Selective trafficking via double OpenVPN server to avoid geo-location
-
WARNING ABSOLUTE AMATEUR: I have small networking system with PfSense running as my main firewall and Raspberry Pi running PIVPN (OpenVPN) at different locations. The purpose for the RPI is to create OpenVPN servers to which I connect to get different content.
Generally, everything works perfectly. My PfSense is constantly connected to my OpenVPN servers in different locations and it routes traffic in accordance with aliases from pfBlockerng, while the rules are set up under general firewall rules.
What I want to do is create an OpenVPN server on my PfSense and that will reflect the same rules as I have when I connect at home to my wifi. The OpenVPN server isn't a problem, the rules for directing traffic are. I tried copying the rules that I have on my home interfaces and put them on the OpenVPN interface but I cannot open the websites. I think I manage to reach out to them but PfSense doesn't know how to get the signal back.
I have drawn a diagram to better illustrate all this. Maybe someone has succeeded in what I am trying to do.
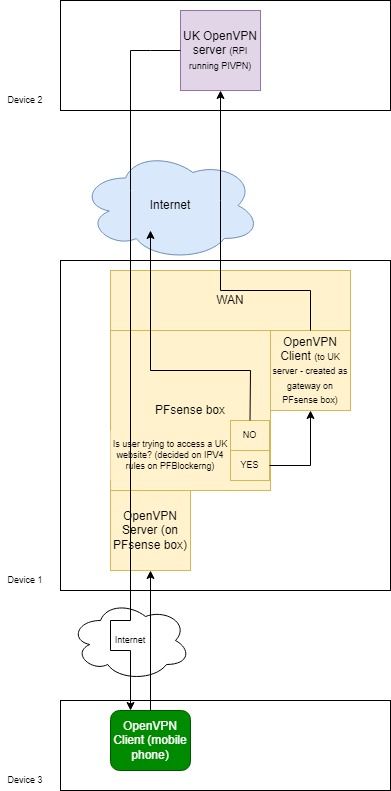
EDIT: forgot to mention the rules
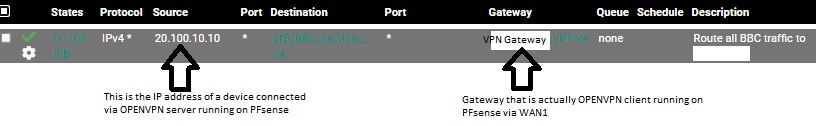
-
@nidema
Did you consider to add an outbound NAT rule to the OpenVPN client interface?And why is the rule limited to a single source IP only? Shouldn't it cover the whole access server tunnel network?
-
@viragomann Thank you. This is when it comes out that I am a self-taught amateur. It solved the issue - I did not have a NAT rule for the OpenVPN server interface.
To answer your second question: That is my mobile phone - the source is there to set it up on one device since other are connected. (I allow access to a bunch of friends via my OpenVPN server (and FreeRadius) accounts to those that host my RPI or live in totalitarian states - they get to watch Netflix and/or read uncensored news).
Thanks and I am closing this post.