Firewall Rules With VLANS
-
I've had pfsense running for about 12 months now and everything is working perfectly. I recently set up 1 VLAN for my security cameras. I have a mix of hard wired & wireless cameras (15 cameras in total) & all cameras are on VLAN 3 (192.168.10.0) my Lan Ip range is 192.168.1.0.
I have blocked internet access to VLAN 3 to everything except my NVR (192.168.10.2). I have also blocked access between my Lan and VLAN 3.
All of the above is working correctly. What im trying to do is give 3 devices on my lan (my phone, wife's phone and laptop) access to VLAN 3 in order to use a native app for my wireless cameras. I only want to give access to the 3 devices when on my network only, not roaming.
Ive tried many different firewall rule configurations on both my lan and security camera's networks to no avail.
My current firewall rules are;
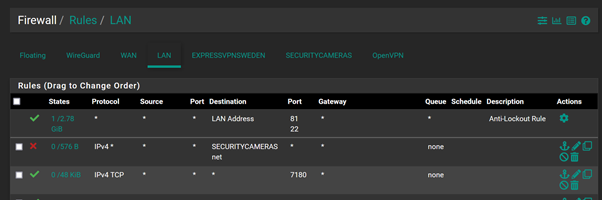
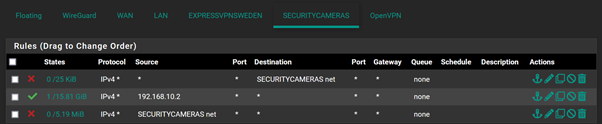
I have assigned the 3 devices i want to give access to the VLAN a static ip address and tried adding a rule at the top of the security cameras network as per the below, however it doesn't work.
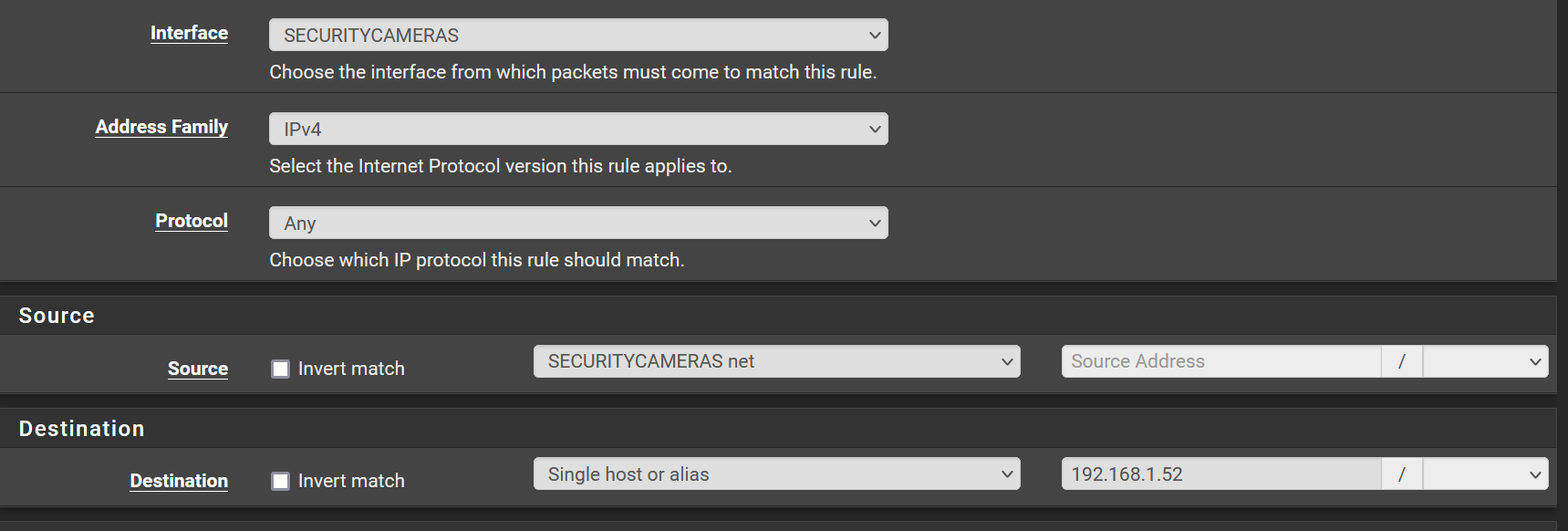 .
.192.168.1.52 is my phones IP.
My current Hardware set up is;
PFsense virtual machine on a Qnap 1602p Switch
Unifi USW 24 pro.Thanks
-
-
Hi Bob,
Thanks for your swift response, it seems i am doing something fundamentally wrong, but i can't quite put my finger on it. I've read through the rule methodology a couple of times, however still can't seem to find it.
Apologies for the small screen shot
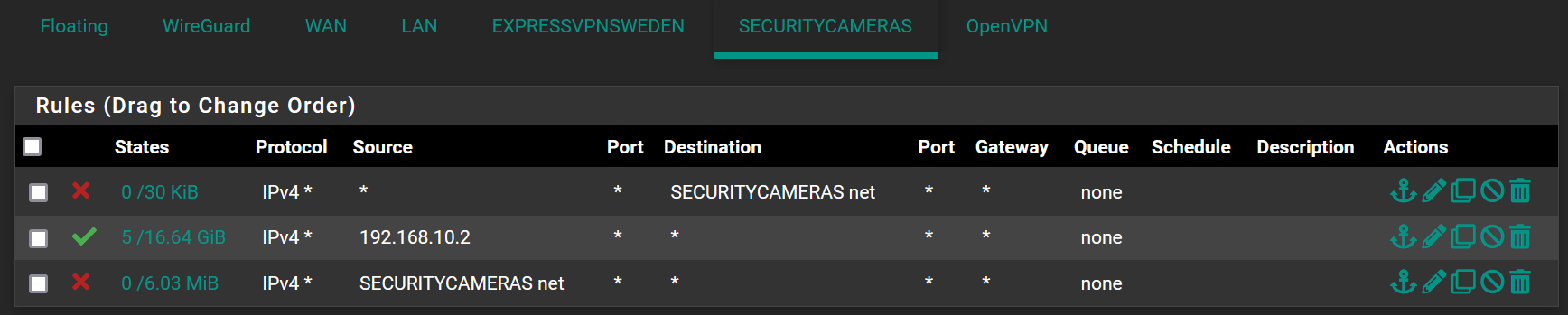
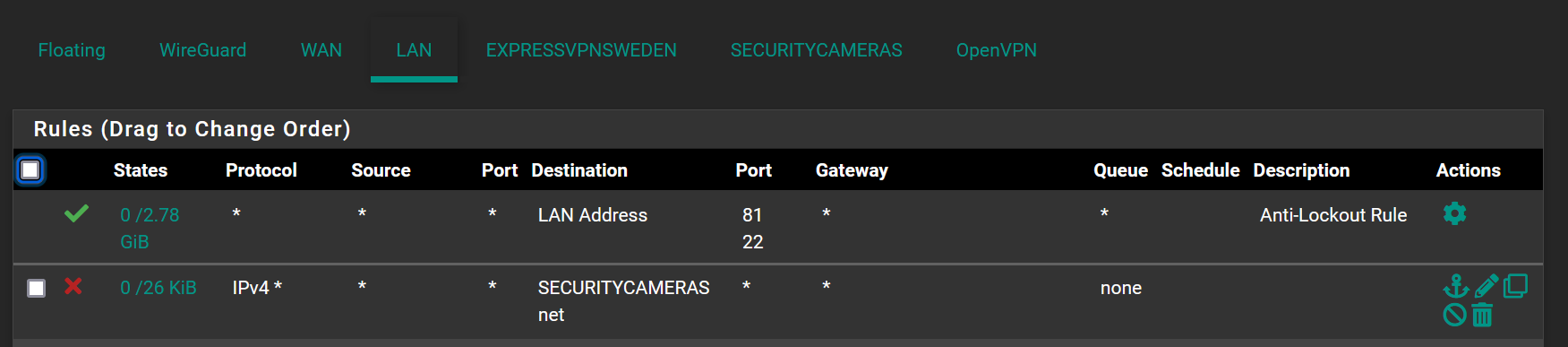
-
@zuch You have to block and allow only on the source interface, for instance, if you want something on your LAN to access something on your VLAN3, you have to make the rule on LAN, not on VLAN3. And so on.
So your rules look wrong. The problem with pfSense is, that it is not telling you, that your rules don't make any sense, it just doesn't care.
-
I'm doing the same with my mobile devices. Here is how mine is setup:
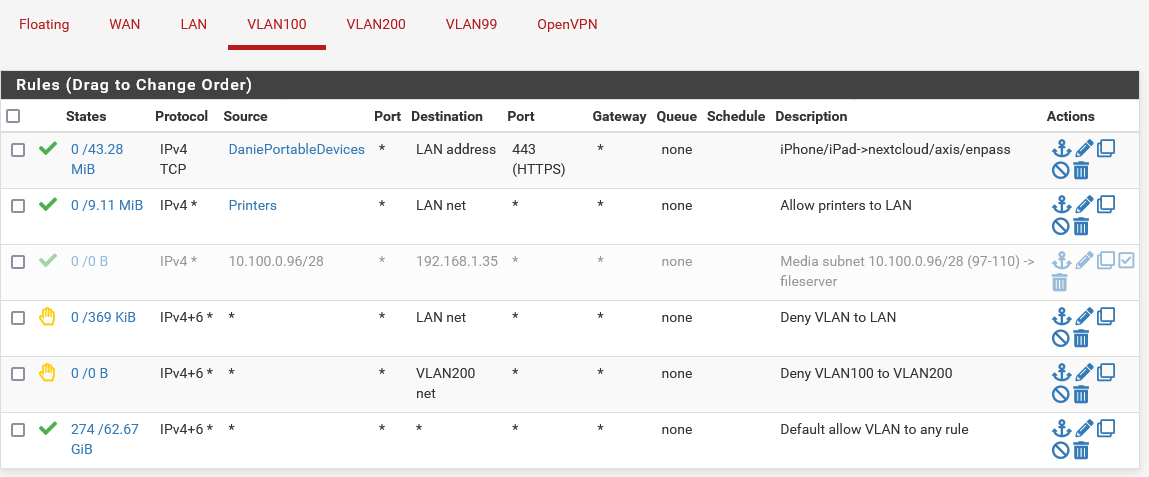
Edit:
In my case my mobile devices are on VLAN100 and I grant them access to LAN, therefore my rule is on the VLAN100 interface. Also, I have a proxy server running on LAN hence allowing them to LAN address instead of LAN net.For your situation in which your mobile devices are on LAN, your rule will need to be on the LAN interface and the allow rule for the mobile devices must be before the deny rule to block everything else.
-
@danievr I did the same thing and asked if I had missed anything.
https://forum.netgate.com/topic/168726/is-there-a-better-way?_=1647555037032I can access the cameras from my primary VLAN with no issues. The cameras cannot get out of the VLAN.
-
Thank you both for your replies, after trying what felt like every possible rule configuration in both my Lan rules and Vlan 3 (security cameras) rules, there seems to be an issue with the native app (tp link) for some of my wireless cameras with Vlans due to broadcast discovery - https://community.tp-link.com/en/smart-home/forum/topic/501882
My firewall rules were working all along, the rules from my first post were incorrect, however once corrected the tp link app still didn't work. I was only using the tp link app as my other half liked the alerts better, however i will set up proper alerts on my NVR.
for anyone wondering my rules below seemed to work,
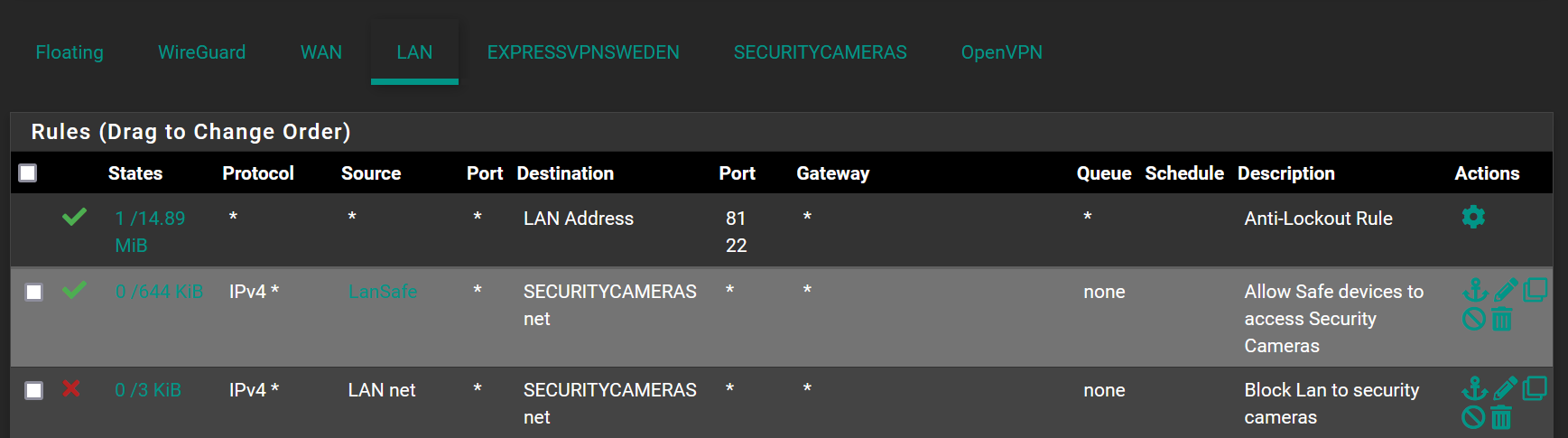
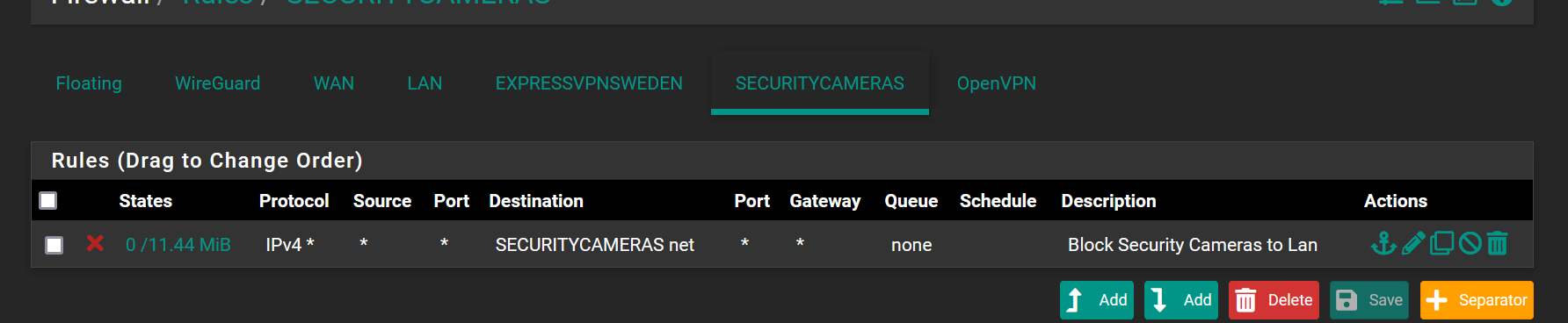
Thanks again
-
@zuch You last rule is something you will not see around here because you can't block traffic from and to the same network. Also, because you don't allow anything there anyway, you don't need a rule in the first place.
But it might be a good idea to allow dns and ntp.
-
Thanks for that, changed now.
