Portforwarding to captive portal
-
@benrofu did you disable the block rfc1918 on the wan... You could create all the port forwards you want, but since your coming from a rfc1918 address 192.168.1.218 they are not going to work.
-
@johnpoz
Hello, and thanks for reply.Both: Block private networks and loopback addresses, and Block bogon networks are unchecked on wan interface.
I suppose this is what you mean by block rfc1918 on wan ?
-
@benrofu Well then do a simple sniff and see what is going on..
https://docs.netgate.com/pfsense/en/latest/troubleshooting/nat.html#port-forward-troubleshooting
Lets see your port forward and your rules..
Nat reflection is pure nat
What would that have to do with accessing it from the wan network? As to captive portal, you most likely would need to make sure the destination your trying to go to 10.0.200.2 is allowed and doesn't have to auth to the captive portal.
Does your AP even have a gateway set? pointing to 10.0.200.1 ? If not then no you wouldn't be able to get to it from another network. Many AP or wifi router being used as AP do not have ability to set gateway, etc. If so then you would need to do souce natting so your AP thinks the traffic is coming from pfsense IP in that network 10.0.200.1
-
@johnpoz
I cant see why a gateway should matter on the AP ?
If i go to diagnostic- test port is ok when i test 83 on 10.0.200.2The AP is a linksys router , with static ip, no dhcp ( dhcp in captive portal).
Cable from opt1 is connected to lan on AP, not wan.Here you can see my settings in NAT and Firewall rules
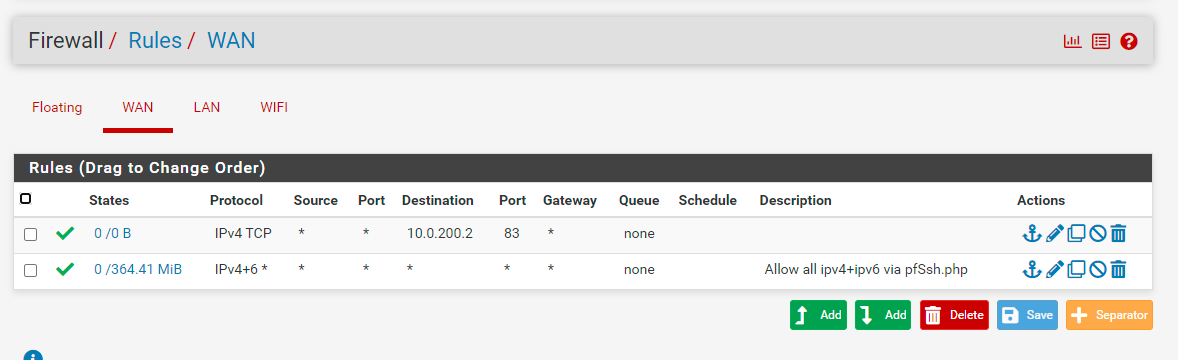
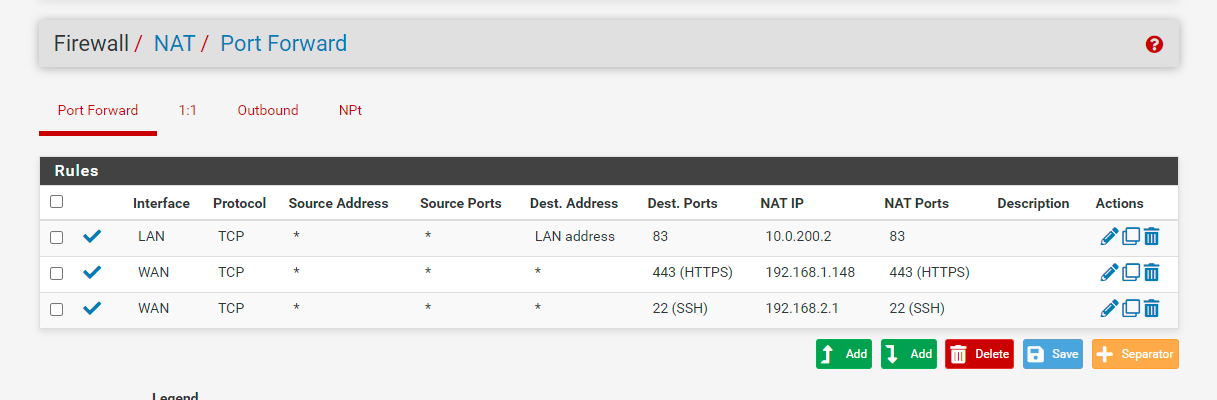
-
@benrofu said in Portforwarding to captive portal:
@johnpoz
I cant see why a gateway should matter on the AP ?
If i go to diagnostic- test port is ok when i test 83 on 10.0.200.2The AP is a linksys router , with static ip, no dhcp ( dhcp in captive portal).
Cable from opt1 is connected to lan on AP, not wan.Here you can see my settings in NAT and Firewall rules



Im sorry, first NAT was wrong with LAN ADDRESS destination, that was just me testing something else. Here is my correct nat settings with wan address.
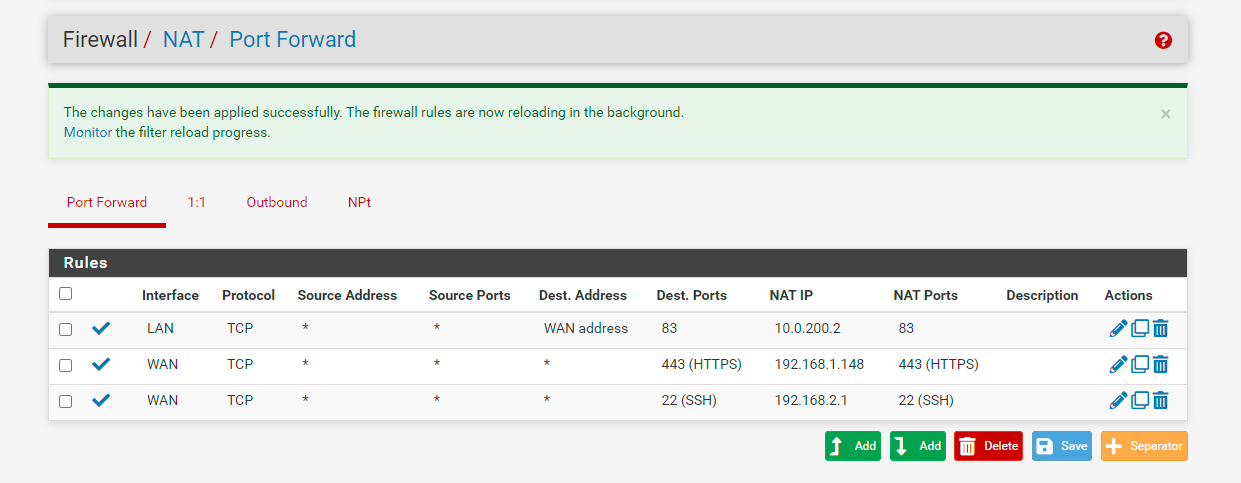
-
@benrofu said in Portforwarding to captive portal:
I cant see why a gateway should matter on the AP ?
How exactly do you think it would get back to this 192.168.1 network from its 10.0.200 network??
How would this ever work?
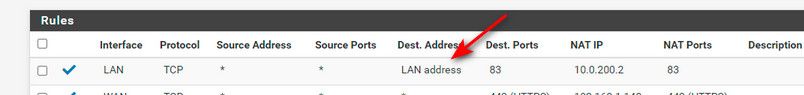
If your on your WAN network the destination would be pfsense wan address..
That is better your new port forward - but AGAIN how would a device without a gateway to be able to get off its own network answer an IP from some other network... If you can not put a gateway on the lan interface on your wifi router your using as AP, then you will have to source nat the traffic so its looking like it came from pfsense 10.0.200.1 address - which is the same network your AP is on, so he doesn't need a gateway.
edit: This still wrong
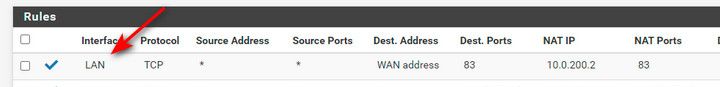
How would that work - your coming from your wan network... The interface your port forward would be on would be your WAN... On your wan you would hit your wan address on the port, and it would forward you to the 10.0.200.2 address..
edit2: Why do you have a any any rule on your wan interface??? Even though your behind a nat with a rfc1918 wan network - its a BAD habit to get into to think an any rule on your "wan" is ok..
-
@johnpoz
Yes, LAN changed to WAN interface, but have tried so many diffrent rules now.I am new to pfsense, earlier i used a router with gargoyle (openwrt). No problems with NAT rules then.
This is the router i am using as AP now.
I dont see how i need a gateway on the router as long as it now just works like a switch with a webserver on port 83.The NAT should just port traffic from wan port to opt with spesified destination 10.0.200.2 (port 83). I cant see why it should be a problem. I have watced a lot of youtube videos for portforwarding and it should be quite easy!?
How do you suggest i set up things? I assume it does not matter if i use the LAN insted of OPT1 ? I use the netgatebox only for captive portal.
-
@johnpoz said in Portforwarding to captive portal:
@benrofu said in Portforwarding to captive portal:
I cant see why a gateway should matter on the AP ?
How exactly do you think it would get back to this 192.168.1 network from its 10.0.200 network??
How would this ever work?

If your on your WAN network the destination would be pfsense wan address..
That is better your new port forward - but AGAIN how would a device without a gateway to be able to get off its own network answer an IP from some other network... If you can not put a gateway on the lan interface on your wifi router your using as AP, then you will have to source nat the traffic so its looking like it came from pfsense 10.0.200.1 address - which is the same network your AP is on, so he doesn't need a gateway.
edit: This still wrong

How would that work - your coming from your wan network... The interface your port forward would be on would be your WAN... On your wan you would hit your wan address on the port, and it would forward you to the 10.0.200.2 address..
edit2: Why do you have a any any rule on your wan interface??? Even though your behind a nat with a rfc1918 wan network - its a BAD habit to get into to think an any rule on your "wan" is ok..
Do i not need to have a rule on wan to access webinterface for pfsense when the netgate box is connected to my lan with wan port?
-
@benrofu said in Portforwarding to captive portal:
but have tried so many diffrent rules now.
That is a problem - your just clicking shit hoping something works without understand how it works..
Do i not need to have a rule on wan to access webinterface for pfsense when the netgate box is connected to my lan with wan port?
Yes create the rule for your wan address an what port your gui is set to and or ssh, etc.
edit: btw your whole setup seems counter productive - why are you trying to manage stuff from the "wan" of pfsense? You and your networks should be behind pfsense.. Why do you have anything on pfsense wan - this should be the internet, or worse case if your modem/gateway devices does not allow bridge mode, etc. then sure behind a double nat for pfsense, but little reason that anything should be on the "wan" of pfsense other than your isp router so pfsense can get to the internet. No port forwards need now to get to anything on your other networks - just firewall rules to allow the traffic.
-
@johnpoz
Hello
You are probably right.
The reason i am using the wan port, is that the pfsense box is just added to the existing network and not using it as a firewall but captive server. There are diffrent servers running on the lan and i am not familiar with pfsense yet and, i suppose i get lot of trouble if i connect the box between ISP router and LAN. There was a lot of work and studying when the isp router was setup with openvpn and forwarding to diffrent servers. I assume if i connect pfsense in between i would need to forward everything through the pfsense.Would it be better if i connect my local network to the LAN port and use it as a gateway for opt1 ? leaving wan disconnected?