Client Export fails after upgrade to 2.5.2 / 2.6
-
@sgw Yes, or at least related to it.
-
@sgw Actually, I misspoke in my earlier comment - the Remote Access (SSL/TLS) does work if the server is likewise configured. I originally tried to generate the Remote Access (SSL/TLS) client and use that to connect to the original server configuration. (Remote Access (SSL/TLS + User Auth)) It doesn't work, and obviously shouldn't. Likewise changing the server mode to just RA (SSL/TLS) and using the original client configurations also doesn't work. Setting the server mode the just RA(SSL/TLS) does work with the clients that have been exported with the same mode. My problem, like I am sure others have, is I have dozens of remote clients that use OpenVPN to connect and I don't want to go through the process of walking 30 or 40 users through the process to upgrade their client.
-
@kitdavis could you explain, why "(SSL/TLS + User Auth)" should not work? Why does that option exist then? Maybe I misunderstand.
What we would like to have: client certs plus user authentication. The certs come from the company's CA, not from an internal pfsense CA. We would also like to avoid having to import dozens of client certs or something.
-
@sgw Sorry for the confusion - I meant that having the server in one mode (RA (SSL/TLS + User Auth) and the client exported in a different mode RA (SSL/TLS) doesn't work. I too want the to utilize the client authorization as well.
-
@kitdavis How would you get the different mode? I don't see the choice to set something like "SSL/TLS + User Auth" (or else) in "Client Export".
-
@sgw are there any updates on this yet. I have 2 new users I need to add but am unable to export. I like others on here don't want to go through having to re do 30 users just to add 2 :(
-
@dave-street unsure what to reply. I have pfsense and OpenVPN authenticated against 2 LDAP backends now. Seems to work although the customer hasn't tested much yet. I can use my tunnel fine, using a user in LDAP.
Do you need a config snippet? or ... ?
-
@sgw I guess I have the same config as @kitdavis, Server Mode is Remote Access (SSL/TLS + User Auth), I suspect that if like others have stated I change the Server Mode, Remote Access to SSL/TLS the export will then work, but I will have to re-export all my other users. I was hoping not having to do this. Thanks,
-
I'm still having this issue and was hoping somebody has come up with a fix.. I try to export a new user and this is the error I get...
A private key cannot be empty if PKCS#11 or Microsoft Certificate Storage is not used.
Failed to export config files!I get the same error if I try to export from an older user or anything, for example "config file only" I'm going to have to change the server mode to SSL/TLS but will I get to see which clients are connected if I do this? I have PFsense and OpenVPN authenticated against the local database. All prior users is working fine, I just cannot export new or even current users since the upgrade to 2.6
-
@dave-street have you checked your OVPN server's SSL cert to make sure there's a PEM value?
-
@rcoleman-netgate Yes there is a x.509 PEM, certificate and private key data are both filled in.
-
In my case it looks like the problem is version 1.6_5
I am currently testing multiple setups. Both running 2.6.0, but the last system i set up is running 1.6_5, and here i get the same error as you do.
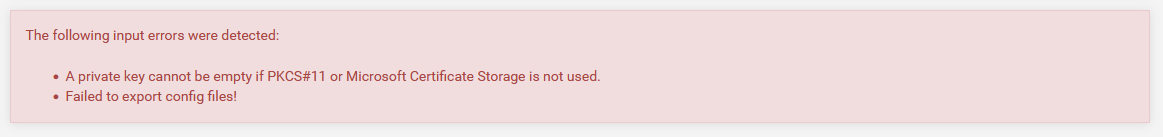
The following input errors were detected:
A private key cannot be empty if PKCS#11 or Microsoft Certificate Storage is not used. Failed to export config files!The working system runs 1.6_4 of openvpn-client-export. Here it works just fine.
-
Just upgraded the working system to 1.6_5, and guess what:
-
@professor The same happened to me! Do we already have a solution?
-
There is an issue open for this still: https://redmine.pfsense.org/issues/12475
If you're seeing the error now it would help to know how your VPNs are setup, including:
- Authentication type: SSL/TLS, User auth, or both
- Authentication source: Local, RADIUS, LDAP, etc.
- If the certificates are per-user (assigned on the user entry in the user manager) or just in the cert manager
- If the certificates in question have a private key present or not
EDIT: This should fix it: https://github.com/pfsense/FreeBSD-ports/commit/34355ebf71b78a6bfca47577fb979d0463684b8a
-
The new 1.6_6 version fixed it.
Thanks for responding fast :) -
Yes, 1.6_6 also fixed the problem for me as well.