Unifi Access Point, Unfi Swifth & pfsense - Looking for a VLAN tutorial
-
My current network is rather simple, diagram below.
Modem <--> pfSense box <---> UniFi Switch <---> Many devices including a UniFi AP
I would like to create a VLAN on my UniFi AP for all IoT devices. I am looking for a tutorial on this - I am new to VLANs.
I found the tutorial below but it doesn't explain how to prevent the VLAN from accessing devices on my main LAN.
https://blog.barclayhowe.com/setting-up-a-vlan-in-pfsense-and-unifi/Does anyone have a forum post or tutorial that explains this?
-
My network is similar, but I have a Cisco switch and the VLAN is used for guest WiFi.
Essentially, you have to use the same VLAN ID everywhere it has to go. In my case, that's pfsense, the switch and access point.
Do you have a 2nd switch for the IoT, so that you can use a single port to connect it and another to the access point? If so, you'd also enable that VLAN to that switch. Depending on what you're doing, there are a couple of ways to do that. For example, if that 2nd switch has only IoT devices, then the port of the 1st switch is configured as an access port attached to the VLAN. If you want both IoT and main LAN to the 2nd switch, then you configure a trunk port to the 2nd switch and then sort things out further on it.
-
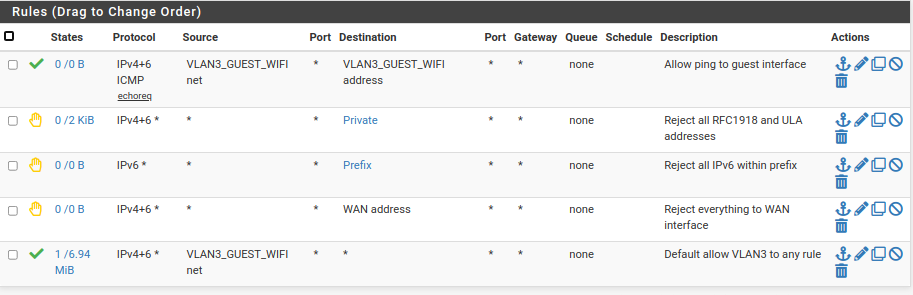
@pulsartiger Have you found this video yet? The blocking of one network (IOT) from talking to another network (LAN) looks to be right about at the 7:30 minute mark...
https://www.youtube.com/watch?v=b2w1Ywt081o
Don't forget, after you do the blocking rule(s), you then need an "allow to any" rule to get the IOT network out to the internet.
-
-
@akuma1x said in Unifi Access Point, Unfi Swifth & pfsense - Looking for a VLAN tutorial:
@pulsartiger Have you found this video yet? The blocking of one network (IOT) from talking to another network (LAN) looks to be right about at the 7:30 minute mark...
https://www.youtube.com/watch?v=b2w1Ywt081o
Don't forget, after you do the blocking rule(s), you then need an "allow to any" rule to get the IOT network out to the internet.
Thanks for the YT video link, I will take a look.
@jknott said in Unifi Access Point, Unfi Swifth & pfsense - Looking for a VLAN tutorial:
My network is similar, but I have a Cisco switch and the VLAN is used for guest WiFi.
Essentially, you have to use the same VLAN ID everywhere it has to go. In my case, that's pfsense, the switch and access point.
Do you have a 2nd switch for the IoT, so that you can use a single port to connect it and another to the access point? If so, you'd also enable that VLAN to that switch. Depending on what you're doing, there are a couple of ways to do that. For example, if that 2nd switch has only IoT devices, then the port of the 1st switch is configured as an access port attached to the VLAN. If you want both IoT and main LAN to the 2nd switch, then you configure a trunk port to the 2nd switch and then sort things out further on it.
I only have (1) switch and (1) AP. Both support VLANs. My pfsense box is connected to the switch using a single port and the AP is connected to the same switch. Unless I misread while doing my research, it should be possible to have multiple VLANs on my AP without having separate ports, correct?
-
You can have as VLANs to the AP as you have available SSIDs. I asked about a 2nd switch, assuming you might have some wired IoT devices.
-
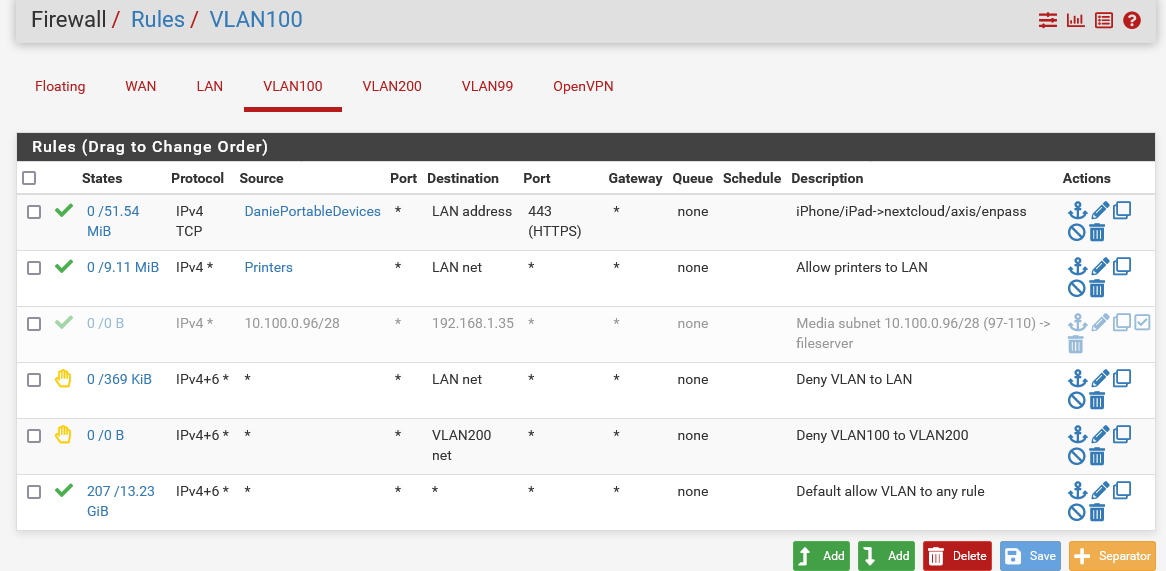
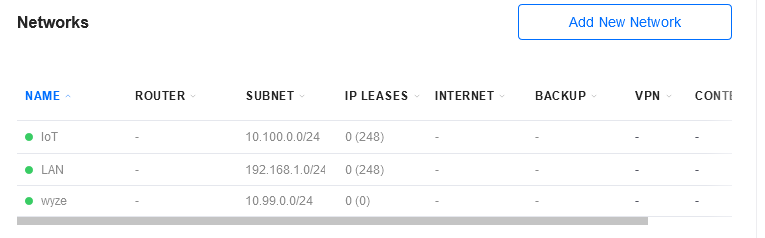
@pulsartiger In the Unifi Controller, for the network you set the subnet for the VLAN as follows
And the VLAN ID as follows
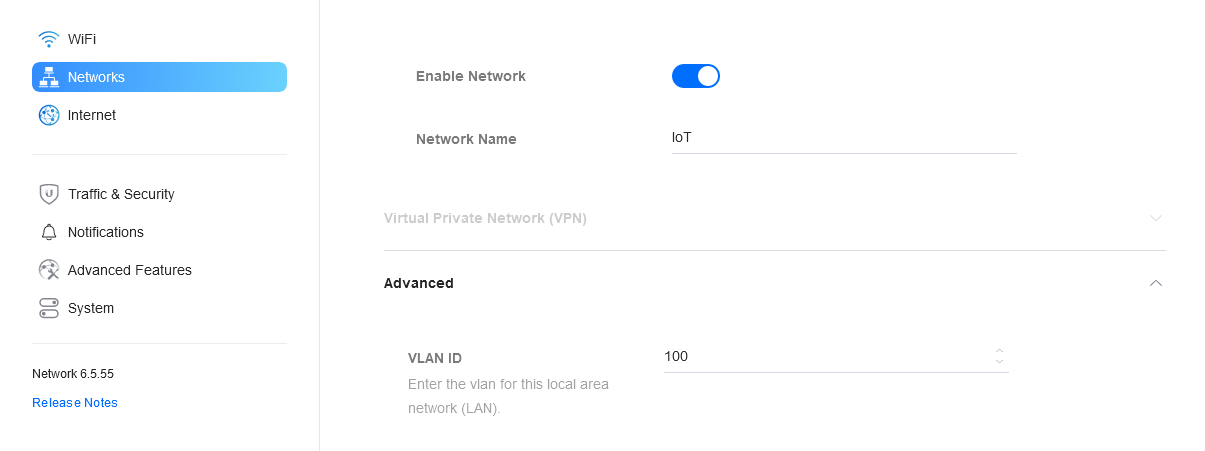
Then in pfSense you create a VLAN for the same ID
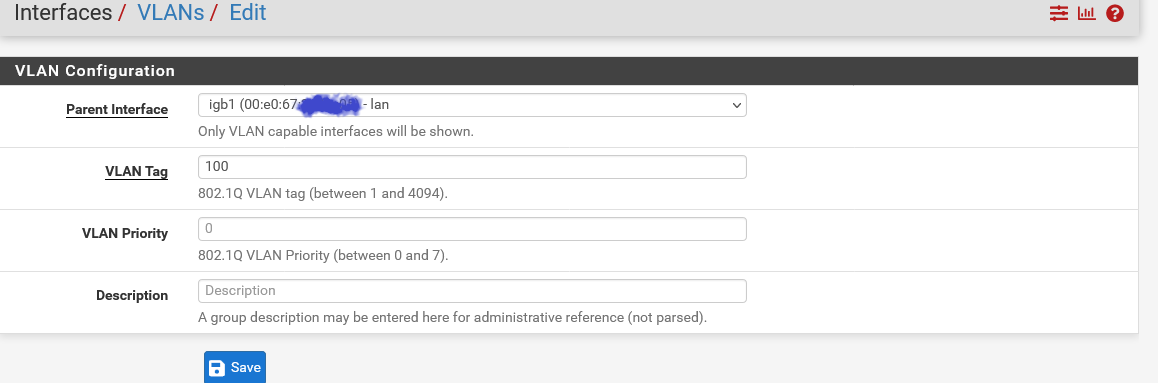
And firewall rules as appropriate. For example I allow my phone/ipad access to certain applications on the LAN (through a HA proxy). Printers are also allowed. I block everything else on VLAN100 to LAN and VLAN200. The last rule is to allow everything, everywhere.