WAN webGUI access after fresh remote install
-
I have remotely made a fresh install of pfSense 2.6.0 on a remote dedicated server, following a crash when upgrading from 2.5.2 to 2.6.0.
I would now like to access the webGUI via wan, to upload the previous config.
To do so I entered the following rule in the shell :easyrule pass wan any MYPUBLICIP any anyBut I still cannot access the webGUI.
What can I do? -
[2.6.0-RELEASE][root@pfsense.mylocal.net]/root: easyrule pass WAN TCP any 192.168.10.3 any Successfully added pass rule!Did you saw the
Successfully added pass rule!message ?
It created
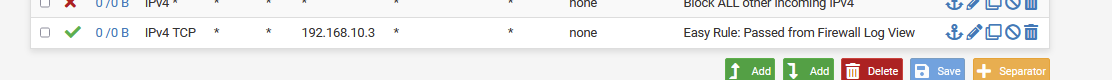
as the last rule.
When you install pfSense, there will be no rules on LAN, so, it should work.Your WAN interface should be using the IP you specified.
I had to move the cerated rule to the top of the list, save and apply.
Now I could access the pfSense from the Internet.
( I had to NAT my ISP upstream router also, of course ) -
Thanks for your help.
What I tried so far:easyrule pass wan any <MYPUBLICIP> any any easyrule pass wan tcp <MYPUBLICIP> <FIREWALLPUBLICIP> 443I saw each time the
Successfully added pass rule!But still no access to the webGUI.
I checked with
sockstat | grep 443that nginx is listening on port 443 and got
root nginx 24254 5 tcp4 *:443 *:* root gninx 24254 6 tcp6 *:443 *:* root nginx 24187 5 tcp4 *:443 *:* root gninx 24187 6 tcp6 *:443 *:* root nginx 24136 5 tcp4 *:443 *:* root gninx 24136 6 tcp6 *:443 *:*I don't understand the use of your rule, what is your 192.168.10.3 IP?
All I want is to access the webGUI once from wan to restore a previous config and my VPN access, then everything will be fine again.
-
When you check with
sockstat | grep 443you will see that a root process called nginx listens on all known interfaces, using both tcp4 and tcp6.
What are these known interfaces ? ;)I guess 127.0.0.1 - and ::1 - LAN, tcp4 and tcp6 and I hope WAN tcp4 and tcp6.
W'll presume WAN exists ^^.The little known secret is : yes, the nginx web GUI server is listing on the WAN interface (I would loc it down to LAN only, but, who am I to decide ^^ - you wouldn't agree we me here).
Check your command line options.
I said :
easyrule pass WAN TCP any 192.168.10.3 any
You said
easyrule pass wan any MYPUBLICIP any anyMy interface is called WAN not wan.
Protocol is TCP, as it is known - 'any' usage is ... dono : awkward ?
My next any == source which should be any ne (from the internet)
My 192.168.10.3 = the destination = my pfSense WAN IP.
The last any is [destination port] and is optional.Type easyrule without parameters to see the help text.
Your command is wrong, as MYPUBLICIP will get interpreted as the source IP.
@marlepou said in WAN webGUI access after fresh remote install:
what is your 192.168.10.3 IP?
My WAN IP :
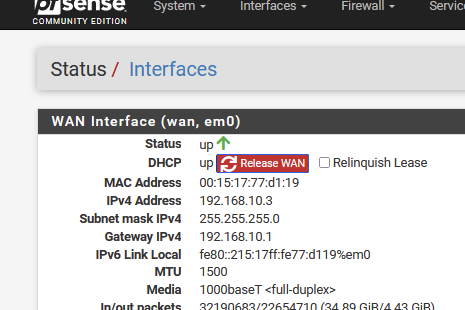
192.168.10.1 is my upstream ISP router - it has only one device on it's LAN : my pfSense, using 192.168.10.3.
-
@gertjan
There are only two interfaces:
WAN (wan) -> igb0 -> v4/DHCP4: x.x.x.x/24 where x.x.x.x is what I called <FIREWALLPUBLICIP> above,
LAN (lan) -> igb1 -> v4: 192.168.1.1/24I am trying to access the webGUI from a remote location which public IP is y.y.y.y where y.y.y.y is what i called <MYPUBLICIP> above.
So my understanding is that my command should work as <MYPUBLICIP> is the source IP and <FIREWALLPUBLICIP> is my pfSense wan IP.
Following your answer I tried the command with wan and tcp in both lowercase and uppercase, but no change.
-
@marlepou does "pfctl -f /tmp/rules.debug" show anything notable?
There is this: https://docs.netgate.com/pfsense/en/latest/troubleshooting/locked-out.html#add-an-allow-all-wan-rule-from-the-shell. If you're going to immediately restore from backup it's not that dangerous to have the login page exposed for a few minutes.
That's the next item down from https://docs.netgate.com/pfsense/en/latest/troubleshooting/locked-out.html#add-a-rule-with-easyrule which looks like what you're trying already.
-
@steveits
Thanks for your help.
I have tried this script already but nothing changes :(And "pfctl -f /tmp/rules.debug" doesn't return anything at all.
-
@marlepou said in WAN webGUI access after fresh remote install:
doesn't return anything at all
That sounds like a worse issue since I would expect that shows the active default set of firewall rules.
You could https://docs.netgate.com/pfsense/en/latest/troubleshooting/locked-out.html#disable-the-firewall
Or get access to a device on the LAN and try to connect, if that is allowed.or at the console:
4) Reset to factory defaults
(which is DHCP on WAN) -
@steveits
Even with the pf disabled (pfctl -d) I still have no access.
And an nmap on the wan IP returns all ports (the first 1000) as filtered even though the pf is disabled...Edit:
And I forgot to answer you: I have absolutely no access on the LAN side without the pfsense properly working. -
Maybe I should try to reinstall from scratch with a 2.5.2 (which surely used to work) instead of the 2.6.0 just in case.
-
Use the dmesg command to see the kernel boot log.
Interface were found, and activated ?Run ifconfig. Can you see the LAN and WAN drivers, the IP, are the interfaces "active" ?
-
Problem solved !
There was an active firewall ISP side filtering all incoming connections.
With it deactivated, I have been able to reach the pfSense and restore the config.Everything back in order.
Thanks a lot Gertjan and SteveITS, your help was much appreciated! -
I'd like to tag the thread as [SOLVED], but I can't edit my initial post any more.
What should I do?