Where to submit need feed for pfBlockerNG
-
I have added it to my feeds, i want to get it added to the overall list that pfblocker comes with.
-
@shoulders said in Where to submit need feed for pfBlockerNG:
https://github.com/dibdot/DoH-IP-blocklists
@nollipfsense said in Where to submit need feed for pfBlockerNG:
pfBlockerNG menu, you'll find it
I run pfBlockerNG-devel v3.1.0_4 under pfsense v2.6.0
Looking in
pfsense -> Firewall -> pfBlockerNG -> Feeds
I can find IPv4, IPv6, DNSBL feeds for DoH but none appear to use github.com/dibdotIs there somewhere else I'm suppose to look?
-
I know how to add a custom feed
 but thanks for the clear answer.
but thanks for the clear answer.I want to get this feed added as a list within the pfBlockerNG package under the Alias/Group DoH and not a custom group.
This list is bigger than the others and updated more recently.
These are examples of Pre-rolled Alias/Groups under the feeds TAB.
- Cryptojackers
- DNS_6
- EaslyList
- Firebog_Malicious
- DoH (which has 'The Great Wall', 'Bambenek Consulting', 'Dallas Haselhorst.)
I might look at https://redmine.pfsense.org/issues
This is also so other people can benefit.
-
-
I have just also done some feature request for these at https://redmine.pfsense.org/issues
-
@shoulders said in Where to submit need feed for pfBlockerNG:
I know how to add a custom feed
Sorry about being cryptic, that post was not aimed at you as you had already said that is what you have done but rather addressing
@nollipfsense said in Where to submit need feed for pfBlockerNG:
If you explore the pfBlockerNG menu, you'll find it...no one will hold you hands and lead you to the promised land.
@shoulders said in Where to submit need feed for pfBlockerNG:
I have just also done some feature request for these at https://redmine.pfsense.org/issues
That is unlikely to achieve your aims.
-
The default feeds in pfBlockerNG-devel are in pfBlockerNG-devel not pfsense.
-
To identify required changes in pfsense use https://redmine.pfsense.org/issues
-
Changes to pfBlockerNG-devel are done by the pfBlockerNG-devel developer BBcan177
-
I do not know how the github.com/dibdot feed compares to those already included in pfBlockerNG-devel nor what criterion BBcan177 uses when selecting feeds to include.
-
-
@patch said in Where to submit need feed for pfBlockerNG:
s there somewhere else I'm suppose to look?
I am not at my machine presently to take a screen shot; however, there is no DOH list or a need for such list. Why, cause if one configures one's pfSense to be the only source to resolve DNS, then all that's need in pfBlockerNG is to turn on "don't allow DoH."
-
The quick version:
There is a small list (Great Wall, Oneoffdallas_DoH, Bambenek_DoH ) and you need to employ block lists to beat DoH. DoT and external DNS queries can be blocked with standard firewall rules. You need to do all of these and then configure your resolver to use encryption (DoT) to an external secure full recursive resolver such as Quad9 that supports DNSSEC to get any protection from DNS being sent out by malicious software on your network."don't allow DoH." - This is just a block list but is not a very large one. I assume that you are on about the one in SafeSearch.
Hope this point you in the right direction
-
@shoulders Okay there is a list; however, all that you're doing can be done with pfSense in my case. I don't have any malicious software on my network that is limited to out family, no one else. All devices must use pfSense to resolve DNS request, no deviation. I have a guest network for such purpose that is separate from my personal network. If one chooses to use external DNS, that's find but is totally unnecessary...see screen shots below.
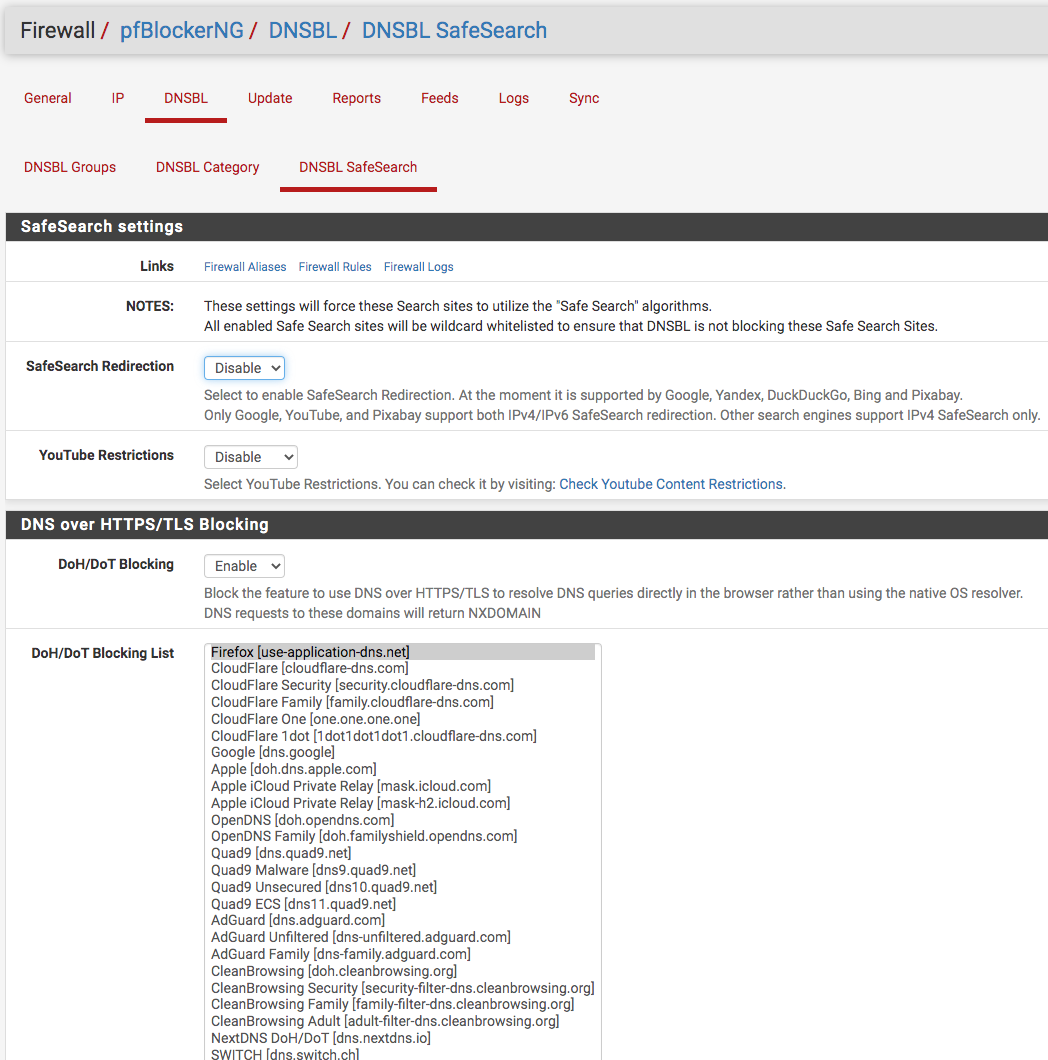
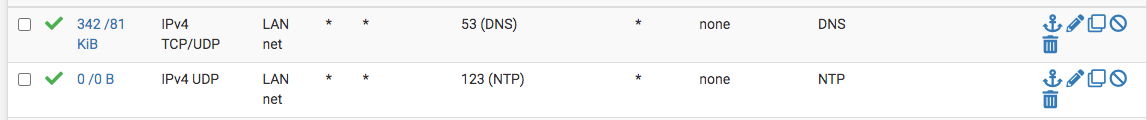
-
From the picture above, you are only blocking DoH servers in FireFox because the canary domain is selected. No other DoH server seems to be selected.
Try this example from a browser that is not FireFox:
https://dns.google.com/resolve?name=www.potaroo.net&type=A
-
@shoulders So, you're saying select all? I do mostly use Firefox and had disabled Doh in the browser itself but don't recall selecting it as the screen shot suggested. I will select all then later
-
Yes you need to select all because you are only telling the Firefox browser to not use DoH. This is not by force, but by an inbuilt mechanism in FF (canary domain), chrome and the other browsers don't use this.
All other devices on your network will still potentially be able to use DoH even with the whole list selected as it is not the largest list.
This list will stop a lot of DoH traffic but it will not stop all of it.
sorry for the delay, I am not getting email notification.
-
@shoulders Cool, thanks.