Custom IPv4 Allow List
-
Hello,
I've just setup a new pfSense firewall for a web hosting environment. On the WAN interface, I have rules in place that allow traffic over specified ports to the desired internal addresses (using VIPs and 1:1 NAT).
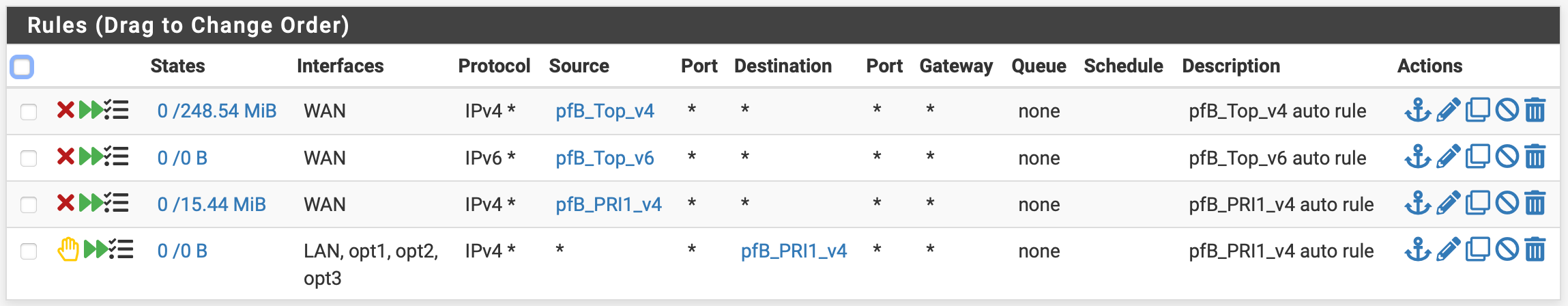
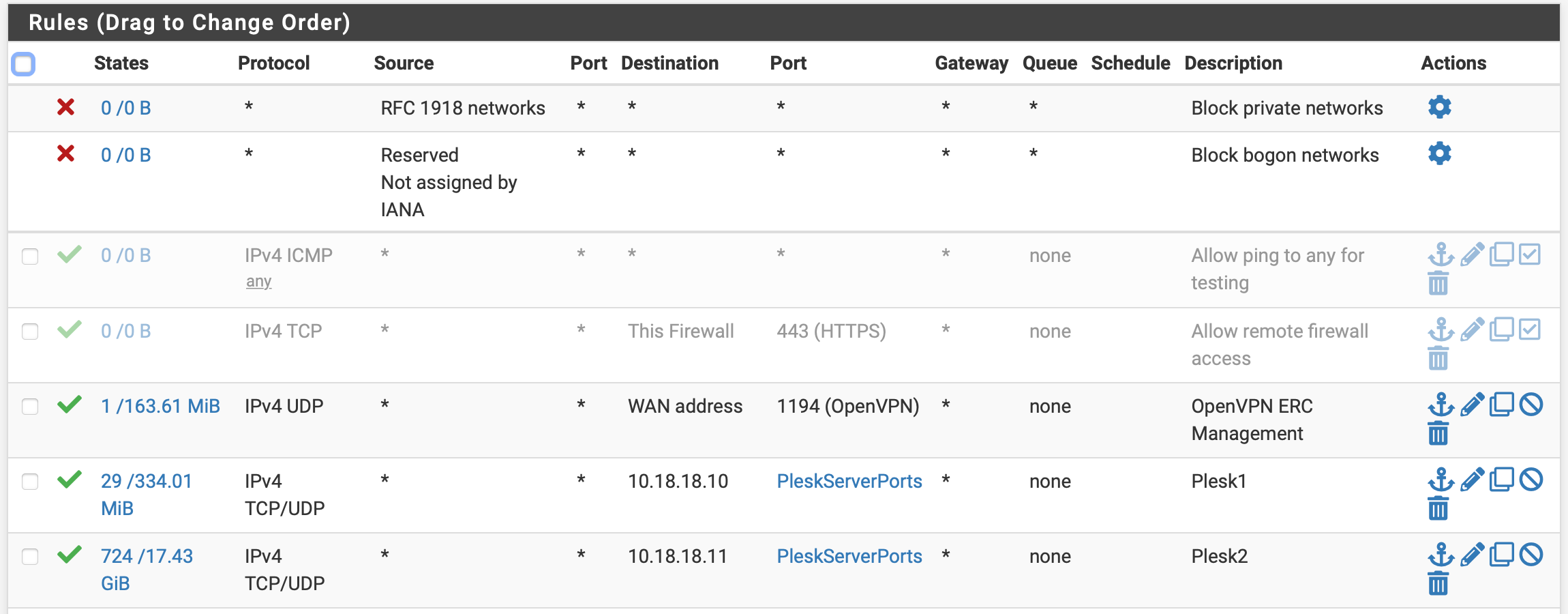
I also have pfBlockerNG setup and use the PRI1 (deny both) and GeoIP Top Spammers (deny inbound) lists.
However, I occasionally need to allow IPs for developers in countries that may appear on these lists. What is the best way to create a custom allowed list for these addresses so that they're not blocked by the above rules created by pfBlocker?
Thanks in advance for any advice!
-
@wesleywillis Tried not using floating rules ?
https://docs.netgate.com/pfsense/en/latest/firewall/rule-methodology.html
-
Hello!
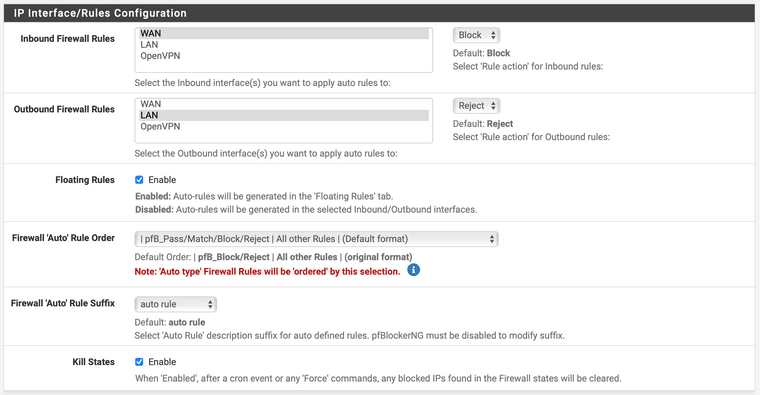
On the PfBlockerNG > IP > IPv4 page you can +ADD an IPv4 list.
Give it a name in the Info section and an Action (Permit Inbound) in the Settings section.
Use the IPv4 Custom_List section at the bottom to specify IP addresses.
Adjust the Advanced Inbound Firewall Rule Settings as required.
Make sure to perform a PfBlockerNG > Update when you are done.John
-
@wesleywillis There is a way to order rules in pfBlocker settings, but what I find easier and clearer is for any of those type of blocks where I need to allow some, create the pfB list as Alias Native. That just creates the alias without any rules. You can then use the alias in whatever rules, NAT forward, etc.
allow from Good_IP
block from Bad_IPs