-
Hi there,
I'm working on an OpenVPN-based Site-to-Site VPN.
Something very weird happened. If I set my IPv4 Tunnel Network to be 10.10.10.0/30, the server site and client site access each other normally..
If I set IPv4 Tunnel Network to be 10.10.10.0/24, only the virtual address of tunnels can be pinged. All sites cannot reach each other.There is no valuable information in the log. With IPv4 Tunnel Network /24, there is no Site-to-Site traffic and no error/warning messages in the log. With /30, traffic is normal between all sites, but a warning keeps appearing:
WARNING: 'ifconfig' is present in local config but missing in remote config, local='ifconfig 10.10.10.1 10.10.10.2'/30 works fine but it cannot hold enough client sites. How can I get Site-to-Site VPN to work properly with /24?
Thak you.
UD
-
@upper-deck Well, this isn't certainly the issue
tunnel network is normaly a /24.
What do you have at client settings/ topology?
Net 30 or subnet?What are you using on the other end?
-
Hi @netblues,
I set it up following this guide strictly: OpenVPN Site-to-Site Configuration Example with SSL/TLS.
All settings:
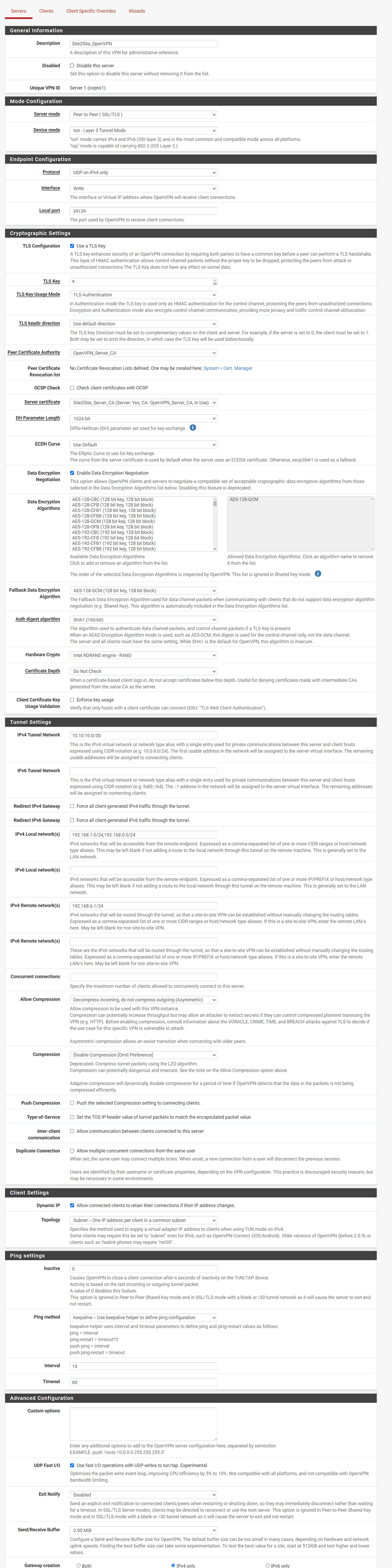
-
@upper-deck What are you using on the other end?
How many devices are you connecting? -
Hi @netblues
Currently I only have one working client set up. The goal is to setup 3 site-to-site clients.
The first client settings:
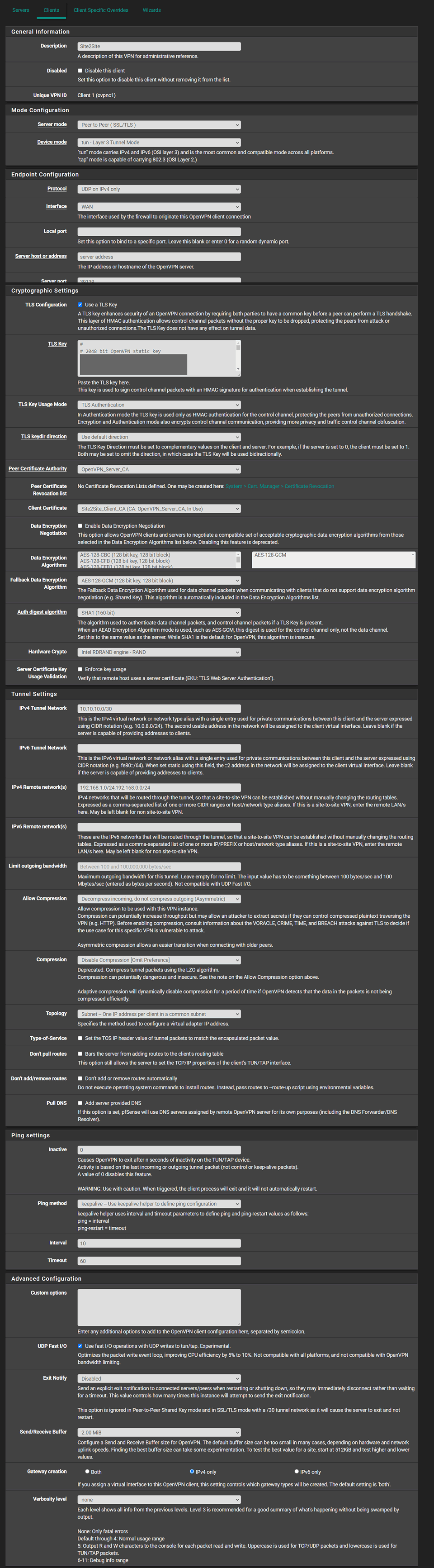
Thank you.
UD
-
Try removing tunnel network on all clients
Server is responsible to assinging ip's.
You create ip conflicts since all clients are assigning the same ip to their side. -
Hi @netblues,
Once the tunnel network removed from the client configuration, the client connected normally but lost its virtual address.
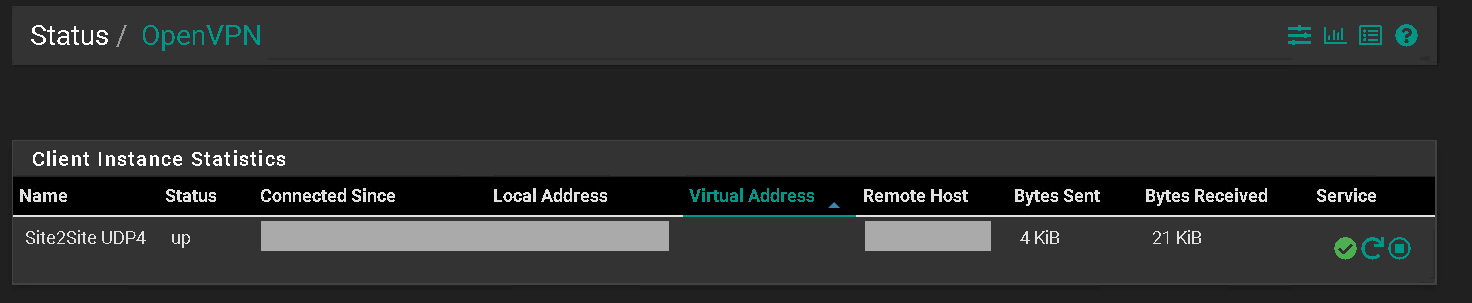
-
And you have a normal /24 at the server tunnel network?
Have you restarted openvpn service both ends after changes?
Have you assigned an interface to the vpn server/client for better monitoring/management?
-
@netblues said in Site2Site OpenVPN only works with /30 IPv4 Tunnel Network?:
And you have a normal /24 at the server tunnel network?
Yes. But using /24 still causes all sites to not be able to access each other.
Have you restarted openvpn service both ends after changes?
Thanks for reminding. The virtual address is normal after restarting.
Have you assigned an interface to the vpn server/client for better monitoring/management?
Yes. Everything looks ok.
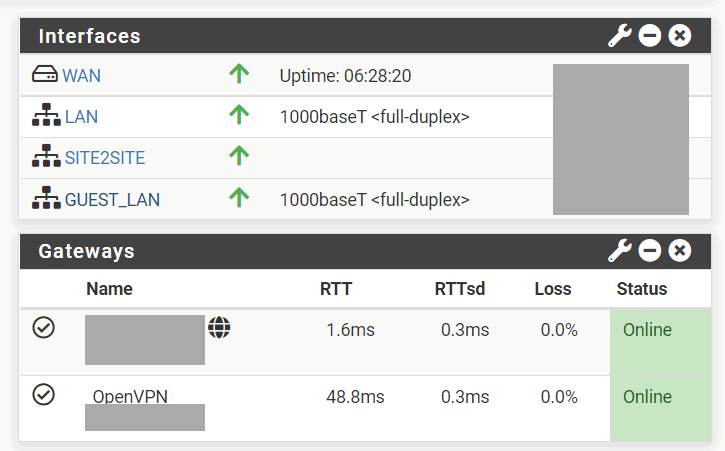
-
@upper-deck
Why not just create a /30 server for each site ?I have 6 x Site to site (S2S) - /30 OVPN servers , and they give me no grief, and since they're "Point to point", all info can be given directly in the definitions.
I have no experience with /24 S2S , just use /24 for "Client Connects .. "dialin"
But since your desired "/24 Server" is a "one to many" i would expect you have to use Client Side Overrides (CSO) , in order to define the Site specific info , like routes etc ....
I absolutely prefer /30 , or more correctly Point-To-Point for (S2S).
And i "think" i get the advantage of having multiple servers , where each can run simultaneously on an available "CPU... Thread".
I have an idea (hope) that this would improve the "OpenVPN" is "locked to one Core" performance. Since several servers, each can use an available "Core" if needed.Edit:
I have i5's or i3's with 4 "threads" , and 8GB Ram, so "multi OVPN server" resources is not an issue for me./Bingo
-
@bingo600 What you suggest is valid, however doesn't correct the mis- configuration issue of the op.
And certainly having 3 servers is more difficult to administer than one.
On the performance side, I would ditch openvpn altogether and opt for wireguard.
-
@netblues said in Site2Site OpenVPN only works with /30 IPv4 Tunnel Network?:
@bingo600 What you suggest is valid, however doesn't correct the mis- configuration issue of the op.
I just commented on the /30 vs /24 S2S setup.
And certainly having 3 servers is more difficult to administer than one.
IMHO that's not correct, since you don't have to do the CSO's on a P2P /30.
I would say they're comparable in complexity.On the performance side, I would ditch openvpn altogether and opt for wireguard.
I don't trust wireguard (yet) ...
OpenVPN is proved "easy and stable", and for my ISP BW 300Mb/s i have no problem "filling the line".For squeezing the last drop out i'd go IPSEC.
/Bingo
-
I did some more tests. Under the premise of keeping other settings all the same, if the IPv4 Tunnel Network goes to /30, both the server and client networks are normal; as long as the IPv4 Tunnel Network is set to /24, the server and client will not be able to access each other. Except for the IPv4 Tunnel Network /24 /30 settings of the server-side and client-side, other configurations remain the same.
Also, I found a very interesting fact. When /30 is set, the Status page of OpenVPN displays server information. When /24 is set, the Status page displays the client connection information. Perhaps when the IPv4 Tunnel Network is set to /24, pfSense also thinks that the server-client VPN mode is used?
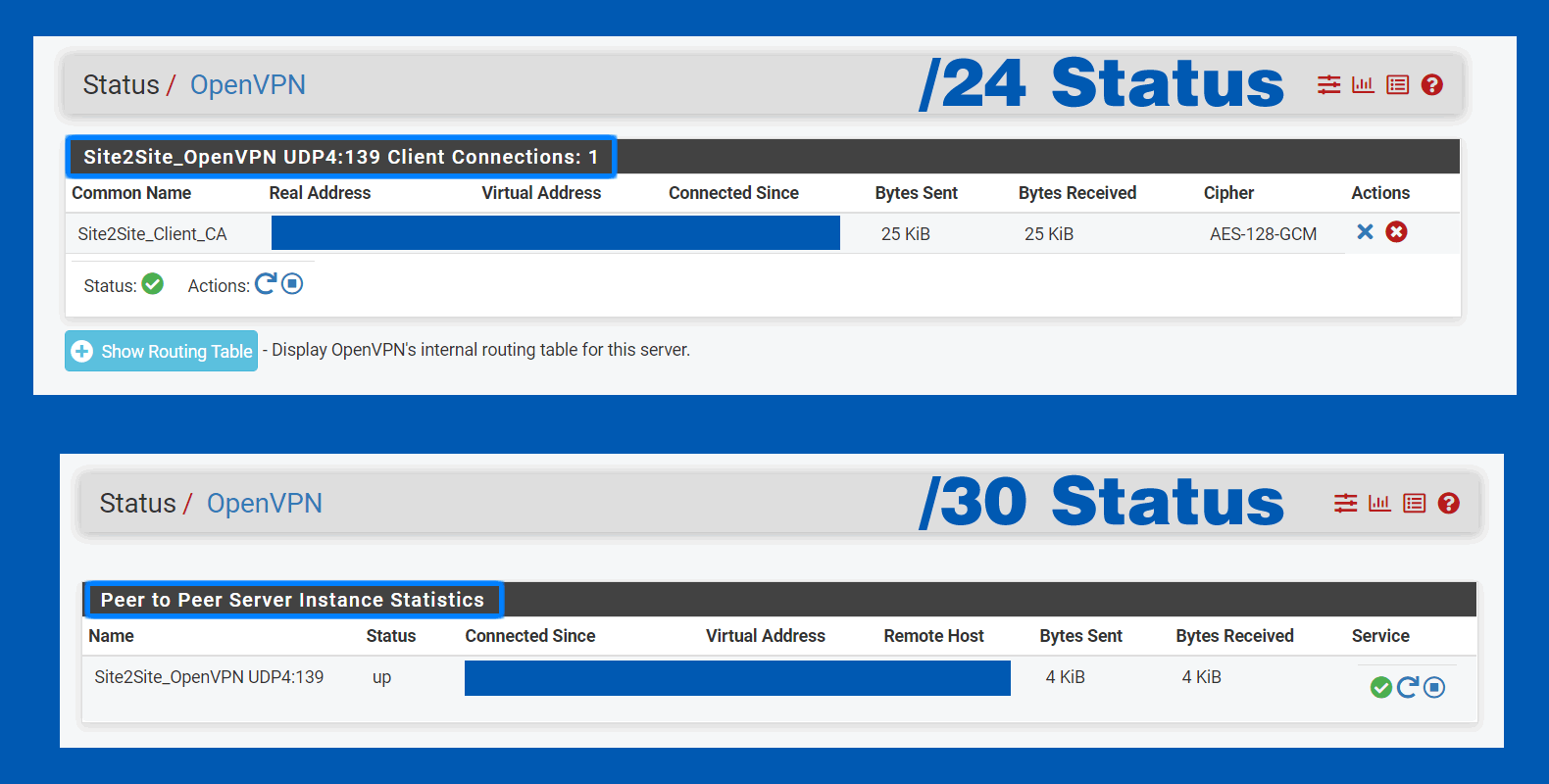
-
@upper-deck said in Site2Site OpenVPN only works with /30 IPv4 Tunnel Network?:
Also, I found a very interesting fact. When /30 is set, the Status page of OpenVPN displays server information. When /24 is set, the Status page displays the client connection information. Perhaps when the IPv4 Tunnel Network is set to /24, pfSense also thinks that the server-client VPN mode is used?
Easy explained ...
When /30 is used pfSense knows it's a Point-to-Point.
And uses the info directly from the Server/Client definition./Bingo
-
Still can't figure out why the /24 tunnel network doesn't work.
-
@upper-deck I thought it did from what you said
-
It's because when you set the server to use /24 topology you need to add client specific overrides for each client site with the remote subnets set. Doing so adds iroutes in OpenVPN so the daemon knows which subnets are at which clients. Note the 'Routing Table' button in the above screenshot for /24. That will display the iroutes and they must exist.
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html#create-client-specific-overridesWhen you use /30 there can be only one client so the daemon assume all remote subnets are there.
Steve
-
 S stephenw10 moved this topic from General pfSense Questions on
S stephenw10 moved this topic from General pfSense Questions on
-
Orz
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.