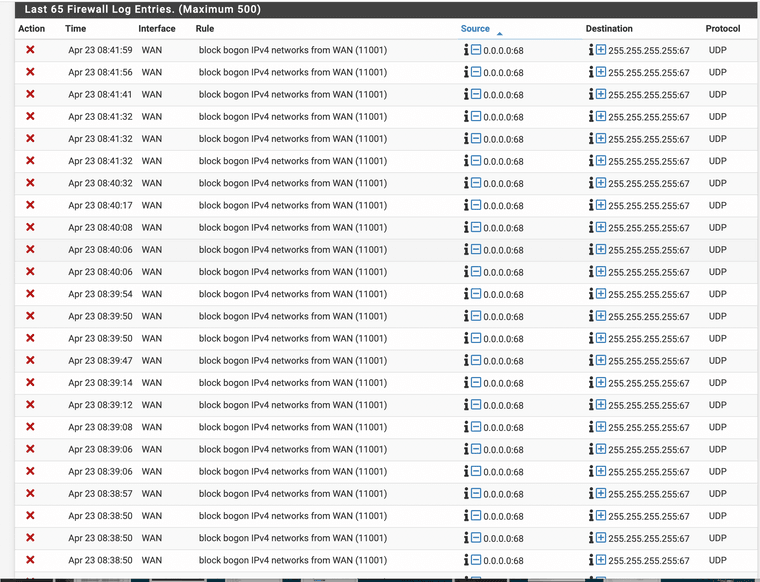
Jump in blocks traffic "block bogon IPv4 networks from WAN (11001) 0.0.0.0:68 255.255.255.255:67 UDP"
-
Why is my WAN side asking for a IP address from the firewall?
That is coming into the firewall correct?
I have seen a massive increase in traffic like this. I do not have a DHCP server running on the WAN side only on the Lan side. The WAN interface gets a DHCP address issued from the ISP via a DSL modem.
if this issued an address to the firewall's wan port why is the WAN asking for an address to send back to the modem?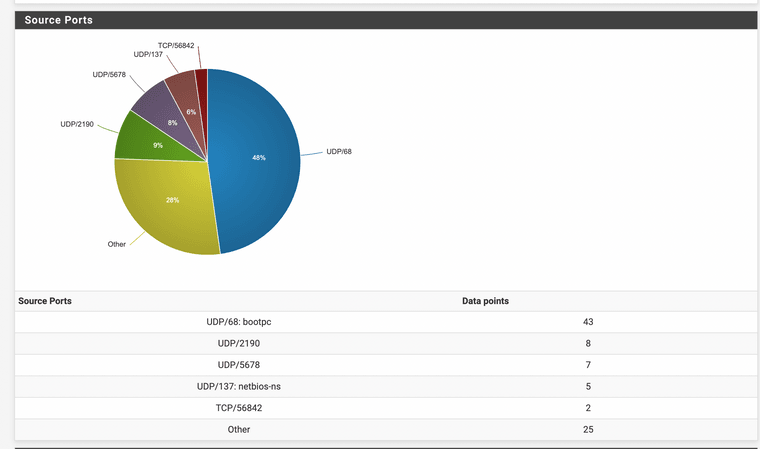
45%? It won't stop if my wan is set to DHCP why is the WAN doing this?
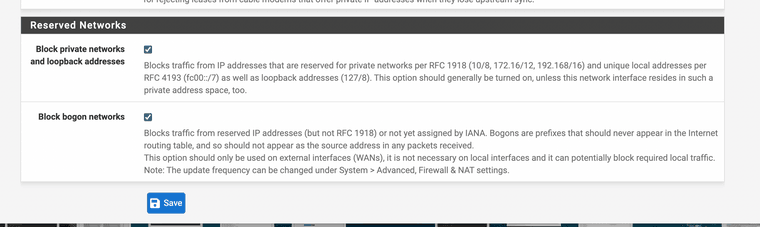
I do have a WAN DHCP address and its working also
-
Is it ok to add a easy pass because it will not reply anyway? This way it will just ignore it.
I am going to try to use Modem MAC as the mac for the wan port to see if it fixes it
-
It's DHCP.
-
0.0.0.0 would be in bogon.. which is why your seeing blocked by bogon.
But yes that is a typical dhcp discover packet.. From 0.0.0.0 port 68 to broadcast 255.255.255.255 port 67
https://en.wikipedia.org/wiki/Dynamic_Host_Configuration_Protocol#Discovery
What I would assume is your seeing all the dhcp discover traffic from other clients on your isp connection..
You could just turn off not logging bogon if you don't want to see such noise. Problem with trying to add a rule to not log it, is bogon is before your rule you would add.
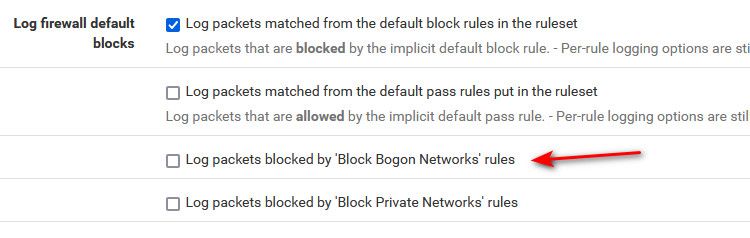
To me your isp is misconfigured their network... Because if your seeing the discover you could answer.. So in theory you could have other isp clients send traffic to you as their gateway - and then do malicious stuff... You prob want to contact your isp.. You shouldn't bee seeing other clients requests for dhcp..
If you sniff the traffic - you could see all the mac addresses of who is actually asking for dhcp.
edit: here I just sniffed on my wan for over a minute - don't see any traffic to 67, your isp should fix it would be the correct solution.. I see lots of arp traffic from from other clients on my isp network.. Which is also not actually good setup, and the isp should filter that traffic as well.. But dhcp is worse than just arp.. I mean in theory you could also do a arp poison sort of attack to other clients of your isp.. But that is a bit more complicated.. And in theory they should get the arp from the isp first, and same goes with dhcp... But still not a good optimal sort of setup..
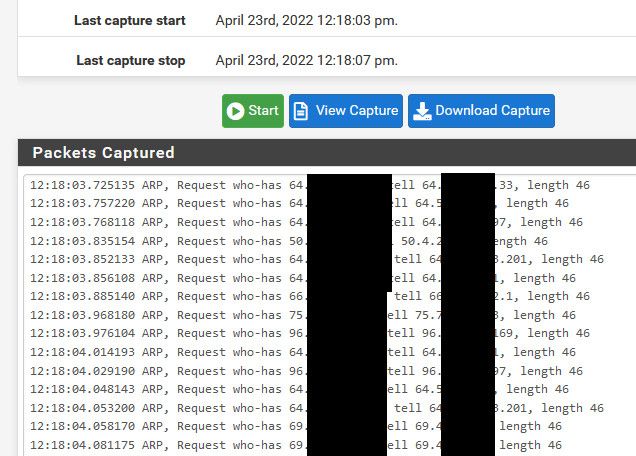
edit: see all the arp traffic ;) I blocked most of the IPs - because some of those are in the same network as my public.. The isp runs multiple L3 on the same L2, which Im not really a fan of either.. But hey its their network ;) I wouldn't set it up that way..
-
@johnpoz That must have been why snort blocked a bunch of tor stuff the other day someone was trying to do something invasive and the firewall blocked it, maybe they tried proxychains. I wonder why it's not just blocked by the ISPs as default. Adding the modem mac address did not work it just disabled the wan.
-
@jonathanlee I would contact your isp with your concerns - show them some of the traffic your seeing, I would throw in some sniffs of the traffic for good measure as well as your logs.
They may just blow you off, or maybe just maybe they will fix it up ;)
-
-
@jonathanlee said in Jump in blocks traffic "block bogon IPv4 networks from WAN (11001) 0.0.0.0:68 255.255.255.255:67 UDP":
I wonder why it's not just blocked by the ISPs as default. Adding the modem mac address did not work it just disabled the wan.
There are rules in place when you enable dhcp on your want to allow for answers to your dhcp request, etc. but your answer wouldn't come from 0.0.0.0 or it shouldn't etc. So answers to your dhcp request wouldn't be considered a bogon anyway.
-
Consolidated ISP said to mark them as ignore on firewall they are looking into it now.
-
@jonathanlee said in Jump in blocks traffic "block bogon IPv4 networks from WAN (11001) 0.0.0.0:68 255.255.255.255:67 UDP":
mark them as ignore
That is default what happens nothing to do but not log them so you don't fill up your logs ;)
they are looking into it now.
Hear that all the time.. Please let us know what they say
-
Info on the "malicious stuff" that could occur with this going on with the ISP side.
"Adversaries may redirect network traffic to adversary-owned systems by spoofing Dynamic Host Configuration Protocol (DHCP) traffic and acting as a malicious DHCP server on the victim network. By achieving the adversary-in-the-middle (AiTM) position, adversaries may collect network communications, including passed credentials, especially those sent over insecure, unencrypted protocols. This may also enable follow-on behaviors such as Network Sniffing or Transmitted Data Manipulation.
DHCP is based on a client-server model and has two functionalities: a protocol for providing network configuration settings from a DHCP server to a client and a mechanism for allocating network addresses to clients.[1] The typical server-client interaction is as follows:
The client broadcasts a DISCOVER message.
The server responds with an OFFER message, which includes an available network address.
The client broadcasts a REQUEST message, which includes the network address offered.
The server acknowledges with an ACK message and the client receives the network configuration parameters.
Adversaries may spoof as a rogue DHCP server on the victim network, from which legitimate hosts may receive malicious network configurations. For example, malware can act as a DHCP server and provide adversary-owned DNS servers to the victimized computers.[2][3] Through the malicious network configurations, an adversary may achieve the AiTM position, route client traffic through adversary-controlled systems, and collect information from the client network.
Rather than establishing an AiTM position, adversaries may also abuse DHCP spoofing to perform a DHCP exhaustion attack (i.e. Service Exhaustion Flood) by generating many broadcast DISCOVER messages to exhaust a network’s DHCP allocation pool."
If there is miss configuration that is allowing these requests to hit the modem why does the modem send it to it's lan ports. Who knows.
Logs are turned off.
Works Cite:
Adversary-in-the-middle: DHCP spoofing. Adversary-in-the-Middle: DHCP Spoofing, Sub-technique T1557.003 - Enterprise | MITRE ATT&CK . (n.d.). Retrieved April 25, 2022, from https://attack.mitre.org/techniques/T1557/003/
. (n.d.). Retrieved April 25, 2022, from https://attack.mitre.org/techniques/T1557/003/ -
@jonathanlee At all loss to why you posted that - is that what they sent you? Yeah no shit like I said you seeing that info points a bad configuration on their network to even to allow it.
Perfect example how simple it is prevent that sort of traffic from being seen by your connection isp would be turn on dhcp snooping as untrusted DHCP messages will be forwarded only to trusted interfaces. . So something like dhcp discover from a client would only go to the isp dhcp server(s), not every other client on the network.
Even the most basic smart switches normally support dhcp snooping, etc. I would assume the isp is using something a bit more capable than a $40 smart switch you could pick up at your local computer store ;) hehe
-
@johnpoz no I only posted this for reference information on reasons this should not be happening on the isp side. You said "malicious stuff" I wanted to add exacting details on how this malicious stuff could occur. This was a new reference on attack mitre posted recently so I wanted to share if others read this post.
The ISP already told me to ignore it.
Have a good day.
I edited it
-
@jonathanlee said in Jump in blocks traffic "block bogon IPv4 networks from WAN (11001) 0.0.0.0:68 255.255.255.255:67 UDP":
The ISP already told me to ignore it.
That was there official response? Yeah they just blew you off.. Sad to hear..