Sanity check on hosting a website behind pfsense
-
I imagine I'm a bit paranoid, and I'm also not a security expert. I have been using pfsense for a while. I prefer to only forward ports with IP source as a condition, but I'd like to run some services where that becomes less feasible.
So I'm hoping to give a run through of my set up and get any input on something I could be missing or don't understand properly.
I have created a VLAN for a "DMZ" network. The only machine on this VLAN is an Ubuntu VM running Nginx as a reverse proxy. This VM has a firewall enabled, and is only allowing traffic via port 22 and port 443.
In pfsense NAT Port Forward settings, I have a port forward to accept TCP traffic over port 443 on the WAN interface, and forward it to the VM running Nginx.
The DMZ VLAN has rules created to allow TCP traffic to a few different resources on different VLANs over port 80.
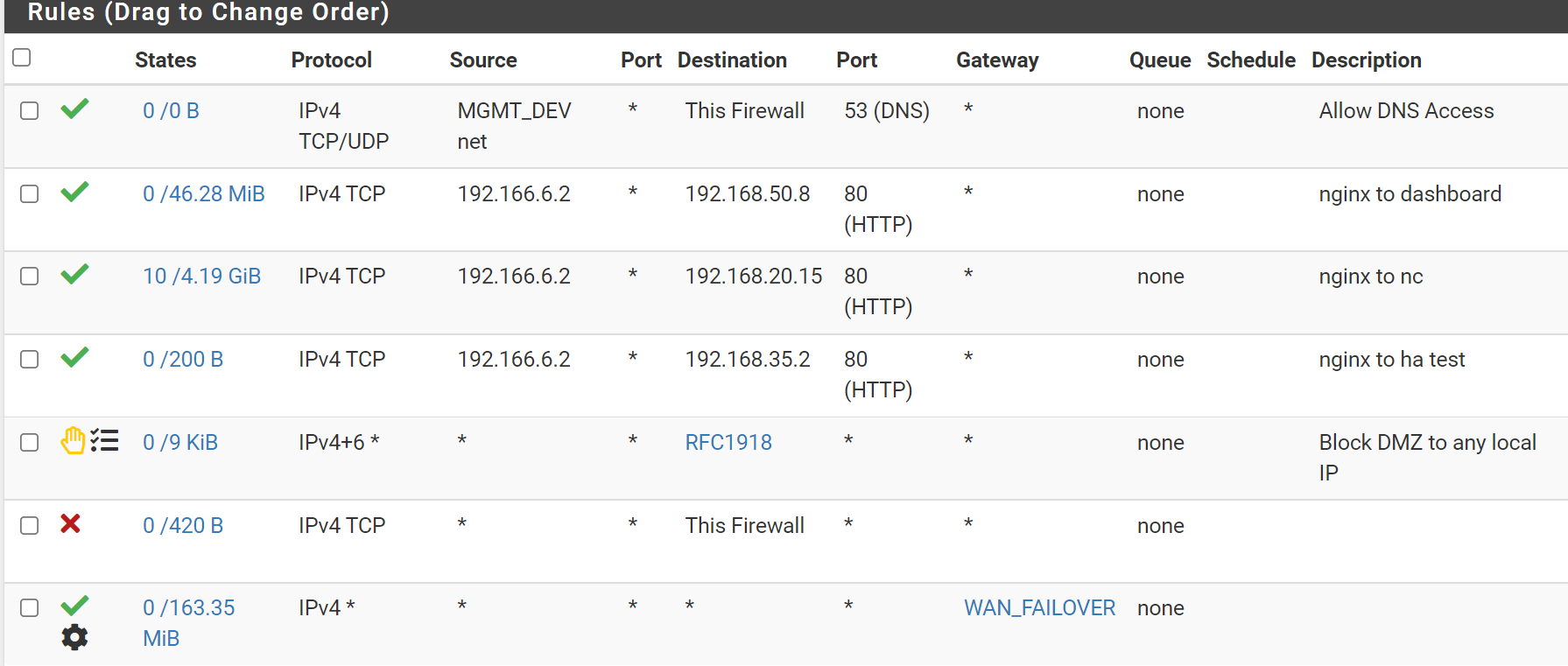
There is also a floating rule to block access to pfsense web GUI, although I think that may be redundant.
So I think this is fairly secure but I'm also worried that I'm missing something. As I understand it, an attacker is only able to access Nginx over port 443. Port 22 is not forwarded so SSH access is local only. And the Nginx VM is only able to communicate with the target resources via their web servers listening on port 80.
So if the Nginx VM was compromised, an attacker would then have to exploit a vulnerability that must be present via the target resources port 80.
Is this considered secure? Would you guys be comfortable exposing servers to the public like this? Some of my uncertainty comes from not knowing all the vectors that attackers exploit.. as I am not a hacker.
I'm also running Suricata for good measure, though I suppose that only stops things caught by its ruleset.
Currently this server is still only exposed to whitelisted IPs, but I'd love to flip the switch on that. Any input is greatly appreciated. Thanks