2.6 cant get openvpn working
-
@gertjan i did follow your recommended instruction at pfsense, ended with the same problem. I couldn't find anything different in setup between my original and your instructions.
-
@honeybadger said in 2.6 cant get openvpn working:
same problem
You mean : you used Configuring OpenVPN Remote Access in pfSense Software and the instructions in that video didn't work right away ?
There are some requirements that are not mentioned :
The latest pfSense version.
Default pfSense setup (no fancy routing, no VLAN, no other packages except the pfSEnse "openvpn-client-export" package.
A OpenVPN client version that uses 2.5.x (pfSense 2.6.0 is using OenVPN 2.5.4)Anyway, I'm curious now. I"ll blow away my settings @home - reboot to default, assign interfaces, change the password and stop there. I'll play back the video.
I'll be using this client OpenVPN Connect Phone or PC version.Since Mars 2020, thousands are using OpenVPN as we all had to work from home.
-
@gertjan excellent!
Thankyou for your time!
I look forward to your reply!
Thank you thank you thank you!
-
@gertjan okay, deleated all users and server and user certs.
Followed: https://www.wundertech.net/how-to-set-up-openvpn-on-pfsense
Valid as of February.Server: Mar 19 19:50:19 openvpn 24728 TLS Error: cannot locate HMAC in incoming packet from [AF_INET6]::ffff:192.168.1.172:50463
Mar 19 19:50:02 openvpn 24728 TLS Error: cannot locate HMAC in incoming packet from [AF_INET6]::ffff:192.168.1.172:50463
Mar 19 19:49:55 openvpn 24728 TLS Error: cannot locate HMAC in incoming packet from [AF_INET6]::ffff:192.168.1.172:50463
Mar 19 19:49:51 openvpn 24728 TLS Error: cannot locate HMAC in incoming packet from [AF_INET6]::ffff:192.168.1.172:50463
Mar 19 19:49:48 openvpn 24728 TLS Error: cannot locate HMAC in incoming packet from [AF_INET6]::ffff:192.168.1.172:50463
Mar 19 19:49:09 openvpn 24728 192.168.1.178:46841 TLS Error: TLS handshake failed
Mar 19 19:49:09 openvpn 24728 192.168.1.178:46841 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 19 19:48:59 openvpn 24728 192.168.1.178:45857 TLS Error: TLS handshake failed
Mar 19 19:48:59 openvpn 24728 192.168.1.178:45857 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 19 19:48:49 openvpn 24728 192.168.1.178:59422 TLS Error: TLS handshake failed
Mar 19 19:48:49 openvpn 24728 192.168.1.178:59422 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 19 19:48:39 openvpn 24728 192.168.1.178:41320 TLS Error: TLS handshake failed
Mar 19 19:48:39 openvpn 24728 192.168.1.178:41320 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 19 19:48:30 openvpn 24728 192.168.1.178:54456 TLS Error: TLS handshake failed
Mar 19 19:48:30 openvpn 24728 192.168.1.178:54456 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 19 19:48:19 openvpn 24728 192.168.1.178:33735 TLS Error: TLS handshake failed
Mar 19 19:48:19 openvpn 24728 192.168.1.178:33735 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
Mar 19 19:48:18 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:18 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:17 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:17 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:16 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:16 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:15 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:15 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:14 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:14 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:13 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:13 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:12 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:12 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:11 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:11 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:10 openvpn 24728 192.168.1.178:46841 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:46841
Mar 19 19:48:10 openvpn 24728 192.168.1.178:46841 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744490) 2022-03-19 19:48:10 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:08 openvpn 24728 192.168.1.178:45857 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:45857
Mar 19 19:48:08 openvpn 24728 192.168.1.178:45857 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744480) 2022-03-19 19:48:00 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:07 openvpn 24728 192.168.1.178:45857 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:45857
Mar 19 19:48:07 openvpn 24728 192.168.1.178:45857 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744480) 2022-03-19 19:48:00 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:06 openvpn 24728 192.168.1.178:45857 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:45857
Mar 19 19:48:06 openvpn 24728 192.168.1.178:45857 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744480) 2022-03-19 19:48:00 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:05 openvpn 24728 192.168.1.178:45857 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:45857
Mar 19 19:48:05 openvpn 24728 192.168.1.178:45857 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744480) 2022-03-19 19:48:00 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:04 openvpn 24728 192.168.1.178:45857 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:45857
Mar 19 19:48:04 openvpn 24728 192.168.1.178:45857 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #1 / time = (1647744480) 2022-03-19 19:48:00 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings
Mar 19 19:48:03 openvpn 24728 192.168.1.178:45857 TLS Error: incoming packet authentication failed from [AF_INET6]::ffff:192.168.1.178:45857Help please?
-
On the way - as soon as I get @home, i'll do a test setup.
Your are testing with 2 IP's on the same network. 192.168.1.178 to 192.168.1.172, I've never tested that, and if it would connect, it would probably still fail.
The situation should be : an openvpn server listening on the WAN port. This WAN port could be RFC1918 and you could have an upstream "ISP" router with the "UDP 1194" port natted to pfSense.
Use your phone with the data carrier (3G/4G/LTE/...) , not the Wifi (!) so it use an arbitrary 'outside' IP, not some local RFC1918.And again :
openvpn TLS Error: cannot locate HMAC in incoming packet from
shows many examples saying just one thing : HMAC on server and client are not the same.
Also : Your OpenCVPN server version is 2.5.4 - what are you using as a client - and what version ?
Just to be sure : check your NTP setup on all devices. Time should be the same, like within a second or so.
Post your openvpn server config file ( Folder /var/etc/openvpn/server1 - the config.opvn file)
How did you create the client config file ?
No client override instruction ? ( here : VPN > OpenVPN > Client Specific Overrides )What have you checked on the VPN > OpenVPN > Client Export Utility page ?
-
@gertjan i created with the openvpn export wizard.
Latest android openvpn client and latest open wizard verson 1.6_4.
My pfsense is 2.6.0
Android client is 3.2.5(7182)
I looked in /var/etc/openvpn/server1 butdont see a config file. (ovpn)
No overridesThanks for the help
-
@honeybadger said in 2.6 cant get openvpn working:
I looked in /var/etc/openvpn/server1 butdont see a config file. (ovpn)
or server2 - or 3 etc - depedning on the number of openvpn servers you have (had) set up :
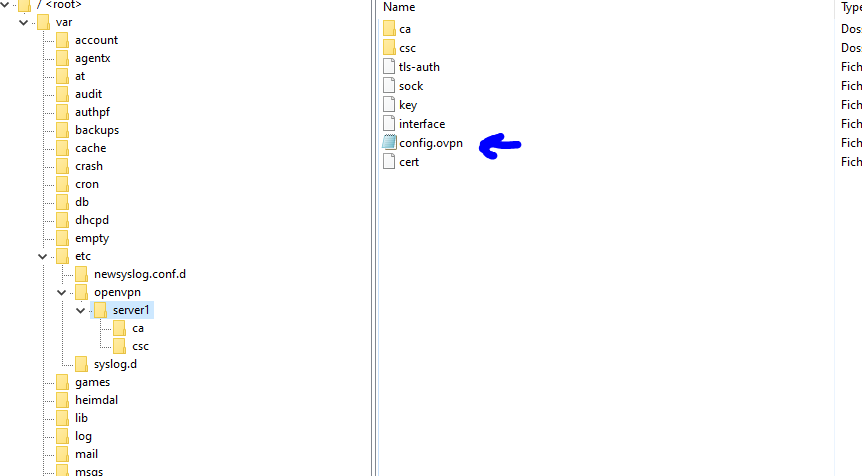
a config.ovpn file must exist, otherwise the openvpn server can't run.
I've just created my home openvpn server according to the Netgate video.
My tunnel network is 192.168.80.0/24
I use only IPv4.What I did that not in the video :
I had to port NAT my ISP router : port 1194 UDP => to my pfSense.
I assigned a OpenVPNserver as an interface :
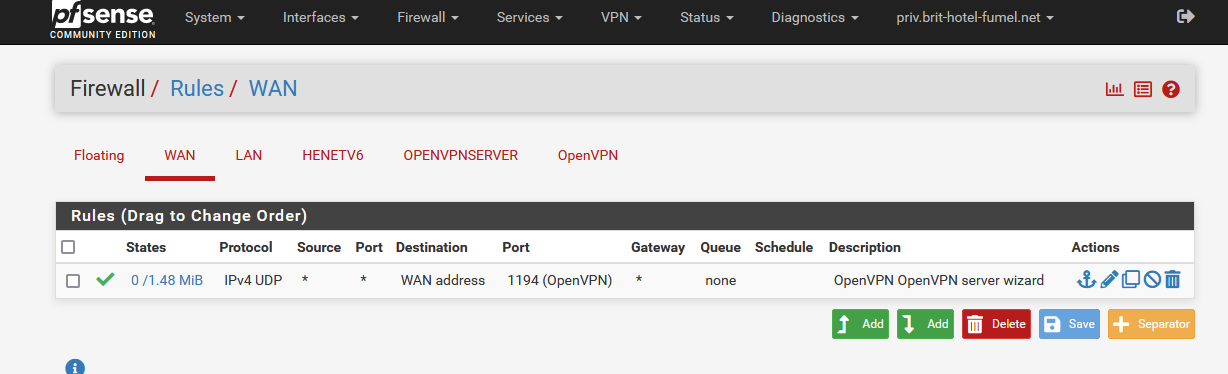
and I moved the Wizard generated firewall rule from the OpenVPN to the new OPENVPNSERVER tab :
I opened the resolver settings page, saw that in the incoming and outgoing connections my new OPENVPNSERVER was listed among the others.
I restarted the Resolver - now it also listens on the OpenVPN network.I also visited Services > NTP > Settings and added OPENVPNSERVER to the "Interfaces" box so my openvpn clients can connect a NTP source.
I don't use "User auth", but TLS only, so without user/password :
so I added a user called 'vpn' with a cert based on the OpenVPN server cert :
(on the user Manager page : )
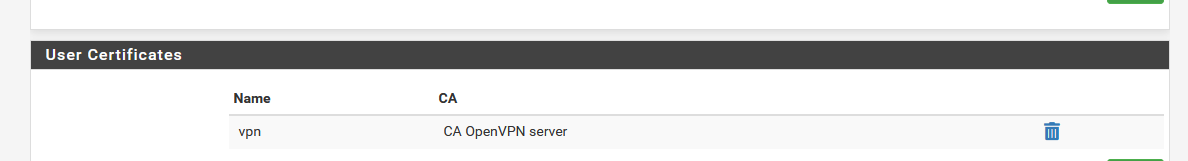
I installed the OpenVPN export package, and saw my openvpn user 'vpn' listed :
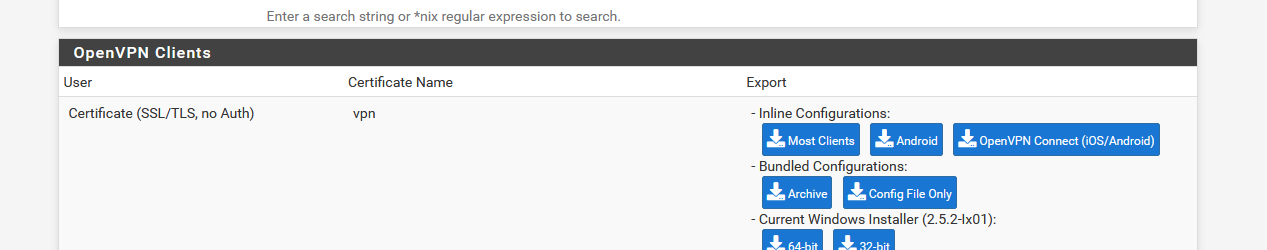
Exported (dwonloaded) the "OpenVPN Connect (OS/Android) openvpn client config file.
Mailed the client config myself, imported it into my iPhone.
I also double checked that the DDNS URL that points to my WAN IP is correct.
I connected just fine.
No errors in the OpenVPN server log, except the two classic wartnings :WARNING: 'keysize' is used inconsistently, local='keysize 256', remote='keysize 128' WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1569', remote='link-mtu 1553'No issues on the client side.
I could visit the pfSense WebGUI, and visit any other web server on my LAN (10.0.0.0/24) and whatever Internet site, like https://forum.netgate.com.Extra OpenVPN server settings :
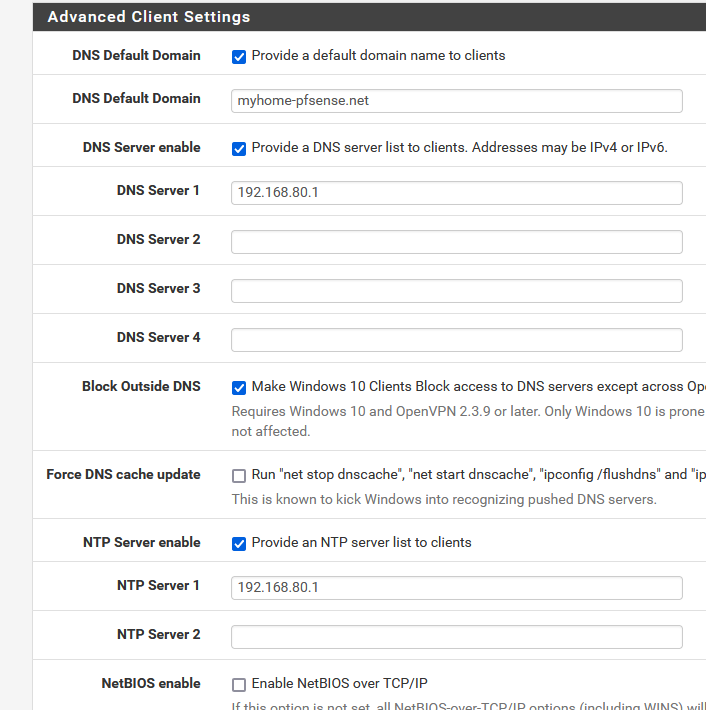
As said earlier, I use the OpenCONNECT app ( made by the OpenVPN authors).
Its compatible with the OpenServer code pfSense uses (version 2.5.4).
I did not see time or 'replay' issues, neither HMAC errors.
I de activated the Wifi on my phone, so I was really accessing the OpenVPN server from the Internet.
-
@gertjan not meaning to argue. In my /var/etc/openvpn/server1 (only server1 exists) are the directories csc and ca and that is it. I am running pfsense on a Netgate 2440 appliance. Maybe 2.6 didn't install properly? It said it did but it's not been able to run openvpn since upgrading.
You're alot more nuts and bolts aware than me.
Last time i set up openvpn, about 2.4 pfsense version. All i had to do was go to vpn/openvpn/wizards, set up server cert, go to user manager and set up a client with user cert and use the export too to send a archive of the 3 files to myphone, tablet, or laptop and if just worked, took about 10 mins.
Can't get it working now.
The config.ovpn was missibg because i deleted everything, i went though and reinstalled (wizard methodl.
Here's my fresh config.ovpn file:
ovpns1
verb 1
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
auth SHA256
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
local 184.103.145.195
tls-server
server 192.168.200.0 255.255.255.0
client-config-dir /var/etc/openvpn/server1/csc
username-as-common-name
plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'OpenVPN_CA' 1"
lport 1194
management /var/etc/openvpn/server1/sock unix
max-clients 10
push "route 192.168.1.0 255.255.255.0"
capath /var/etc/openvpn/server1/ca
cert /var/etc/openvpn/server1/cert
key /var/etc/openvpn/server1/key
dh /etc/dh-parameters.4096
tls-auth /var/etc/openvpn/server1/tls-auth 0
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
allow-compression no
persist-remote-ip
float
topology subnet
explicit-exit-notify 1
inactive 300Now when i try to export I get: Could not locate the CA reference for the server certificate.
Failed to export config files!.I checked my server cert is openvpn_ca.
Looks right in server and client setups
-
@honeybadger said in 2.6 cant get openvpn working:
not meaning to argue. In my /var/etc/openvpn/server1 (only server1 exists) are the directories csc and ca and that is it. I am running pfsense on a Netgate 2440
Something is running, as you showed the log.
You use a Netgate appliance, not me. Normally, that shouldn't differ - but doesn't your pfSense ( should ?) uses something like pfSense 22.x ?Open a console or SSH access and run :
ps ax | grep openvpn
You'll see a line like :4000 - Ss 0:00.33 /usr/local/sbin/openvpn --config /var/etc/openvpn/server1/config.ovpnThat's a way to determine where the config file is located.
Left is my config file - right is yours :
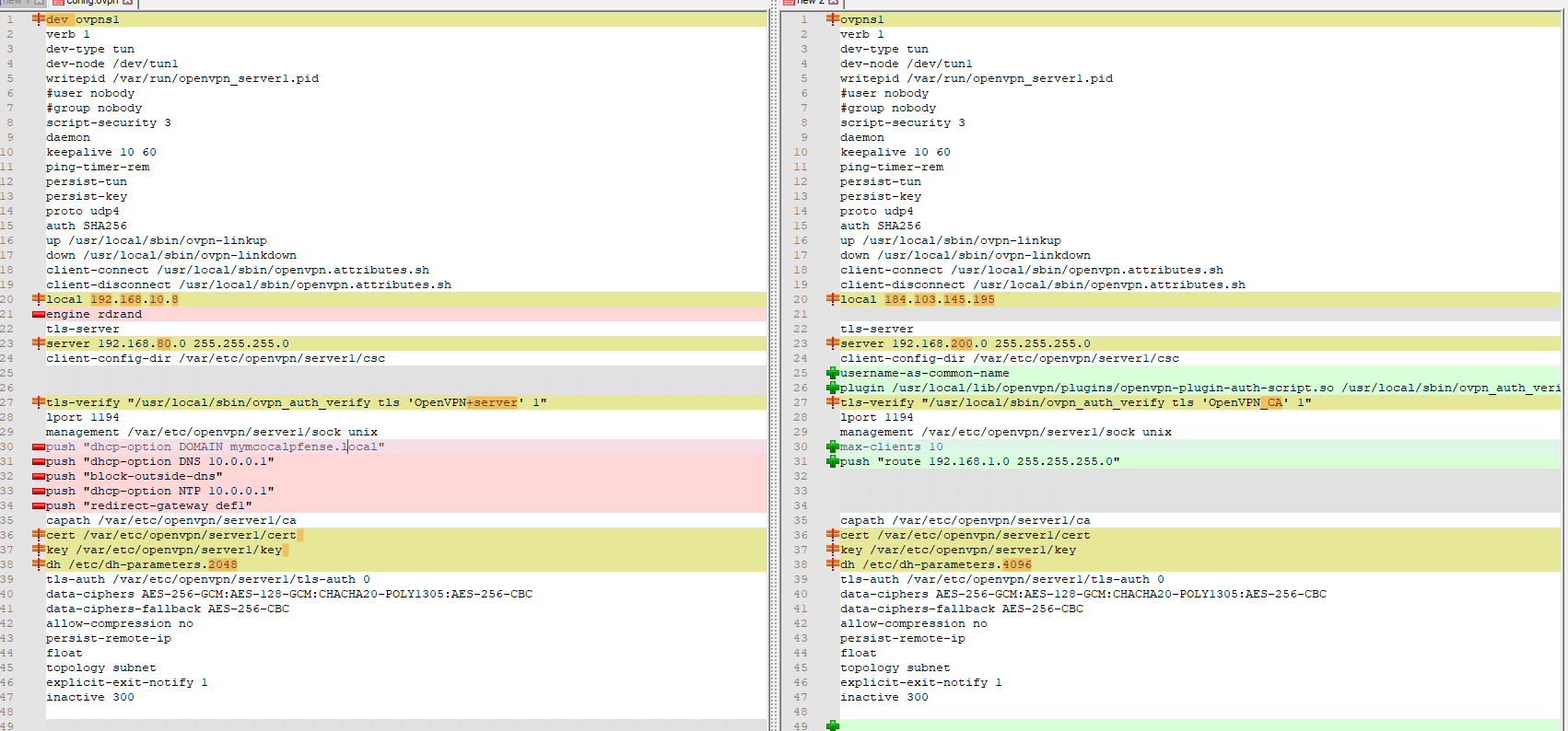
The first line :
I have dev ovpns1, you doesn't have 'dev' in front - - not important ?
The 'local' is ok, these are our WAN IPs - not important
I have the AES-NI Intel engine activate - not important
My tunnel network is 192.168.80.0/24 - yours is 192.168.200.0/24 - that's ok.
The TLS-verify are identical except the CA cert name : strange : Mine use the OpenVPN server cert from the Certificate page. Do you use somehow ( ? ) the cert from the CA (first) page ?I have this :
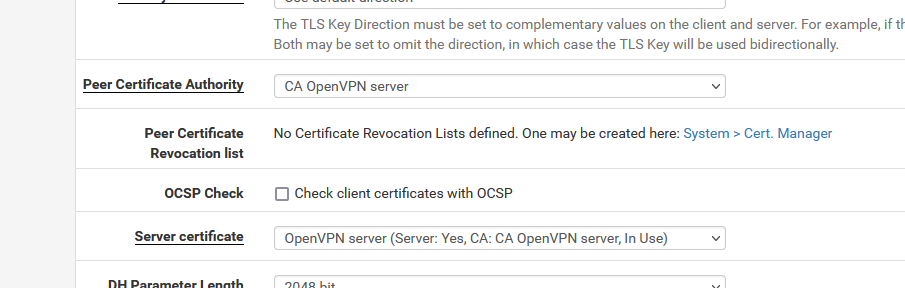
Where "CA OpenVPN server" is on the CA page.
Server certificate, I called it "OpenVPN server" is on the Certificate page.You limit the number of clients, i don't - not important
I have checked :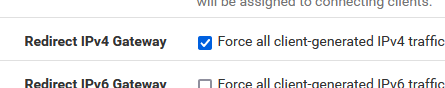
so that explains my "push "redirect-gateway def1"
I don't push routes - probably not important.
On the other hand, I push a lot of other image, as said above - - not important - that said, pushing a working DNS, our Resolver, 10.0.0.1 is my LAN, seems important to me.
I could also be using 192.168.80.1 as I instantiated the OpenVPN interface and now the resolver is also listening on 192.168.80.1.
dh /etc/dh-parameters.2048 or 4096 -not importantBtw : I don't know what this is :
username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYWwgRGF0YWJhc2U= false server1 1194Is that the extra stuff we have if we use a Netgate device ? Dono.
What I think : the issue is your on the client side the app used.
@honeybadger said in 2.6 cant get openvpn working:
Now when i try to export I get: Could not locate the CA reference for the server certificate.
Failed to export config files!.How is that shown ? Where ?
Btw : you better remove your WAN IP in your message.
-
@gertjan it shows this message when i try to output my client config archive file.
-
@gertjan thanks for worrying about my security, its very kind.
I will change it as soon as we fix my openvpn issue.
-
@gertjan none of your advice worked but you were a kind sounding board as i worked through the issue!
Yes it's working now.
My solution was found here, this procedure works: https://www.ceos3c.com/pfsense/openvpn-on-pfsense/#step-4-configure-openvpn-on-pfsense-using-the-openvpn-wizard
Stay safe and healthy all!
-
@honeybadger said in 2.6 cant get openvpn working:
My solution was found here, this procedure works: https://www.ceos3c.com/pfsense/openvpn-on-pfsense/#step-4-configure-openvpn-on-pfsense-using-the-openvpn-wizard
Compare what you found there with the OpenVPN Netgate video I mentioned above.
It uses port 1195 instead of the default 1194. Ok, why not.
It proposes to include a DNS, which is an obvious thing to do.I've used the Netgate OpenVPN intructions video last weekend on a 'clean' pfSense. VPN access worked in a couple of minutes.
-
@gertjan honestly i still used 1194