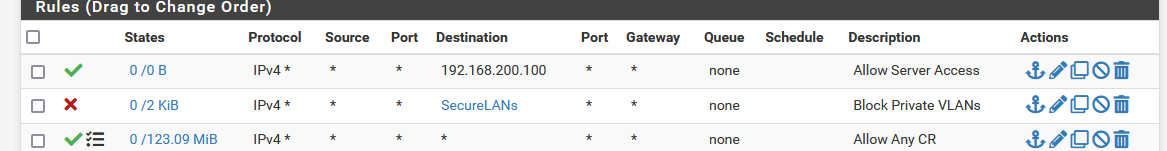
Block All VLANs
-
@zinder said in Block All VLANs:
DNS is pfSense. 192.168.20.1 for VLAN20. Seems to be working.
and how would that be working from your rules, your blocking anything 192.168.20.1 via your block rule are you not.. If your alias contains 192.168.20.0/24 as network.. Your clients would not be able to talk to 20.1 for dns..
So either your clients are not actually using pfsense as dns - maybe they are using doh in your browser.. Or they have a state still allowing access to dns.. But if your vlan alias is how you say it is - then clients on this interface would not be able to talk to 192.168.20.1 for dns, unless you have a floating rule allowing that?
edit: here is example lock down preventing a network from talking to your other vlans, pfsense gui etc. etc..
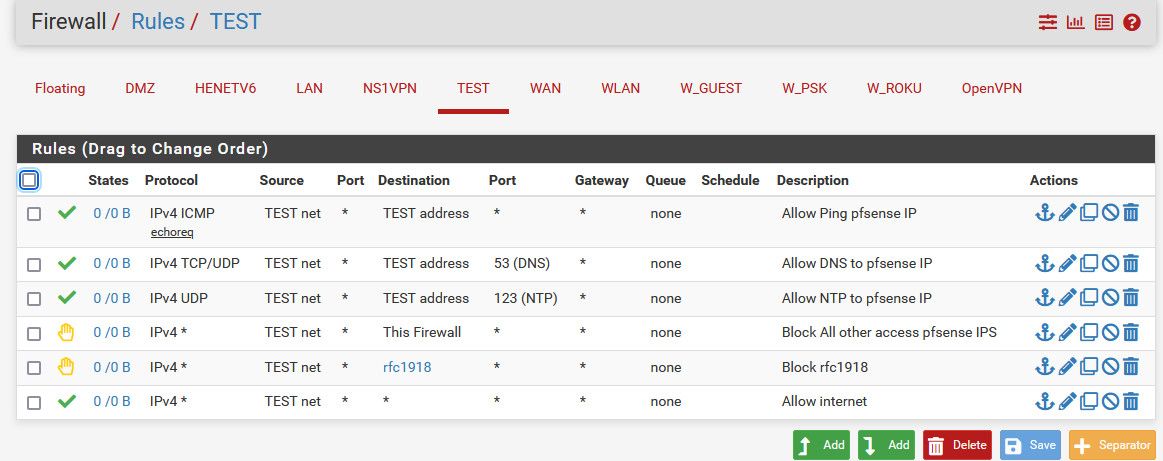
This allows to ping pfsense IP to validate connectivity, allow for dns and ntp to pfsense IP on on this interface. But block all other access to any pfsense IP, say trying to access the gui of pfsense wan that is public IP and would not be blocked by your rfc1918 block, and could change.
Blocks all other access to any of your other network/vlans - because I would assume they are in the rfc1918 space. And then allows anything else - ie the internet.
-
Why DNS works puzzles me also. From a DOS box on a PC on 192.168.20.0/24....
ipconfig
DHCP Enabled. . . . . . . . . . . : Yes
IPv4 Address. . . . . . . . . . . : 192.168.20.10(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.20.1
DHCP Server . . . . . . . . . . . : 192.168.20.1
DNS Servers . . . . . . . . . . . : 192.168.20.1ping google.com
Pinging google.com [142.250.31.102] with 32 bytes of data:
Reply from 142.250.31.102: bytes=32 time=17ms TTL=106
Reply from 142.250.31.102: bytes=32 time=11ms TTL=106
Reply from 142.250.31.102: bytes=32 time=18ms TTL=106
Reply from 142.250.31.102: bytes=32 time=16ms TTL=106Ping statistics for 142.250.31.102:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 11ms, Maximum = 18ms, Average = 15msping 192.168.20.1
Pinging 192.168.20.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.Ping statistics for 192.168.20.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss), -
@zinder said in Block All VLANs:
From a DOS box on a PC on 192.168.20.0/24....
so do a nslookup or something..
My "guess" would be your browser is actually using doh to do dns, to google dns or something - you know because you as the admin of your network are too stupid to manage it securely - so we are going to in your best interest point to our doh servers for dns..
The different browsers are moving towards doh being default - now the user/admin has to go out of their way to make sure browsers don't do doh..
That would be my guess, because your rules are not allowing for dns to work.. So in that scenario it would not be possible for your browser to access the internet.. Unless it was using somethinig else for dns - like doh.
this is the curious one
Pinging google.com [142.250.31.102] with 32 bytes of data:windows shouldn't be able to resolve that, unless it was cached.. Even if your browser was using doh.. do a nslook for something that you haven't looked up before..
Or flush your local dns cache.. ipconfig /flushdns
-
I appreciate your help, but I don't think calling me stupid was necessary. I'm new to some of this and I'm testing to ensure a secure network.
I tried to ping google.com from a cmd prompt on another PC on 192.168.20.0/24 and its not finding it. So it appears to be blocked..as you say. If I run Firefox, then the cmd prompt can ping google.com, but DoH is not checked. So it does seem to be related.
I'll look into the rules in your example.
-
@zinder said in Block All VLANs:
but I don't think calling me stupid was necessary
I wasn't calling you stupid ;) heheh Its the browser makers thinking all users are too stupid to run their own networks or dns.. heheh It was not meant at you directly at all..
They like to enable doh by default.. I am all for them offering up dns if they want - but it should be required OPT in, not any sort of default... Its like they think users that want to use doh are too stupid or lazy to click the button to opt in.. So they will do it for you..
Chrome is doing it too.. If I wanted to send you all my dns, I would - setting the default to use anything other than my OS dns is not a good direction... If I want to use doh, it should be an OPT in where the user has to actually select it, not default.. Or the admin has to configure it..
-
This DoH thing doesn't make much sense. Maybe something is in a cache somewhere. On one PC, ping google.com didn't work from a cmd prompt. I open Forefox and then ping google.com worked from the cmd prompt. I close FF and ping google.com still works. It seems, somehow, FF affects the cmd prompt. But DoH is turned off in FF Settings. I'll work on it more tomorrow.
-
@johnpoz said in Block All VLANs:
@zinder said in Block All VLANs:
but I don't think calling me stupid was necessary
I wasn't calling you stupid ;) heheh Its the browser makers thinking all users are too stupid to run their own networks or dns.. heheh It was not meant at you directly at all..
They like to enable doh by default.. I am all for them offering up dns if they want - but it should be required OPT in, not any sort of default... Its like they think users that want to use doh are too stupid or lazy to click the button to opt in.. So they will do it for you..
Chrome is doing it too.. If I wanted to send you all my dns, I would - setting the default to use anything other than my OS dns is not a good direction... If I want to use doh, it should be an OPT in where the user has to actually select it, not default.. Or the admin has to configure it..
@johnpoz you can call me stupid..... What is DoH? no really
-
@flat4 DoH = DNS over HTTPS
It is a secure DNS request that happens on 443 so it is hard to see and stop. -
@flat4 Doh is dns over https
https://en.wikipedia.org/wiki/DNS_over_HTTPS
Browsers are making it the default - and it bypasses your local dns, and sends all the dns requests from a browser to their dns servers over a 443 https tunnel - making it very difficult for a local admin to block..
While I am not a fan of it at all - I don't have a problem with browser makers offering it.. The problem is making it the default is not the way to go about it..
And then you run into issues like this user. They think their clients are using pfsense for dns, but clearly they are not because they have no rules that would even allow it.. Browser is circumventing the local dns by using doh is what seems to be happening..
See quite a few threads where users think something is broken in dns on pfsense, like host overrides not working - when their browsers isn't even asking pfsense dns because its using doh...
edit:
I have spent time I shouldn't have had to spend making sure my browsers and other devices are not circumventing what I have setup for dns on my network.. Dot (dns over tls) isn't as bad because it uses a specific port 853 which is easy enough to block. But using 443 is clearly an attempt to allow the browser to circumvent restrictions put in place on the network.. Circumvention of the local networks controls is not something I want my browser doing that is for damn sure.. If I don't want you looking up xyz, then you shouldn't go out of your way to look it up if I filter it on my dns..You have a bunch of stuff now hard coding dns, or trying to use doh.. F!! off - use the dns I as the network admin hand you, or don't use any dns.. How is circumvention of my controls have anything to do with security or privacy.. No its about sending you dns, and allowing your thing to circumvent local controls..
If user wants to circumvent their ISP dns by using something like doh - then they should have to on purpose select to do that, after fully understand what is happening vs the browser maker making that decision.. There is no legit reason why such a thing should ever be "default"..
If you couldn't tell - not a fan of doh ;) hehehe
-
thank you
-
@johnpoz I would agree, I will now have to look at my devices to see if my family has accepted this without thinking about it.
For the record at first i thought DoH was a reference to Homer
-
@flat4 said in Block All VLANs:
DoH was a reference to Homer
Yeah I agree - its something stupid like Homer would do that is for sure ;)
-
Thanks to all for explaining doh. I changed my SecureLANs alias to not include the 192.168.20.0/24 network. So now, all PCs on 20.0 seem to get DNS, etc. I added a rule to block source from 20.0 network and destination to This Firewall/443. I think I'm good, unless I missed something else.