Block inbound requests to specific pages
-
What about : use a firewall ?
On the LAN interface : trusted users that can access whatever they want.
Second LAN2 : a second pass all rule, and a first "block all port "22 80 443" TCP that has a destination of tyhe LAN2 IP, the one pfSense is using. These users can't access pfSense anymore.Or, with just one LAN, but block access to pfSense except if the device is your device == your IP.
I don,'t understand what you managed to do with "pfBlockerNG-devel (pfBlockerNG is far to old).
snort might help, if the payload is in clear, or non-https. These days are nearly over, and https means : snort can't see the payload anymore, that is : a request for a page. -
@gertjan said in Block inbound requests to specific pages:
snort can't see the payload anymore, that is : a request for a page.
It can if you do it on the lan side and use haproxy to do the ssl offoad.. So to pfsense wan you don't see anything because https, but anything actually going to the server would be in the clear.
And could be filtered by an IPS.
-
I'm not caring about LAN at all. Right now there is absolutely no need to regulate LAN on this setup but it's WAN that must be harnessed. ;) With these 2 packages I managed to reduce bad requests by over 90% without too much finetuning. Only 10 very basic custom rules set up next to default settings. So I guess the better I understand snort syntax the better the threats will get blocked.
Now, I just need to get more refined custom rules set up in snort to block the remaining trash requests. Most of them get in over port 80 which is then blocked or redirected via url rewrite and redirect rules if it would be an existing url on https.
So even if pfBlockerNG might be old, it's still quite efficient in combination with snort.
Br,
Pascal -
@translating-it Hi Pascal! Can you send more details about snort+pfBlockerNG configuration? Thanks, Ale
-
@translating-it You need HA Proxy package for this.
So i am running a custom application where example.com/admin should not be accessible from the outside. The way its done today is by creating HA Proxy 'AND' rules that disallow this traffic.Another way is to have Cloudflare be your DNS. Using their ZeroTrust model you can control who can hit your page when resolving [ by GeoIP for example] the hostname of your application.. I use it for my home lab but for a more business situation, I use HA Proxy.
-
@michmoor Thanks for that hint. Can I also set up a rule that only traffic to specific (existing urls should go through, everything else would be blocked?
e.g. allow www.url.lb/impressum, www.url.lb/index
if anyone tries to access www.url.lb/ag4i they get blocked.Where can I find some good tutorials on how to set up such WAN rules?
Br,
Pascal -
@translating-it said in Block inbound requests to specific pages:
e.g. allow www.url.lb/impressum, www.url.lb/index
if anyone tries to access www.url.lb/ag4i they get blocked.Firewall rules can act upon IP addresses, ports and all kind of IP stuff.
Not on (part of) URLs.
Even pfBlockerng can't deal with URLs, just host names.
That's something dot somethin-else and morehere dot something dot somethin-else etc.This is the DNS part, and thats where pfBlockerng can do something for you.
All these :
www.url.lb/impressum
www.url.lb/index
www.url.lb/ag4iThe only part that is visible to pfSense is 'url.lb' (and maybe www.url.lb : check the resolver and/or pfblockng DNS query logs), as that happens when the browsers ask : what is the IP of 'url.lb'. And maybe also 'www.url.lb'.
From then, on, it's game over.
As the browser now uses that IP, opens a TLS connection to that IP, and asks for a page like /index.html or www.url.lb/impressum (www.url.lb/impressum/index.html).Now, there is no need to explain that you, me and no one else can see what happens in that TLS stream.
Because, that's what you want : security and privacy ;)If, by any chance, the site is http (only) : blacklist 'url.lb' all together. As Google did, years ago.
It would be a good thing if yoiu could proof me wrong on this.
For example : https://superuser.com/questions/763987/block-specific-url-paths
shows a possible solution : It's starts with : get a proxy ...
Another one : https://superuser.com/questions/1413274/how-to-block-specific-url-rather-than-the-entire-domain-on-a-computer-without-so
So, pfSense won't help you breaking TLS (https:// ...)

-
-
@translating-it There are a few ways to do this - control inbound requests to a url that doesn't exist
so if you have example.com/admin
-
HA Proxy package with ACLs on your FrontEnd settings. Anyone attempting to hit example.com/admin will receive a 400 message.
-
Have your domain in CloudFlare and it is your authoritative name server. Cloudflare has a WAF component where you create firewall rules. See below
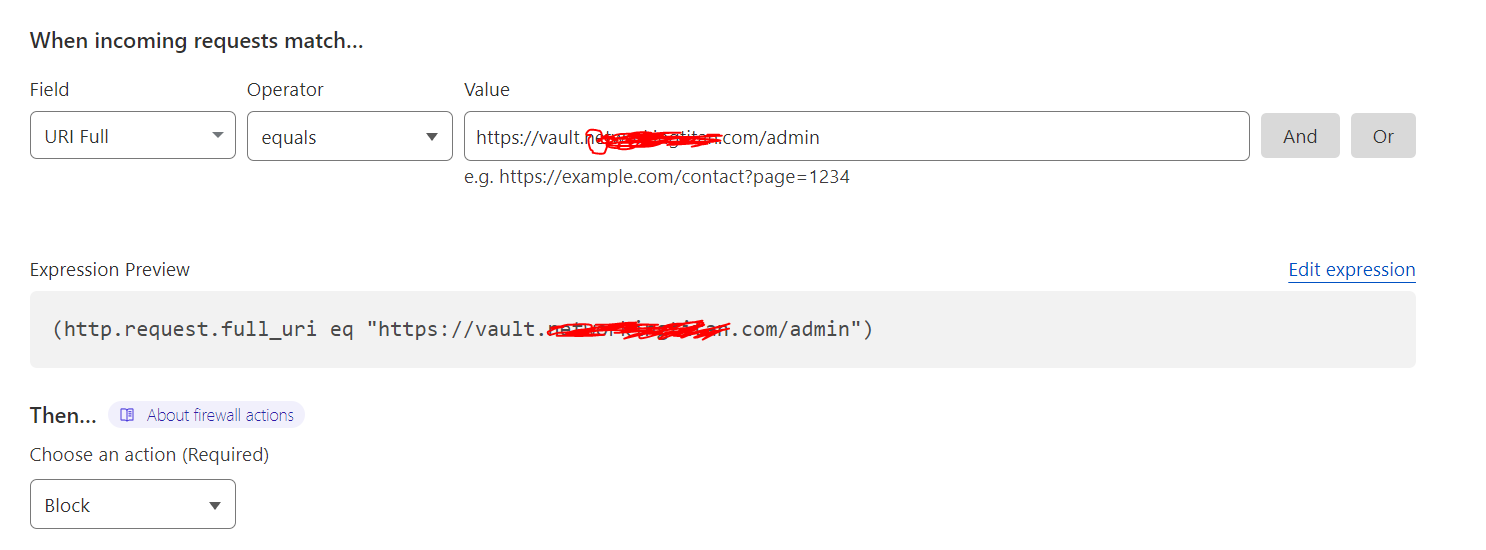
The block/ban isnt something that HA proxy can do..As far as im aware. There may be a way. You would need to search the HA documentation for that.
-
-
@michmoor due to security and GDPR reasons ClouldFlare is NOT an option for me. I use my own server at a hoster in Germany and not services like CloudFlare or similar. So only the first option would be interesting, although I have no idea how this could be set up without any example or tutorials.