I can't get VLANs to work / No DHCP
-
@robh-0 did you take your switch out of the equation? And just connect a box that you know you can send out a tag on - you can view via sniff on the machine that your actually sending a tag..
-
@robh-0 well trying to get esxi 7 running on my old HP N40L ;) I got it up and running after using allowLegacyCPU=true
all was looking good, I was going to be able to run through using vlans.. But ran into a snag where my VM would boot, but whenever I would try to connect to it via console or VMRC it would crash.. So can not get a vm running to test anything with.. Let alone pfsense..
So installing 6.7 now - same no longer cpu supported. But hoping I can get vm running, networking shouldn't be that different, and same sort of settings for vswitches and port groups.. And 6.7 supports freebsd 12..
I won't have any hardware to play with esxi that is somewhat current until I get my new work laptop, then my old laptop I get to keep and can run esxi on that..
-
@robh-0 Ok I had to go out - just got back... So I booted esxi 6.7 update3, and set my allowLegacyCPU=true. This seems seems to be working, and remote console working - so got a ubuntu vm installed. I will have to do some digging into why on version 7, whenever I would try and launch a console it would crash the vm..
Anyhoo - so got ubuntu 20.04.4 server install, min install no gui just console. So I could do some testing real quick
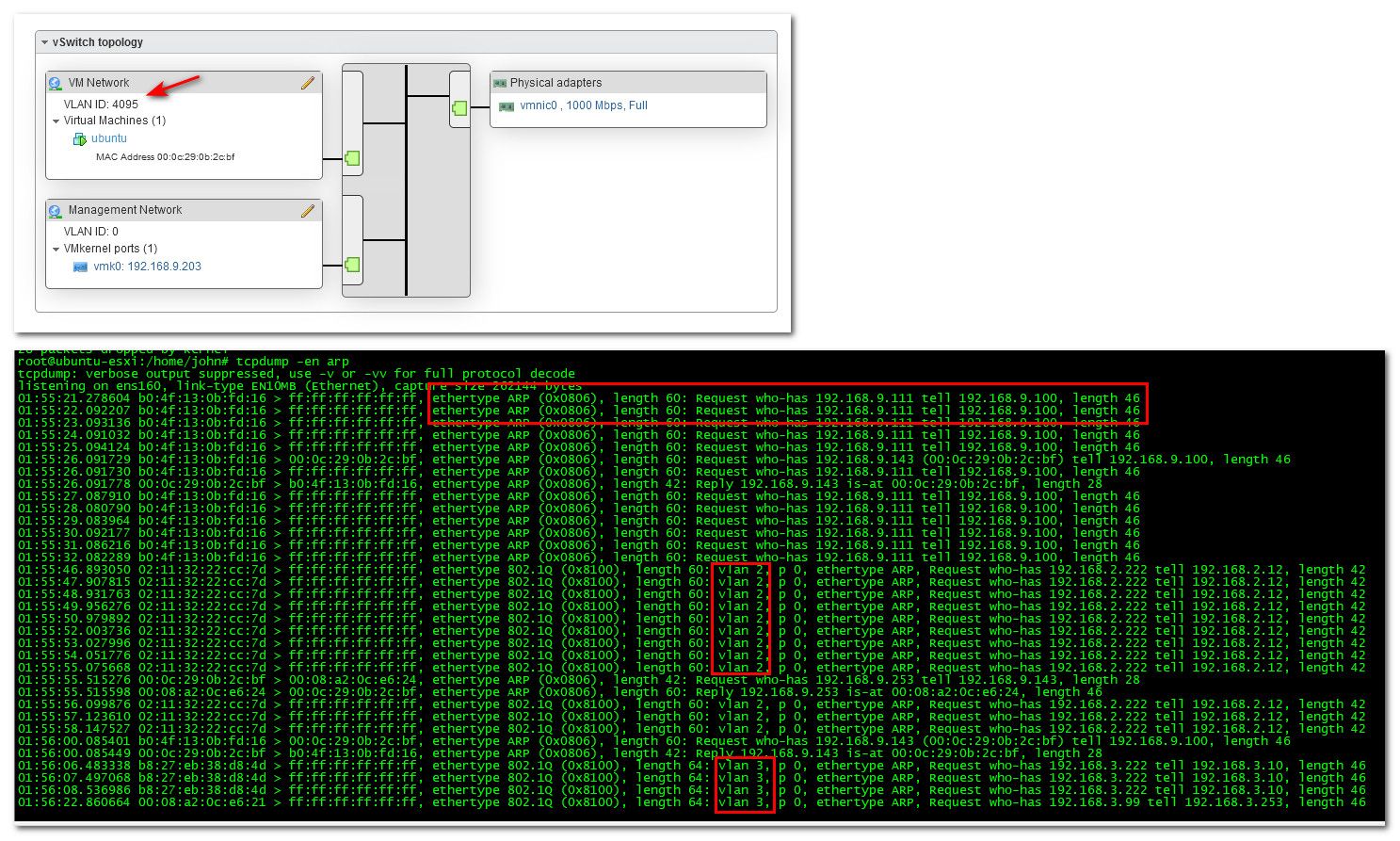
So simple test... I set on my switch port that connects to my esxi host to pass my untagged vlan 9, which is 192.168.9/24 and also pass tagged vlan 2 and vlan 3, which are 192.168.2/24 and 192.168.3/24
Now on the VM that I connected to a port group that is set to vlan 4095, did simple sniff with -e to show the vlans.. Then forced some arps on boxes on those vlans to something that doesn't exist so I could see the arps.. As you see the vm sees the untagged arps on 192.168.9/24 and also when I arp for something on tagged network 2 and 3, it sees those arps as well. So esxi is passing tagged traffic through this port group without stripping it.
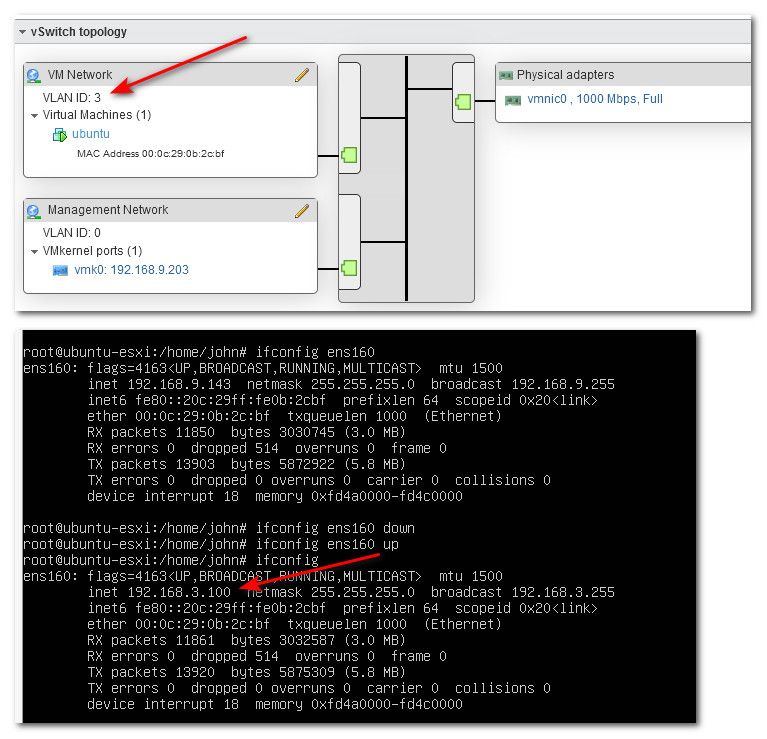
Now if I change the port group to be vlan 3, and then have the vm get a new dhcp address via bring the interface down and then back up - you see it gets an address from my vlan 3 dhcpd.
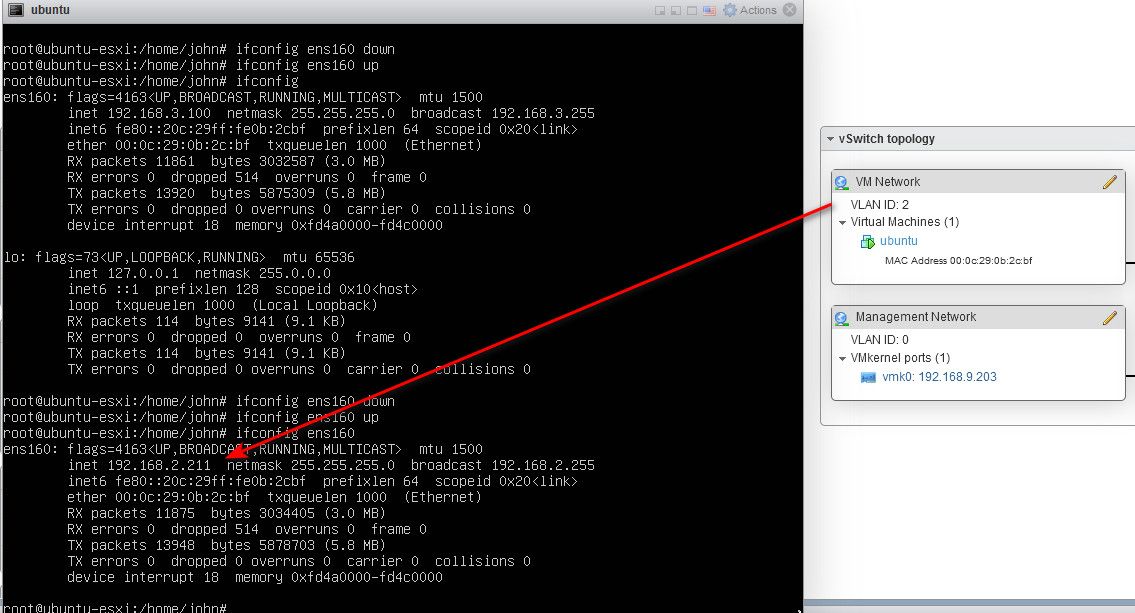
Then I can do the same thing for vlan 2
-
@johnpoz Hey thanks for all of this!
Unfortunately, my father's health took a nosedive over the weekend, so I haven't had time to do anything fun. We are heading up to his place tonight to be there for several days. I'm keeping a link to this so that I can get back to it eventually, but for now it's probably going to be at least a week until I get back to it.
-
@robh-0 no problem - hope your father is ok.. Thanks for chiming in though.. Was wondering where you had gone.
-
@johnpoz The new 4 port Intel NIC just arrived, so when I get back home I'm going to try going physical on that i3-2100 system I told you about. Should be a breeze. If nothing else, I can get that going to cover for my failing USG while I figure out the VM.
-
@johnpoz Well, it was a fun ride getting here, but I'm up and running on physical. My new NIC arrived as mentioned, and when I put it in my spare PC, it did not work. I tried everything I could think of, but nothing. So I decided to pull a NIC from my VMWare host, an IDENTICAL NIC, and it worked. So I put the non-working NIC in the VMWare host, and IT WORKS. So go figure, just my luck.
I set up a new instance of pfSense on the physical box, set up the VLAN in the firewall, and BINGO, the same VLANs on the switches and all are working. DHCP works, it all works. So I have no idea right now what is causing the VLANs to not work in VMWare, but since this physical is working and it cost me a whopping $32 for the 4 port Intel NIC, I'm just going to run like this. It's fine.
Thanks for all the help trying to get me up and running in VMWare, I really do appreciate it. I am going to keep a copy of this link in the event I want to go back and try again, but for now I'm good on physical. This old i3 2100 draws very little power, and I have a very efficient Seasonic power supply in it, so there's really not a huge push to sit and have to work on the VM right now, especially with all I have going on with my father.
-
@robh-0 I've only skimmed this thread while trying to solve my own obscure problems (tl;dr), but when I ran pfSense under ESXi, I passed all VLANs through from the physical world to the pfSense VM so that from pfSense's point of view I just had one network interface and then defined whatever VLANs I needed within pfSense. It met my needs; you may be trying to do something similar.
The port(s) on the physical switch: I had 6-8 different VLANS defined and in use for different purposes. All of the defined VLANs were tagged on the port(s) connected to the ESXi server.
ESXi:
Virtual Switch/port groups:
If I had a (non-pfSense) virtual machine that needed access to any given LAN, I had a port group defined for that particular VLAN (1-4094).
For a pfSense virtual machine, I had a port group defined for VLAN 4095 so that all VLANs would be passed through to pfSense in the VM. I also needed to enable Promiscuous Mode for ONLY this VLAN 4095 port group.pfSense virtual machine:
I configured the pfSense virtual machine to only have one virtual NIC, which was mapped to the VLAN4095 port group. Within pfSense, I then had only one network interface, but I was able to add/remove VLANs as needed to match the physical network's VLAN config.Promiscuous Mode on your VLAN4095 port group may be what you're missing. It seems I needed to enable that, as I recall. HTH.
-
UniFi needs to be aware of the VLAN's that are set in pfSENSE and ESXi in order to pass this traffic at all. Setting UniFi Switch Ports to "Trunk/All" is not enough.
Hi, I notice this is old and unresolved. I found this while having a similar issue with some VLANs working and one specific one not.
I have pfSENSE installed on a physical box with an Intel 4 Port NIC. 2 UniFi Switches and a Cloud Key. My issue was actually with the UniFi configuration. It's good that you have all switch ports set as Trunk/All, though you need to configure each VLAN as a "Network" in the UniFi controller.
tl:dr I had 2 VLANS working and 1 not working because I had forgotten to configure the network on the UniFi Switch's controller.
-
@cneep said in I can't get VLANs to work / No DHCP:
Virtual Switch/port groups:
If I had a (non-pfSense) virtual machine that needed access to any given LAN, I had a port group defined for that particular VLAN (1-4094).
For a pfSense virtual machine, I had a port group defined for VLAN 4095 so that all VLANs would be passed through to pfSense in the VM. I also needed to enable Promiscuous Mode for ONLY this VLAN 4095 port group.Thanks. Been trying to get this to work for past 2 days, and finally started looking here and found this!