Setting up new device on LAN
-
Configuring new device with pfSense 2.6 on my LAN with the device's WAN interface given an IP on the local network and gateway address of my production gateway. Private and Bogon blocks disabled on the WAN interface for now.
Simple network 192.168.4.0/24
WAN interface IP 192.168.4.244
Gateway 192.168.4.1
LAN IP 192.168.1.253 (connected to standalone host for configuration)
I can ping the WAN IP from my LAN (I have a rule in place to allow pings on all interfaces) but I cannot ping gateway IP from pfSense GUI. Gateway 192.168.4.1 shows offline in the GUI. -
I assume 192.168.4.1 is your upstream router, does it allow pings?
-
@networkcowboy
Yes, it does. I can ping from other hosts on this network. -
So you can ping 192.168.4.1 from devices on the pfSense LAN just not from the pfSense GUI?
-
@networkcowboy
I haven't tried this before. It didn't occur to me to try it from hosts on its LAN because it was an obvious NO since the gateway shows "offline".
But now that you mentioned it, I tried and not only can I ping 4.1 from hosts on the 192.168.1.0 LAN but I can even get websites.So why is the gateway showing "offline"?
-
I would check your rules related to ICMP because it should be working.
-
@networkcowboy
It's not just ICMP. pfSense can't do DNS lookups in Diag and it can't check for updates nor Retrieve support information on the [Netgate Services And Support] widget. It itself cannot see the gateway or anything past it, but it can NAT hosts on its LAN. -
Does the gateway IP appear in the ARP table?
Have you configured your WAN with a static IP?
-
@peterlecki
can you tell us what is in the arp table (diagnostics > arp table) ? -
@peterlecki questions:
- does the "production gateway" allow icmp?
- make sure your pfSense has outbound NAT enabled so source IP of your pings from 192.168.1.x gets translated to 192.168.4.244
- maybe production gateway blocks traffic to rfc1918 subnets? check its rules....
edit: sorry I see you answered some of these already. I would really check your outbound NAT rules, try setting to Hybrid and then save and then switch back to Automatic and save again. And check System -> Routing and make sure you have the correct gateway as your default system gateway, and monitor IP should probably be something beyond the 4.1 gateway like 1.1.1.1 or 8.8.4.4
-
@stephenw10 @f-meunier
MAC for the gateway's IP is "incomplete"? But then again, clients on the LAN get NATted to the WAN just fine. pfSense cannot reach the gateway for its own purposes but can do it on behalf of others.
-
@luckman212
NAT works fine for clients on the LAN, it's only pfSense itself that cannot see the gateway but yet can NAT clients to it just fine.I tried the gateway settings both monitor to the IP and past it but it did make a difference:


-
@peterlecki ok confused, thought you said your gateway was 192.168.4.1 - why are you blocking it out? from the wangw on the gateway tabs.
Is what pfsense show for it wangw not 192.168.4.1 and some public IP?
If pfsense was actually sending traffic to 192.168.4.1 there is no possible way it could work without a mac address... Just not possible at all..
You say clients behind pfsense work - lets see your state table please to some remote site... So for example... get a constant ping going to say 8.8.8.8, you say that works right from your clients..
In the state table list that... So example here is mine..

See where you see state on lan from my pc at 192.168.9.100 sending to 8.8.8.8 and then pfsense natting this to my wan IP (which is public IP address)..
-
This post is deleted! -
There is no NAT on those WAN states so something upstream is NATing it. Or not NATing it since there are no replies.
More importantly that's not ping traffic so where ever you're pinging from there is not going through the firewall at all.
Steve
-
8.8.8.8 does show states in UDP on port 53 but 8.8.8.8 is my primary configured DNS. Still no icmp states, though. So 8.8.4.4 is a better test you wanted to see, John.


-
Where are you running that ping? It's not passing the firewall.
-
@peterlecki yup clearly that client isn't using pfsense at all..
Do a simple traceroute, or even lets see the ipconfig /all of that box..
Clearly pfsense that you say is connect to your other router isn't - since if it was it would see the mac address. Since it can not see the mac address - there is no way anything could route through it, etc..
Your states of your wan IP trying to talk to 8.8.8.8:53 go unanswered.. Not even sure why it would create a state - if has no where to send it, ie no mac of your gateway 4.1
Still not sure why you would hide your wangw if like you say its 192.168.4.1..
-
@johnpoz @stephenw10
This was an ID10T error. I had wireless active on the client device I was testing from so of course it was accessing the internet via the normal gateway. I now noticed this after you pointed it out and turned it off. Now it no longer can access the internet. Apologies for wasting your time and energy and thank you for pointing this out.Anyway, now that I no longer complicate the situation even further with "fake news", let's get back to the issue at hand. John, blocked out in that screenshot was my real ISP gateway IP. The WANGW_TEMP was configured as the gateway for the WAN interface. So the public WANGW gateway was available but not used. Just to eliminate any potential problems, I now completely removed it:

And here are the icmp states:
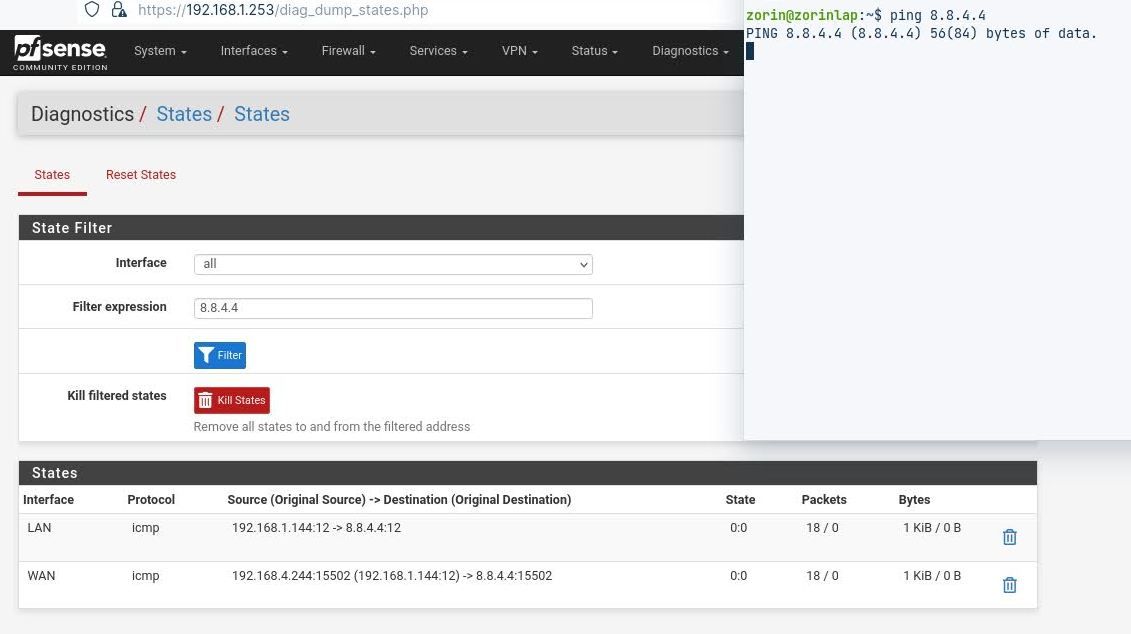
-
Ok, so the states look correct but your temporary WAN gateway is not responding so the pings go nowhere.
I assume it is not in the ARP table still?So what is 192.168.4.1? How is the WAN interface connected to it?
I would not expect the public WAN gateway to be available at the same time if there is another router in between.
Steve