Router on a Stick - pfSense 2.6.0 with Cisco Catalyst1000
-
Greetings everyone,
I am new to pfsense, hoping to get a router-on-a-stick running with a cisco catalyst switch. I am currently running into issues when pulling a DHCP lease from my ISP via the WAN interface. I am not sure if the issue is due to misconfiguration of pfSense or the switch.
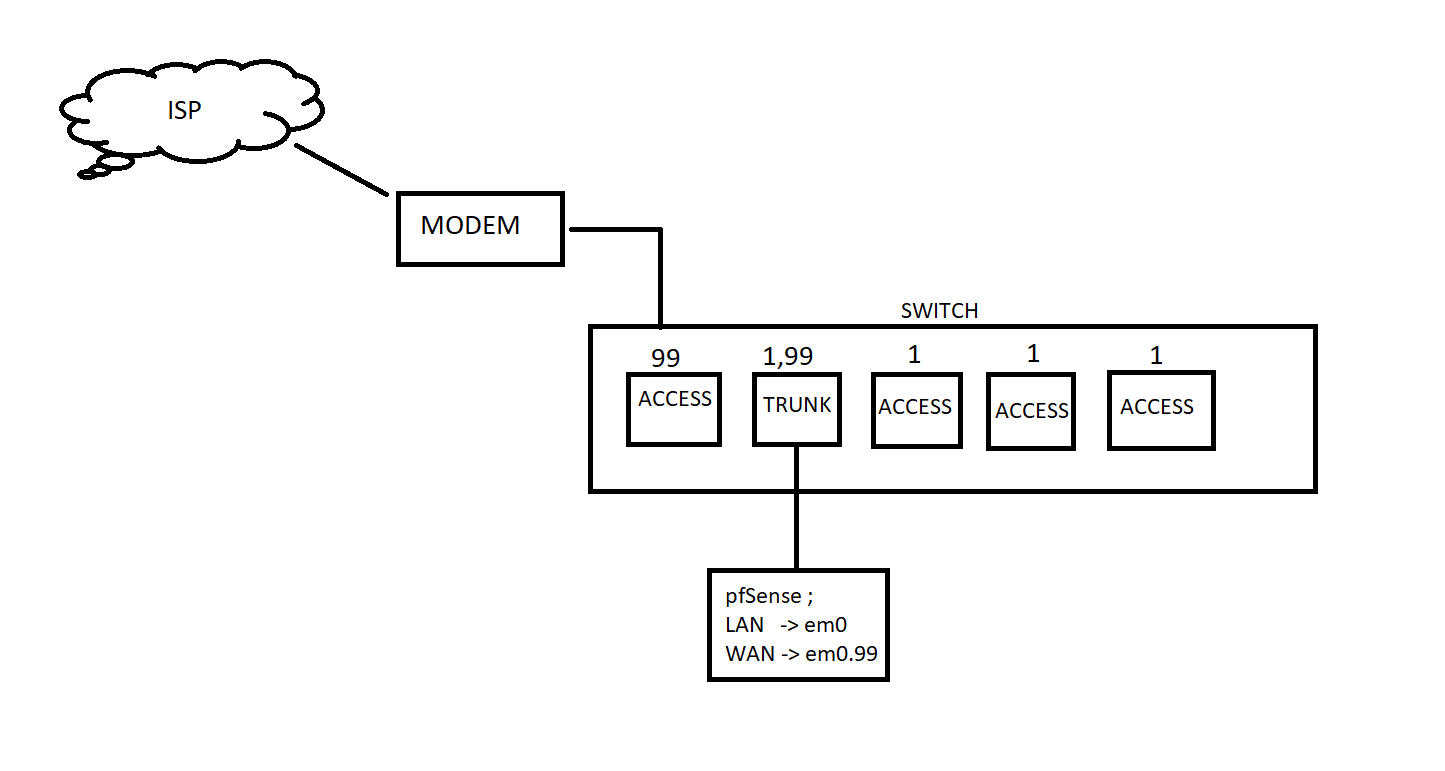
My network topology (the #s above the switchports are VLAN assignments):
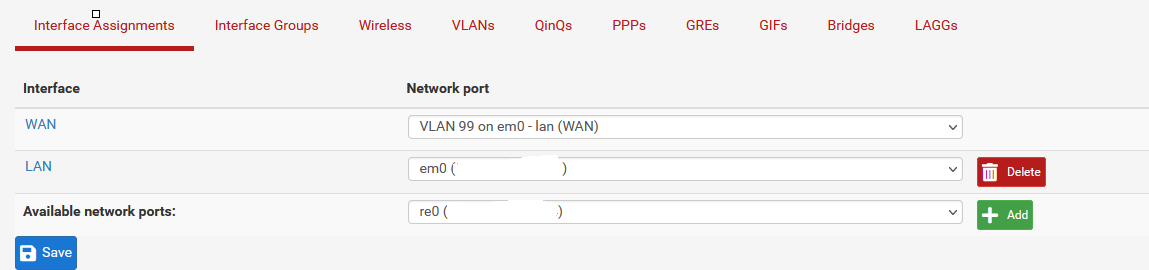
pfSense setup:
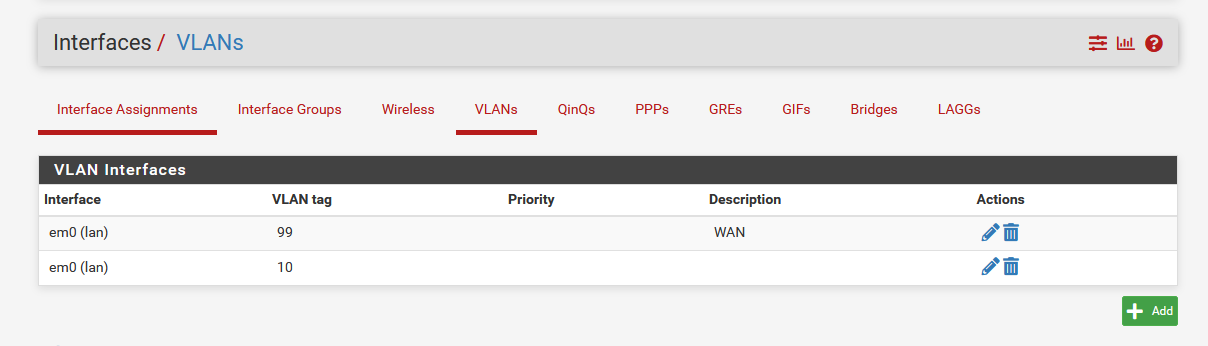
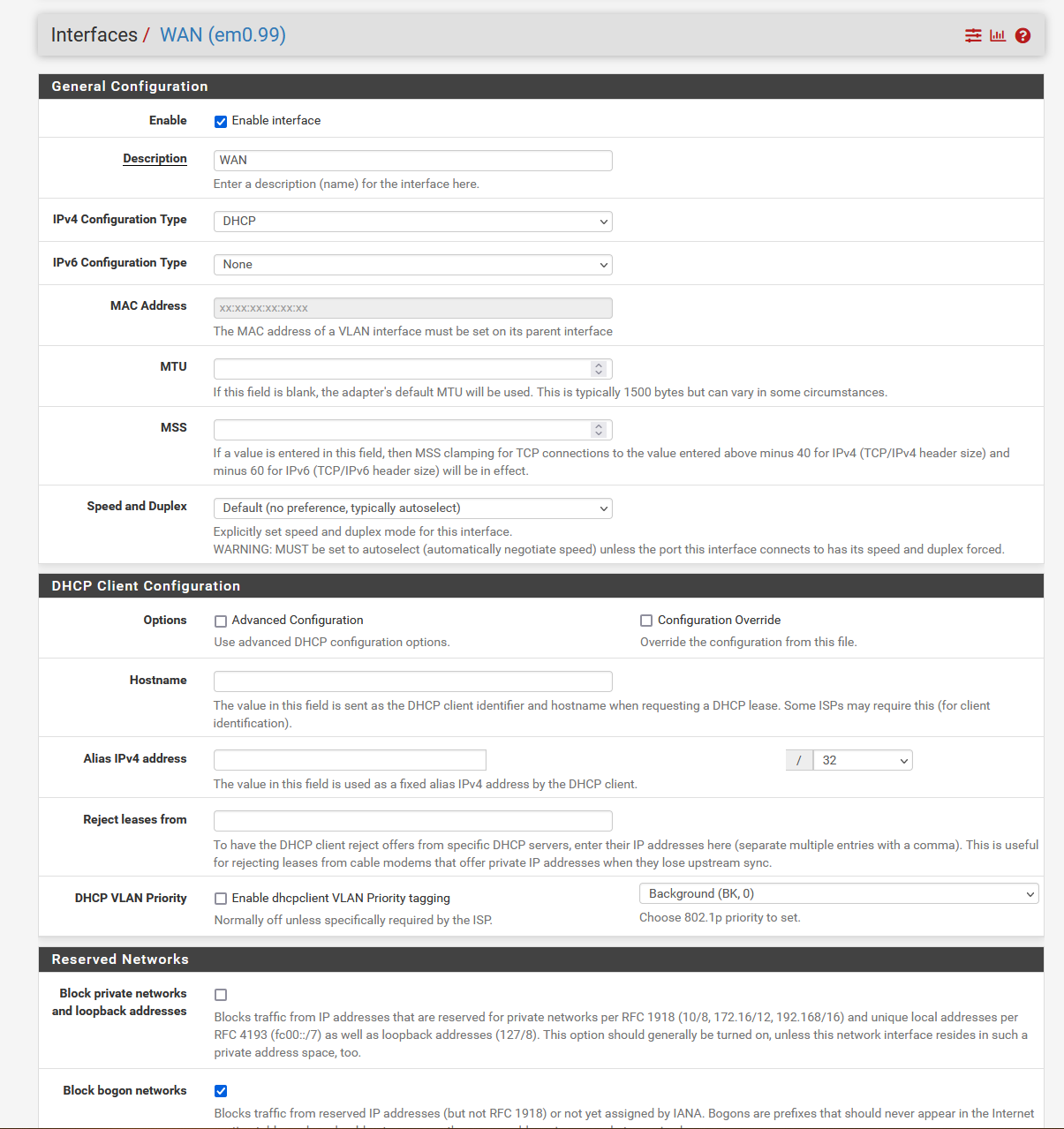
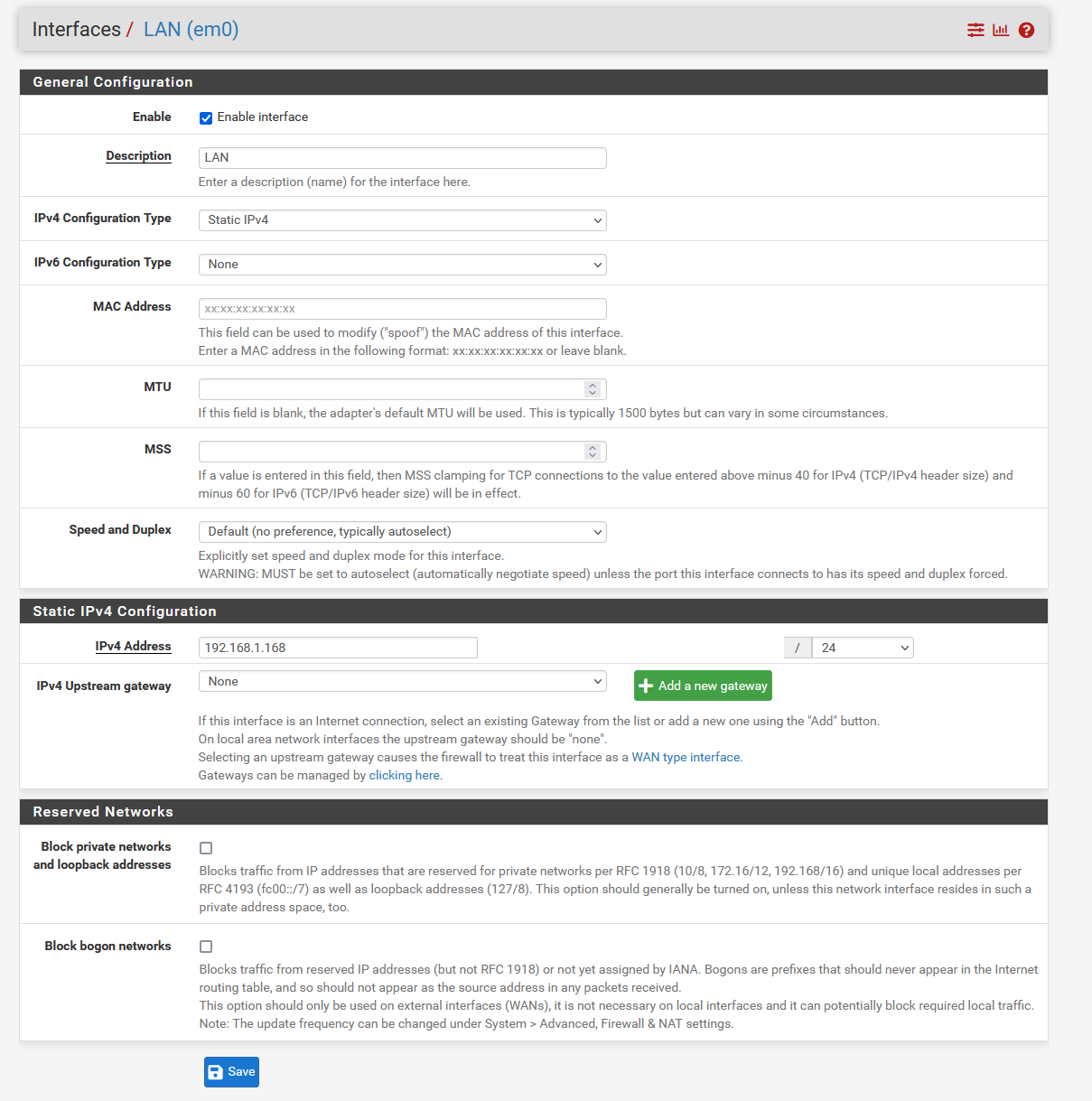
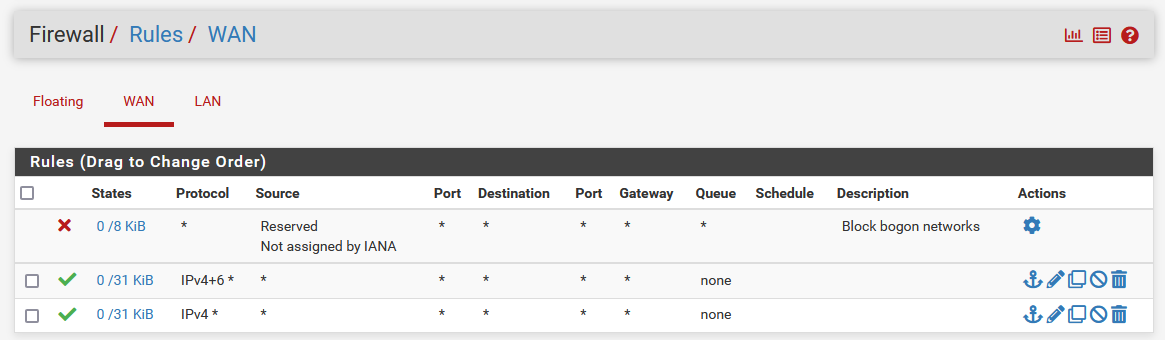
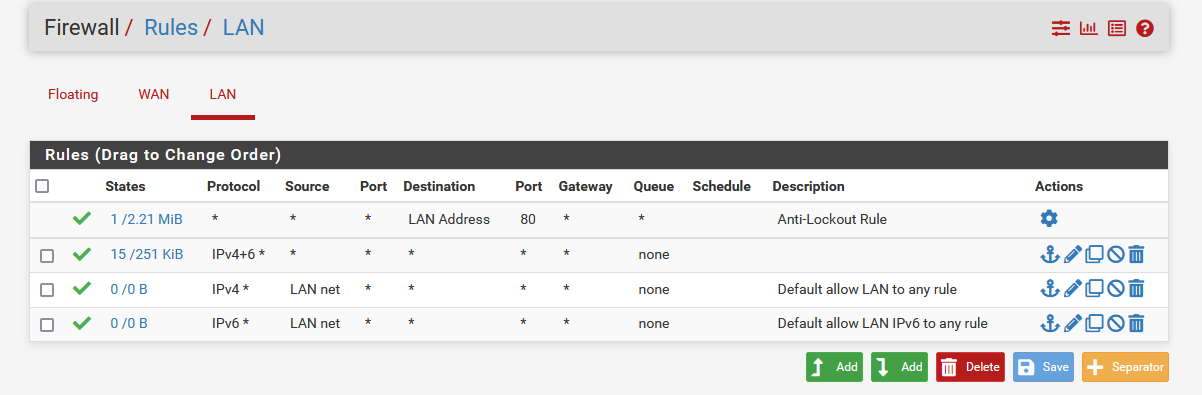
Switch setup:
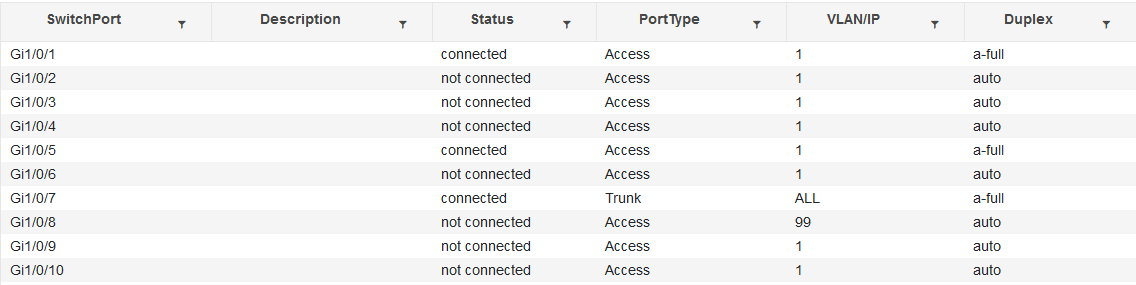
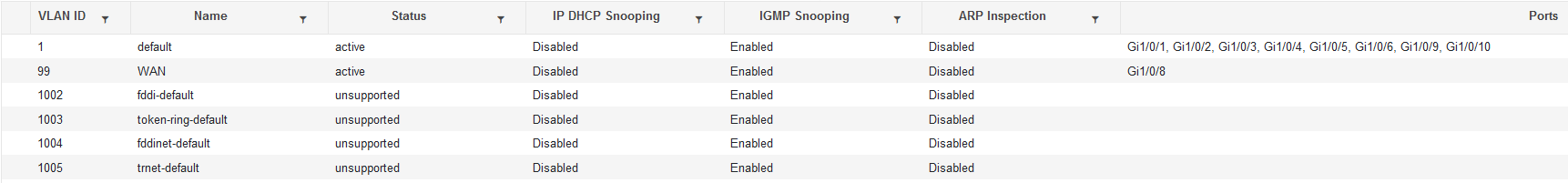
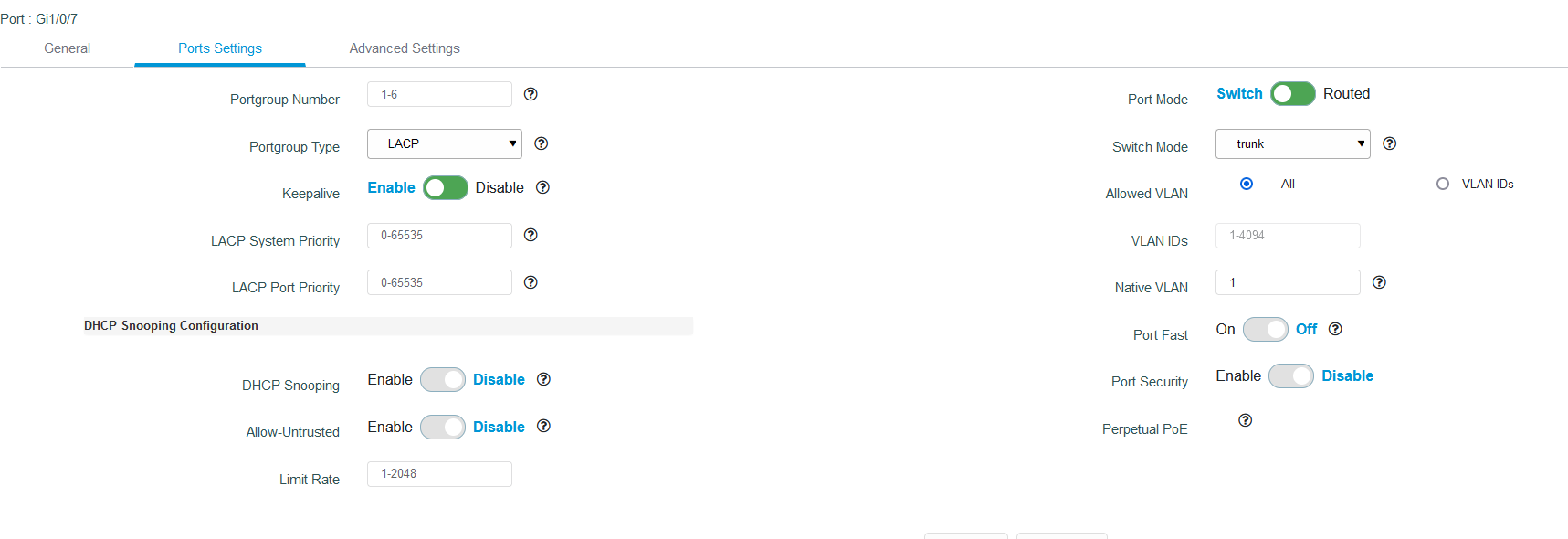
switchport trunk:
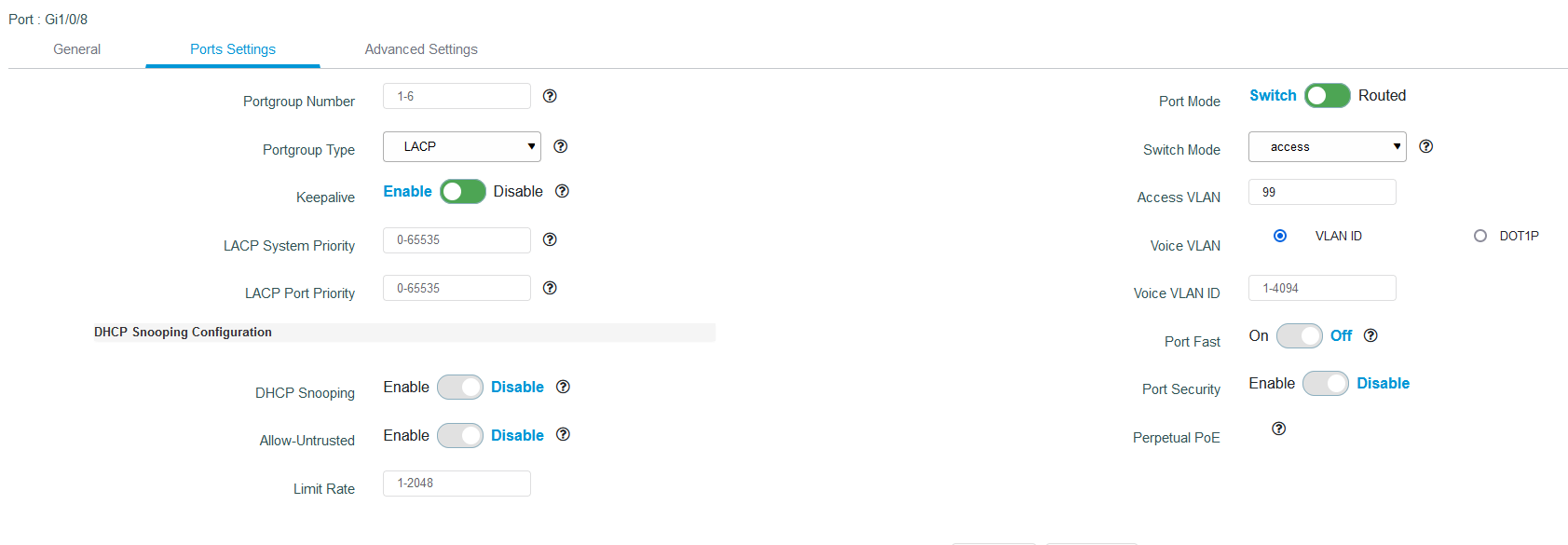
switchport for WAN:
switch running config:
ip igmp snooping vlan 10 mrouter learn cgmp
ip igmp snooping vlan 99 mrouter learn cgmp
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-**
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-**
revocation-check none
rsakeypair TP-self-signed-**
!
!
crypto pki certificate chain TP-self-signed-**
certificate self-signed 01
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
!
interface GigabitEthernet1/0/6
!
interface GigabitEthernet1/0/7
switchport mode trunk
!
interface GigabitEthernet1/0/8
switchport access vlan 99
switchport trunk native vlan 99
switchport mode access
!
interface GigabitEthernet1/0/9
!
interface GigabitEthernet1/0/10
!
interface Vlan1
ip dhcp client client-id ascii cisco-ccdb.93ac.3940-Vl1
ip address 192.168.1.254 255.255.255.0
no ip route-cache
!
ip default-gateway 192.168.1.1
ip http server
ip http banner
ip http secure-server
!
!
!
!
line con 0
line vty 0 4
login
transport input none
line vty 5 15
login
transport input none
!
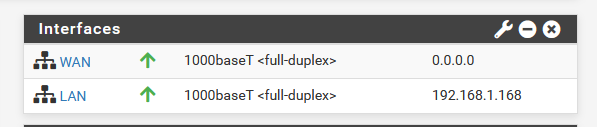
endIf I assign my WAN interface on pfSense to the parent interface of em0 then I am able to pull a DHCP lease from my ISP (requires reboot of modem though), however I cannot get the DHCP lease to go through when connected to a VLAN.
I am not sure if I need to set up some sort of routing rule on the switch to allow traffic to/from VLAN99, but I thought that was where pfSense would come into play.
Any ideas or suggestions?
Thanks for taking a look!
-
@spideypfsense At a glance, it looks like you're doing things somewhat backwards. Why are you trying to tag the WAN interface with VLAN 99?
What is the overall goal? If you're trying to segment your LAN using VLANs then your current setup will not work. -
In my experience running the ISP through a switch you need to have the WAN untagged and let the switch set the native VLAN the same on the "WAN" and ISP ports. You tag the LAN and set the native VLAN on the client ports.
-
@andyrh I asked about the overall goal because it seems like unnecessary complexity has been added here. The native VLAN is untagged, which means the untagged frames will end up hitting the parent interface, not the tagged (99) interface.
Is there a reason you're not plugging your modem directly into the WAN interface on PFsense?
-
@marvosa Currently this is a project to learn more about networking in general. Currently, my setup runs from ISP--> Modem -->Router/WAP-->Switch , the switch then provides ethernet to other devices. I am hoping to 1) install a firewall in front of my LAN and 2) convert my existing Router/WAP to become strictly a WAP that is connected to an access port on the switch. This should allow the WAP traffic to be forwarded to other devices for monitoring. I was following this guide but had to adjust for the differences between cisco terminology and tp link: https://www.joe0.com/2019/11/16/converting-single-nic-mini-pc-into-pfsense-router-firewall-by-using-virtual-lan-configuration-on-a-managed-switch/
My reason for not plugging modem/ISP directly into pfsense was to achieve this "router on a stick" configuration.
It was my hope that by tagging the ISP-connected switchport with vlan99, and creating a switch trunkport for vlans 1/99 (vlan1 is native) that pfsense is connect to, that the pfsense machine would be able to pass the traffic from WAN to LAN.
I am not sure I am explaining this very well, apologies for poor terminology. My assumption was that vlan1 was tagged for 802.1Q - but it appears that is not the case and is maybe why the author of the guide linked above uses VLAN 10 as well. @AndyRH I think you are saying this too - but with more concise wording!
thx for taking a look. I will rework the vlans and let you know how this goes
-
@marvosa I run the WAN through the switch so I can put a device on the ATT network if I need to without cabling and to see if I could make it work.
-
What IP range is used in the router before pfSense? I think pfSense is looking ok, don't know about that switch.