Not able to connect to some website
-
Greetings,
I encounter weird problem, I'm not able to connect to some website, in this case, is "archlinux.org", let me describe what happened.Here are the general network config of my setup.
Modem -> pfSense/Router -> MyPC, WAN configure as PPPoE, LAN configure as DHCP for IPv4, and track6 for IPv6. There's no DHCPv6 on LAN, RA set to assisted.
In my case, I am able to use IPv6 network to connect to major website, e.g. google.com, youtube.com, ipv6-test.com. I got perfect score from ipv6-test.com. But, I'm not able to connect to archlinux.com, connection always timed out. However, when I force my web browser to use IPv4, I'm able to connect to archlinux.org without any issue. Interestingly, I'm able to ping and tracepath to archlinux.org via IPv6 and IPv4 from MyPC. I even set WAN wide open, still, same result.
When I configure my network as "Modem/Router -> MyPC", everything works without any issue.Is there any way to fix this issue, maybe something related to resolving or DNS.
Below are some pfSense config.
- interfaces config
<interfaces> <wan> <enable></enable> <if>pppoe0</if> <blockpriv></blockpriv> <blockbogons></blockbogons> <descr><![CDATA[WAN]]></descr> <ipaddr>pppoe</ipaddr> <ipaddrv6>dhcp6</ipaddrv6> <dhcp6-duid></dhcp6-duid> <dhcp6-ia-pd-len>0</dhcp6-ia-pd-len> <dhcp6usev4iface></dhcp6usev4iface> <adv_dhcp6_prefix_selected_interface>wan</adv_dhcp6_prefix_selected_interface> <spoofmac></spoofmac> </wan> <lan> <enable></enable> <if>igb1</if> <descr><![CDATA[LAN]]></descr> <ipaddr>192.168.2.1</ipaddr> <subnet>24</subnet> <ipaddrv6>track6</ipaddrv6> <track6-interface>wan</track6-interface> <track6-prefix-id>0</track6-prefix-id> <spoofmac></spoofmac> </lan> <opt1> <descr><![CDATA[modem]]></descr> <if>igb0</if> <enable></enable> <ipaddr>dhcp</ipaddr> <dhcphostname></dhcphostname> <alias-address></alias-address> <alias-subnet>32</alias-subnet> <dhcprejectfrom></dhcprejectfrom> <adv_dhcp_pt_timeout></adv_dhcp_pt_timeout> <adv_dhcp_pt_retry></adv_dhcp_pt_retry> <adv_dhcp_pt_select_timeout></adv_dhcp_pt_select_timeout> <adv_dhcp_pt_reboot></adv_dhcp_pt_reboot> <adv_dhcp_pt_backoff_cutoff></adv_dhcp_pt_backoff_cutoff> <adv_dhcp_pt_initial_interval></adv_dhcp_pt_initial_interval> <adv_dhcp_pt_values>SavedCfg</adv_dhcp_pt_values> <adv_dhcp_send_options></adv_dhcp_send_options> <adv_dhcp_request_options></adv_dhcp_request_options> <adv_dhcp_required_options></adv_dhcp_required_options> <adv_dhcp_option_modifiers></adv_dhcp_option_modifiers> <adv_dhcp_config_advanced></adv_dhcp_config_advanced> <adv_dhcp_config_file_override></adv_dhcp_config_file_override> <adv_dhcp_config_file_override_path></adv_dhcp_config_file_override_path> <blockbogons></blockbogons> <spoofmac></spoofmac> </opt1> <opt2> <descr><![CDATA[OPT2]]></descr> <if>igb2</if> <enable></enable> <spoofmac></spoofmac> <alias-address></alias-address> <alias-subnet>24</alias-subnet> <ipaddr>192.168.3.1</ipaddr> <subnet>24</subnet> </opt2> <opt3> <descr><![CDATA[OPT3]]></descr> <if>igb3</if> <enable></enable> <spoofmac></spoofmac> <alias-address></alias-address> <alias-subnet>24</alias-subnet> <ipaddr>192.168.4.1</ipaddr> <subnet>24</subnet> </opt3> </interfaces>- Firewall config
<filter> <rule> <id></id> <tracker>1651862950</tracker> <type>pass</type> <interface>wan</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <protocol>icmp</protocol> <icmptype>echoreq</icmptype> <source> <any></any> </source> <destination> <any></any> </destination> <descr></descr> <updated> <time>1651862951</time> <username><![CDATA[admin@192.168.2.102 (Local Database)]]></username> </updated> <created> <time>1651862951</time> <username><![CDATA[admin@192.168.2.102 (Local Database)]]></username> </created> </rule> <rule> <type>pass</type> <ipprotocol>inet</ipprotocol> <descr><![CDATA[Default allow LAN to any rule]]></descr> <interface>lan</interface> <tracker>0100000101</tracker> <source> <network>lan</network> </source> <destination> <any></any> </destination> </rule> <rule> <type>pass</type> <ipprotocol>inet6</ipprotocol> <descr><![CDATA[Default allow LAN IPv6 to any rule]]></descr> <interface>lan</interface> <tracker>0100000102</tracker> <source> <network>lan</network> </source> <destination> <any></any> </destination> </rule> <rule> <id></id> <tracker>1651861838</tracker> <type>pass</type> <interface>opt1</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <protocol>tcp/udp</protocol> <source> <network>opt1</network> </source> <destination> <network>(self)</network> </destination> <descr></descr> <created> <time>1651861838</time> <username><![CDATA[admin@192.168.2.102 (Local Database)]]></username> </created> <updated> <time>1652297698</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </updated> </rule> <rule> <id></id> <tracker>1652295088</tracker> <type>pass</type> <interface>opt1</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <protocol>icmp</protocol> <icmptype>echoreq</icmptype> <source> <network>opt1</network> </source> <destination> <network>(self)</network> </destination> <descr></descr> <updated> <time>1652295088</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </updated> <created> <time>1652295088</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </created> </rule> <rule> <id></id> <tracker>1652297670</tracker> <type>pass</type> <interface>opt1</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <protocol>tcp/udp</protocol> <source> <network>opt1</network> </source> <destination> <network>lan</network> </destination> <descr></descr> <updated> <time>1652297670</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </updated> <created> <time>1652297670</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </created> </rule> <rule> <id></id> <tracker>1652199951</tracker> <type>pass</type> <interface>opt1</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <protocol>icmp</protocol> <icmptype>echoreq</icmptype> <source> <network>opt1</network> </source> <destination> <network>lan</network> </destination> <descr></descr> <created> <time>1652199951</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </created> <updated> <time>1652297638</time> <username><![CDATA[admin@192.168.2.85 (Local Database)]]></username> </updated> </rule> <rule> <id></id> <tracker>1652538077</tracker> <type>pass</type> <interface>opt2</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <source> <network>opt2</network> </source> <destination> <any></any> </destination> <descr></descr> <created> <time>1652538077</time> <username><![CDATA[admin@192.168.1.10 (Local Database)]]></username> </created> <updated> <time>1652549759</time> <username><![CDATA[admin@192.168.1.10 (Local Database)]]></username> </updated> </rule> <rule> <id></id> <tracker>1652539826</tracker> <type>pass</type> <interface>opt3</interface> <ipprotocol>inet46</ipprotocol> <tag></tag> <tagged></tagged> <max></max> <max-src-nodes></max-src-nodes> <max-src-conn></max-src-conn> <max-src-states></max-src-states> <statetimeout></statetimeout> <statetype><![CDATA[keep state]]></statetype> <os></os> <source> <network>opt3</network> </source> <destination> <any></any> </destination> <descr></descr> <updated> <time>1652539826</time> <username><![CDATA[admin@192.168.1.10 (Local Database)]]></username> </updated> <created> <time>1652539826</time> <username><![CDATA[admin@192.168.1.10 (Local Database)]]></username> </created> </rule> <separator> <opt1></opt1> <wan></wan> <opt4></opt4> <opt2></opt2> <opt3></opt3> </separator> </filter> -
@jeff_wuyo said in Not able to connect to some website:
archlinux.org
I just tried that site and it worked fine.
-
@jeff_wuyo Could be a DNS/unbound problem. What are your outputs from the commands below when running directly on your pfSense console?
dig +short -t aaaa google.com dig +short -t aaaa archlinux.org -
@luckman212
Thanks for your reply.
Here is the output.[2.6.0-RELEASE][root@pfSense.jeff.arpa]/root: dig +short -t aaaa google.com 2404:6800:4012:4::200e [2.6.0-RELEASE][root@pfSense.jeff.arpa]/root: dig +short -t aaaa archlinux.com [2.6.0-RELEASE][root@pfSense.jeff.arpa]/root:So there does something wrong, but how to fix it tho? Any hint would be great.
-
@jeff_wuyo Hmm it seems you're mixing up the hostnames -- you started by saying archlinux.org but then switched to archlinux.com
The .org seems to have AAAA records in DNS, while the .com does not. So it seems normal that you wouldn't be able to connect to archlinux.com via IPv6....
https://mxtoolbox.com/SuperTool.aspx?action=aaaa%3aarchlinux.com&run=toolpage
-
@luckman212
Oops, I mean "archlinux.org", not "archlinux.com". I used the wrong hostname on previous comment. Here are new output.[2.6.0-RELEASE][root@pfSense.jeff.arpa]/root: dig +short -t aaaa google.com 2404:6800:4012:3::200e [2.6.0-RELEASE][root@pfSense.jeff.arpa]/root: dig +short -t aaaa archlinux.org 2a01:4f9:c010:6b1f::1For now, I have no clue.
-
@jeff_wuyo ok, so DNS is working. And you have a 10/10 on test-ipv6.com? Might be time to do some digging with
tcpdump -ni igb0 ip6etc on pfSense or Wireshark and see where those packets are getting diverted. -
@luckman212
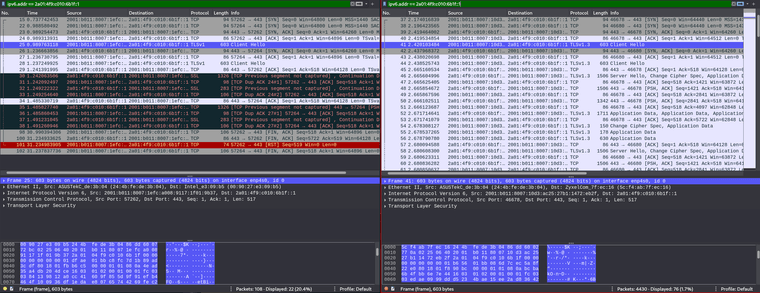
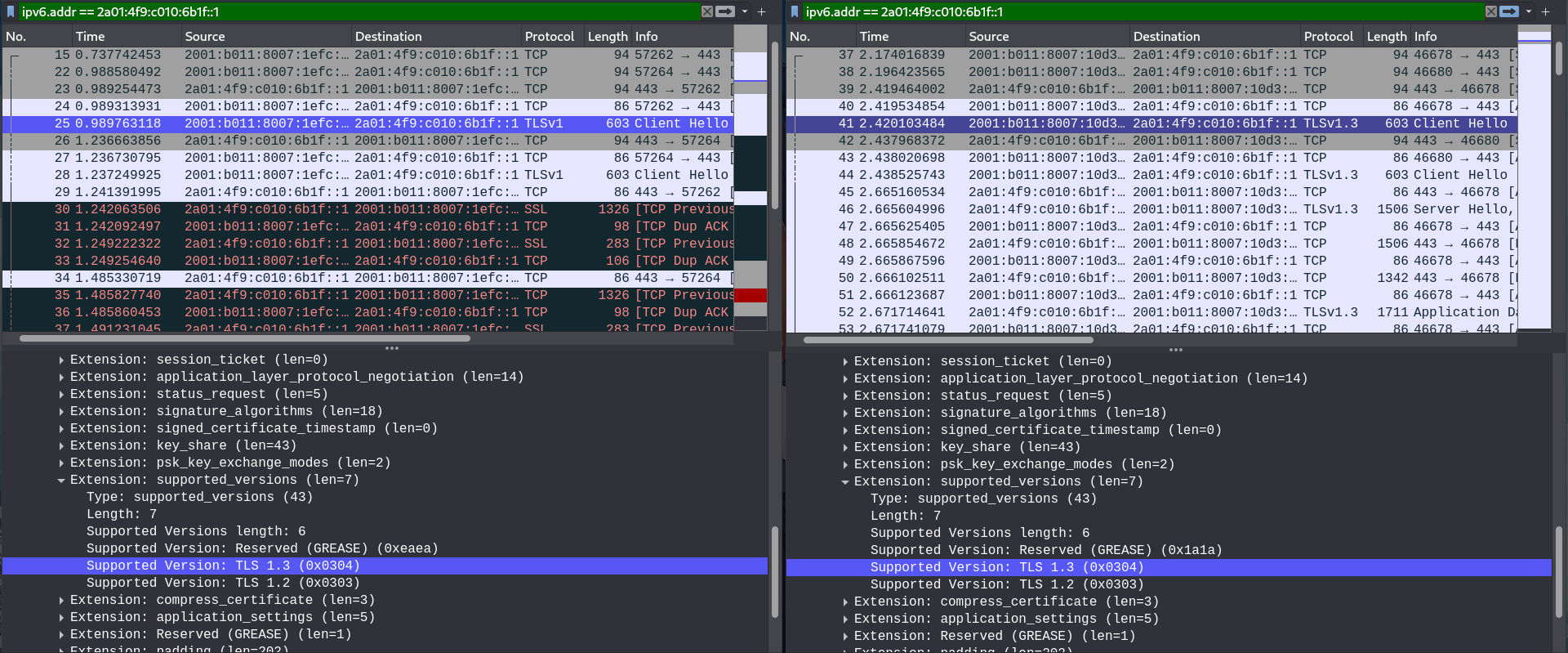
I captured locally on MyPC, I'm not sure what to look for, here is a simple screenshot.
I filter out using [2a01:4f9:c010:6b1f::1], which is the IPv6 of archlinux.org I get from pinging.
On the left is connecting via pfSense as router, when MyPC try to connect to archlinux.org, it uses TLSv1, and there's no respond from server; on the right is connecting via my ISP router, when MyPC try to connect to archlinux.org, it uses TLSv1.3, and the server respond with same protocol.
Maybe wrong protocol is the reason, but why it behaves like this? During testing under pfSense, I still see TLSv1.3 being used. -
That is very odd. I just tested it on my end (I don't have IPv6 where I am currently, but via IPv4 it definitely connects via TLSv1.3 to archlinux.org). I am not aware of what pfSense being "in the middle" of this connection could possibly have to do with your browser's choice of TLS level, or the way the server "sees" your connection capabilities, unless there was some MITM going on. But I assume you are not running any kind of proxy (snort, haproxy etc) that could be tampering with these packets, right? Maybe someone else has some idea...
-
if you look at the ssl test for archlinux.org - they do not support 1.0 or 1.1 so no if your client isn't able to do atleast 1.2 then your not going to connect
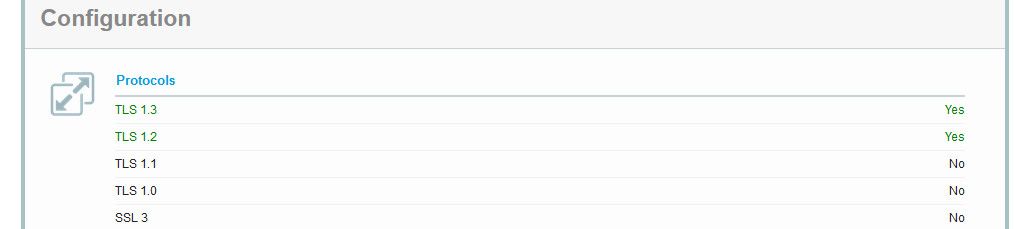
Unless you were running some sort of mitm setup pfsense would do nothing with your tls connection, what your client is capable of would come from the client.. You can look in the handshake to see what your client offers, etc.. In your sniff.
Here is an example handshake.. and what my client is saying it supports
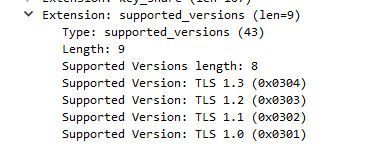
You can read up on how the handshake works here
https://www.cloudflare.com/learning/ssl/what-happens-in-a-tls-handshake/
But again pfsense out of the box would have no way to mess with that handshake..
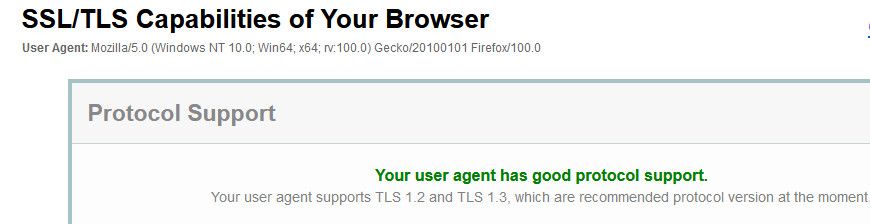
I would go here - what does it show for what your browser supports?
https://clienttest.ssllabs.com:8443/ssltest/viewMyClient.html
-
@johnpoz
Here is a screenshot about my browser. Seams all good.
Below is a screenshot about what TSL version MyPC support. (From the same sniffs above.) Both with and without pfSense, MyPC reports it support TSLv1.2 and 1.3 in both.
This results are consistent on my every device, windows, android, etc.
As for MITM, I can't not recall I did anyting like it, or I just don't realize what I did. My pfSense is quite vanilla, no other addon package.
Some weird thing I did is that I bridged LAN, OPT2, OPT3 together (as bridge0) but not assign bridge0, instead I assign each interface. I setup 3 DHCP server on LAN, OPT2, OPT3, tracking WAN on LAN, set RA assisted, no IPv6 configuration on OPT2 and OPT3. (MyPC is under LAN.) I can't get more interface to track WAN since my ISP gives me /64 prefix. Under this configuration, I can get IPv6 and IPv6 connectivity form every port which is kinda weird.
If I assign bridge0, and configure bridge0 IPv6 to track WAN interface, IPv6 just doesn't work, no ip, no connection. I suspect is due to some limitation or lack of proper switch chip. -
@jeff_wuyo said in Not able to connect to some website:
I setup 3 DHCP server on LAN
huh? But you bridged them?
my ISP gives me /64 prefix
Yeah you got some weirdness setup there for sure.
If your wanting to use IPv6 behind pfsense, but your ISP does not do delegation of a prefix to use behind a router. Prob better to just get a IPv6 tunnel from hurricane electric. Here you can get a /48 to use how you wish. On your different segments behind pfsense.
I am not exactly clear what your doing with your bridging - but can tell you for sure if what you want is switch, then get a switch vs doing anything with a bridge.
-
@jeff_wuyo WAN interface MTU + MSS entered correctly?
e.g.
-
@nonick said in Not able to connect to some website:
@jeff_wuyo WAN interface MTU + MSS entered correctly?
I think you shouldn't reduce the value of MSS, it is done by pfSense, see the explanation under it.
-
@bob-dig said in Not able to connect to some website:
I think you shouldn't reduce the value of MSS, it is done by pfSense, see the explanation under it.
Unfortunately not, it's a bug in pfSense.
-
@nonick said in Not able to connect to some website:
Unfortunately not, it's a bug in pfSense.
And where is the redmine to that? I sure do not need to edit my mtu or mss values? Are you on some sort of say PPPoE connection or something where standard mtu does not work?
Unless your on some isp connection that requires something lower, there should be no need to edit those.
-
@nonick said in Not able to connect to some website:
Unfortunately not, it's a bug in pfSense.
Maybe it is fixed? That's why I think it is.
-
@johnpoz said in Not able to connect to some website:
but can tell you for sure if what you want is switch
Yes, what I want is indeed switch. I also want to have different subnet, or rather different network to manage other device. Perhaps I should get a managed switch.
huh? But you bridged them?
Yeah, it's the way I figure out how to make all port have IPv6 connectivity. The way I do it is against my knowledge about how router and switch work, it just looks wrong. The machine which pfSense runs on has 4 ports, thus I want to make it works as router/switch. But if I bridged them and assign bridge0, only IPv4 worked, no IPv6 connectivity. Assigning bridge to me is more correct way to do it, but I'll lose IPv6.
@nonick said in Not able to connect to some website:
WAN interface MTU + MSS entered correctly?
No. I leave it blank, which would be default. I'm not fully understand MTU and MSS, thus I ignore it for now.
-
@jeff_wuyo said in Not able to connect to some website:
Perhaps I should get a managed switch.
Doesn't have to be a full managed switch, you can get a 8 port gig smart switch (does vlans) and some other limited features of a fully managed switch. For very reasonable price, there are many on the market in the $40 price range.
But yes if your goal is to segment your network - a vlan capable switch is going to be be helpful ;) Next would be a access point that can also do vlans. If you want your wireless clients to be on different networks as well.
While a bridge does have use cases, trying to turn interfaces into switch ports is not really a good use for a bridge. You can fry up a hamburger patty and "call" it steak - but its not a very "good" steak ;)
-
@johnpoz said in Not able to connect to some website:
trying to turn interfaces into switch ports is not really a good use for a bridge
That's true. I'm asking pfSense for too much lol.
The topic is altered.
Is the bridge-thingy I did causing my TLS connection to change? Hard to tell I think. I might reset pfSense and test again eventually. For now, I think I can still tinkering around.