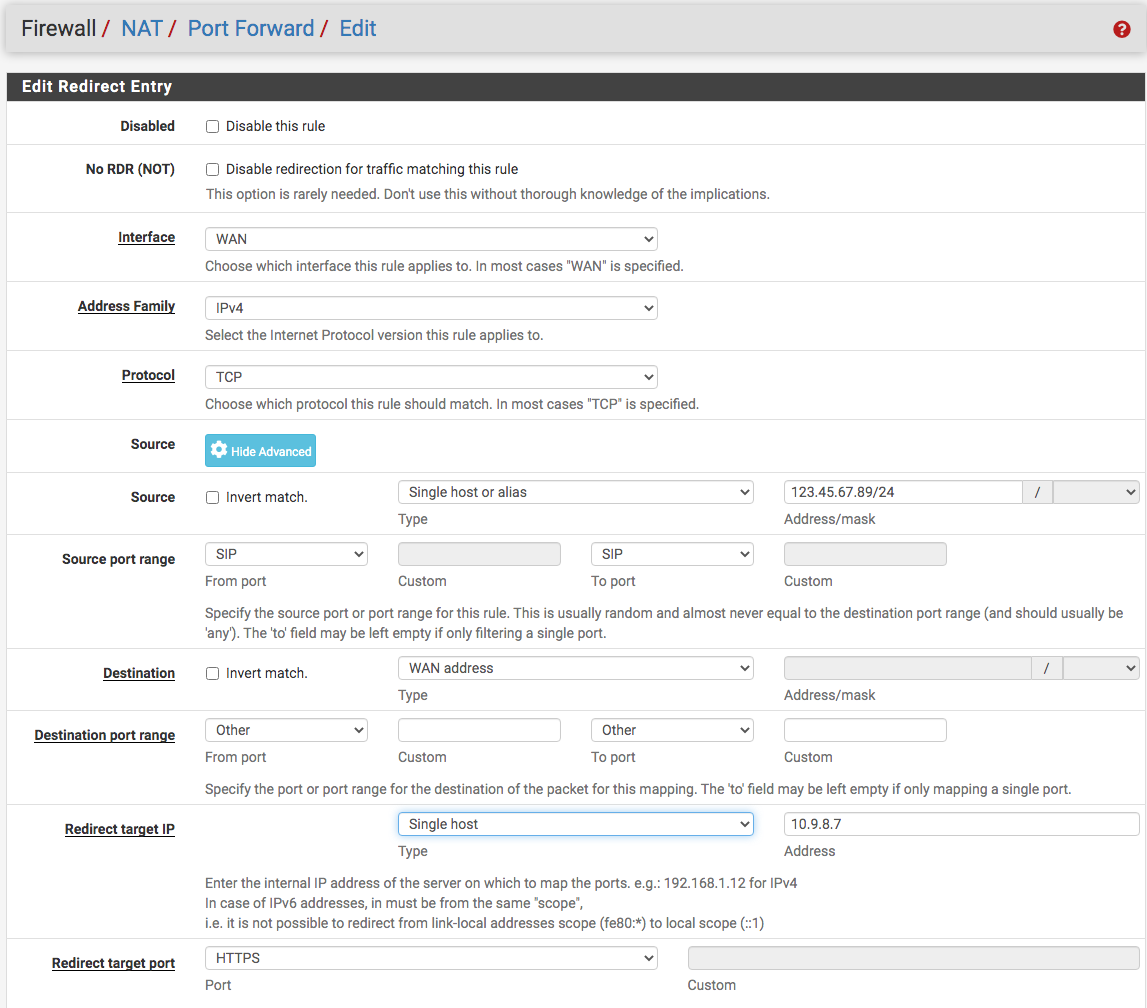
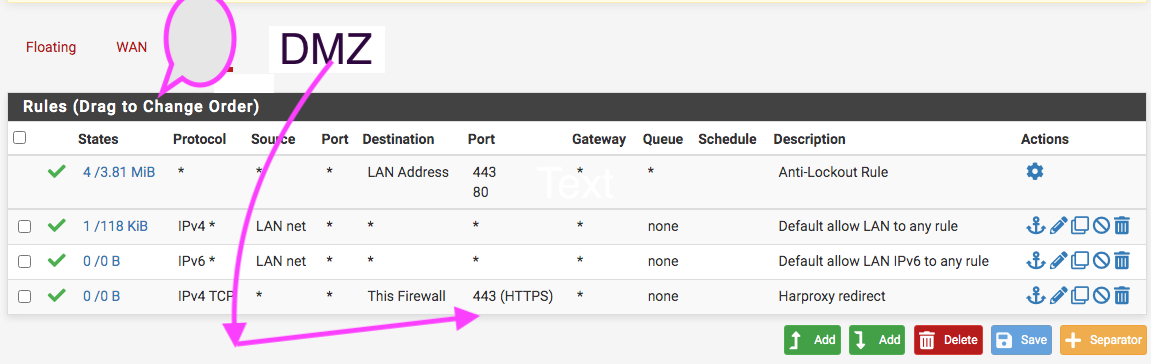
Would this all work? How can I improve it...make it simpler? The idea I am seeking to implement is to use Haproxy as a secure tunnel to FreePBX allowing less chances of observation of the DMZ by making it airtight.
-
All the above isn't what it should be and that was a case of watching misinformation on YouTube, yet I found the answer on the said YouTube through Lawrence System's video: Haproxy Troubleshooting -- https://www.youtube.com/watch?v=fLV3kF3QIws
For instance, one needs only one frontend and one backend for each service in Harproxy...also, one needs the interface Haproxy will be listening on, in my case the DMZ (see image below). Also, one doesn't need to port forward except as in my case since the calls are coming on port 5061 and Haproxy will be listening on port 443. One really doesn't another firewall rule as well.
It would be cool if Netgate-pfSense's Hangout can do a video on this since home office had become the new normal and having a server(s) as a part of one's network.
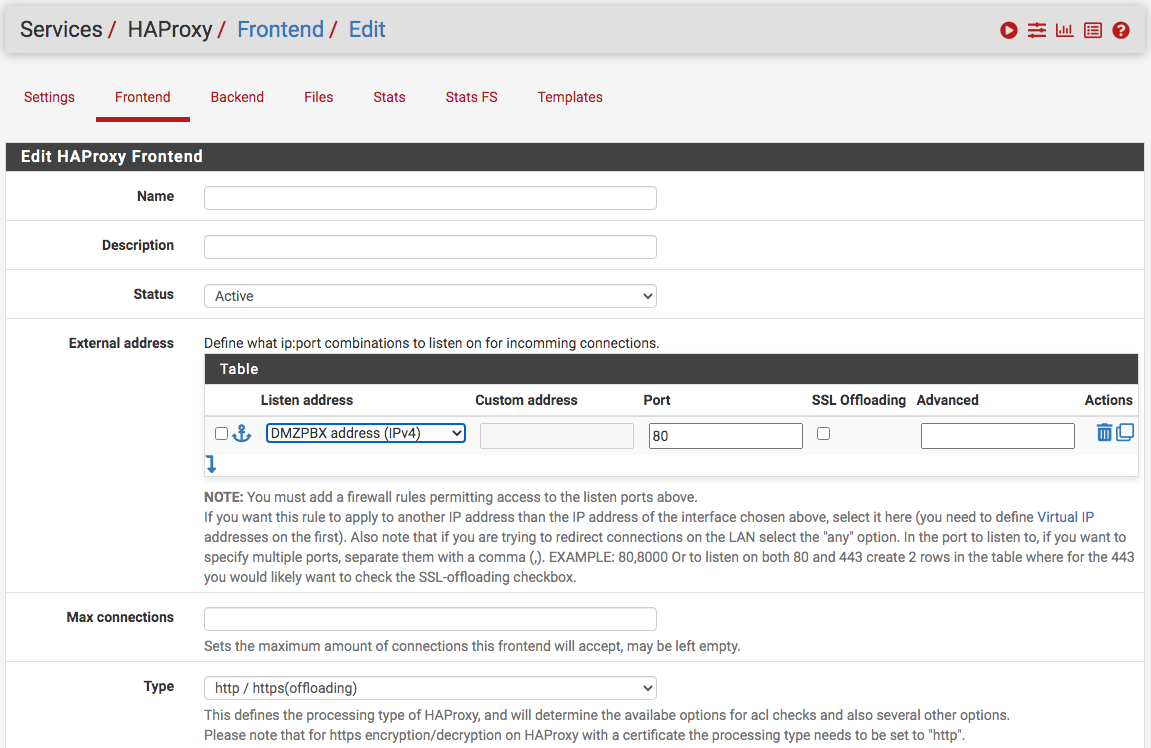
-
@nollipfsense Freepbx is an asterisk server application manager.
asterisk is using sip which is by default unencrypted and udp, typically on port 5060.As far as I know, haproxy doesn't support udp, and using tcp for voip isn't exactly recommended.
What are you trying to accomplish?
-
@netblues Thanks for responding...what I am seeking is to use Haproxy's reverse proxy as a secure tunnel to redirect calls to a FQDN FreePBX server on a DMZ so as to prevent snooping around on the DMZ thus making it airtight...makes sense?
-
@nollipfsense Yes, you've said that in the first place.
How about rtp/udp?
In general what you are looking for is an sbc, not haproxy.
-
@netblues Thanks for the continued conversation. As this thread I am just going through points out (see link below), in this 21st century an SBC is passe despite some still use. https://forum.netgate.com/topic/151239/is-pfsense-a-sbc-or-is-there-a-package-for-sbc/14?loggedin=true
A member on the FreePBX forum had shared the idea of using Haproxy but stated that this method is a bit disruptive in terms of other users using it. It immediately clicked in my mind, but I needed to learn how to set up Haproxy to give the idea a try. Of course, that member wants me to help myself like most forum. I had setup FreePBX in the pass on a DMZ but had problems receiving inbound calls and the SIP Trunk provider claimed it was my firewall. Shortly thereafter, I had to suspend the project, then changed the hardware I had used to a new pfSense box.
-
@nollipfsense said in Using Haproxy to Redirects Calls to FreePBX:
As this thread I am just going through points out (see link below), in this 21st century an SBC is passe despite some still use. https://forum.netgate.com/topic/151239/is-pfsense-a-sbc-or-is-there-a-package-for-sbc/14?loggedin=true
What is said on this thread is completely wrong.
A firewall is not an sbc, as much as a firewall is not a waf.In the particular link port forwards are recommended which are neither needed nor recommended.
pfsense doesn't need this for sip trunking.Additionally, in the post you are referring, the op suggedts limiting the source to the ip's of the sip trunk provider.
Good luck doing this with multiple users connecting from everywhere.
So, no an sbc is still needed in the 21 st century.
And no, haproxy can't do udp, so it is irrelevant. -
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
And no, haproxy can't do udp, so it is irrelevant.
It wouldn't forward the UDP through the port 443 to a FQDN? I am also waiting to hear from that member on FreePBX to confirm also...I saw that I had participated on the thread mentioned earlier.
-
@nollipfsense Using pfsense as a firewall for normal sip traffic is fine and works well.
As for haproxy and udp. google is your friend.
Have it here from the haproxy github.
As official as it getshttps://github.com/haproxy/haproxy/issues/62
-
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
https://github.com/haproxy/haproxy/issues/62
I just read the thread and it doesn't make it very clear on my use case. I will not carry UDP traffic through Haproxy so to speak; it's TCP/TLS that will encapsulates the UDP traffic and only doing so on inbound calls to the voip server. From what the member on FreePBX said of using Haproxy and why, I doubt he's misleading me. Despite my searching the web and YouTube, I have not found anyone directly mentioning this use case; however, I saw one by accident in their reverse proxy demo (in back-end drop down, you can see PBX for a few second). So, I believe it's possible; it's just not popular yet. Here the link to that video: https://www.youtube.com/watch?v=7WiZ1i2u-Lc
-
Tls yes, and srtp too.
But tcp? for sip/voip?It can be done, but is certainly NOT a common/recommended way
-
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
Tls yes, and srtp too.
But tcp? for sip/voip?It can be done, but is certainly NOT a common/recommended way
So, therefore, I would need an ACL like Server name Indication like in the pic below...how would I take care of the SRTP part? Would it all travels with TLS? Port 443? Two folks on FreePBX had mentioned SNI and TLS; however, only one of the two mentioned using Haproxy and claimed it would solve almost all security issues...but then, I needed to do the homework.
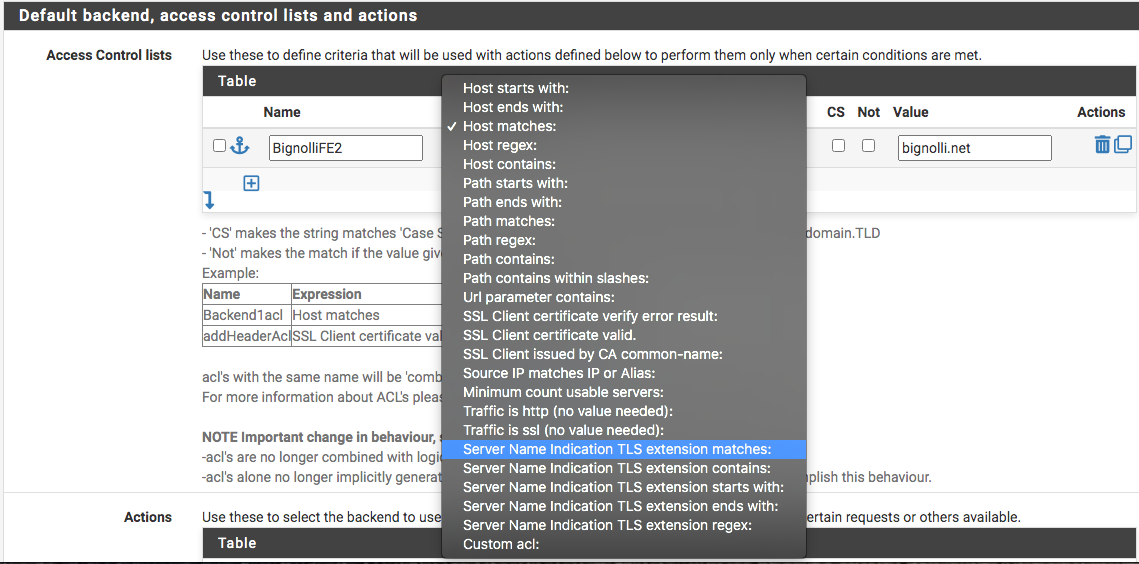
Thanks Netblues for help me doing my homework indirectly. From TLS Wiki: https://en.wikipedia.org/wiki/Transport_Layer_Security
Transport Layer Security (TLS), the successor of the now-deprecated Secure Sockets Layer (SSL), is a cryptographic protocol designed to provide communications security over a computer network. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible.The TLS protocol aims primarily to provide cryptography, including privacy (confidentiality), integrity, and authenticity through the use of certificates, between two or more communicating computer applications. It runs in the application layer and is itself composed of two layers: the TLS record and the TLS handshake protocols.
So, in essence Haproxy's reverse proxy would be acting as well as vouching for each calls before present to the voip server limiting the exposure between the DMZ and the voip server (FreePBX).
-
@nollipfsense Please finish your homework.
sni is related to https and has nothing to do with srtp or tls per se.As you already said, tls works at the application layer.
Haproxy works at the transport layer
in transport layer we have tcp or udp or icmp
( there are more but these are the most known ones)
tls can run on top of udp or tcp
same goes for srtp
( its the voice we need to protect in the end , and voice in sip IS rtp)
Unfortunately srtp in voip uses udp and since haproxy cannot handle udp, you need something else to handle UDP packets.
The industry standard for this is an sbc.
Can you spell kamailio? -
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
@nollipfsense Please finish your homework.
sni is related to https and has nothing to do with srtp or tls per se.As you already said, tls works at the application layer.
Haproxy works at the transport layer
in transport layer we have tcp or udp or icmp
( there are more but these are the most known ones)
tls can run on top of udp or tcp
same goes for srtp
( its the voice we need to protect in the end , and voice in sip IS rtp)
Unfortunately srtp in voip uses udp and since haproxy cannot handle udp, you need something else to handle UDP packets.
The industry standard for this is an sbc.
Can you spell kamailio?Kamaillo seems would be taking me in another direction though, and I have already committed to FreePBX since I invested in a Lenovo M93 SFF 250SSD 16GB RAM and Htek enterprise phones admittedly overkill for my home office-lab with at most three extensions.
You seem to have intimate knowledge of voip setup; I must admit. I am waiting for the member of FreePBX forum to respond. I have decided to try Voip.MS SIP Trunk provider and most likely contact them tomorrow or over the weekend.
-
@netblues Okay, I got a reply and it seems that the member on FreePBX doesn't use UDP on or through Haproxy...I am pressing for details as it seems that member use SNI to validate SIP Trunk provider through Haproxy with the voip server (FreePBX) then, route the media (voice) regularly and separately. I am seeing why the member said the method is disruptive and I am intrigued despite the feeding one line at a time
-
@nollipfsense Again, an sbc won't replace freepbx
And no, you don't need an sbc for your home office.Freepbx will work great with any decent sip trunk provider.
You don't need to open any inbound ports, and don't need any plugins
Obviously you don't need redundancy with two fbx hosts too.
As for security you can always put freepbx in a dmz and filter traffic to the phones as needed.You will have to trust your sip provider. If the setup provides srtp, then you will have to go by the security standards of the provider.
Which brings us to the next level. Do you have external voip users?
Do they use sip mobile phones to connect to your home office?
Do they also need to receive incoming calls ?As for the hardware, its way more than you need.
2 cores and 3 gigs of ram is more than enough for fpbx
I would put a hypervisor and run pfsense on the same box too, -
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
As for the hardware, its way more than you need.
2 cores and 3 gigs of ram is more than enough for fpbx
I would put a hypervisor and run pfsense on the same box too,I know its overkill but I am kind of like that. The latest Raspberry Pi all dressed up for voip would have been around the same cost of what I got the Lenovo with 8GB, and no hard-drive for $60 and I added the SSD as well as the other 8GB RAM I already had. At first, I had put ESXI on with FreePBX 14 and Ubuntu server but last weekend I removed Ubuntu and ESXI and reinstalled FreePBX 16 bare metal. I already have pfSense on a Lenovo M93 with 32GB RAM...another overkill as expected of me. I have two Mac Mini servers internally.
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
As for security you can always put freepbx in a dmz and filter traffic to the phones as needed.
I already have FreePBX in a DMZ...I was just looking to tighten security before getting a SIP Trunk provider.
I also heard from the member of FreePBX forum who explain that his setup is a separate box that in not behind a firewall and NAT as in my case. Just for fun and experimenting, I see what exploring a setup with HAproxy does after checking with Voip.ms...seems their system would cooperate since they're using port 5004 srtp based on my reading. I also in my research I found this voip paper: https://www.govinfo.gov/content/pkg/GOVPUB-C13-3cee6719f04b98ad3d753a966b662c51/pdf/GOVPUB-C13-3cee6719f04b98ad3d753a966b662c51.pdf
-
@nollipfsense I wouldn't be bothered with anything being written in 2005 for todays systems, unless it is for historical reasons.
As for voip.ms, yes, they offer tls for sip, (over tcp) which would work with haproxy, as far as signaling is concerned, but when the call start it would be srtp over udp again, and you calls will be audioless.
There is 0 benefit into using haproxy in this scenario.
Srtp and sip/tls will make your calls secure on the Internet.
And you don't have to open ANY ports to the internet too.
freepbx will be originating all registration requests
If voip,ms decides to attack you via sip registration replies, it can still do it.
Haproxy will never be used, since there are NO incoming connectionsIf you really want to be paranoid, then use and sbc,
Its the only thing in your setup that can add an extra level of isolation at
the sip level. -
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
I wouldn't be bothered with anything being written in 2005 for todays systems, unless it is for historical reasons.
It was more for how we got were we are today.
@netblues said in Using Haproxy to Redirects Calls to FreePBX:
There is 0 benefit into using haproxy in this scenario.
Srtp and sip/tls will make your calls secure on the Internet.Well, I signed up with Voip.ms today (demo) and was looking through the various setting without configuring anything and it appears you maybe correct that incorporating HAproxy, as rosy as the learning experience was, as well as my burning desire to experiment with the package, may actually prove counterproductive. Still, it wouldn't hurt to speak with Voip.ms support on the matter before finally giving up. I will however run Snort IDS on the DMZ.
-
@nollipfsense Making srtp to work properly isn't always straight forward.
But its certainly worth investigating.Are you hosting anything? Any open ports to the Internet? Why do you need a dmz in a home office scenario?