Configuring Home Assistant Web socket behind Pfsense's HAProxy
-
Hi, Everyone.
Please help me with my problem. Currently I have Pfsense's HAProxy package installed. I am trying to make HomeAssistant worked behind HAProxy so I can access it from the Internet. I am able to reach the username and password screen and was able to login but it does not open the page. I only get the is prompt: Unable to connect to Home Assistant. I believe the cause of this is websocket. As of this moment I also have Synology Surveillance station also using websocket and I am able to access it from the internet without any problem.
Having a working websocket interfere with the websocket that I am trying to configure for Home Assistant? If not I have attached my configuration below please help check if I have misconfigured it or miss anything so I can fix my issue.
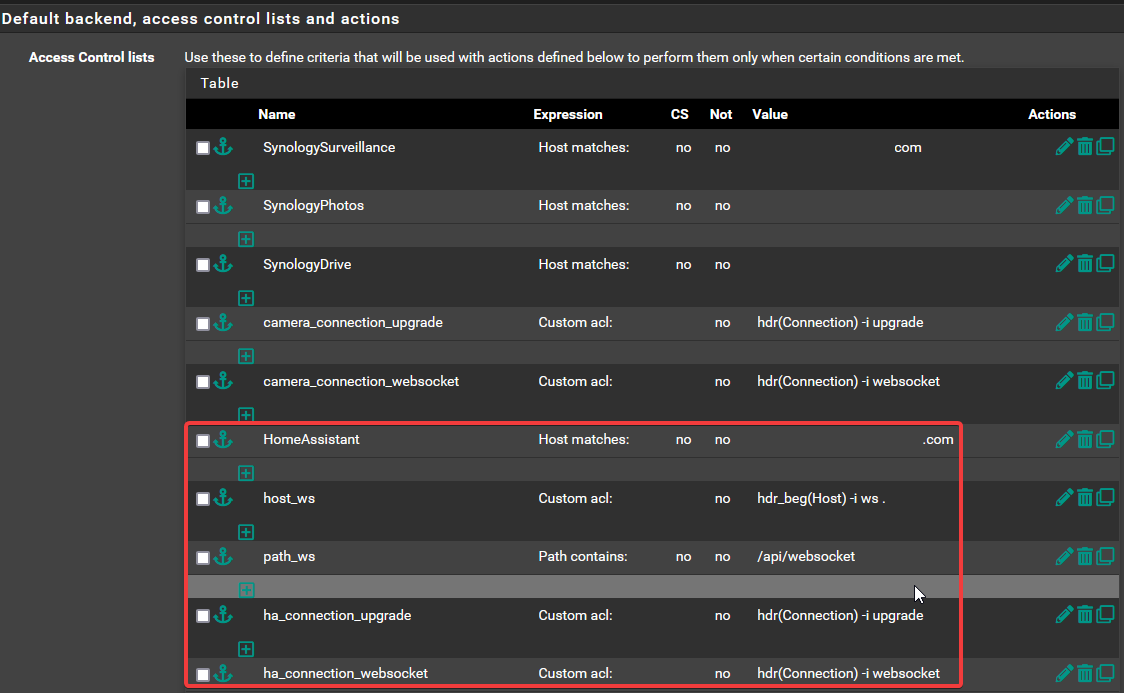
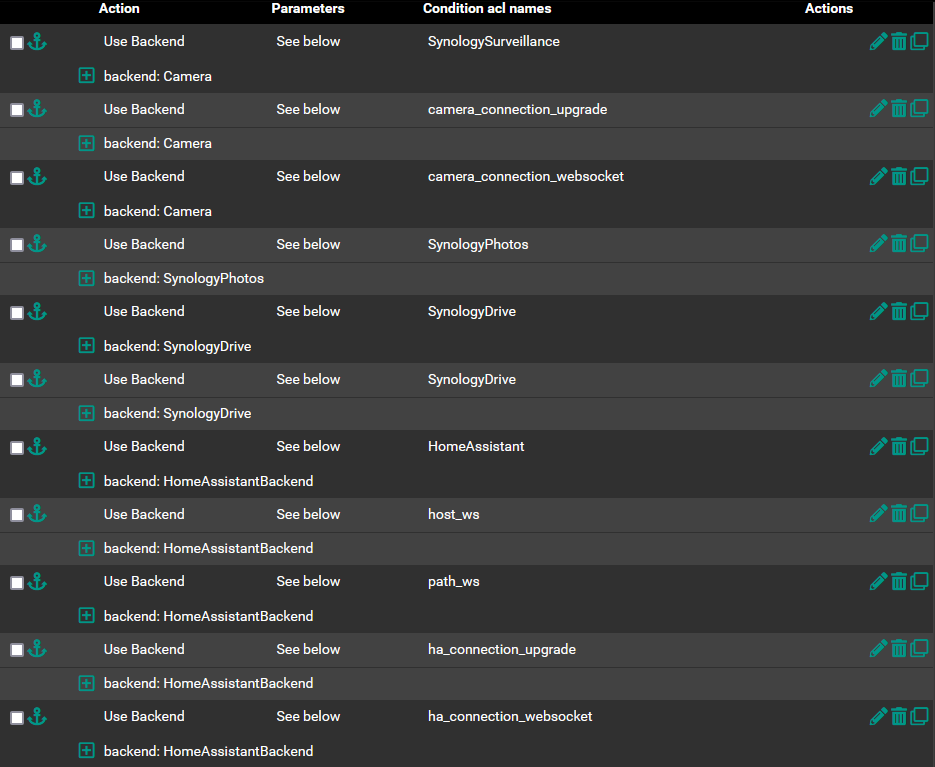
-
Just to provide an update on this ticket. I forgot to mention, SSL offload is enabled in HAProxy.
Also here is the firewall logs and error logs from Home Assistant
Firewall logs
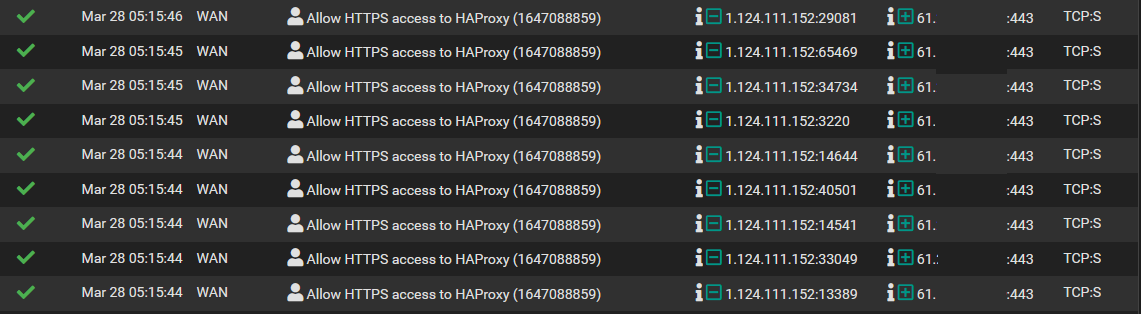
Error message from Home Assistant:
2022-03-28 05:12:22 WARNING (MainThread) [homeassistant.components.http.ban] Login attempt or request with invalid authentication from 1.124.111.152 (1.124.111.152). (Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:98.0) Gecko/20100101 Firefox/98.0) 2022-03-28 05:14:31 WARNING (MainThread) [homeassistant.components.http.ban] Login attempt or request with invalid authentication from 1.124.111.152 (1.124.111.152). (Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:98.0) Gecko/20100101 Firefox/98.0) -
Did you figure out this problem? I have the exact same problem and hoped there was an answer here :)
-
Yes I was able to make it work, at the Front end, I place HomeAssistant at the top of the ACL and place the surveillance station at the bottom. That is the only change I made to make it work.
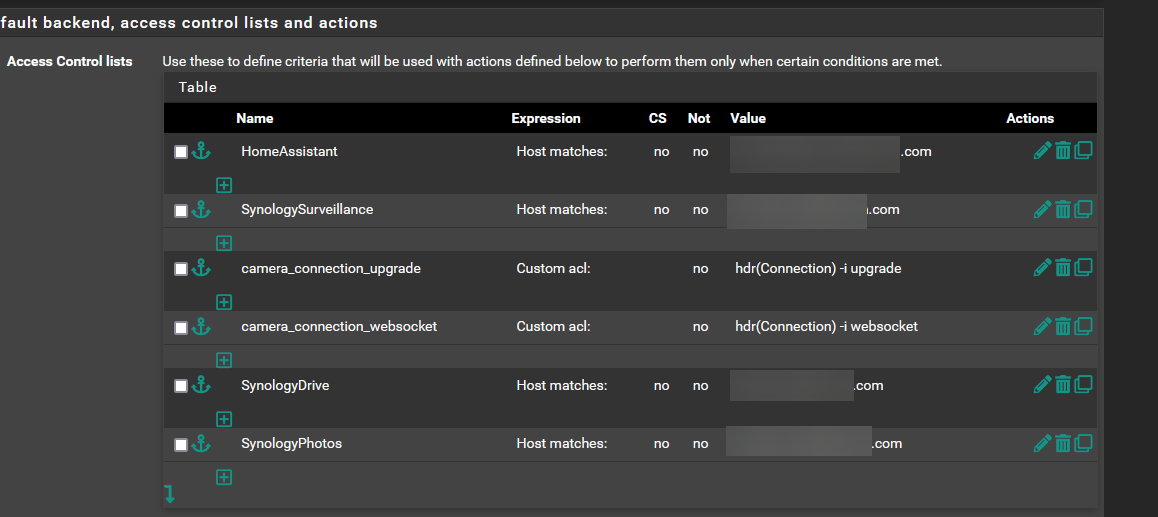
-
Thanks for such a fast reply!
Do you have websocket upgrades on the homeassistant as well. Or are those two used for both HA and Synology camera? -
The websocket was only configured for Synology and no websocket configuration for home assistant
-
I've also problem with home assistant behind ha proxy.
If I ste a direct nat roule to port 8123 works all good, but if I try to use the ha link I receive a 503 error page.
this is my ha config, any idea?
p.s. all other backends are working correctly# Automaticaly generated, dont edit manually. # Generated on: 2023-07-31 19:46 global maxconn 1000 stats socket /tmp/haproxy.socket level admin expose-fd listeners uid 80 gid 80 nbproc 1 nbthread 1 hard-stop-after 15m chroot /tmp/haproxy_chroot daemon tune.ssl.default-dh-param 2048 server-state-file /tmp/haproxy_server_state frontend http bind 192.168.1.220:80 name 192.168.1.220:80 mode http log global option http-keep-alive option forwardfor acl https ssl_fc http-request set-header X-Forwarded-Proto http if !https http-request set-header X-Forwarded-Proto https if https timeout client 30000 http-request redirect scheme https frontend https_443 bind 192.168.1.220:443 name 192.168.1.220:443 ssl crt-list /var/etc/haproxy/https_443.crt_list mode http log global option http-keep-alive option forwardfor acl https ssl_fc http-request set-header X-Forwarded-Proto http if !https http-request set-header X-Forwarded-Proto https if https timeout client 30000 acl ha var(txn.txnhost) -m beg -i ha.mysite.org acl NAS var(txn.txnhost) -m beg -I nas.mysite.org acl www var(txn.txnhost) -m beg -I www.mysite.org acl proxmox var(txn.txnhost) -m beg -I proxmox.mysite.org acl firewall var(txn.txnhost) -m beg -I firewall.mysite.org http-request set-var(txn.txnhost) hdr(host) use_backend ha_ipvANY if ha use_backend NAS_ipvANY if NAS use_backend serverweb_ipvANY if www use_backend proxmox_ipvANY if proxmox use_backend firewall_ipvANY if firewall backend ha_ipvANY mode http id 102 log global timeout connect 30000 timeout server 30000 retries 3 timeout tunnel 60000s server ha 192.168.1.138:8123 id 103 ssl verify none backend NAS_ipvANY mode http id 100 log global timeout connect 30000 timeout server 30000 retries 3 server nas8 192.168.1.112:8080 id 101 backend serverweb_ipvANY mode http id 104 log global timeout connect 30000 timeout server 30000 retries 3 server www 192.168.1.239:80 id 105 backend proxmox_ipvANY mode http id 106 log global timeout connect 30000 timeout server 30000 retries 3 server proxmox 192.168.1.236:8006 id 107 ssl verify none backend firewall_ipvANY mode http id 108 log global timeout connect 30000 timeout server 30000 retries 3 server firewall 192.168.1.1:80 id 105Thanks