can't update rules suricata
-
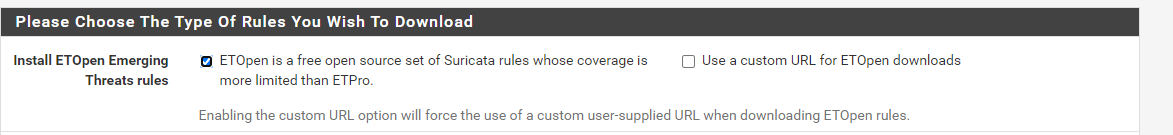
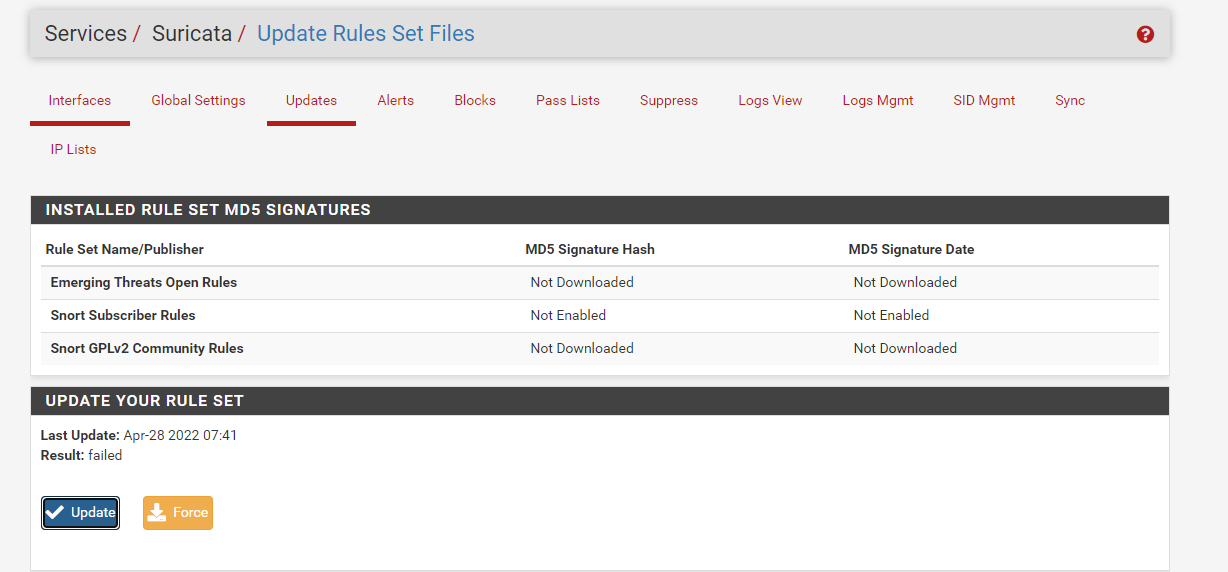
this is the result, sir, it still fails
-
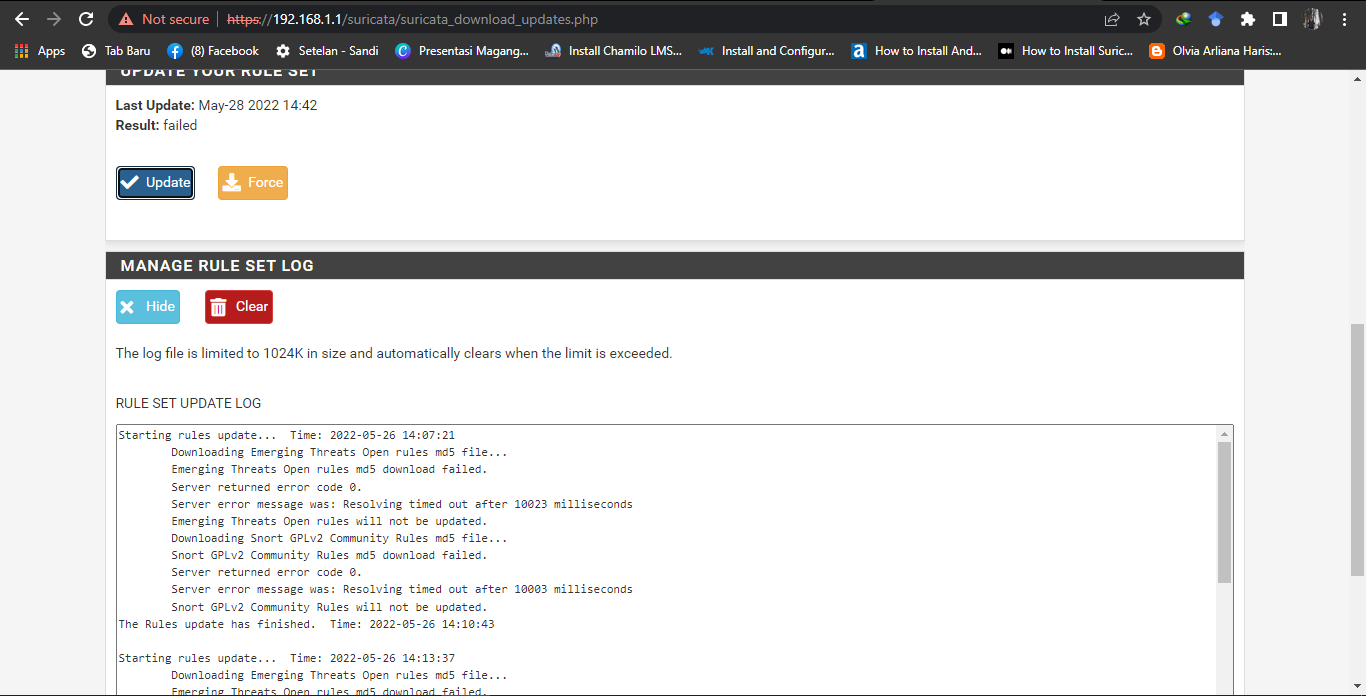
this is the display of the diagnostic dns lookup sir, there are 2 IP that appear
-
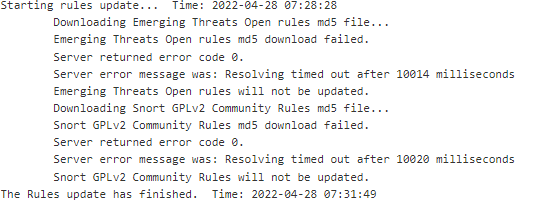
You are still having DNS issues. Notice in the update log snippet it says it waited over 10,000 milliseconds for a response and timed out. That means it waited 10 seconds for DNS to resolve the URL to an IP, then it timed out and gave up. So without DNS working correctly, you can't download rules.
Your DNS Lookup result:
@ezvink said in can't update rules suricata:
Examine the output from the DNS Lookup screen from DIAGNOSTIC > DNS LOOKUP:
Notice that the lookup first went to 127.0.0.1 (which would typically be
unboundrunning on the firewall itself), and that lookup timed out. The Query Time column says "No response".What is that second IP listed in your screenshot (the 192.168.18.1)? It resolved in 46 mSecs.
Here is the same command when run from my firewall:
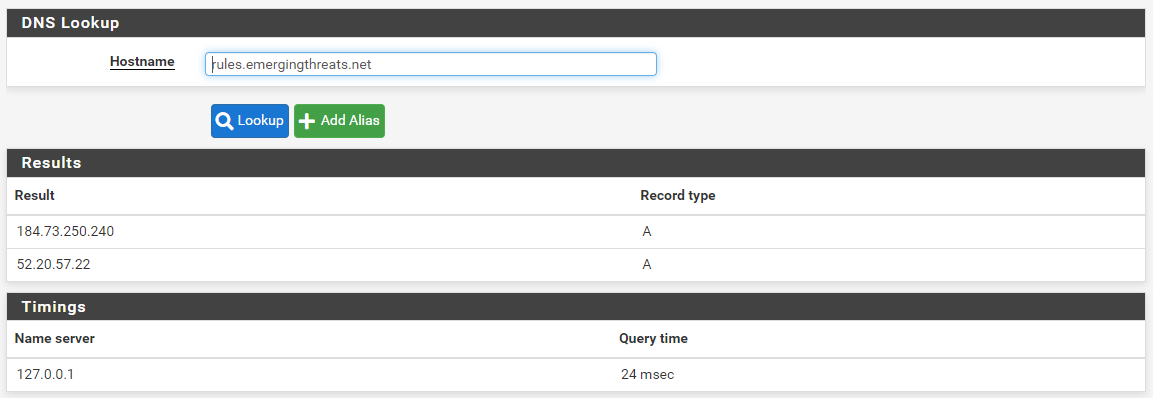
Notice that only a single Name Server was tried on my system, 127.0.0.1. That's what I would expect to have happened on your system as well. That loopback address represents the local DNS Resolver service on my firewall.
What do you have under SYSTEM > GENERAL SETUP in the DNS Settings section? This is what a typical out-of-the-box default setup should look like:
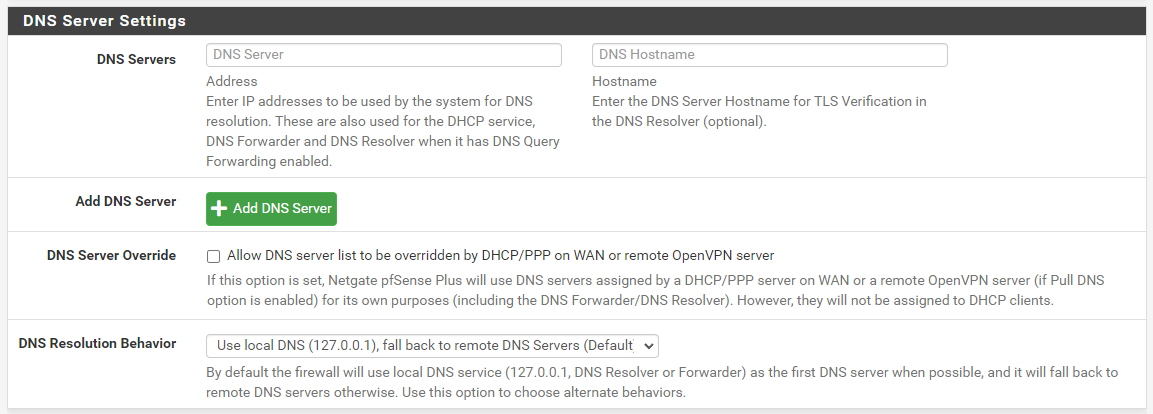
I would normally expect the
curlutility that is used by the Suricata package to download rules packages to wait long enough for that second DNS lookup to succeed. But maybe not ?? That's something under the control of that utility. All the Suricata package does is use the PHP system calls to download the file from the URL. The DNS configuration on your firewall is not optimized. The firewall is first trying to ask the localunboundservice (or possiblydnsmasqif you are using the DNS Forwarder instead of the DNS Resolver) for the lookup, and that lookup is timing out. Then it tried that 192.168.18.1 IP and that one worked. Maybe by then the PHPcurlprocess had given up, though. -
@bmeeks Then what should I do, sir?
-
@ezvink said in can't update rules suricata:
@bmeeks Then what should I do, sir?
Troubleshoot your DNS. That's where your problem is. You need to determine why 127.0.0.1 is returning "No response" when querying.
That's the best I can offer you for now. This is not a Suricata problem. It is a DNS resolution/configuration problem on your firewall. Examine the system log and see if
unboundis displaying any errors, or if it is frequently restarting, or not running at all.For starters, return all the DNS configuration on the firewall to its defaults. Or even better, reinstall pfSense from scratch and DO NOT change any of the defaults related to DNS -- nothing. Do not put any IP addresses in any text box anywhere related to DNS settings. In that setup,
unboundwill auto-start when the firewall boots and it will operate as a resolver. That's what you want. Something you changed on your firewall has caused DNS lookups to malfunction/timeout. You need to find out what that is and correct it. -
@ezvink ASI wrote above, “Have you tried restarting the DNS Resolver service, or your router?”
-
@bmeeks I have a question for you sir.
is installing packages for snort and suricata the same? if it's the same I don't get this kind of problem when installing packages on snort.
please sir, can you help me to solve this dns problem? please tell me how -
I have restarted the dns solver sir, but it still fails when installing the suricata package
-
@ezvink said in can't update rules suricata:
@bmeeks I have a question for you sir.
is installing packages for snort and suricata the same? if it's the same I don't get this kind of problem when installing packages on snort.
please sir, can you help me to solve this dns problem? please tell me howThe two packages work generally the same way. When you install Snort, what rules packages do you enable for it? Perhaps you are not configuring any rules to download with it?
You may have something left over in configuration for Suricata that is breaking the package. Best approach in my opinion is to wipe the current machine clean, reinstall pfSense from a USB or CD ISO image, and start over fresh with installing Suricata. And do not attempt to import any previous configuration. Start with a new, green field installation.
-
@bmeeks
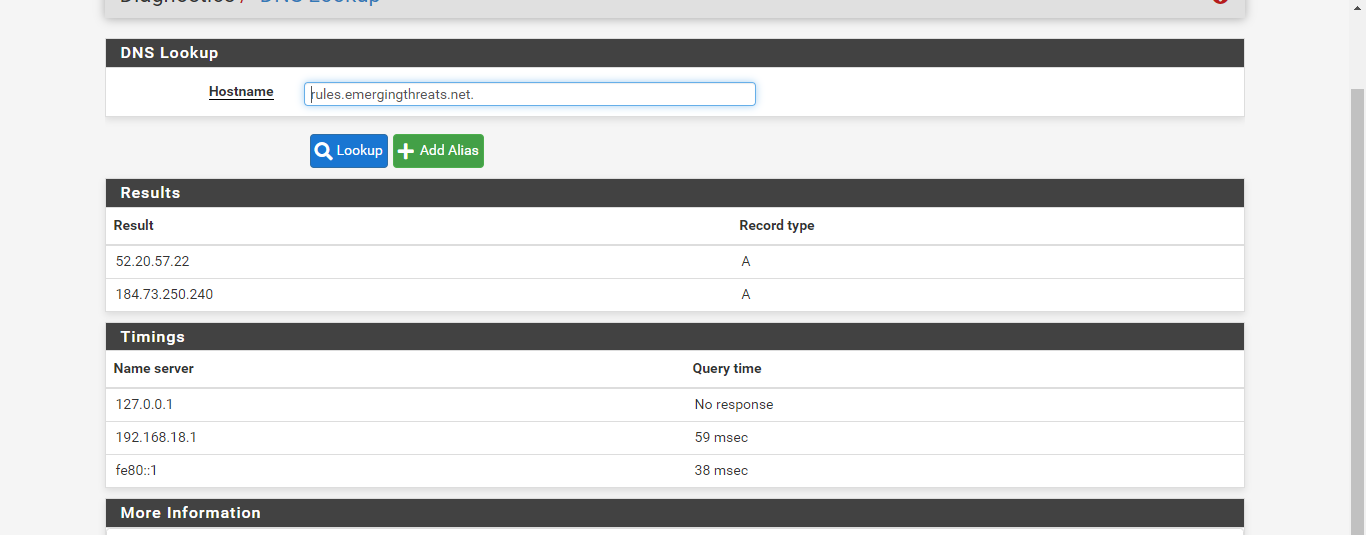
I've reinstalled pfsense from the beginning, sir and I didn't add any ip to the pfsense, but the DNS lookup is still the same as before -
@ezvink said in can't update rules suricata:
@bmeeks

I've reinstalled pfsense from the beginning, sir and I didn't add any ip to the pfsense, but the DNS lookup is still the same as beforeIt's clear from the above screenshot that the local DNS service is not available on your firewall. Notice the request to 127.0.0.1 timed out. That should not happen.
What device is the 192.168.18.1 IP address? Is that one of the interface IPs on the pfSense box? Why is the firewall even using that IP address as a DNS server? Out-of-the-box with a default configuration it would not do that. It would use 127.0.0.1 as the only DNS server. So it does not appear you did a reinstall of pfSense from a clean slate. If you did, that 192.168.18.1 IP address would not be there.
I just installed the Suricata package on a test virtual machine. Everything worked fine. It downloaded the rules package from Emerging Threats just fine. Here is the entire installation log :
>>> Installing pfSense-pkg-suricata... Updating pfSense-core repository catalogue... pfSense-core repository is up to date. Updating pfSense repository catalogue... pfSense repository is up to date. All repositories are up to date. The following 1 package(s) will be affected (of 0 checked): New packages to be INSTALLED: pfSense-pkg-suricata: 6.0.4_1 [pfSense] Number of packages to be installed: 1 The process will require 1 MiB more space. 149 KiB to be downloaded. [1/1] Fetching pfSense-pkg-suricata-6.0.4_1.pkg: .......... done Checking integrity... done (0 conflicting) [1/1] Installing pfSense-pkg-suricata-6.0.4_1... [1/1] Extracting pfSense-pkg-suricata-6.0.4_1: .......... done Saving updated package information... done. Loading package configuration... done. Configuring package components... Loading package instructions... Custom commands... Executing custom_php_install_command()...Saved settings detected... Migrating settings to new configuration... done. Downloading Emerging Threats Open rules md5 file... done. There is a new set of Emerging Threats Open rules posted. Downloading... done. Downloading Snort VRT rules md5 file... done. There is a new set of Snort rules posted. Downloading... done. Downloading Snort GPLv2 Community Rules md5 file... done. There is a new set of Snort GPLv2 Community Rules posted. Downloading... done. Downloading Feodo Tracker Botnet C2 IP rules file... done. Installing Feodo Tracker Botnet C2 IP rules...Feodo Tracker Botnet C2 IP rules were updated. Downloading ABUSE.ch SSL Blacklist rules file... done. Installing ABUSE.ch SSL Blacklist rules...ABUSE.ch SSL Blacklist rules were updated. Installing Emerging Threats Open rules... done. Installing Snort rules... done. Installing Snort GPLv2 Community Rules... done. Updating rules configuration for: WAN ... done. Updating rules configuration for: LAN ... done. Cleaning up after rules extraction... done. The Rules update has finished. Generating suricata.yaml configuration file from saved settings. Generating YAML configuration file for WAN... done. Generating YAML configuration file for LAN... done. Finished rebuilding Suricata configuration from saved settings. Setting package version in configuration file. done. Executing custom_php_resync_config_command()...done. Menu items... done. Services... done. Writing configuration... done. >>> Cleaning up cache... done. SuccessIf you examine that log output you can see it installed both Snort and Emerging Threats Open rules without a problem. Here is the log output from the UPDATES tab:
Starting rules update... Time: 2022-05-28 12:40:43 Downloading Emerging Threats Open rules md5 file... Checking Emerging Threats Open rules md5 file... There is a new set of Emerging Threats Open rules posted. Downloading file 'emerging.rules.tar.gz'... Done downloading rules file. Downloading Snort VRT rules md5 file... Checking Snort VRT rules md5 file... There is a new set of Snort rules posted. Downloading file 'snortrules-snapshot-29170.tar.gz'... Done downloading rules file. Downloading Snort GPLv2 Community Rules md5 file... Checking Snort GPLv2 Community Rules md5 file... There is a new set of Snort GPLv2 Community Rules posted. Downloading file 'community-rules.tar.gz'... Done downloading rules file. Downloading Feodo Tracker Botnet C2 IP rules file... Done downloading rules file. Extracting and installing Feodo Tracker Botnet C2 IP rules... Feodo Tracker Botnet C2 IP rules were updated. Downloading ABUSE.ch SSL Blacklist rules file... Done downloading rules file. Extracting and installing ABUSE.ch SSL Blacklist rules... ABUSE.ch SSL Blacklist rules were updated. Extracting and installing Emerging Threats Open rules... Installation of Emerging Threats Open rules completed. Extracting and installing Snort rules... Installation of Snort rules completed. Extracting and installing Snort GPLv2 Community Rules... Installation of Snort GPLv2 Community Rules completed. Copying new config and map files... Updating rules configuration for: WAN ... Updating rules configuration for: LAN ... The Rules update has finished. Time: 2022-05-28 12:41:02There is no problem with the Suricata package itself. Something is wrong with DNS on your installation. What that is, I have no idea. But until DNS works properly, Suricata is not going to be able to download rules. It fails to resolve each URL in your log output from the UPDATES tab.
-
Make sure that on the GLOBAL SETTINGS tab of Suricata, yours looks like this:
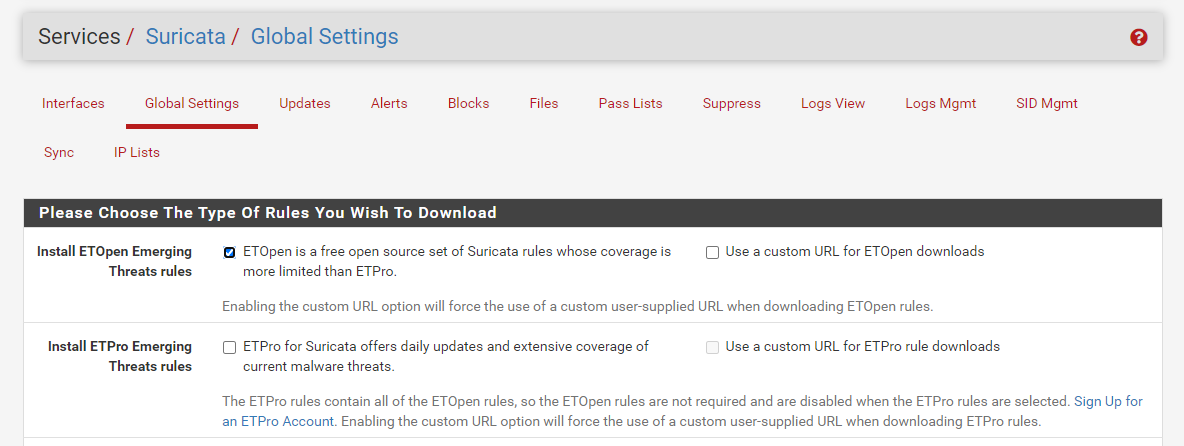
The "Use a custom URL for ETOpen downloads" checkbox should be clear (not checked). If you have it checked, remove any text you have in the Custom URL textbox, then clear the checkbox and save the change. You most definitely do NOT want to put a custom URL value (or any value there) for normal installs.
-
Make sure your General Setting page looks like this with two DNS servers such as here with OpenDNS or Google's 8.8.8.8 and 8.8.4.4
so you can finish your work...good luck!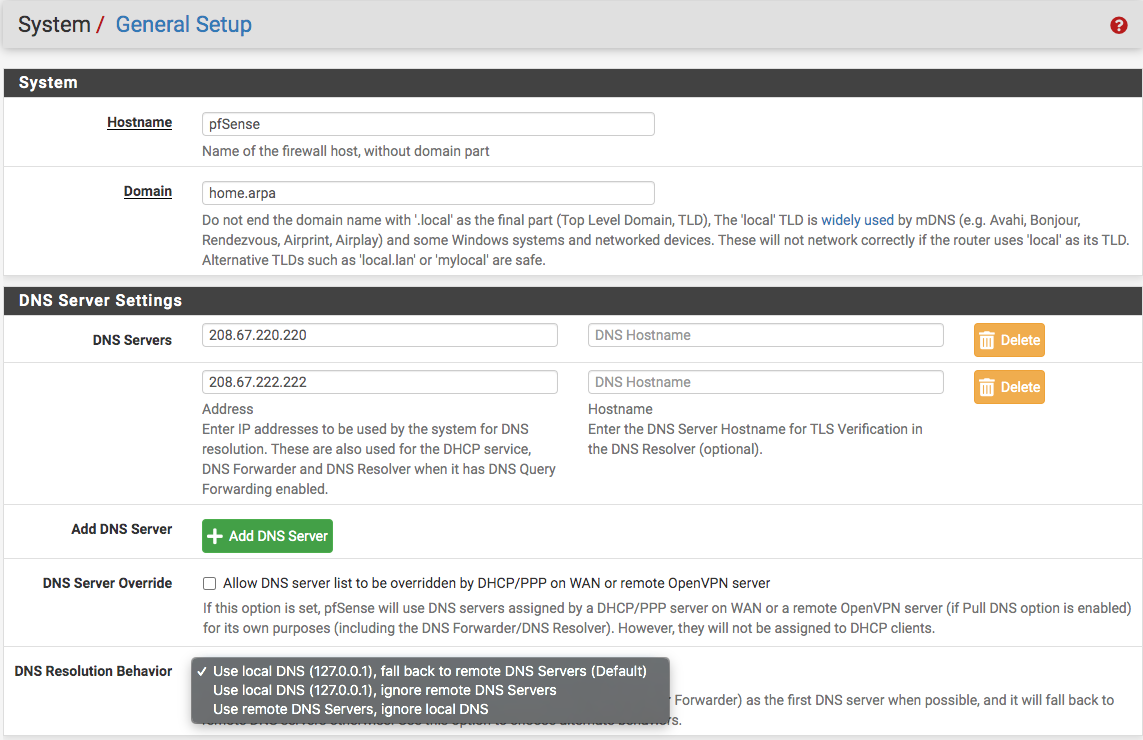
-
This post is deleted! -
@bmeeks
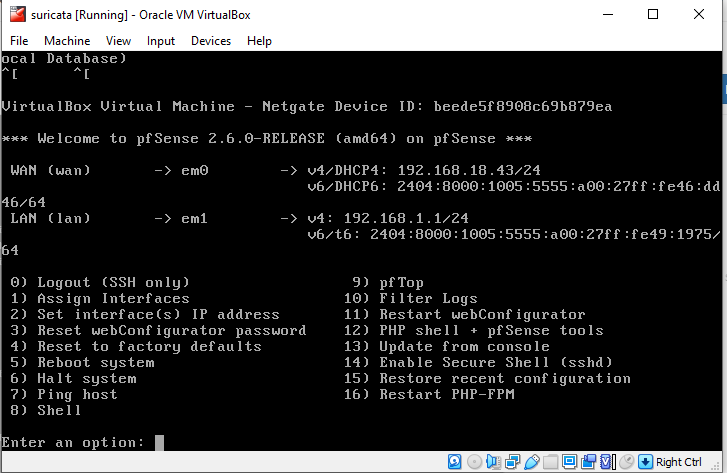
I installed pfsense on a virtual box, sir, and to install it using a wifi network that has an IP Gateway 192.168.18.1 automatically from my home router -
I have added the DNS 8.8.8.8 and 8.8.4.4, sir, but still when I update the rules for Suricata it fails
-
@bmeeks
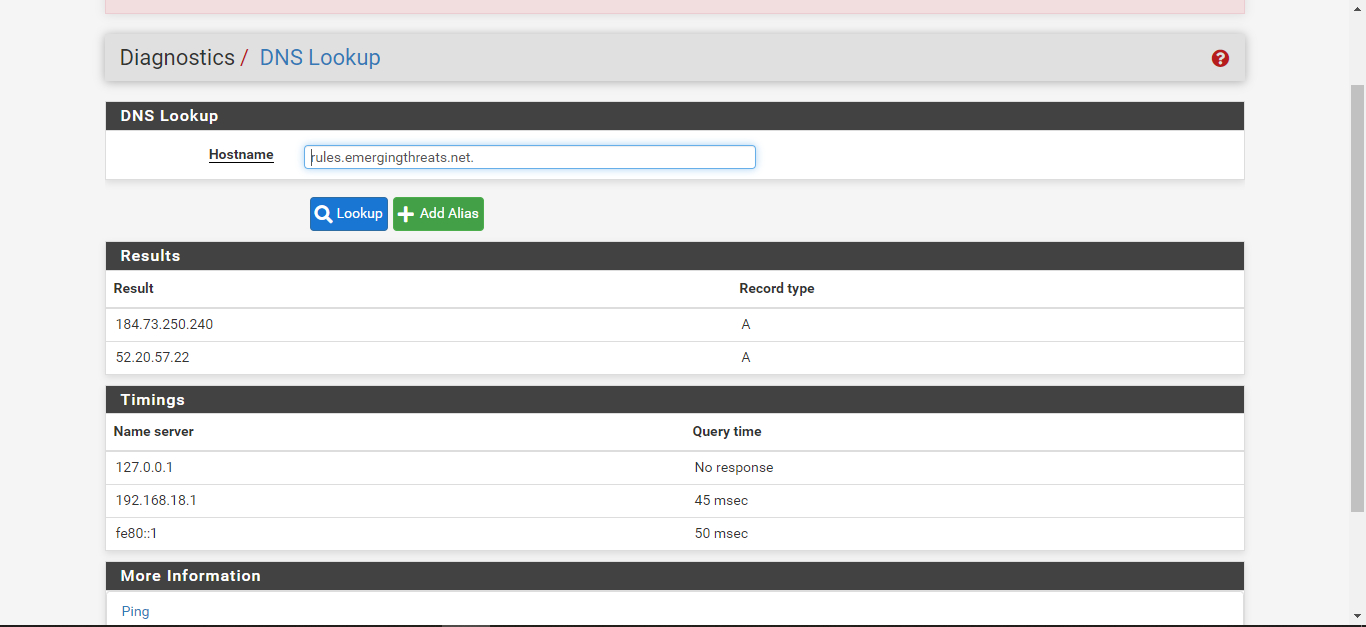
this is my pfsense i installed snort, still the same dnslookup still fails but i have no problem with snort rules snort exists. -
-
@bmeeks
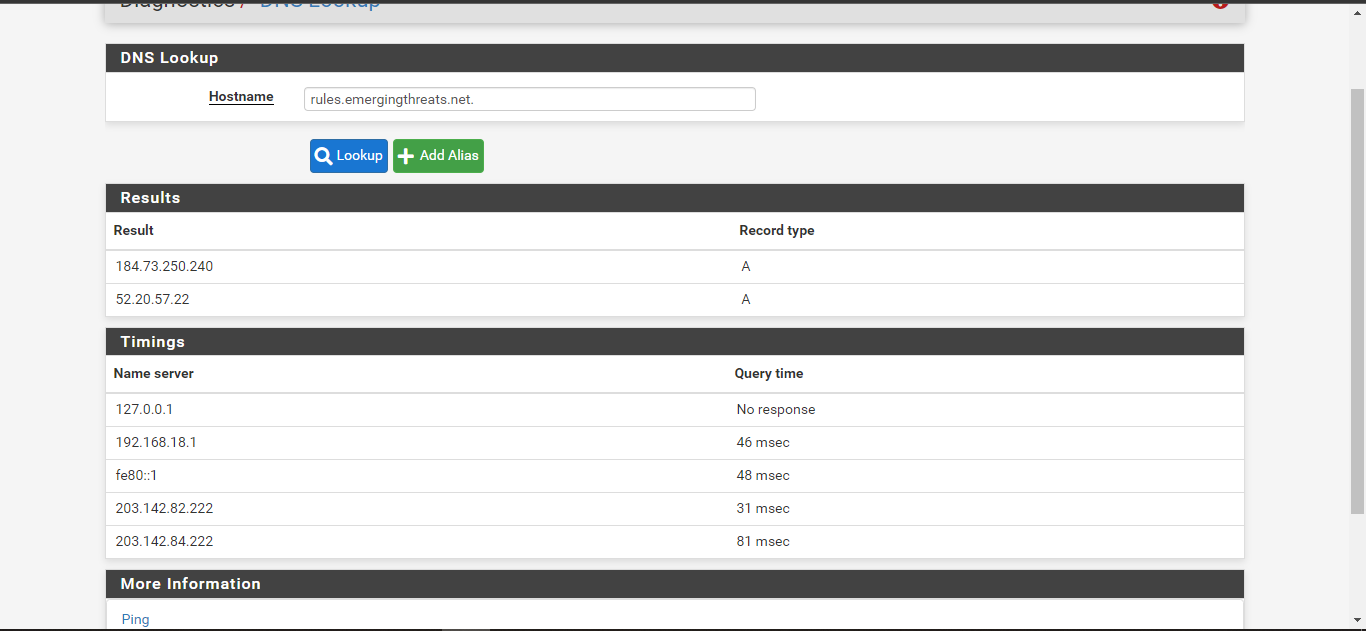
this is the pfsense I just reinstalled.
I tried to add a dns server from the ISP that I use, but still IP 127.0.0.1 does not respond, but the dns server that I use responds.
will this still not work? -
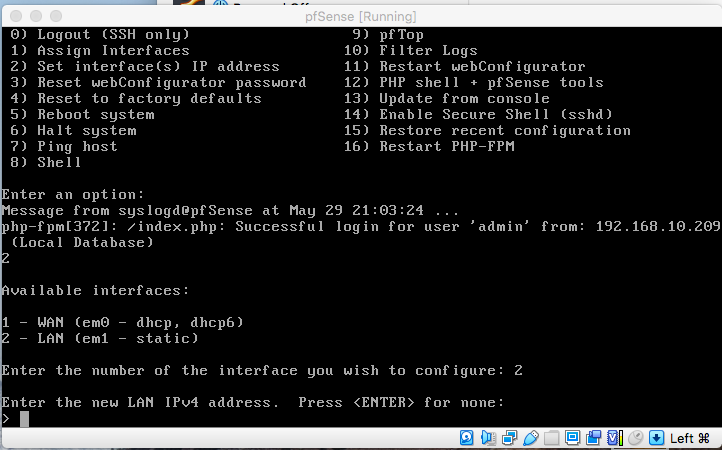
@ezvink I think I found your problem since you said you're using VirtualBox... it seems that your LAN is not on the same network as your WIFI although IPv6 seems to be. Try this...notice yours and mine... wondered whether you're able to see your webgui...
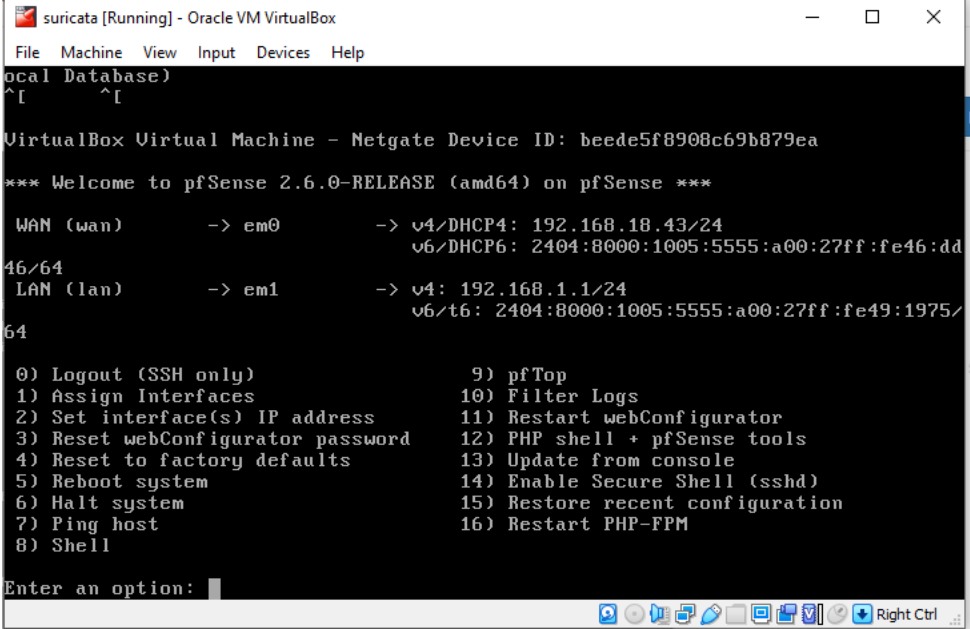
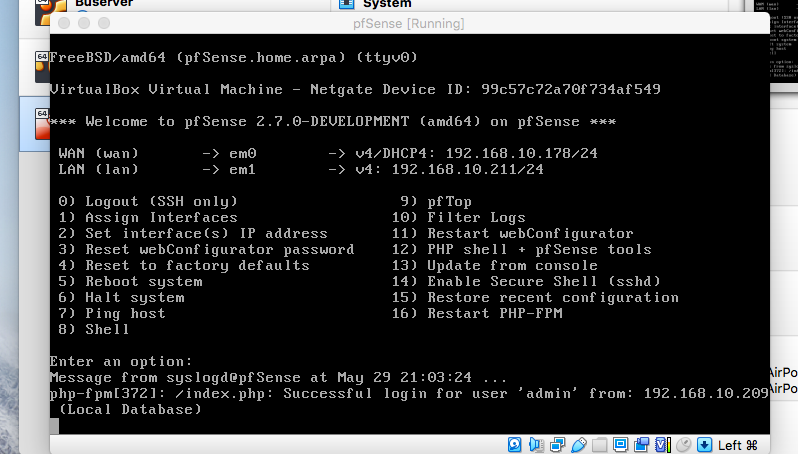
Set your adapter 2 on WIFI like here:
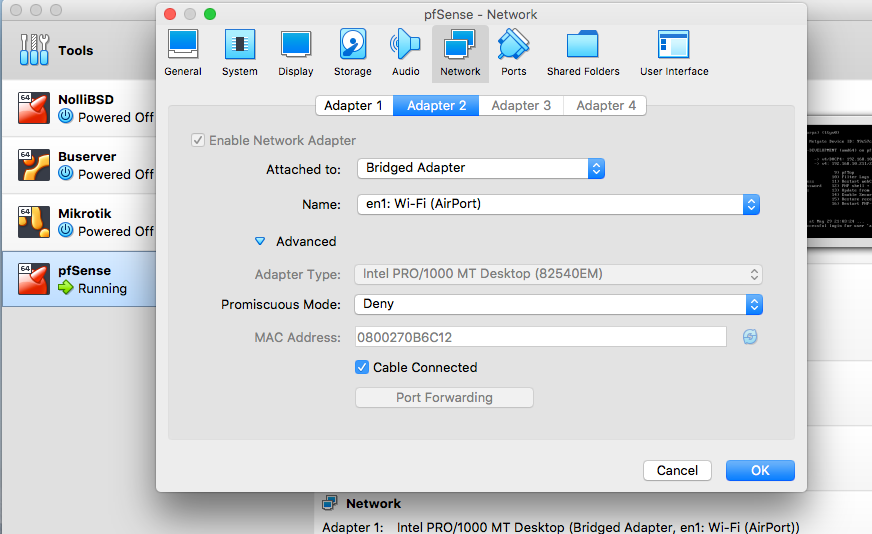
Then at the console select 2 then 2 and enter LAN address on your WIFI network exanple 192.168.18.211/24 and no to DHCP as well as no change to webgui. You should be able to login on your webgui and then you should be able to load Snort/Suricata.