Certificate does not have key usage extension
-
@viragomann
Do I need to restart all the OPENVPN services or is the one "OpenVPN server: Mobil-Video-CCTV_NEW"on which I conduct experiments enough?
I reloaded one"OpenVPN server: Mobil-Video-CCTV_NEW".
-
@testsia
Yes, it's sufficient to restart a single service, but the changes only affects to the restarted services naturally. -
@viragomann
Then I don't know what to do with this problem!
I will try to restart the whole server tonight -
Hey!
I rebooted the server but my problem was not solved.
I went further in my experiments.
I have generated a new "CA" certificate. Generated a certificate for the server, specified them in my OPENVPN configuration and now it works fine. But as soon as I return certificates that were not generated on PFSENSE, my problem returns. Does anyone have any ideas how to solve the problem? -
@testsia
Hi friends!
I went further in my experiments.
I installed Pfsense version 2.5, performed a restore from a backup.And OPENVPN works as expected!
I can conclude that the problem is Pfsense version 2.6.
I don't know where to write to inform the developers. But the problem is exactly Pfsense version 2.6.
It does not work with certificates that were generated outside Pfsense. -
@testsia
I determined what the problem is.
My client certificates do not have serverAuth and clientAuth ExtendedKeyUSage ("EKU") attribytes.
In version 2.6 this check is mandatoryCertificate does not have key usage extension 91.203.115.5:56352 VERIFY KU ERRORWho knows how I can disable this check on the server???
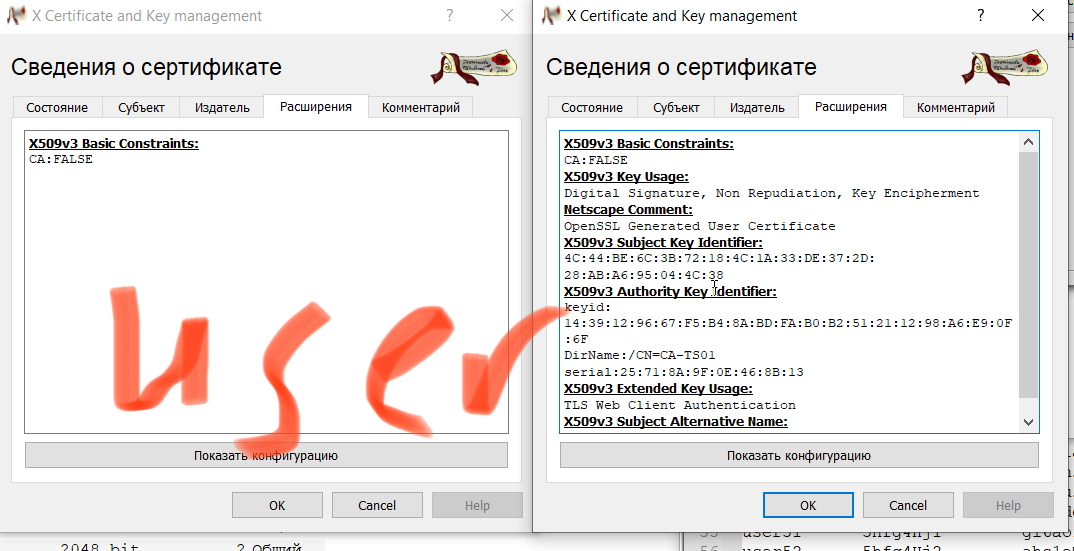
-
@testsia said in Certificate does not have key usage extension:
Who knows how I can disable this check on the server???
That was already answered upthread.
- Read https://redmine.pfsense.org/issues/13056
- Install the System Patches package
- Create entries in the System Patches package for
48cf54f850c5bf4fe26a8e33deb449807e71c204and47f2f4060d9e5b71c5c69356b61191fd2931383c - Fetch and apply both patches
- Uncheck "Client Certificate Key Usage Validation" in the OpenVPN server and Save
-
@jimp said in Certificate does not have key usage extension:
@testsia said in Certificate does not have key usage extension:
Who knows how I can disable this check on the server???
That was already answered upthread.
- Read https://redmine.pfsense.org/issues/13056
- Install the System Patches package
- Create entries in the System Patches package for
48cf54f850c5bf4fe26a8e33deb449807e71c204and47f2f4060d9e5b71c5c69356b61191fd2931383c - Fetch and apply both patches
- Uncheck "Client Certificate Key Usage Validation" in the OpenVPN server and Save
I am very grateful to you!
You helped solve my problem!
Thanks!!! -
-
@jimp said in Certificate does not have key usage extension:
Uncheck "Client Certificate Key Usage Validation" in the OpenVPN server and Save
Does this create a security issue? If so, is there a proper way within pfSense to set-up the certificate so that the EKU works?
The post at the link below indicates it does:
https://superuser.com/questions/1446201/openvpn-certificate-does-not-have-key-usage-extension -
If you create a new cert structure the cert manager in pfSense will put the proper set of attributes in everything these days.
Those certs may have been made externally or before the cert manager was adding the correct attributes.
-
A ads76 referenced this topic on
-
A ads76 referenced this topic on
-
@jimp
thank you Jim, I'm running into the same problem with some older VPN clients/certs.