Noob WireGuard Setup Questions
-
Here's a good video from the developer of the Wireguard package that goes into how to set up a remote access tunnel:
https://www.youtube.com/watch?v=bCNnP8FDSNA
It should help you get things sorted out.
-
@dma_pf said in Noob WireGuard Setup Questions:
Here's a good video from the developer of the Wireguard package that goes into how to set up a remote access tunnel:
https://www.youtube.com/watch?v=bCNnP8FDSNA
It should help you get things sorted out.
Thanks for that. I'd been watching another of his videos on Basic Site-to-Site VPN Using WireGuard and pfSense:
https://youtu.be/2oe7rTMFmqc
but it wasn't giving me the information I needed. I never thought to dig into his Project Reports.
-
@areckethennu said in Noob WireGuard Setup Questions:
Thanks for that.
Your welcome, glad I could help. If you run into issues post back here and I'll see if I can help you further.
-
I followed the video at:
https://www.youtube.com/watch?v=bCNnP8FDSNA
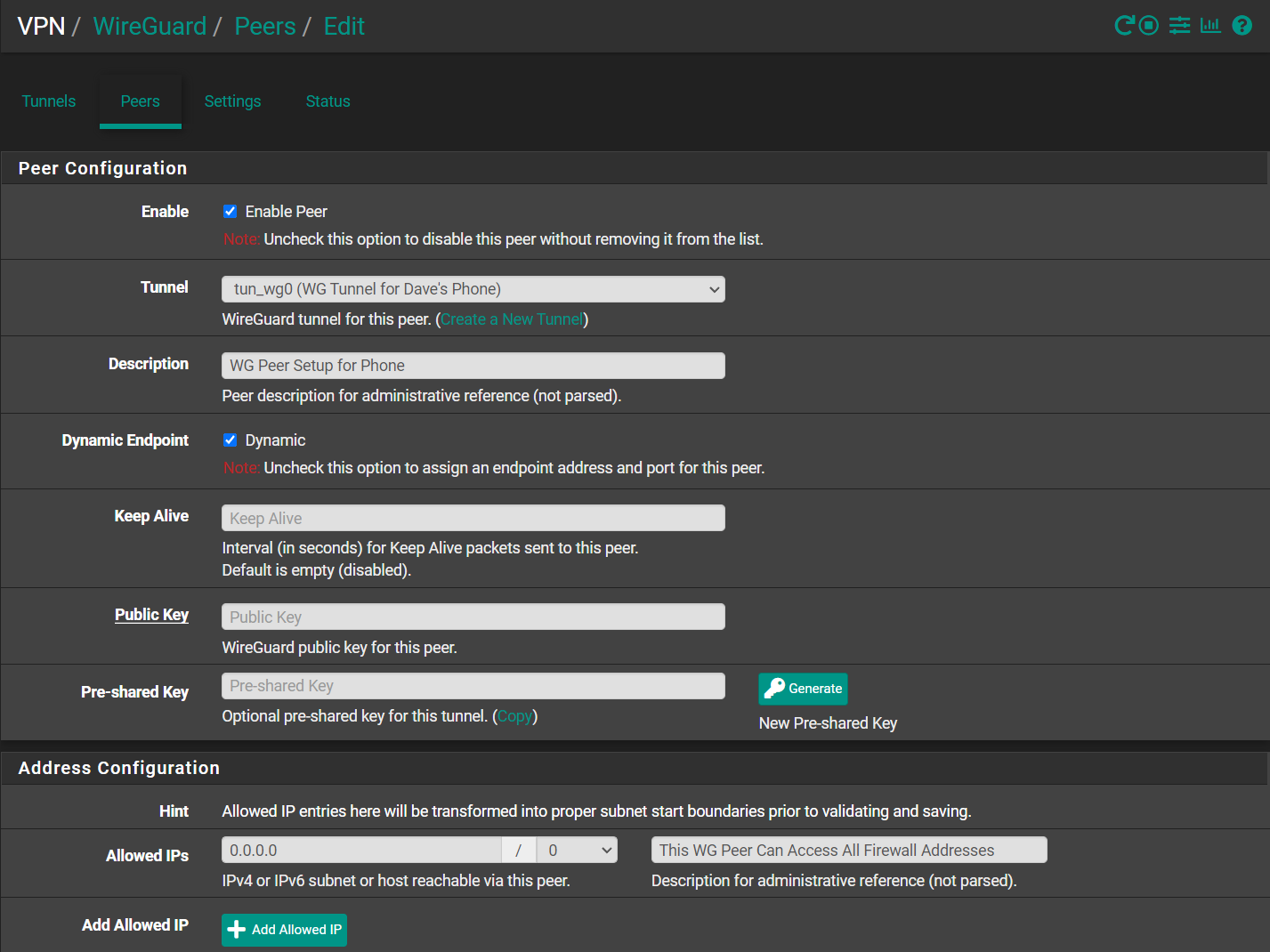
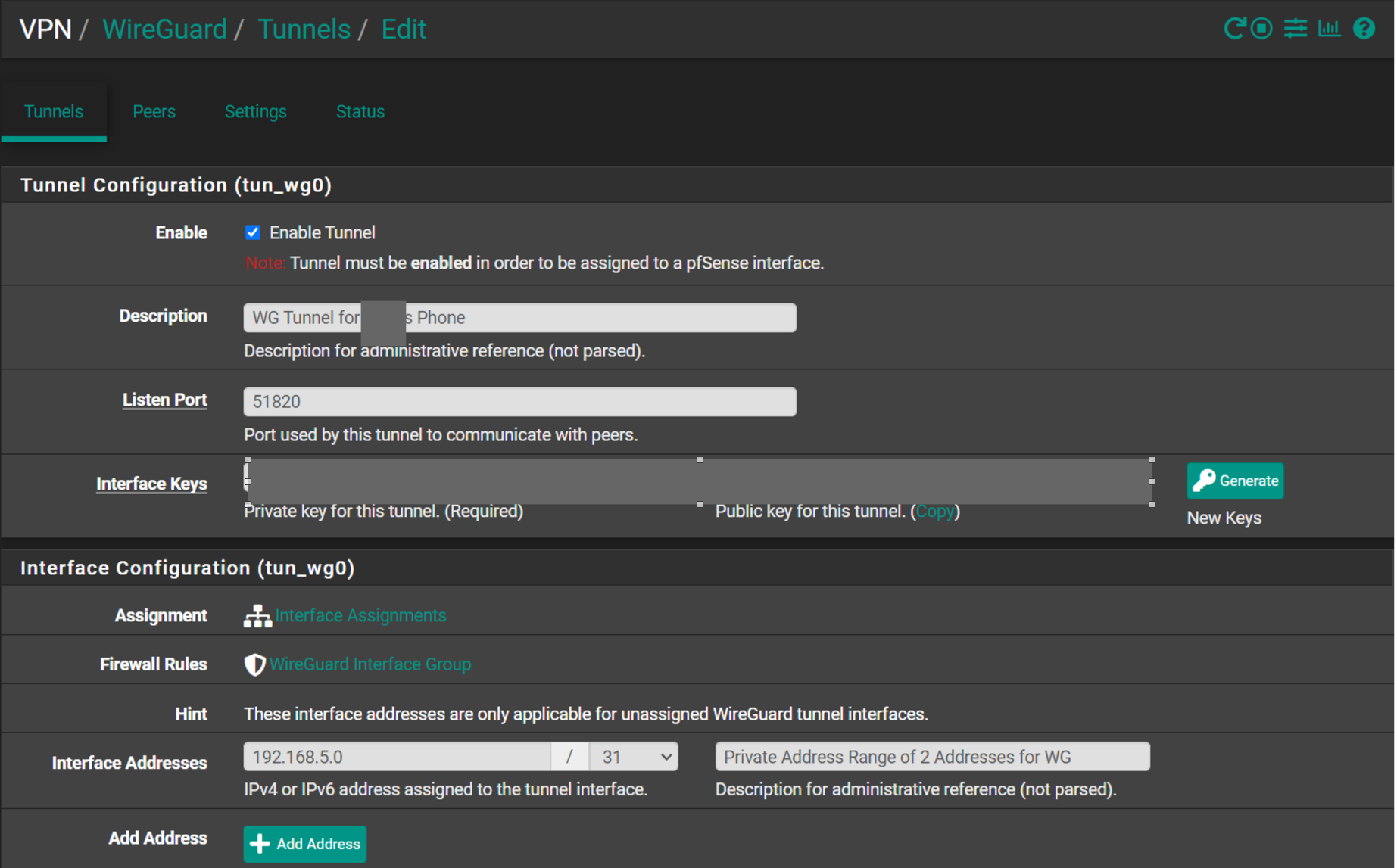
And got WireGuard working between my phones and pfSense. The biggest difference between what I was trying and what the developer said to do is that the remote devices could actually share a single tunnel. So, I modified my tunnel address range to be a /24 from a /31 (yes, that's way too big, but that's what he used and I didn't want to introduce a variable). Also, with the tunnel, I changed the address range to 192.168.5.1 from 192.168.5.0. For the peers, I changed the address of each remote device from my attempt at 0.0.0.0/0 to 192.168.5.n/32 (where n is the nth device I set up as a peer). There were also some minor differences in the Firewall rules (basically restricting the network to the tunnel range instead of leaving it open to all).
On the phones, the Interface addresses match what was set up in the peer, except it's a /24 instead of a /32. I also had to include the pfSense local address as the DNS server (192.168.1.1). On the Peer side of the phones, I gave it the DDNS address for my pfSense box (without any http prefix stuff) and the Allowed IPs are that 0.0.0.0/0 wildcard.
Again, on the phones, that works fine. But, on a Windows laptop, it doesn't work at all. Once I turn on the WG tunnel, I lose the network/internet. It looks like the laptop won't connect to the wireless access point (which is in bridge mode to pfSense for IPs and stuff). I thought the phones might be working because they were connecting through the data plan instead of wireless. But, even with the data plan turned off, they still connect. Meanwhile, the laptop won't. I'm going to have to research this some more.
-
@areckethennu It helps to actually enter the right information into the peer setup on pfSense. It turns out I copied the private key into where the public key was supposed to go. So, all my remote devices are working correctly now.
-
OK. Next noob question. Is there some way to let the remote devices coming into the network from the outside see resources on the inside? My remote devices are coming in on 192.168.5.x, but everything on my internal network (specifically, my NAS) is on 192.168.1.x. (different subnets).
-
@areckethennu said in Noob WireGuard Setup Questions:
Is there some way to let the remote devices coming into the network from the outside see resources on the inside?
Easy! You need to set up a rule on the wireguard interface to allow traffic from the 192.168.5.0/24 network to the 192.168.1.0/24 network. If you want to limit access to only certain peers you can create an alias with IPs of the allowed peers and use the alias as the source in the rule. Likewise, if you want to limit access to only certain resources on the 1.x network. As you're new to pfsense it's a good time to read up on how the rules work in pfsense: https://docs.netgate.com/pfsense/en/latest/firewall/rule-methodology.html
If you did not set up a dedicated interface and gateway for the wireguard tunnel and the above rule does not work then you will also have to add an outbound NAT rule. The rule should have the .5.x network as the source and the .1.x network as the destination. https://docs.netgate.com/pfsense/en/latest/nat/outbound.html
The firewall rule allows the traffic coming from your wireguard interface to enter pfsense so that it can be routed. The NAT rule keeps track of the traffic leaving the interface so that it can be properly routed back into the wireguard interface. Both of the rules need to be in place for the traffic to work.
-
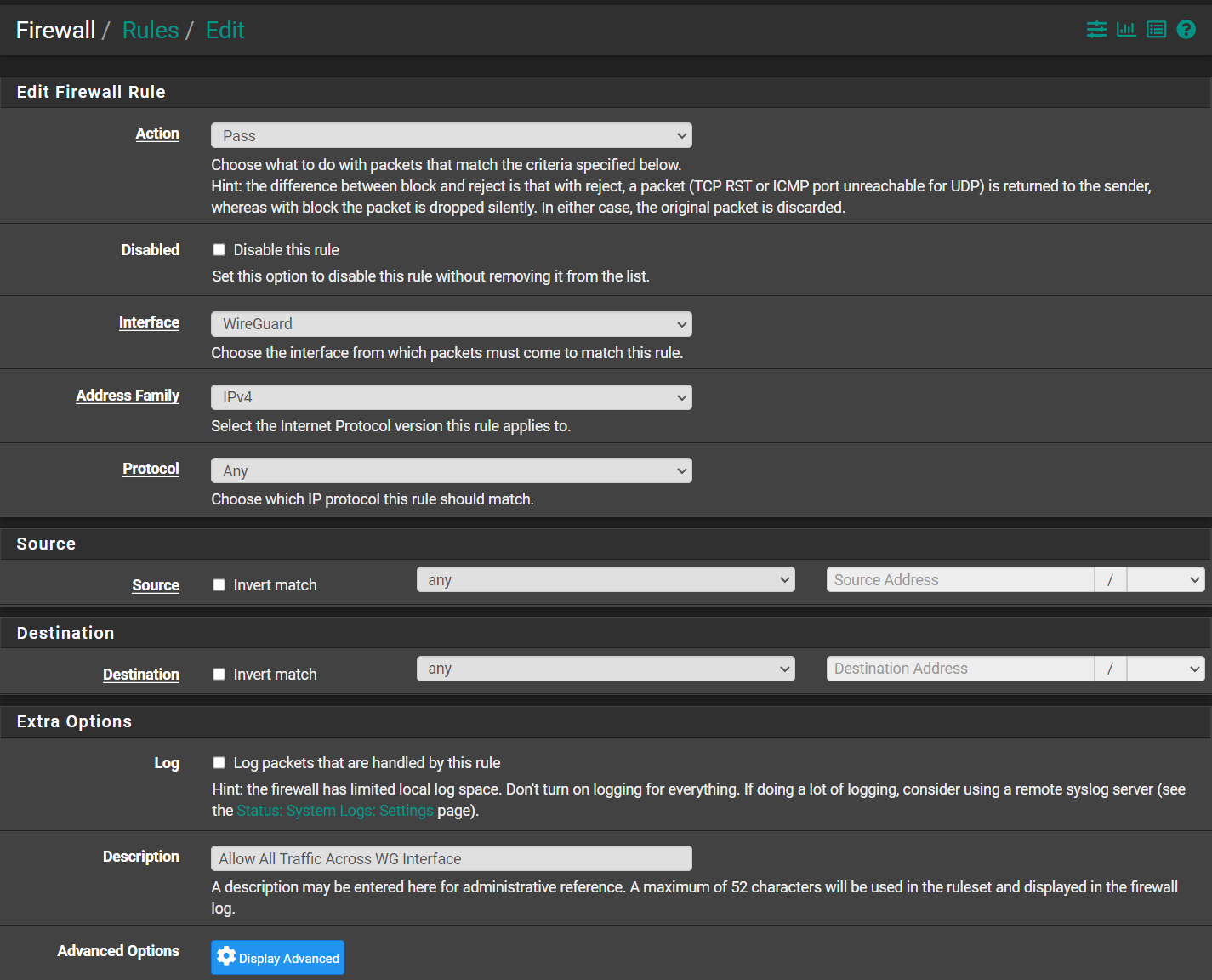
@dma_pf I'd already had a rule under Firewall > Rules > WireGuard
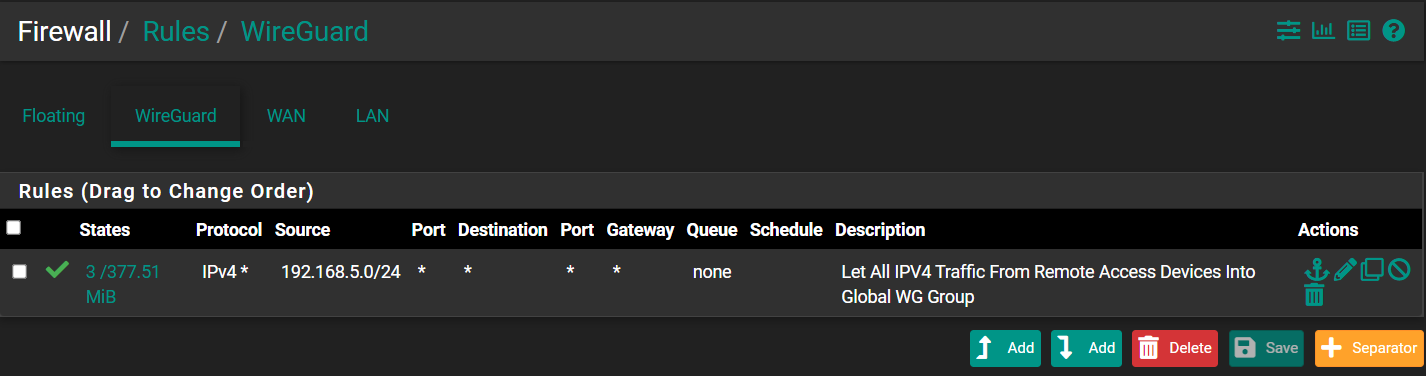
That should give my WireGuard remote devices access to all. But, just in case, I modified the rule to give a Destination of This Firewall (self). Though I have no idea what the difference is between All (*) and everything (This Firewall (self)). Anyway, it made no difference.
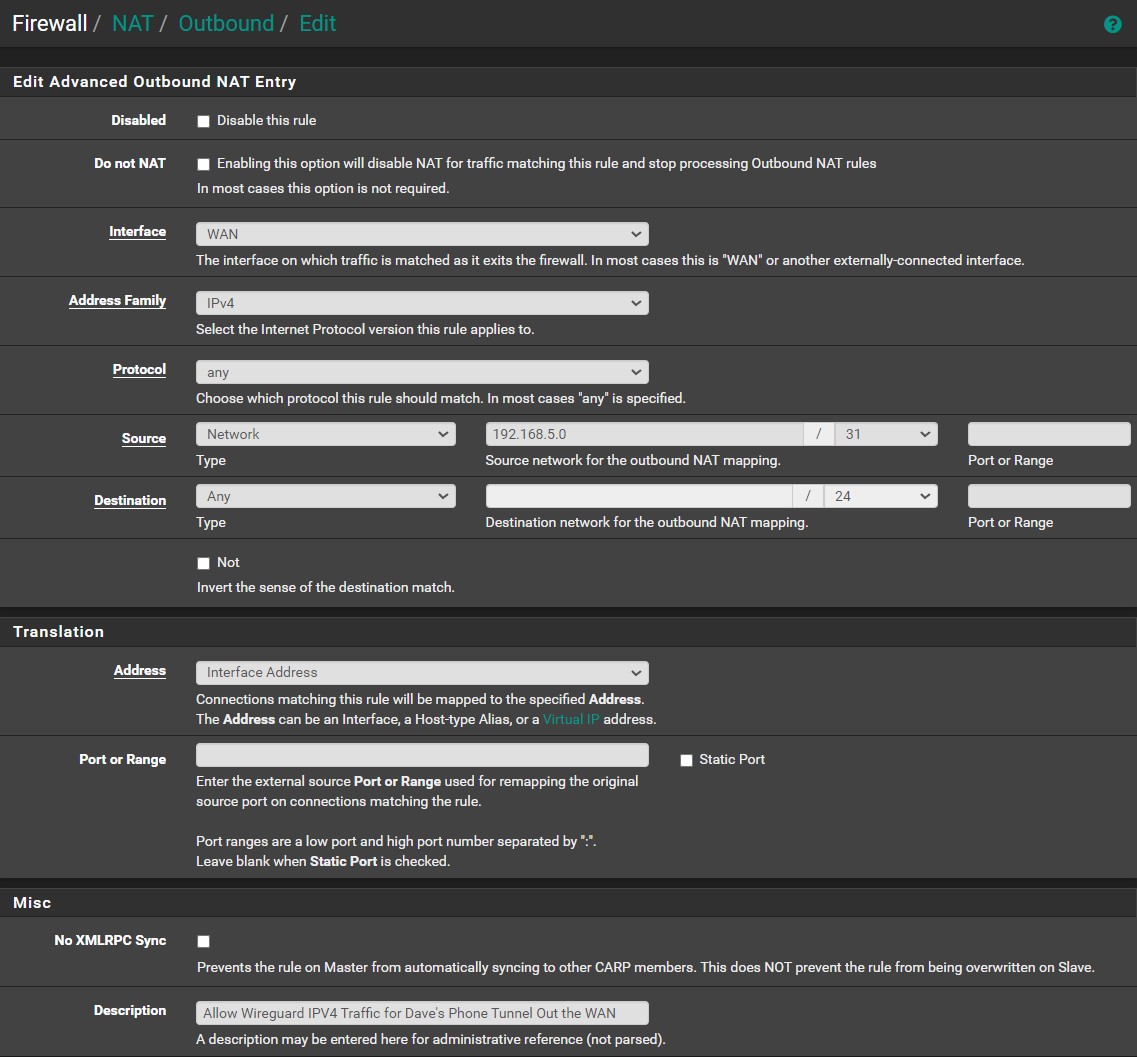
So, off I went to Firewall > NAT > Outgoing and set up a rule to translate my WireGuard remote devices' address over to my LAN (the second hybrid rule showing below):
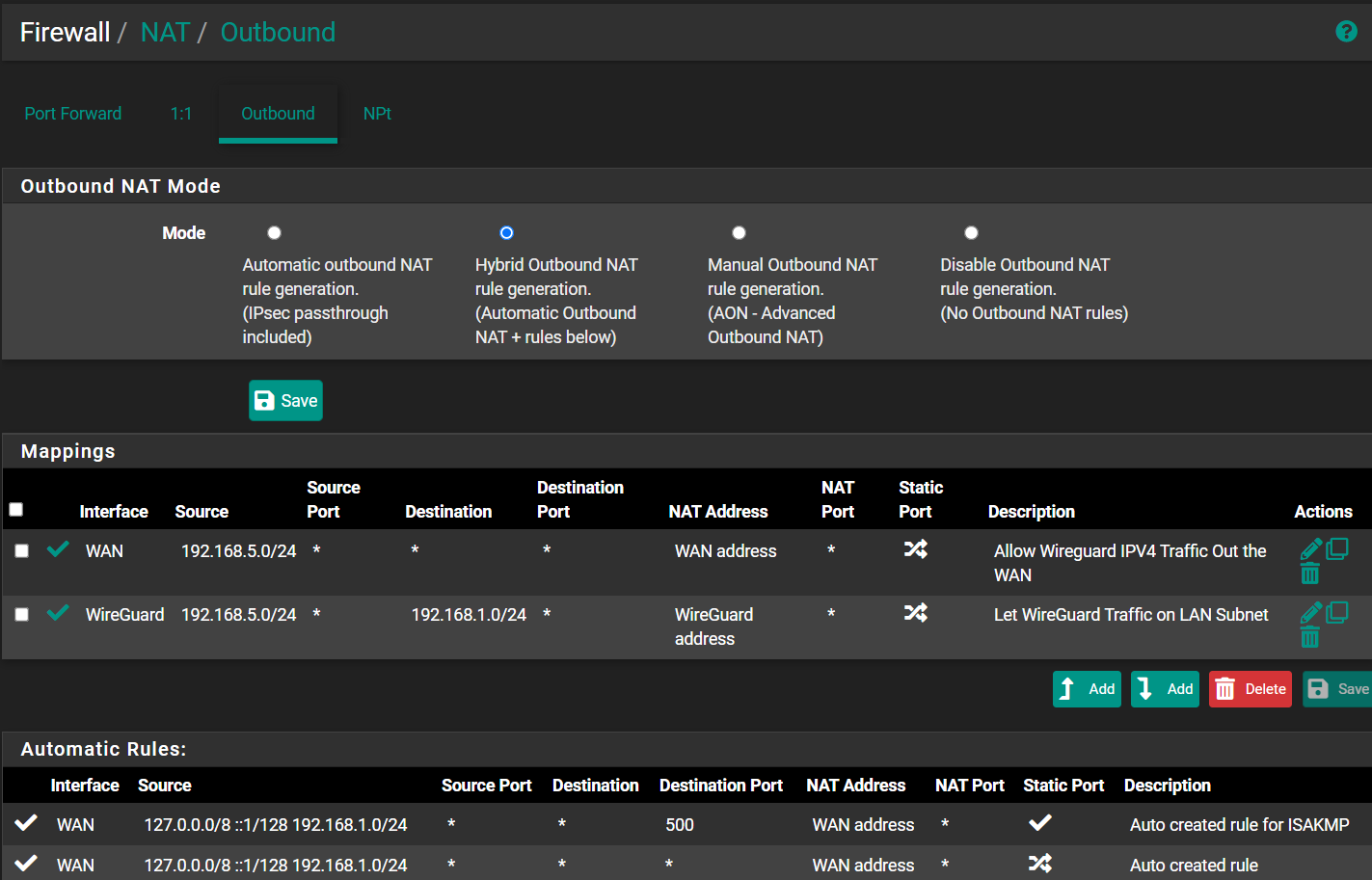
That worked (mostly). The phones continued working and the notebook finally connected. BUT, again with the notebook, even though it can now get to the internet, it won't look at the local network. In Windows File Explorer, my network mappings come up with a red circle, and trying to go to a 192.168.1.x address doesn't work. In the browser, I get an error that I'm denied access to the network. I THINK it's because the WireGuard tunnel is showing as a Public connection instead of a Private one (and I can't figure out how to change it). But, even if I change the Sharing Settings for Windows' Public connections to allow network discovery, it still doesn't work.
I don't understand why there's such a behavioral difference between Android phones and Windows notebook going through the same Wireguard tunnel.
-
@areckethennu Sorry man, my mistake...on theWwireGuard NAT rule try changing the source to 192.168.1.0/24 and change the value in Destination to Any.
-
@dma_pf said in Noob WireGuard Setup Questions:
@areckethennu Sorry man, my mistake...on theWwireGuard NAT rule try changing the source to 192.168.1.0/24 and change the value in Destination to Any.
I'm confused. I thought that second hybrid Outgoing NAT rule allows the translation of traffic leaving my WireGuard remote devices from the WireGuard interface to my LAN subnet (192.168.1.0/24). Of course, I think the NAT Address on the rule shouldn't be WireGuard Address. It should probably be the LAN subnet.
I agree with making the destination any (*). But, I don't understand why I'd want my Source addresses to be from my LAN subnet instead of my from my WireGuard subnet.
I'm going to play around with the NAT rules some more. But, I think I'm to the point where Windows is the problem instead of the tunnel.
I did find a way to make the WireGuard tunnel a Private one instead of a Public one. Either edit the Windows Registry:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles ```, find the correct network connection by scrolling through them and change "Category" from 0 to 1. Apparently, another way is a PowerShell (admin) command:Set-NetConnectionProfile -InterfaceAlias 'wg0' -NetworkCategory 'Private'
where wg0 is whatever it is in Windows. I also went into the Windows Firewall and told it to allow the WireGuard app access to both Public and Private networks. Unfortunately, none of that fixed the problem. I'll see if any NAT rule changes help.