Can't get OpenVPN to work
-
Hi@all,
I have been trying to get OpenVPN to work for two days.
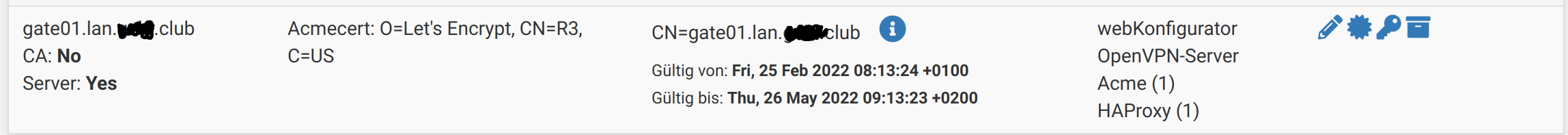
I have set up a certificate for the host 'gate01.lan.example.club' with ACME:

and a certificate is created:
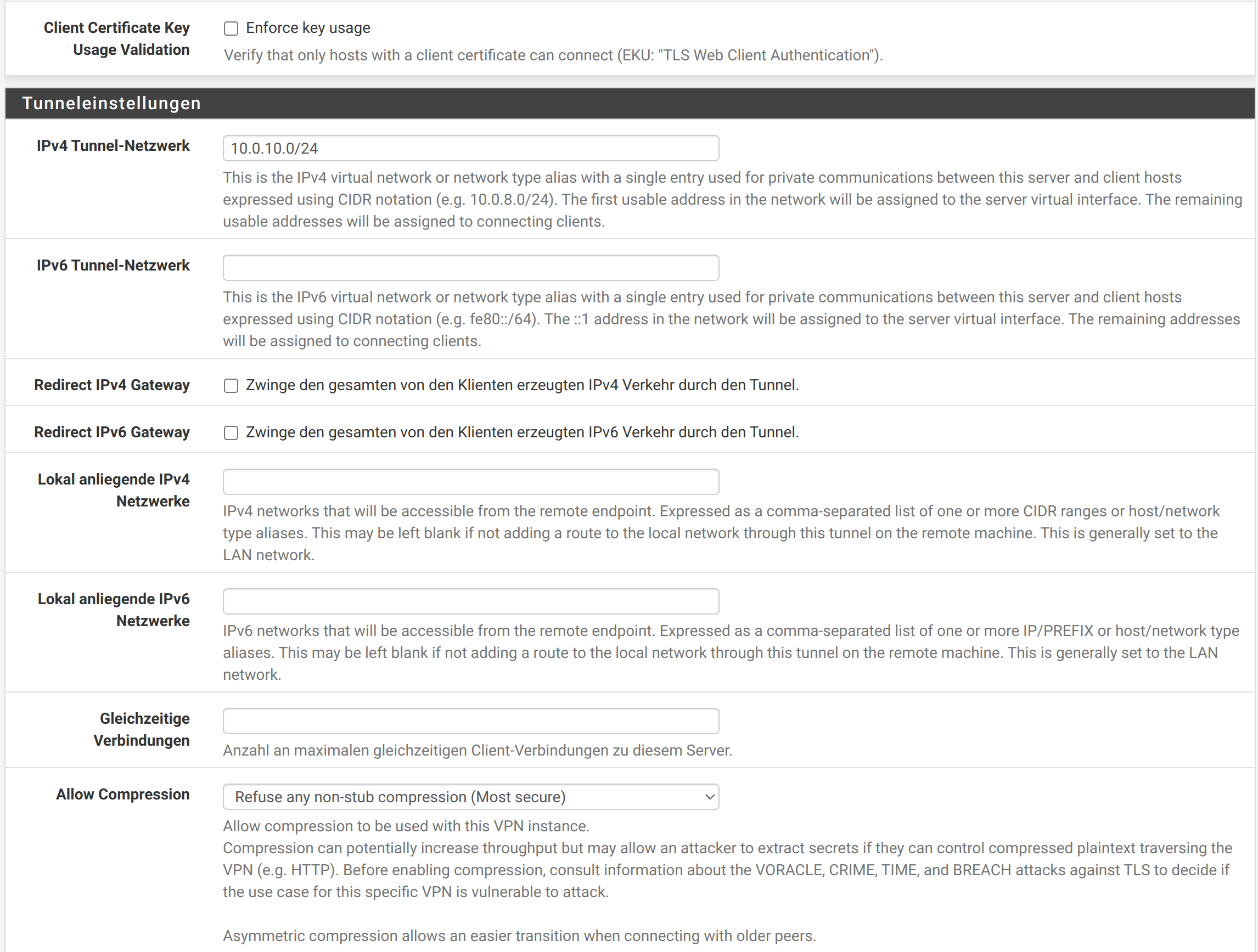
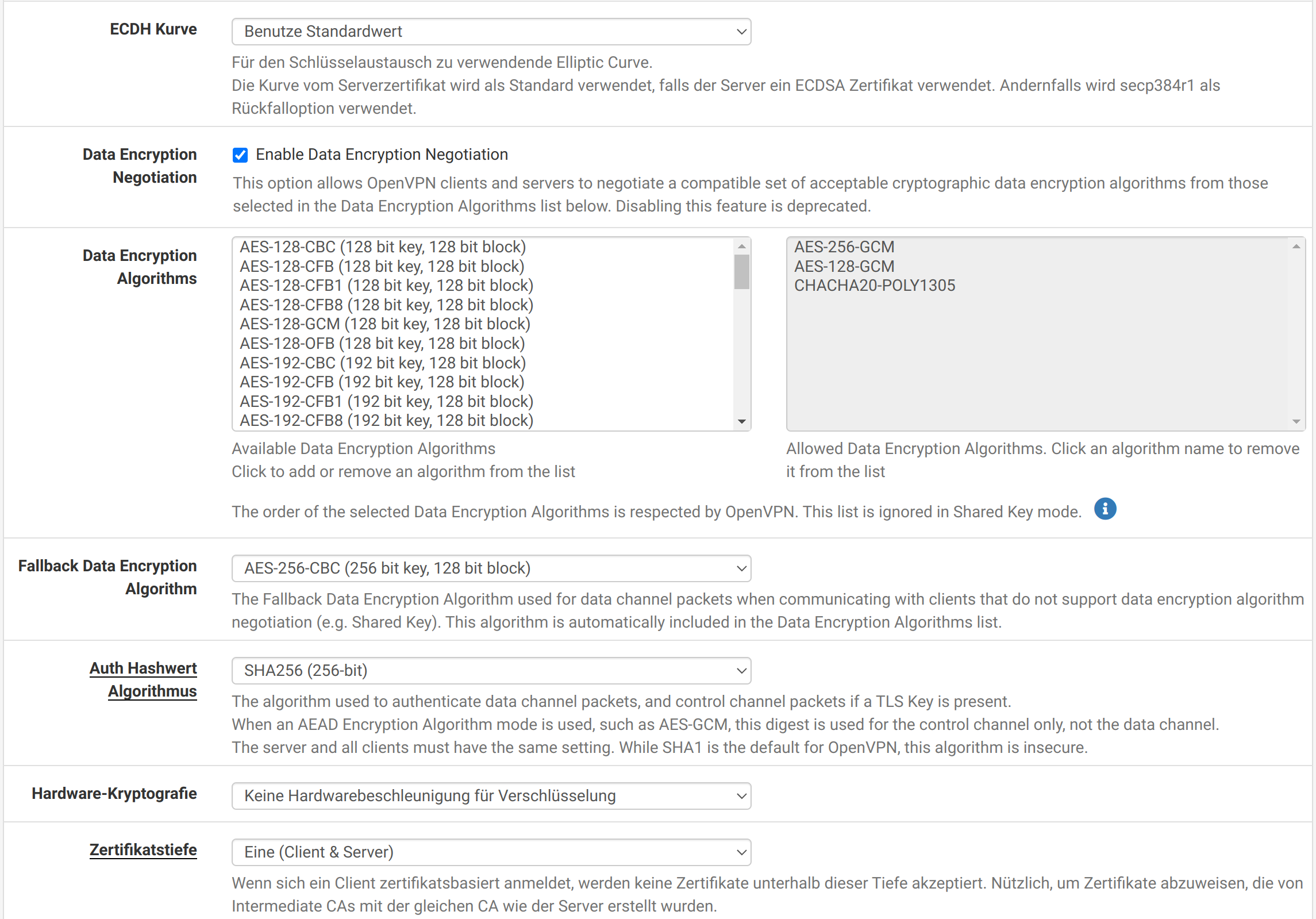
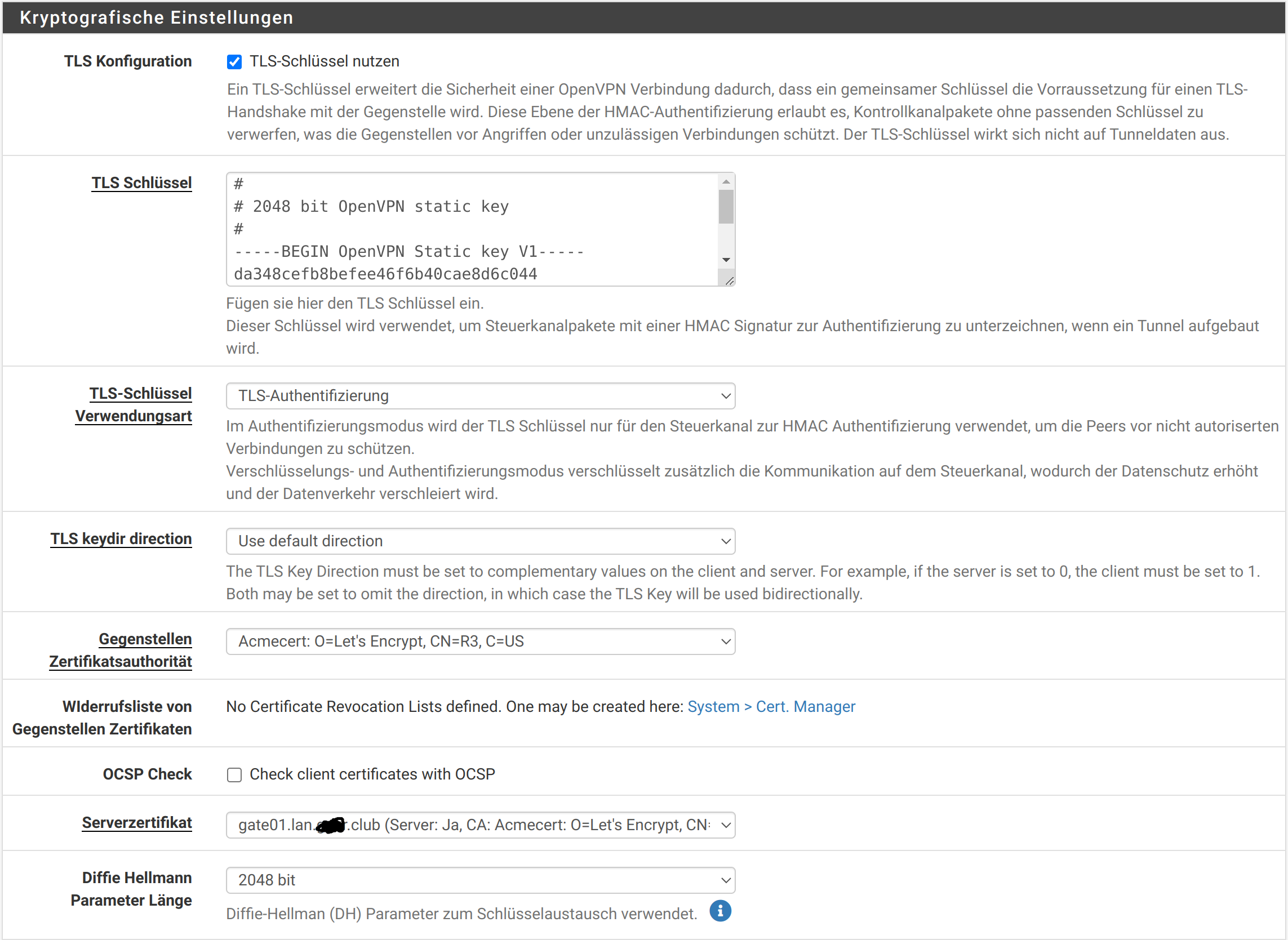
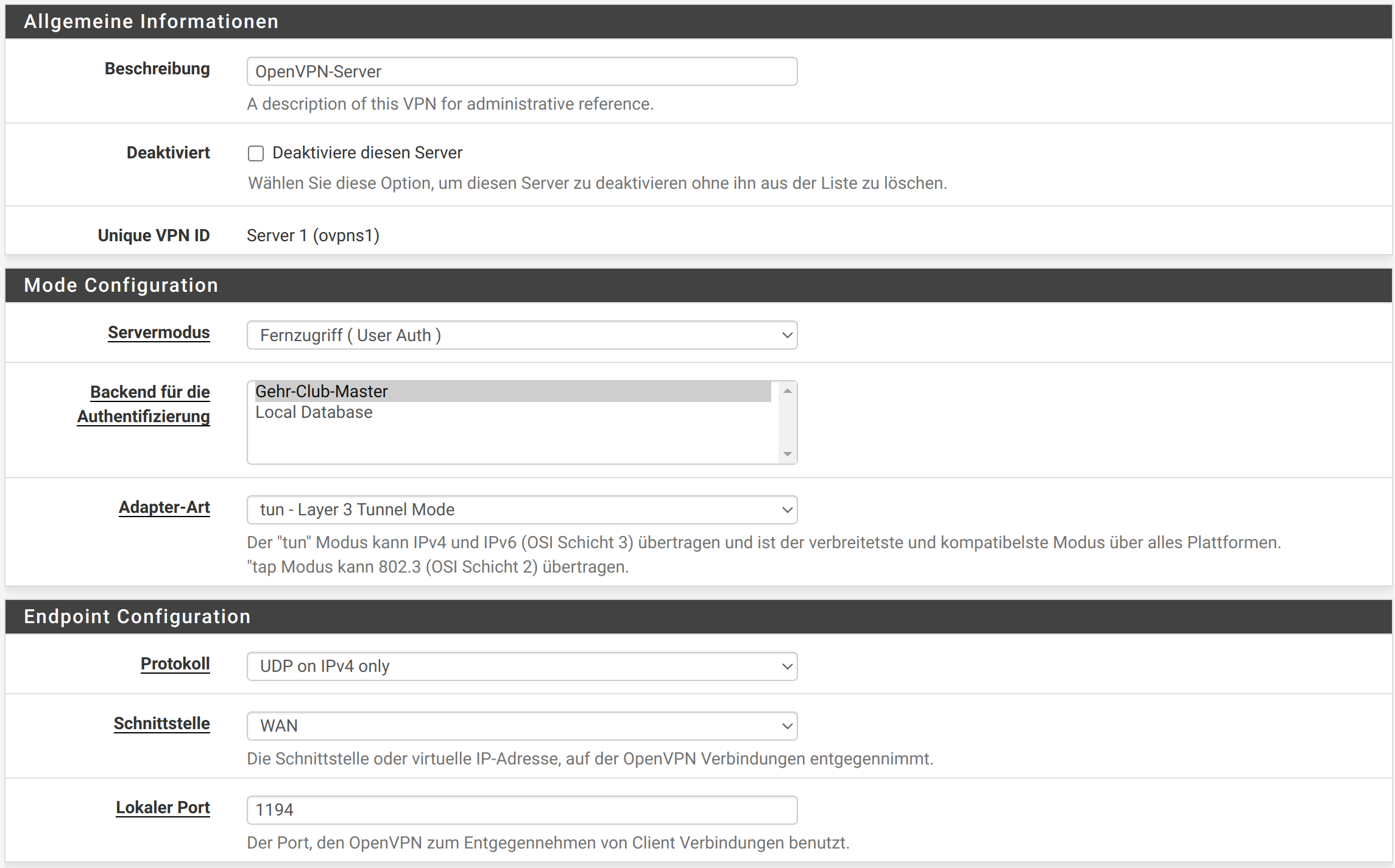
then configures the OpenVPN server:
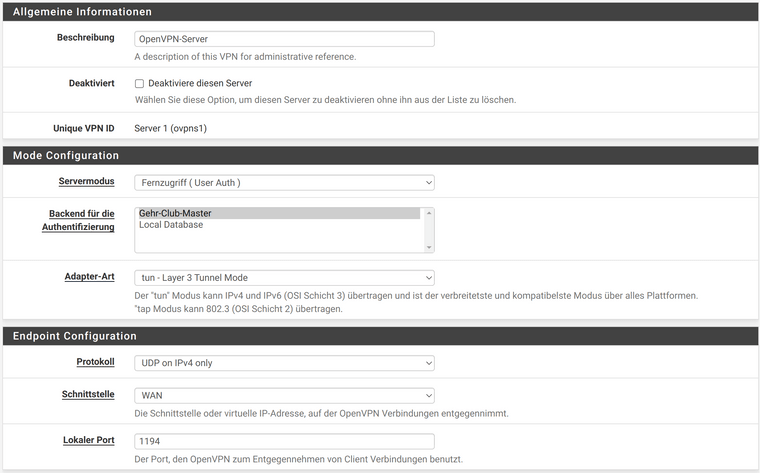
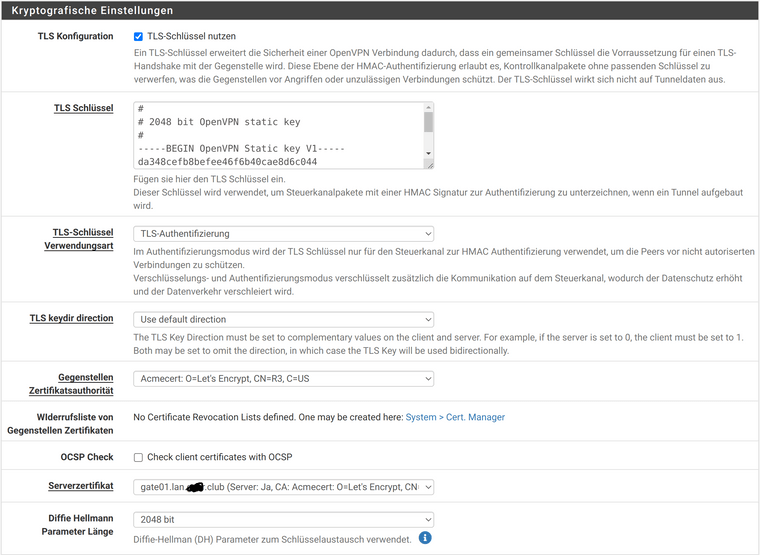
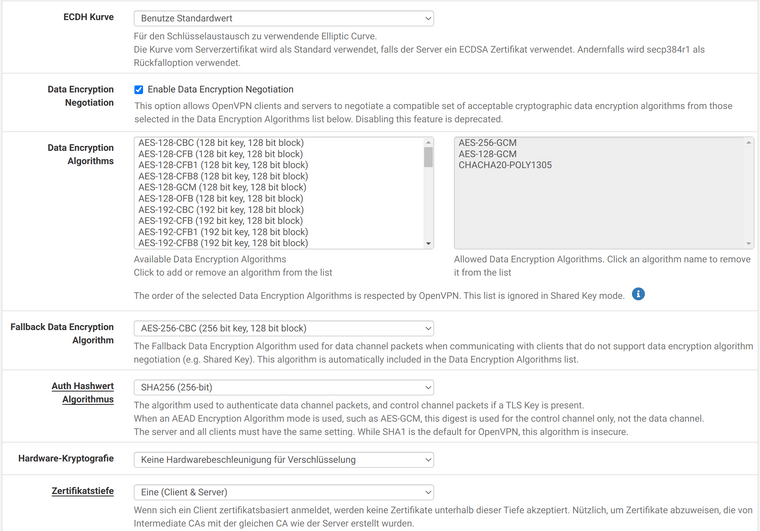
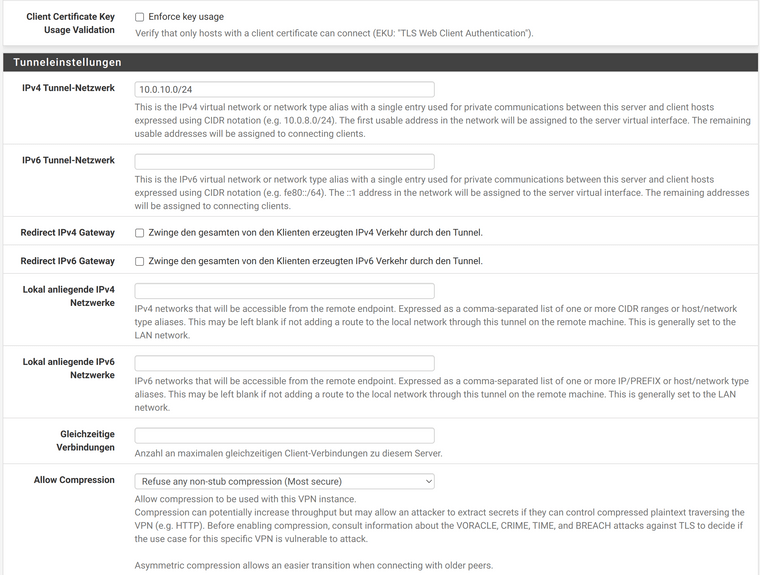
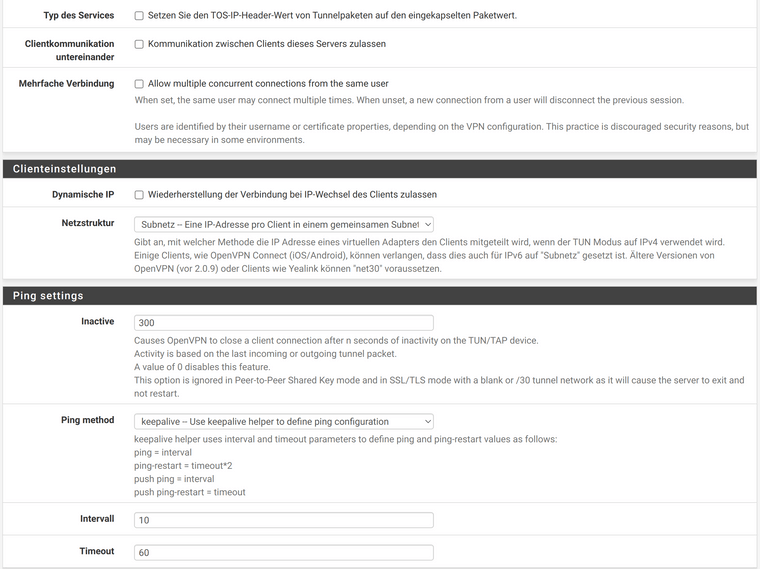
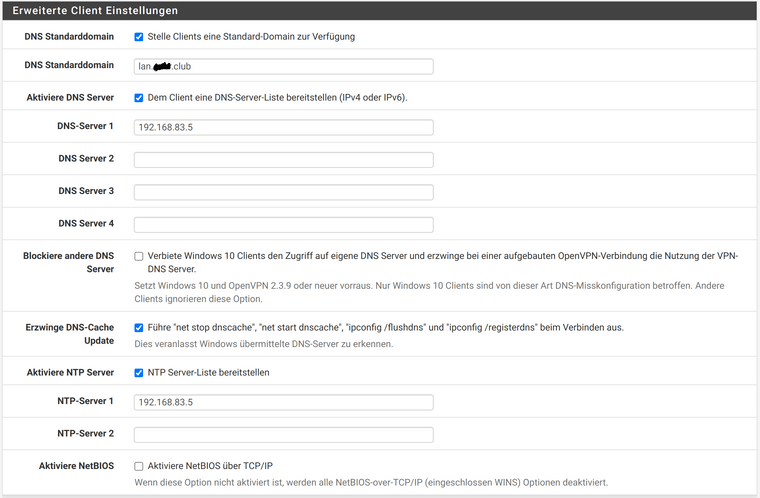
For the client (Ubuntu 20.04), I export the bundle on the server:
dev tun persist-tun persist-key data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC auth SHA256 tls-client client resolv-retry infinite remote gate01.lan.example.club 1194 udp4 nobind auth-user-pass ca gate01-UDP4-1194-ca.crt tls-auth gate01-UDP4-1194-tls.key 1 remote-cert-tls server explicit-exit-notifyA firewall rule is created:
When I now try to extend the connection, I only find the following on the pfSense in the openvpn.log:
Feb 25 12:00:21 openvpn 58429 OpenVPN 2.5.4 amd64-portbld-freebsd12.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on Jan 12 2022 Feb 25 12:00:21 openvpn 58429 library versions: OpenSSL 1.1.1l-freebsd 24 Aug 2021, LZO 2.10 Feb 25 12:00:21 openvpn 58761 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/server1/sock Feb 25 12:00:21 openvpn 58761 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 12:00:21 openvpn 58761 PLUGIN_INIT: POST /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so '[/usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so] [/usr/local/sbin/ovpn_auth_verify_async] [user] [R2Voci1DbHViLU1hc3Rlcg==] [false] [server1] [1194]' intercepted=PLUGIN_AUTH_USER_PASS_VERIFY Feb 25 12:00:21 openvpn 58761 Diffie-Hellman initialized with 2048 bit key Feb 25 12:00:21 openvpn 58761 WARNING: experimental option --capath /var/etc/openvpn/server1/ca Feb 25 12:00:21 openvpn 58761 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication Feb 25 12:00:21 openvpn 58761 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA256' for HMAC authentication Feb 25 12:00:21 openvpn 58761 TUN/TAP device ovpns1 exists previously, keep at program end Feb 25 12:00:21 openvpn 58761 TUN/TAP device /dev/tun1 opened Feb 25 12:00:21 openvpn 58761 /sbin/ifconfig ovpns1 10.0.10.1 10.0.10.2 mtu 1500 netmask 255.255.255.0 up Feb 25 12:00:21 openvpn 58761 /sbin/route add -net 10.0.10.0 10.0.10.2 255.255.255.0 Feb 25 12:00:21 openvpn 58761 /usr/local/sbin/ovpn-linkup ovpns1 1500 1621 10.0.10.1 255.255.255.0 init Feb 25 12:00:21 openvpn 58761 Socket Buffers: R=[42080->42080] S=[57344->57344] Feb 25 12:00:21 openvpn 58761 UDPv4 link local (bound): [AF_INET]37.49.18.169:1194 Feb 25 12:00:21 openvpn 58761 UDPv4 link remote: [AF_UNSPEC] Feb 25 12:00:21 openvpn 58761 MULTI: multi_init called, r=256 v=256 Feb 25 12:00:21 openvpn 58761 IFCONFIG POOL IPv4: base=10.0.10.2 size=252 Feb 25 12:00:21 openvpn 58761 Initialization Sequence Completed Feb 25 12:00:26 openvpn 58761 MANAGEMENT: Client connected from /var/etc/openvpn/server1/sock Feb 25 12:00:26 openvpn 58761 MANAGEMENT: CMD 'status 2' Feb 25 12:00:26 openvpn 58761 MANAGEMENT: Client disconnectedIt looks like nothing arrives at the OpenVPN server at all.
What have I overlooked?
with best
pixel24 -
@pixel24
You will get more usefully information from the client log.Which client are you using?
-
Feb 25 12:36:54 lt001 NetworkManager[709]: <info> [1645789014.1006] audit: op="connection-activate" uuid="9e6a7e66-3741-4d0c-b4c1-96edc5d329ab" name="example-Club" pid=10803 uid=1049601120 result="success" Feb 25 12:36:54 lt001 NetworkManager[709]: <info> [1645789014.1040] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: Started the VPN service, PID 12377 Feb 25 12:36:54 lt001 NetworkManager[709]: <info> [1645789014.1103] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: Saw the service appear; activating connection Feb 25 12:36:54 lt001 NetworkManager[709]: <info> [1645789014.1595] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: VPN plugin: state changed: starting (3) Feb 25 12:36:54 lt001 NetworkManager[709]: <info> [1645789014.1596] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: VPN connection: (ConnectInteractive) reply received Feb 25 12:36:54 lt001 nm-openvpn[12387]: WARNING: file '/data01/Sicherheit/OVPN/example-Club/gate01-UDP4-1194/gate01-UDP4-1194-tls.key' is group or others accessible Feb 25 12:36:54 lt001 nm-openvpn[12387]: OpenVPN 2.4.7 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Jul 19 2021 Feb 25 12:36:54 lt001 nm-openvpn[12387]: library versions: OpenSSL 1.1.1f 31 Mar 2020, LZO 2.10 Feb 25 12:36:54 lt001 nm-openvpn[12387]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 12:36:54 lt001 nm-openvpn[12387]: TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.83.254:1194 Feb 25 12:36:54 lt001 nm-openvpn[12387]: UDPv4 link local: (not bound) Feb 25 12:36:54 lt001 nm-openvpn[12387]: UDPv4 link remote: [AF_INET]192.168.83.254:1194 Feb 25 12:36:54 lt001 nm-openvpn[12387]: NOTE: chroot will be delayed because of --client, --pull, or --up-delay Feb 25 12:36:54 lt001 nm-openvpn[12387]: NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay Feb 25 12:37:07 lt001 systemd[1]: Starting SSSD Sudo Service responder... Feb 25 12:37:07 lt001 chown[12393]: /bin/chown: Zugriff auf '/var/log/sssd/sssd_sudo.log' nicht möglich: Datei oder Verzeichnis nicht gefunden Feb 25 12:37:07 lt001 systemd[1]: Started SSSD Sudo Service responder. Feb 25 12:37:07 lt001 sssd_sudo[12394]: Starting up Feb 25 12:37:08 lt001 systemd[1]: Starting SSSD PAM Service responder... Feb 25 12:37:08 lt001 systemd[1]: Started SSSD PAM Service responder. Feb 25 12:37:08 lt001 sssd_pam[12396]: Starting up Feb 25 12:37:08 lt001 sudo[12392]: s.example : TTY=unknown ; PWD=/home/s.example ; USER=root ; COMMAND=/usr/lib/linuxmint/mintUpdate/dpkg_lock_check.sh Feb 25 12:37:08 lt001 sudo[12392]: pam_unix(sudo:session): session opened for user root by (uid=0) Feb 25 12:37:08 lt001 sudo[12392]: pam_unix(sudo:session): session closed for user root Feb 25 12:37:08 lt001 sudo[12399]: s.example : TTY=unknown ; PWD=/home/s.example ; USER=root ; COMMAND=/usr/bin/mint-refresh-cache Feb 25 12:37:08 lt001 sudo[12399]: pam_unix(sudo:session): session opened for user root by (uid=0) Feb 25 12:37:11 lt001 NetworkManager[709]: <info> [1645789031.8259] audit: op="connection-deactivate" uuid="9e6a7e66-3741-4d0c-b4c1-96edc5d329ab" name="example-Club" pid=10803 uid=1049601120 result="success" Feb 25 12:37:11 lt001 dbus-daemon[708]: [system] Activating via systemd: service name='org.freedesktop.nm_dispatcher' unit='dbus-org.freedesktop.nm-dispatcher.service' requested by ':1.10' (uid=0 pid=709 comm="/usr/sbin/NetworkManager --no-daemon " label="unconfined") Feb 25 12:37:11 lt001 systemd[1]: Starting Network Manager Script Dispatcher Service... Feb 25 12:37:11 lt001 dbus-daemon[708]: [system] Successfully activated service 'org.freedesktop.nm_dispatcher' Feb 25 12:37:11 lt001 systemd[1]: Started Network Manager Script Dispatcher Service. Feb 25 12:37:11 lt001 nm-openvpn[12387]: event_wait : Interrupted system call (code=4) Feb 25 12:37:11 lt001 nm-openvpn[12387]: SIGTERM[hard,] received, process exiting Feb 25 12:37:11 lt001 NetworkManager[709]: <warn> [1645789031.8444] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: VPN plugin: failed: connect-failed (1) Feb 25 12:37:11 lt001 NetworkManager[709]: <info> [1645789031.8445] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: VPN plugin: state changed: stopping (5) Feb 25 12:37:11 lt001 nm-dispatcher[13801]: run-parts: failed to stat component /etc/network/if-post-down.d/avahi-daemon: No such file or directory Feb 25 12:37:11 lt001 NetworkManager[709]: <info> [1645789031.8465] vpn-connection[0x564dc19e4310,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"example-Club",0]: VPN plugin: state changed: stopped (6) Feb 25 12:37:12 lt001 dbus-daemon[708]: [system] Activating via systemd: service name='org.freedesktop.PackageKit' unit='packagekit.service' requested by ':1.179' (uid=0 pid=14178 comm="/usr/bin/gdbus call --system --dest org.freedeskto" label="unconfined") Feb 25 12:37:12 lt001 systemd[1]: Starting PackageKit Daemon... Feb 25 12:37:12 lt001 PackageKit[14181]: daemon start Feb 25 12:37:12 lt001 dbus-daemon[708]: [system] Successfully activated service 'org.freedesktop.PackageKit' Feb 25 12:37:12 lt001 systemd[1]: Started PackageKit Daemon. Feb 25 12:37:15 lt001 sudo[12399]: pam_unix(sudo:session): session closed for user root Feb 25 12:37:22 lt001 systemd[1]: NetworkManager-dispatcher.service: Succeeded. -
@pixel24
Doesn't show really much at all. I assume, the "example-Club" is your replacement of the destination host name?However, as far as I know, the NetworkManager OpenVPN plugin doesn't like separated CA an client certs.
I only succeed with it by using encrypted pkcs12 file ("Password Protect Certificate" checked in the export utility and a password stated).
Then I downloaded the archive and extracted it on the client.
You may import the .ovpn file in NM, but then ensure the all the paths of CA, client cert and private key goes to the p12 file and enter the password for the p12. The TLS key has to be stated additionally on the security tab. -
@viragomann said in Can't get OpenVPN to work:
Doesn't show really much at all. I assume, the "example-Club" is your replacement of the destination host name?
Yes, I have replaced the real part of the name with example.
This log file was written when I tried to establish the VPN connection from the LAN.
I have just tried it again "from outside". I can get more information here:
Feb 25 12:55:08 lt001 NetworkManager[709]: <info> [1645790108.3077] audit: op="connection-activate" uuid="9e6a7e66-3741-4d0c-b4c1-96edc5d329ab" name="Example-Club" pid=10803 uid=1049601120 result="success" Feb 25 12:55:08 lt001 NetworkManager[709]: <info> [1645790108.3116] vpn-connection[0x564dc19e4520,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"Example-Club",0]: Started the VPN service, PID 15691 Feb 25 12:55:08 lt001 NetworkManager[709]: <info> [1645790108.3168] vpn-connection[0x564dc19e4520,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"Example-Club",0]: Saw the service appear; activating connection Feb 25 12:55:08 lt001 NetworkManager[709]: <info> [1645790108.3667] vpn-connection[0x564dc19e4520,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"Example-Club",0]: VPN plugin: state changed: starting (3) Feb 25 12:55:08 lt001 NetworkManager[709]: <info> [1645790108.3667] vpn-connection[0x564dc19e4520,9e6a7e66-3741-4d0c-b4c1-96edc5d329ab,"Example-Club",0]: VPN connection: (ConnectInteractive) reply received Feb 25 12:55:08 lt001 nm-openvpn[15701]: WARNING: file '/data01/Sicherheit/OVPN/Example-Club/gate01-UDP4-1194/gate01-UDP4-1194-tls.key' is group or others accessible Feb 25 12:55:08 lt001 nm-openvpn[15701]: OpenVPN 2.4.7 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Jul 19 2021 Feb 25 12:55:08 lt001 nm-openvpn[15701]: library versions: OpenSSL 1.1.1f 31 Mar 2020, LZO 2.10 Feb 25 12:55:08 lt001 nm-openvpn[15701]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 12:55:08 lt001 nm-openvpn[15701]: TCP/UDP: Preserving recently used remote address: [AF_INET]37.49.18.169:1194 Feb 25 12:55:08 lt001 nm-openvpn[15701]: UDPv4 link local: (not bound) Feb 25 12:55:08 lt001 nm-openvpn[15701]: UDPv4 link remote: [AF_INET]37.49.18.169:1194 Feb 25 12:55:08 lt001 nm-openvpn[15701]: NOTE: chroot will be delayed because of --client, --pull, or --up-delay Feb 25 12:55:08 lt001 nm-openvpn[15701]: NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay Feb 25 12:55:08 lt001 nm-openvpn[15701]: VERIFY ERROR: depth=2, error=unable to get issuer certificate: C=US, O=Internet Security Research Group, CN=ISRG Root X1 Feb 25 12:55:08 lt001 nm-openvpn[15701]: OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed Feb 25 12:55:08 lt001 nm-openvpn[15701]: TLS_ERROR: BIO read tls_read_plaintext error Feb 25 12:55:08 lt001 nm-openvpn[15701]: TLS Error: TLS object -> incoming plaintext read error Feb 25 12:55:08 lt001 nm-openvpn[15701]: TLS Error: TLS handshake failed Feb 25 12:55:08 lt001 nm-openvpn[15701]: SIGUSR1[soft,tls-error] received, process restarting Feb 25 12:55:13 lt001 nm-openvpn[15701]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Feb 25 12:55:13 lt001 nm-openvpn[15701]: TCP/UDP: Preserving recently used remote address: [AF_INET]37.49.18.169:1194 Feb 25 12:55:13 lt001 nm-openvpn[15701]: UDPv4 link local: (not bound) Feb 25 12:55:13 lt001 nm-openvpn[15701]: UDPv4 link remote: [AF_INET]37.49.18.169:1194 -
@pixel24
So the client cannot verify the issuer certificate.Are the server and client certs issued by an intermediate CA?
Did you provide the p12 file in the meantime?
It should include all needed certs.
If you use PEM style files, you have to combine CA and intermediate manually. -
@viragomann said in Can't get OpenVPN to work:
Are the server and client certs issued by an intermediate CA?
As far as I understand it, yes:
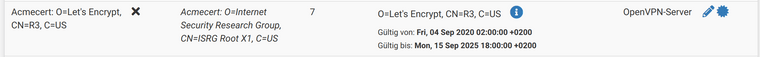
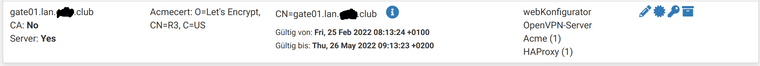
What surprises me is that the Client Export field says "No Cert":
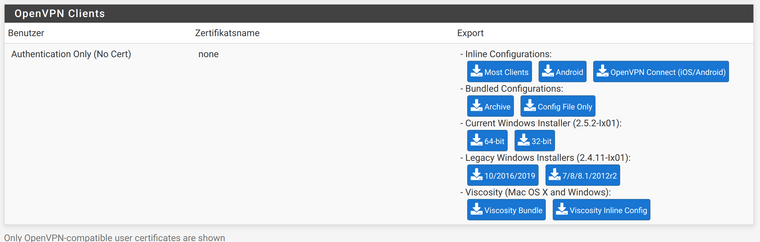
I download the bundle, unpack it:
Import it:
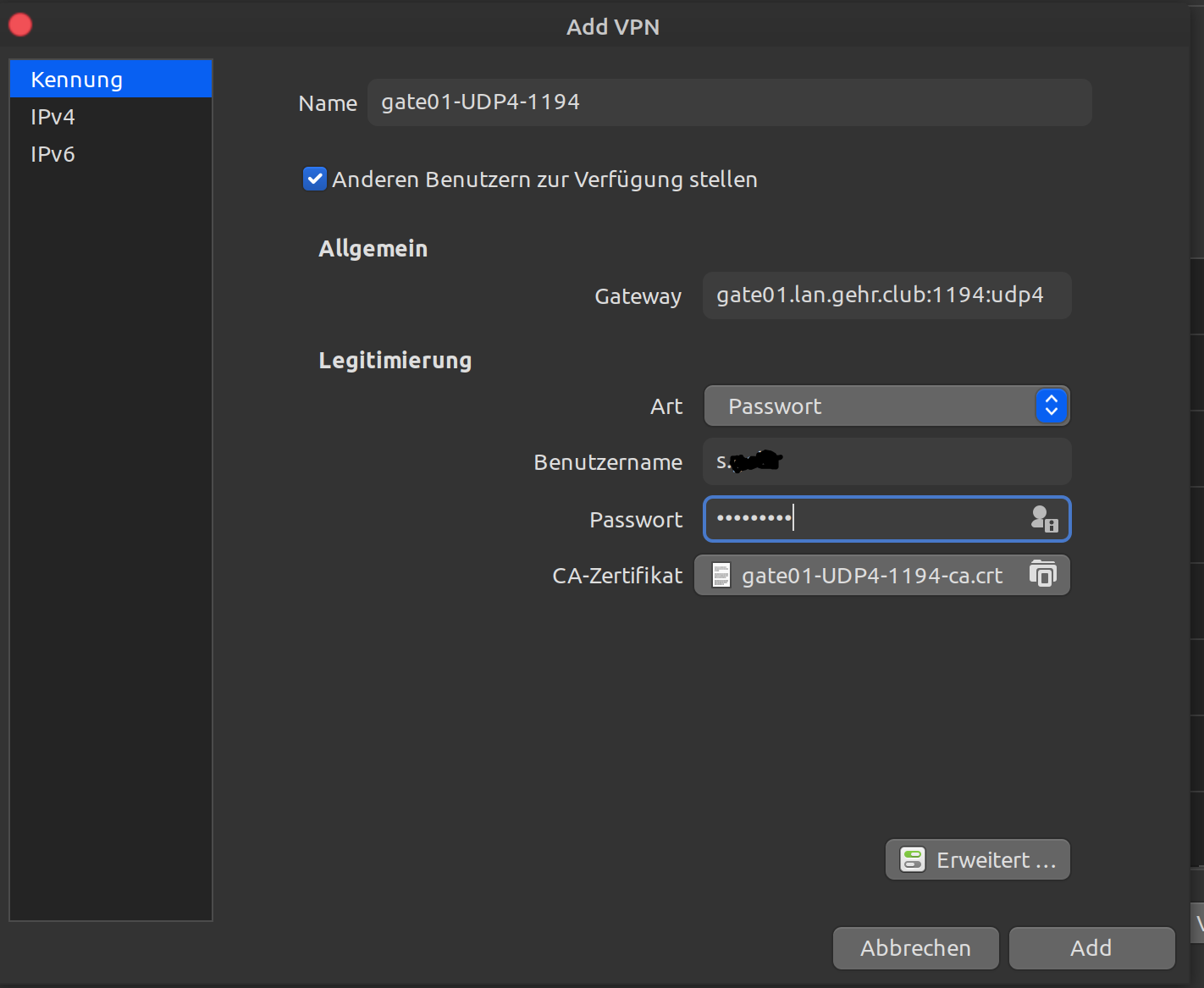
But the error remains the same
Feb 25 13:58:14 lt001 nm-openvpn[19759]: VERIFY ERROR: depth=1, error=unable to get issuer certificate: C=US, O=Let's Encrypt, CN=R3 Feb 25 13:58:14 lt001 nm-openvpn[19759]: OpenSSL: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed Feb 25 13:58:14 lt001 nm-openvpn[19759]: TLS_ERROR: BIO read tls_read_plaintext error Feb 25 13:58:14 lt001 nm-openvpn[19759]: TLS Error: TLS object -> incoming plaintext read error Feb 25 13:58:14 lt001 nm-openvpn[19759]: TLS Error: TLS handshake failed@viragomann said in Can't get OpenVPN to work:
Did you provide the p12 file in the meantime?
Where exactly do I do that?
@viragomann said in Can't get OpenVPN to work:
It should include all needed certs.
If you use PEM style files, you have to combine CA and intermediate manually.How exactly do I have to proceed here?
-
@pixel24 said in Can't get OpenVPN to work:
What surprises me is that the Client Export field says "No Cert":
This regards to the user cert.
So there might no client cert be assigned to that user.But not clear, how this should be accepted by the client. When you set up an SSL OpenVPN a client cert is required.
-
@pixel24
Just noticed that your server is in "user auth" mode. So it doesn't require any CA and cert at all.
But I'm wondering why it is providing the CA and server cert stuff in this mode.You have to set the server into SSL/TLS (+Auth) mode to use SSL certificates.
It should include all needed certs.
If you use PEM style files, you have to combine CA
and intermediate manually.How exactly do I have to proceed here?
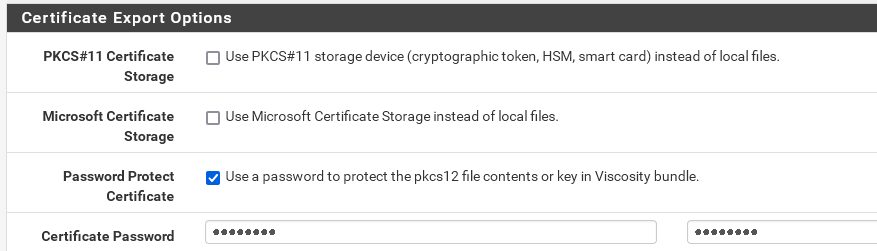
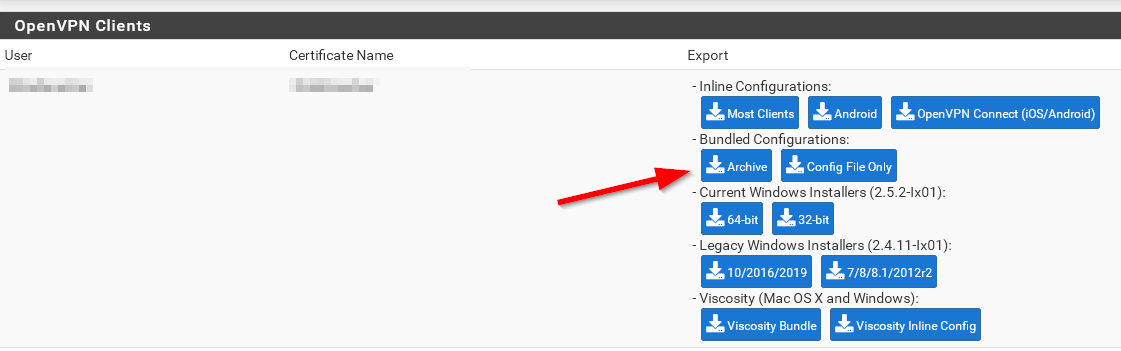
-
@viragomann said in Can't get OpenVPN to work:
Just noticed that your server is in "user auth" mode. So it doesn't require any CA and cert at all.
But I'm wondering why it is providing the CA and server cert stuff in this mode.
You have to set the server into SSL/TLS (+Auth) mode to use SSL certificates.That's how I've always done it so far and never had any problems. However, it was version 2.5. Now I have 2.6.
I have removed the access on the laptop again, changed the OpenVPN server to "SSL/TLS (+Auth) mode" and activated the password protection for thed pkcs12 file.
However, the option to download the package for the client is missing under "OpenVPNClient -> Export Utility".
-
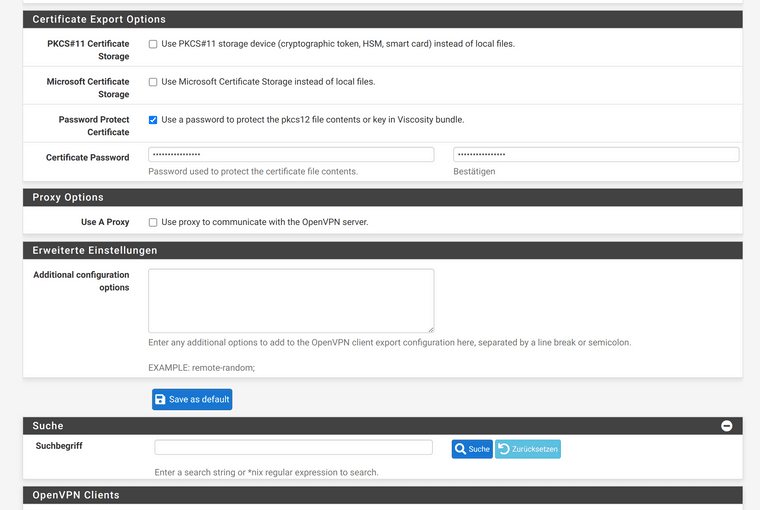
-
@pixel24 said in Can't get OpenVPN to work:
However, the option to download the package for the client is missing under "OpenVPNClient -> Export Utility".
This is only available if there is any user on the system who has assigned a certificate from the same CA as the selected server.
As you upper screeshot shows you're using an external user database. But I don't know how to assign a user certs in this case.
-
@viragomann I have specified the Let's Encrypt CA and the real certificate of the host in the OpenVPN server. This does not work although the certificate has been signed and is valid.
I have now set up an internal CA for OpenVPN again. Auth: User & Pass. Package imported on the client.
Works.
-
@pixel24 said in Can't get OpenVPN to work:
I have specified the Let's Encrypt CA and the real certificate of the host in the OpenVPN server.
No, not this.
The client needs both, the CA cert and the intermediate cert to verify the server certificate, as far as I know. That's what the client error log hints to me.So when you use p12 file both should be included. When using PEM file (crt) you can simply bundle both with an text editor.
-
@pixel24 said in Can't get OpenVPN to work:
OpenVPN 2.4.7
pfSense uses OpenVPN 2.5.4
I won't say : it couldn't work.
I will say : only experts will try to mix 2.5.x series with the 2.4.x series ;)Btw : no need to use a certificate from Letsencrypt.
See the Netgate channel on Youtube, the official OpenVPN video's. These videos are old, but still very valid. -
@gertjan said in Can't get OpenVPN to work:
pfSense uses OpenVPN 2.5.4
I won't say : it couldn't work.
I will say : only experts will try to mix 2.5.x series with the 2.4.x series ;)So I'm an expert, obviously.

We never had issues here with OpenVPN 2.5.2 on pfSense and 2.4.x and 2.5.x on Windows and 2.4.x Linux clients.
-
@viragomann said in Can't get OpenVPN to work:
obviously
Very possible

I guess you've been cheating, that is, reading the OpenVPN release notes so you knew what 2.4.x option (server or client) can be used with a 2.5.x server or client.
-
That setting doesn't work for me in the issue I've been having.