Geoip firewall issue - questions
-
After I've updated from 2.5. to 2.6.0 , I was not able to browse the internet or connecting to sites like Steam.
I'm using pfBlockerNG and Geoip to allow only the
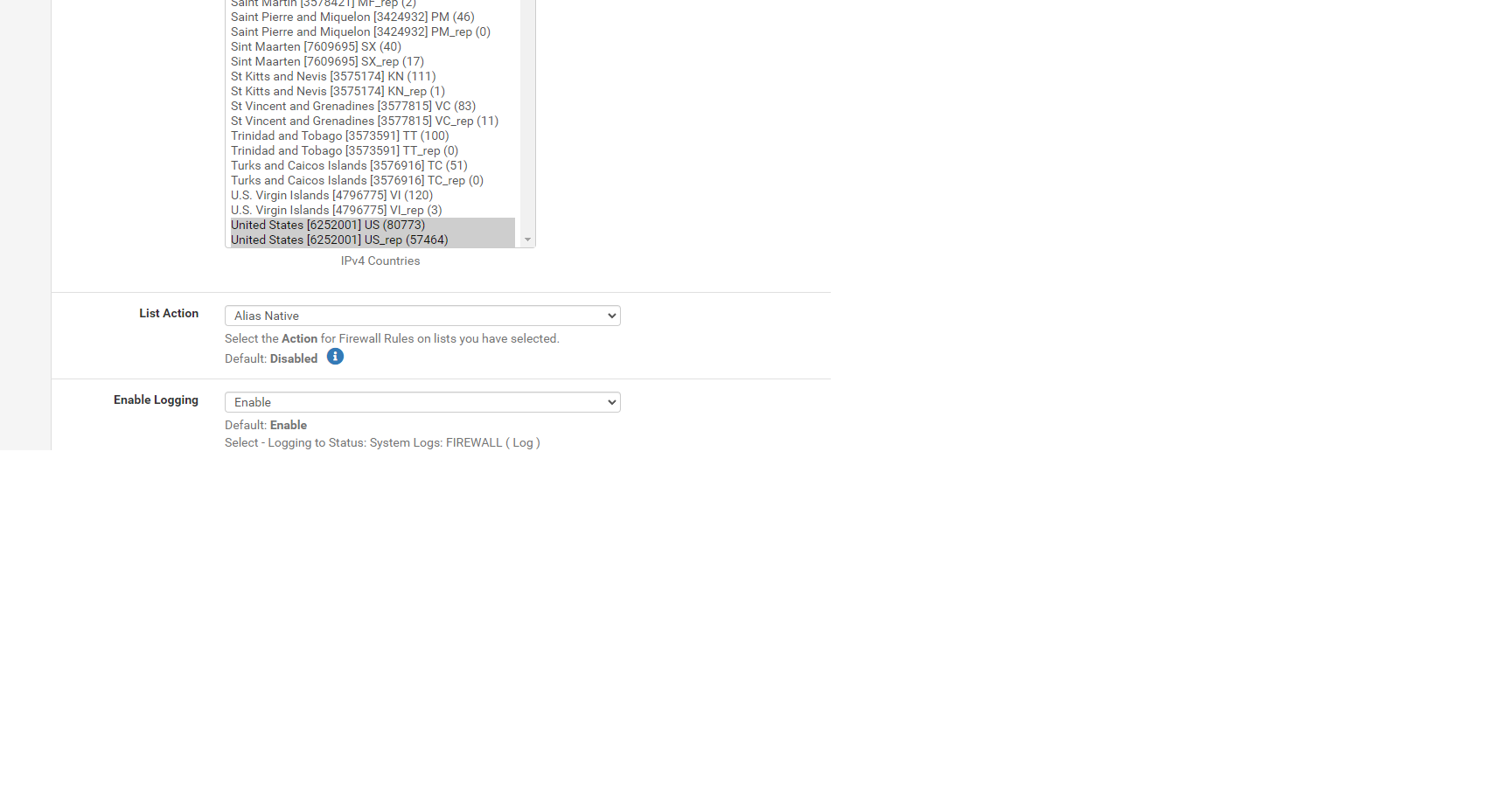
United States (80773) (135342)
United States rep (57464) (27411)
IPv4 and IPv6 ( have a website that was being accessed by countries outside the United States)the list action was "alias native"
I had to change it to "permit both" before I could now browse.- what is the difference between the two list actions?
- why did alias native prevent me from browsing?
- should I permit Both or only outbound or inbound
- what is United States rep ?
I have a native alias that points to my websites IP.
5) would the change to permit both override the alias, making it useless?
6) should I have a second alias for all other U.S. traffic and switch back to alias native?my main goal is to block all inbound traffic not requested from my systems, mainly from outside the U.S.
TIA Tim
system Info.
Version
2.6.0-RELEASE(amd64)
built on Mon Jan 31 19:57:53 UTC 2022
FreeBSD 12.3-STABLEThe system is on a later version than official release.
Version information updated at Tue May 3 20:22:59 UTC 2022 CPU Type
Intel(R) Core(TM)2 Duo CPU E7400 @ 2.80GHz2 CPUs: 1 package(s) x 2 core(s)
AES-NI CPU Crypto: No
QAT Crypto: No -
@tross9 Alias Native creates an alias but does nothing with it, so you can use the alias in your own rules.
Permit Both allows all traffic on WAN and LAN from those IPs.
Had you run an Update in pfBlocker after upgrading? I normally uninstall pfBlocker during pfSense upgrades, but still occasionally see warnings for an alias that "doesn't exist" after an upgrade, so I usually run an Update process.
_rep I believe is representative...seem to recall the example posted here was a US military base in another country would be US_rep.
In a pfBlocker IPv4 entry, under Action, click the "Click here for more info --> " (i) button and you'll see:
Select the Action for Firewall Rules on lists you have selected.
'Disabled' Rules: Disables selection and does nothing to selected Alias.
'Deny' Rules:
'Deny' rules create high priority 'block' or 'reject' rules on the stated interfaces. They don't change the 'pass' rules on other interfaces. Typical uses of 'Deny' rules are:Deny Both - blocks all traffic in both directions, if the source or destination IP is in the block list
Deny Inbound/Deny Outbound - blocks all traffic in one direction unless it is part of a session started by traffic sent in the other direction. Does not affect traffic in the other direction.
One way 'Deny' rules can be used to selectively block unsolicited incoming (new session) packets in one direction, while still allowing deliberate outgoing sessions to be created in the other direction.'Permit' Rules:
'Permit' rules create high priority 'pass' rules on the stated interfaces. They are the opposite of Deny rules, and don't create any 'blocking' effect anywhere. They have priority over all Deny rules. Typical uses of 'Permit' rules are:To ensure that traffic to/from the listed IPs will always be allowed in the stated directions. They override almost all other Firewall rules on the stated interfaces.
To act as a whitelist for Deny rule exceptions, for example if a large IP range or pre-created blocklist blocks a few IPs that should be accessible.'Match' Rules:
'Match' or 'Log' only the traffic on the stated interfaces. This does not Block or Reject. It just Logs the traffic.Match Both - Matches all traffic in both directions, if the source or destination IP is in the list.
Match Inbound/Match Outbound - Matches all traffic in one direction only.'Alias' Rules:
'Alias' rules create an alias for the list (and do nothing else). This enables a pfBlockerNG list to be used by name, in any firewall rule or pfSense function, as desired.Options - Alias Deny, Alias Permit, Alias Match, Alias Native
'Alias Deny' can use De-Duplication and Reputation Processes if configured.
'Alias Permit' and 'Alias Match' will be saved in the Same folder as the other Permit/Match Auto-Rules
'Alias Native' lists are kept in their Native format without any modifications. -
Thanks for replying and the permission explanations, but I'm still not 100% sure what alias native does,
does alias native permit the all inbound/outbound traffic from
United States (80773) (135342)
United States rep (57464) (27411)
like permit both and any alias' that I created I assume that it does, seeing that I just tried resetting the permissions back to alias native and I'm able to browse.what i would like to know is , how to set up the rules to prevent all unwanted traffic, i'm not sure if i'm setting up the rules correctly.
this is my current geoip settings
(
this is my only alias
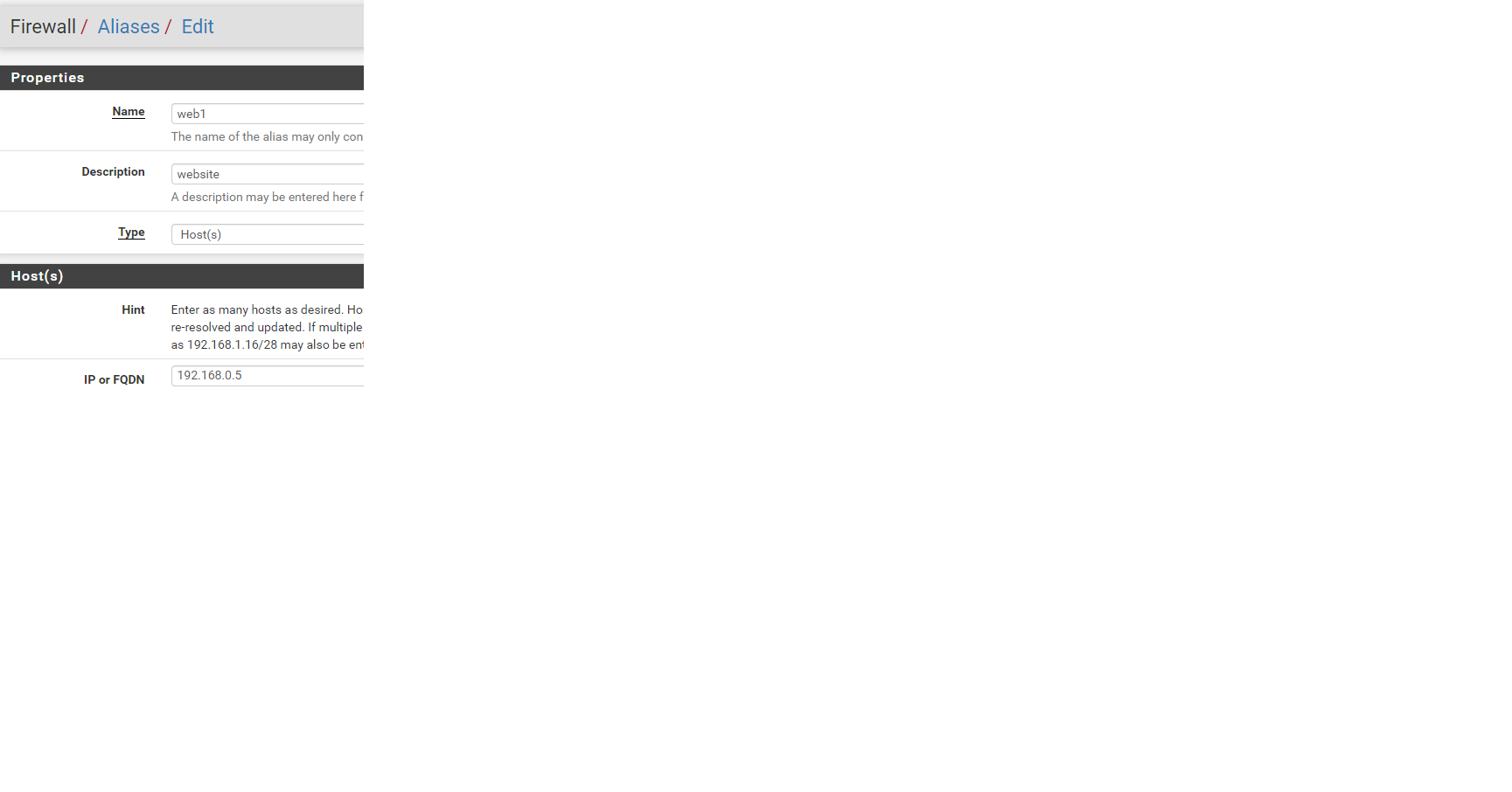
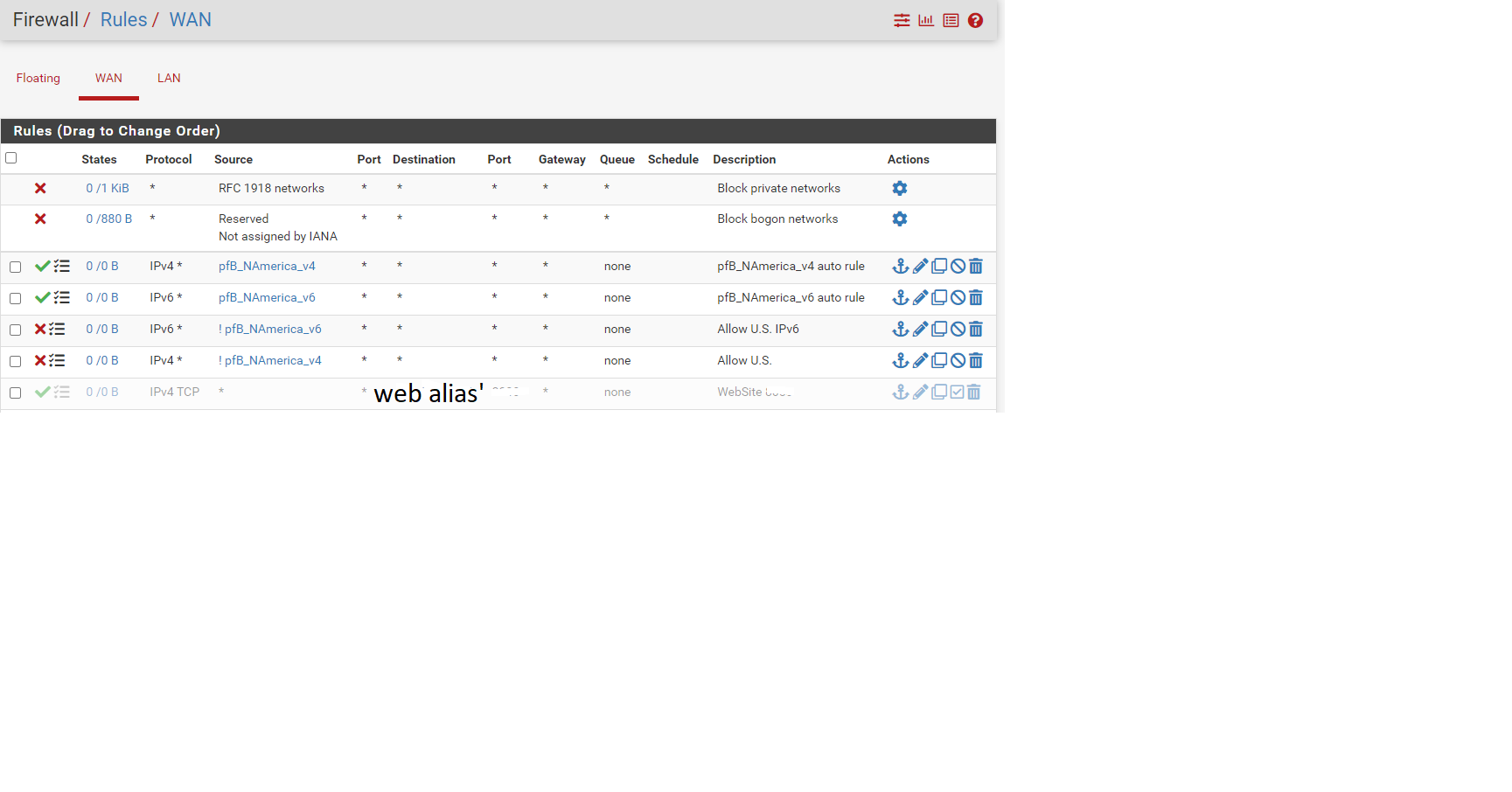
and rules
Again Thanks
Tim -
@tross9 Alias Native doesn't permit or deny anything, it creates an alias. When editing a rule you should be able to type "pfb" or "us" in a field that takes an alias, and pfSense will show matching names.
BTW if you are just looking for certain countries, and/or need multiple country aliases, another option is to enter them on the IP tab:
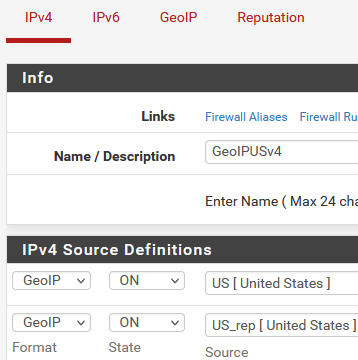
-
not sure where the entry you are showing is to be made, I assume that it is in
Firewall/pfBlockerNG/Edit/IPv4there is no geoip option -- i've registered for a MaxMind License Key and have the key in the 'MaxMind GeoIP Settings'so i should be using the geoip function, unless I've missed something.
these are the listed option under Firewall/pfBlockerNG/Edit/IPv4
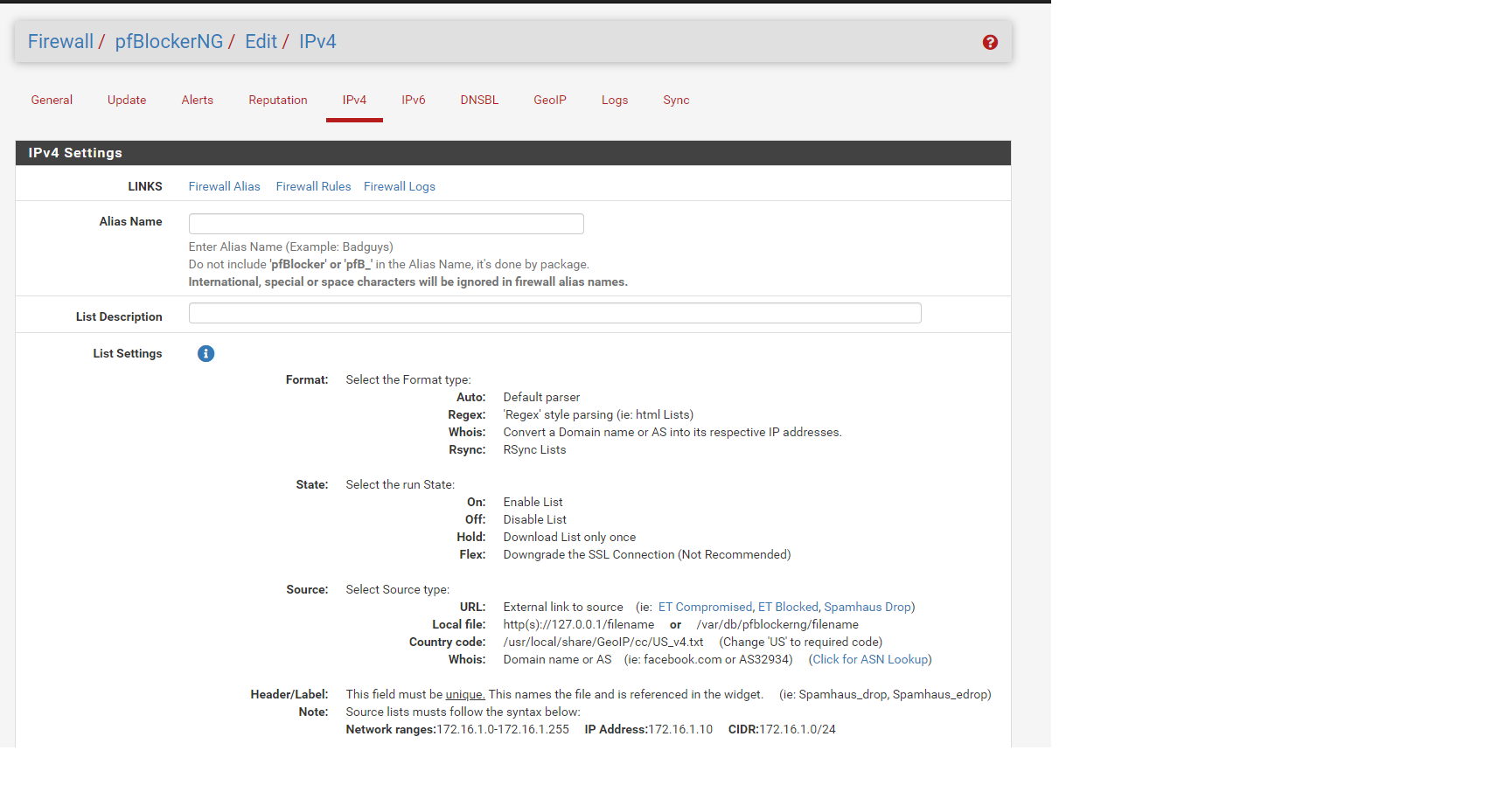
-
@tross9 You are using pfBlockerNG, I recommend pfBlockerNG-devel. Despite the name we have been using it for clients for a couple years, because we could not get the new MaxMind keys to work on pfBlockerNG.
-
sounds like pfBlockerNG-devel is the upgrade to pfBlockerNG
and if i'm correct, i should- save my Maxmind key
- uninstall pfBlockerNG ( or will installing pfBlockerNG-devel replace it)
- install pfBlockerNG-devel
- enter my Maxmind key
- set up the geoip ( select the countries and allow in and out bound)
and any alias' the i need. ( unless step 2 replaces the package and leaves the settings).
as i understand it firewalls deny all by default.
question: what would happen if I stop using pfBlockerNG ? (remove the allow US options)
technically all I want to prevent any unrequested access to my systems, and allow me to browse the internet and connect to systems like Steam and Discord, the only inbound traffic would be replies to requests, and allow private/whitelist access to my website. ( which is for family only, not the general public)
i have very limited firewall knowledge, mostly port forwarding and some know ip range whitelisting, but nothing on how to deny almost all traffic.history:
I started with a Ubuntu server for my family website.
found that countries like Turkey, Russia, China, Etc.. where accessing it.
I started to use Ubuntu to block the IP ranges but that proved to be to much,
found Pfsense and started whitelisting the families ip address but they kept changing
heard about pfBlockerNG and setup denying all ( and i mean ALL) of the countries.
they someone suggested allowing only the US.is there some tutorials or pdf's on details of pfBlockerNG , i'm still confused on the alias native, can't remember why it use selected, it may have been recommended four years ago when i first set up pfsense.
pfBlockerNG is the only package install, is there a recommendation for packages to install, I'm mainly concerned about network intrusion ( maybe install snort, if it easy to setup and use) .
-
@tross9 said in Geoip firewall issue - questions:
firewalls deny all by default
pfSense allows all outbound (LAN to any, including Internet). It denies inbound traffic on all other interfaces by default including WAN.
It sounds like you are hosting a web server behind pfSense so you have allowed that access.
Once a server is accessible on the Internet lots and lots of bots and scanners will probe it trying to hack in. That's just life.
Most residential IP addresses are dynamic meaning they can change over time. Some ISPs do this rarely, others frequently as they make network changes.
@tross9 said in Geoip firewall issue - questions:
i should
save my Maxmind key
uninstall pfBlockerNG ( or will installing pfBlockerNG-devel replace it)
install pfBlockerNG-develYes, uninstall the old first. pfBlockerNG-devel will import the settings.
I don't know of tutorials but I'm sure there are lots out there. There is a pfBlocker subforum here.
Alias Native just creates an alias and nothing else (after an Update is run). The purpose is so you can create your own rules, in whatever order you want. So you might set a NAT rule with source of US forwarding to your web server.
Snort is more complicated in the sense that one needs to understand why rules are triggering. I would read through all the pinned posts in the IDS subforum, as well as other posts there. If you enable it, I suggest not enabling blocking right away, just watch the Alerts and see what is triggering. There is a category specifically for web servers in the ETOpen Emerging Threats rules. Note HTTPS traffic can't be scanned by Snort, so if you only allow HTTPS and not HTTP to your web server there's not much point.
-
Steve , thanks for the info.
I have some question about pfBlocker , so i'll have to give the pfBlocker subforum a look.
again thanks, tim
-
look like PfBlocker was the reason It was blocking all outbound traffic.
it looks like, if I made a change in the NICs, trying to change a 10/100 for a gigabit or back , I would not be able to browse the internet , it look like if i ran the blocker update things would get corrected or at least it appeared to work 99% of the time.
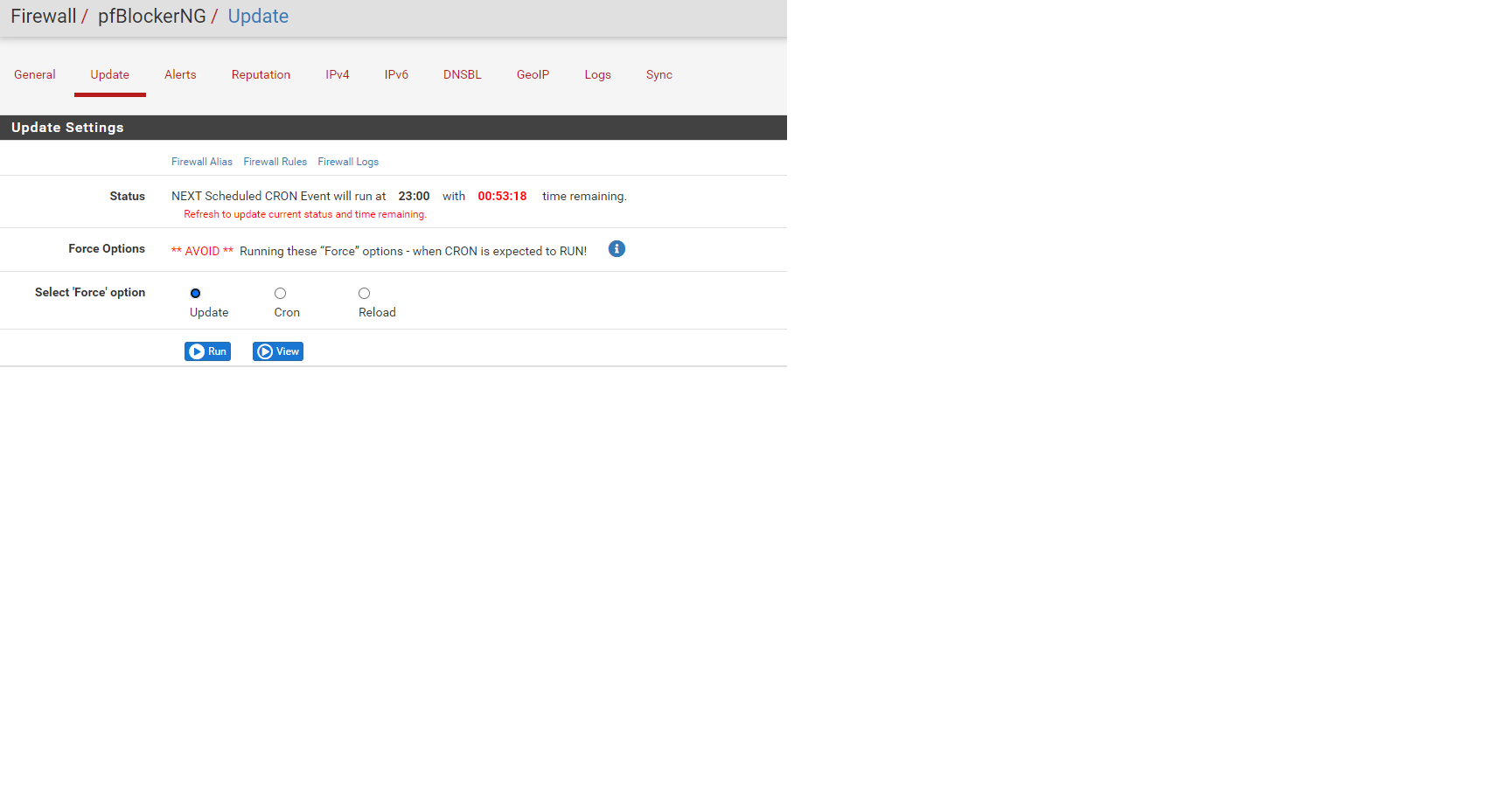
and now it looks like i have duplicate rules
one set that allows US (auto rule)
and one that allows US inverted ( !pfB_NAmerica_v6 )
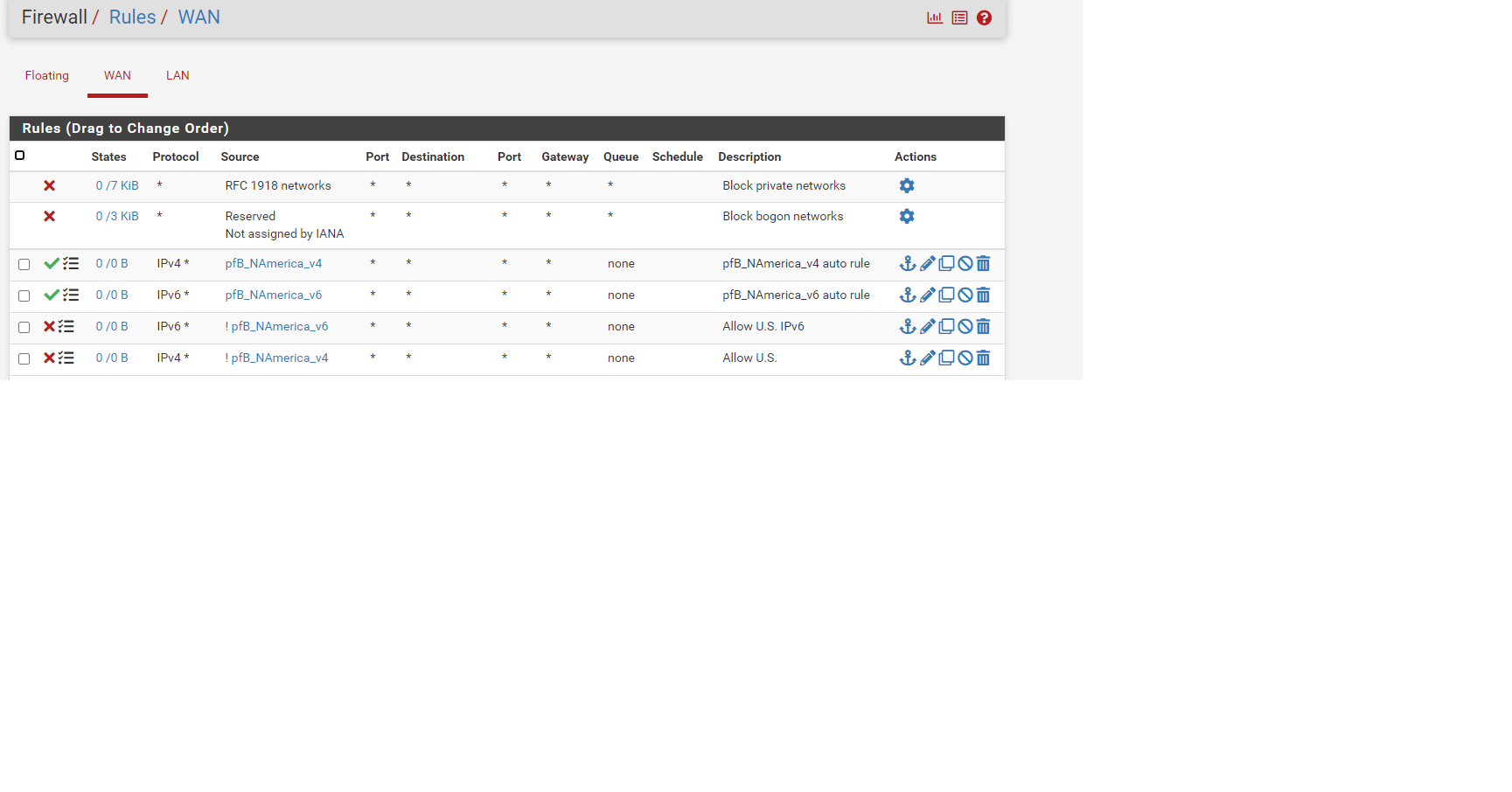
I assume I can delete one set, i think the inverted rules might be slower to process, assuming that if not = is slower to process then if =
i'll see if I can install pfblocker-dev later, been a few days of fighting issue on not browsing, things are working and what to let the dust settle .
Tim