Issues with Subnet behind UDM Pro
-
@misinthe, it's just as i thought.
-
@viragomann @Silence Man, doing all this testing messed my pfSense up, now it won't boot up, so I just deleted the VM, I don't know if I'll rebuild it or if I'll just remove it from the equation and just add a piHole VM to the network.
-
@misinthe There are many ways to solve your problem here.
Now my suggestion is the following:
in my case I create the vlan in Pfsense and only use the UDM PRO FOR SWICTH
In this way when connecting via openvpn to your pfsense and everything will be Ok.
-If you decide to continue doing routing in pfsense and Routing in DM PRO then the suggestion is to start cleaning the openvpn configuration is wrong and static routes in pfsense.
rule in wan for your UDM PRO and with that everything should work without problem.
-
@misinthe said in Issues with Subnet behind UDM Pro:
Man, doing all this testing messed my pfSense up, now it won't boot up, so I just deleted the VM, I don't know if I'll rebuild it or if I'll just remove it from the equation and just add a piHole VM to the network.
wtf, So if I delete his pfsense how does he have access to the internet?
what is the ip of your computer?
-
@silence said in Issues with Subnet behind UDM Pro:
@misinthe said in Issues with Subnet behind UDM Pro:
Man, doing all this testing messed my pfSense up, now it won't boot up, so I just deleted the VM, I don't know if I'll rebuild it or if I'll just remove it from the equation and just add a piHole VM to the network.
wtf, So if I delete his pfsense how does he have access to the internet?
what is the ip of your computer?
I just connected my ISP directly to the WAN port of the UDM Pro, the pfSense was acting mainly just for pfBlocker, DHCP is controlled by the UDMP and DNS is controlled by my Domain Controller, I only had to redirect that Domain Controller to the UDMP and that's it.
-
@misinthe
I'm sorry, I have no idea what you could have done wrong here.
I didn't told you to do any changes on pfSense apart from the route a week ago.
But now we got news, it was a VM. Would maybe worth to mention.Anyway your setup seem quite simple. So no idea, why this should not work, just some networking. Router should be able to do this.
-
@viragomann It's okay, I don't know why it being a VM would've changed anything? And what I did was shut it down to give it 2 more cores and 4GB more of RAM because I noticed it was about to be maxed, then it didn't come back up. Like I said, my LAN is all within the UDM Pro, so I'm not too worried about it, the only thing I really lost was pfBlockerNG and the DMZ, but I can create a DMZ network on the UDM Pro pretty easy, and like I said, I can just add a piHole VM to act as the pfBlockerNG .
-
@misinthe said in Issues with Subnet behind UDM Pro:
I don't know why it being a VM would've changed anything?
Because the hypervisor comes into play and may take affect on the networking.
But yes, there should be no need to have 2 firewalls normally, but it should be possible though.
-
@viragomann Well, my VM Host has 3 x 4Ports NIC Cards, so what I did was assign 3 physical ports to the pfSense, one for each WAN, LAN, and Opt1. That way it didn't use the virtual NIC.
-
@misinthe
I see. So the hypervisor should do nothing on the NICs assigned to pfSense VM. -
@viragomann
Right, they're just bridges. Anyways, I guess we can close this for now, I don't know if I'll try again in the future or not. -
@viragomann said in Issues with Subnet behind UDM Pro:
So no idea, why this should not work, just some networking
IT DIDN'T WORK, BECAUSE HE HAD DOUBLE ROUTING UNDER NAT AND DID NOT EVEN EXPLAIN THAT HE USED VM.
LACK OF INFORMATION IS ALWAYS THE CAUSE OF THE PROBLEM.
-
@silence said in Issues with Subnet behind UDM Pro:
@viragomann said in Issues with Subnet behind UDM Pro:
So no idea, why this should not work, just some networking
IT DIDN'T WORK, BECAUSE HE HAD DOUBLE ROUTING UNDER NAT AND DID NOT EVEN EXPLAIN THAT HE USED VM.
LACK OF INFORMATION IS ALWAYS THE CAUSE OF THE PROBLEM.
Why are you yelling? I appreciate everyone's time and effort, like we specified, it being a VM had nothing to do with the issue, so that piece of information didn't matter. And even if it was double NAT, the static routing should've fixed that issue.
-
The one test I don't see mentioned here and what I would have done first is to try to ping the UDM LAN IP from an OpenVPN client or from pfSense using the OpenVPN server IP as source.
That IP (I'd guess it's 10.10.0.1) should always respond as long as firewall rules allow it.
Really in that situation you are using the UDM as a router only, which you would expect to work.
Whether or not pfSense has/had a private WAN IP would only be an issue if it conflicted with one of the internal subnets which is unlikely given their numbering. Since OpenVPN clients were able to connect it probably wasn't.
Steve
-
@stephenw10 I did test that from the pfSense using LAN and it couldn't reach 10.10.0.1. I didn't mentioned it because no one asked, but it was one of the pings I tried, and yeah. In theory the pfSense is only doing firewall and the UDM Pro is routing, and all the UDM Pro networks work fine reaching the internet and everything, so the setup was working. It was just the internal networks on the pfSense weren't able to go through the UDMP.
-
Then it was almost certainly a config issue in the UDM.
Outbound connections would work without any special config in the UDM but it's probably still outbound NATing traffic which you don't really want. It should just be routing traffic and not NATing in either direction with pfSense handling outbound NAT for 10.10.0.0/24.That shouldn't prevent it routing inbound traffic but clearly it wasn't doing that for some reason.
Steve
-
@misinthe said in Issues with Subnet behind UDM Pro:
It was just the internal networks on the pfSense weren't able to go through the UDMP.
Most likely because the UDMP was still natting, and to get behind you would have had to setup port forwarding on the UDMP, etc.
If your going to use the pfsense LAN as transit network to downstream router, please do not put any devices on this network - or your going to run into asymmetrical traffic flow. Whenever you connect 2 or more routers together, especially if they can firewall devices on this "transit" network between routers are going to have asymmetrical flow unless you route on each of these hosts to which router to go to get to specific networks..
If the downstream router does not nat you will most likely see the problem with downstream network trying to talk to devices on the transit..
You run into this problem..
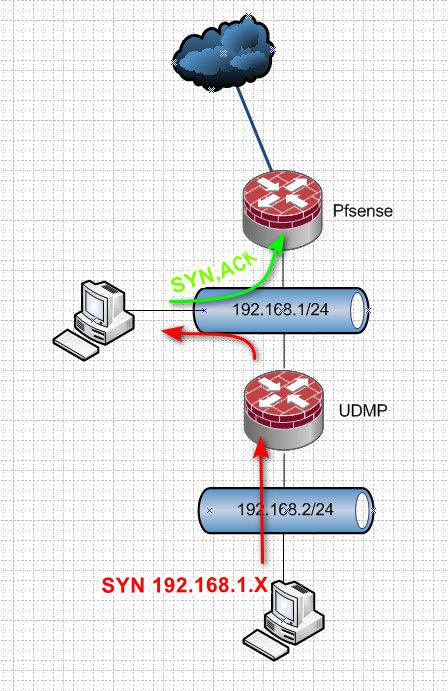
Pfsense never saw the SYN, so a SYN,ACK going to be block.. If your going to setup routers that talk to each other and route between networks they are attached to.. Setup a transit network.. See this diagram.