iOS OpenVPN: Authentication Failed - Data channel cipher negotiation failed (no shared cipher)
-
iOS OpenVPN v3.2.3 (3760)
pfSense 22.01 (SG-4860)Greetings :)
I am looking for some assistance/guidance on solving a likely misconfiguration issue on my part with my OpenVPN setup.
I have been successfully running a remote OpenVPN connection to my pfSense box (SG-4860) for a couple of years. I wanted to upgrade the setup to strengthen my former choice of ciphers and created a new setup. Somehow though, my authentication seems to fail due to a "Data channel cipher negotiation" issue.
iOS OpenVPN client
When connecting from my iOS device using the official OpenVPN client, I am getting the following error:
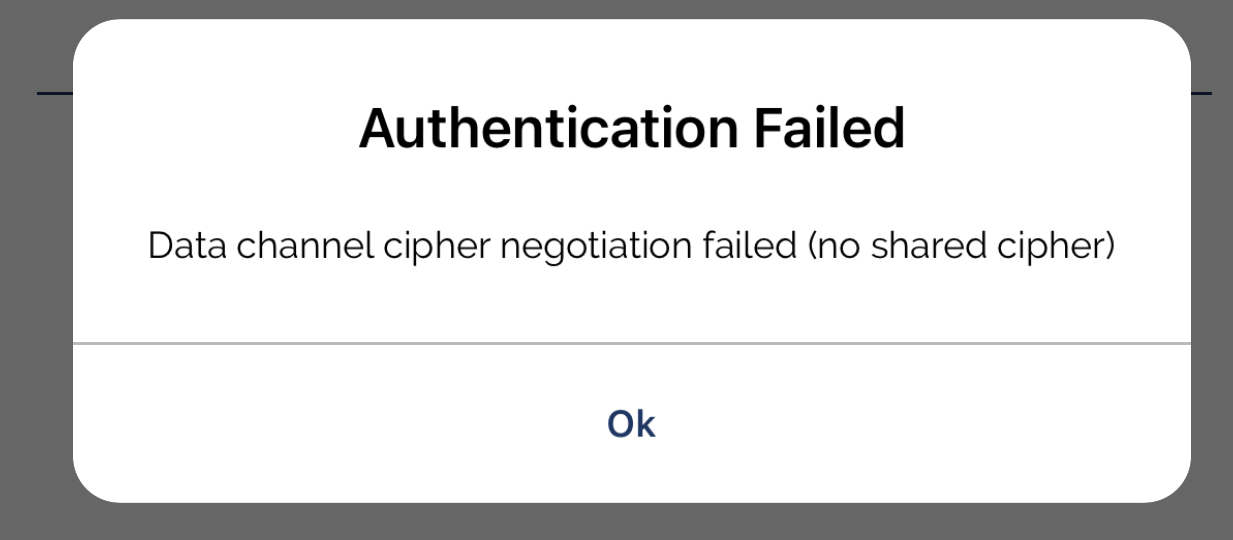
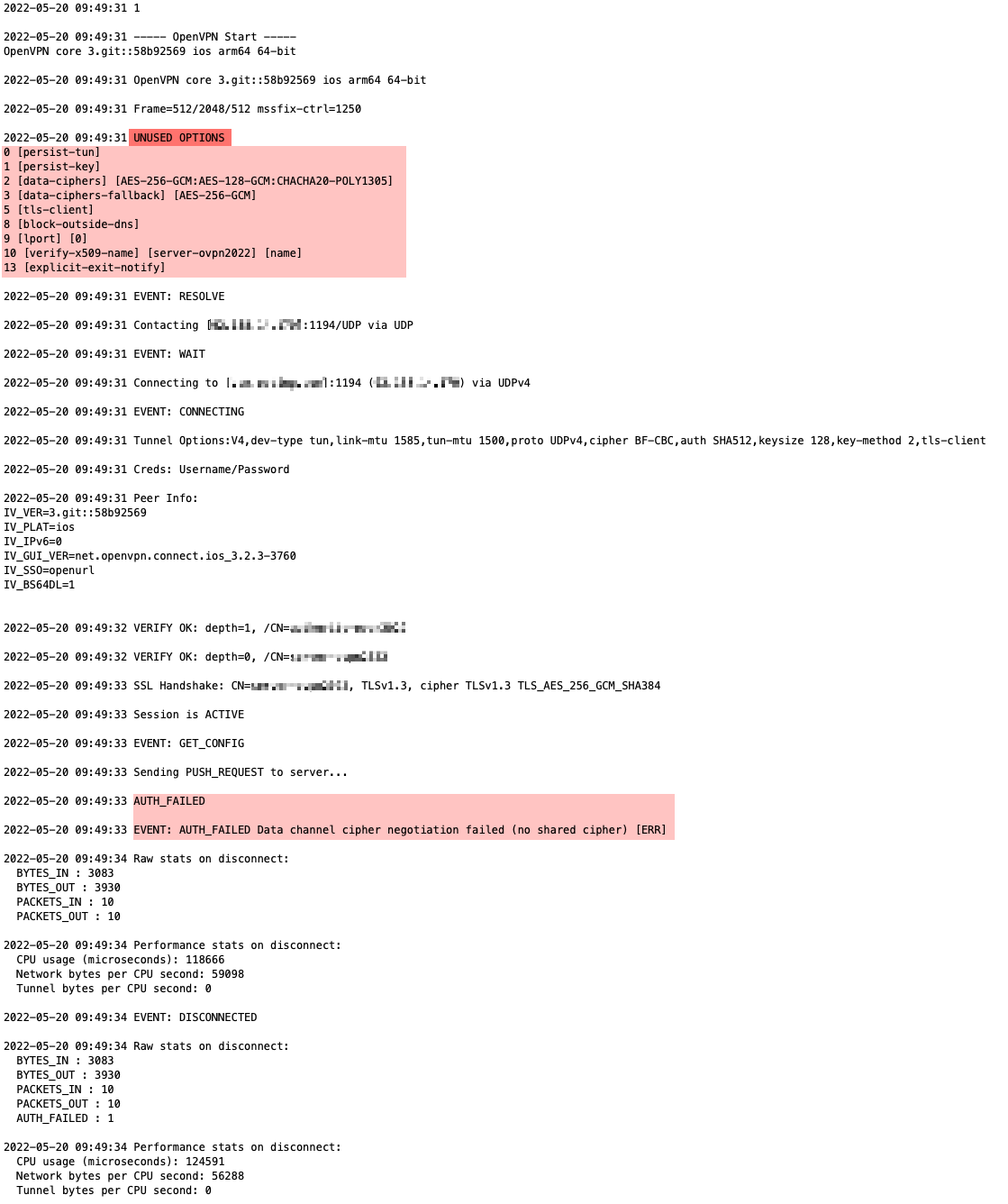
My iOS OpenVPN log shows the following:
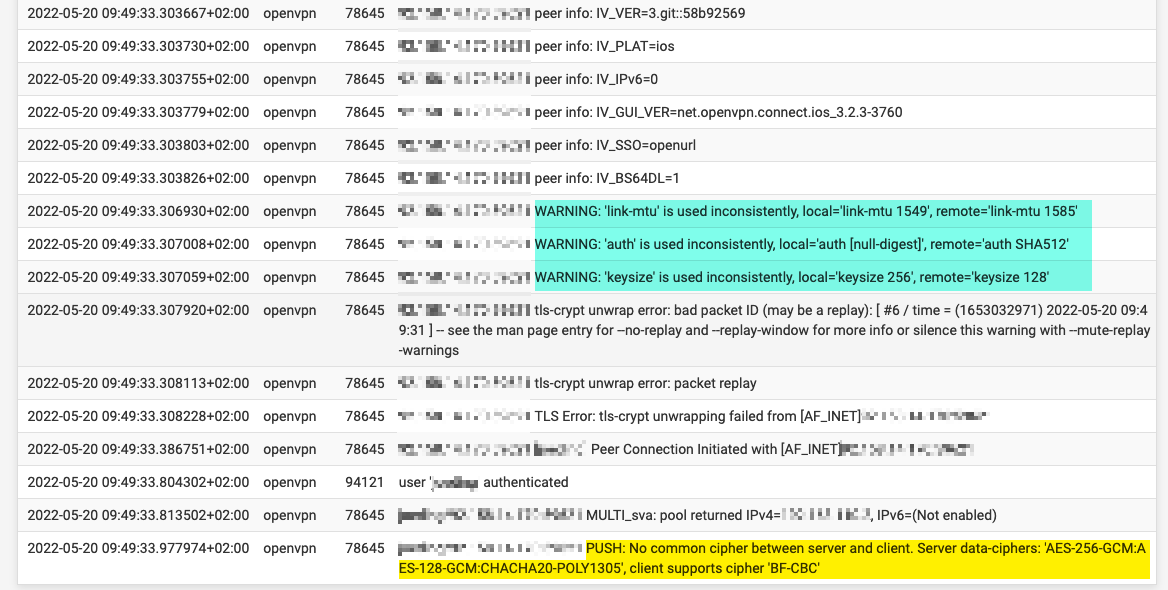
My pfSense OpenVPN log shows the following (not sure the blue part is related but maybe that's another issue I need to address?):
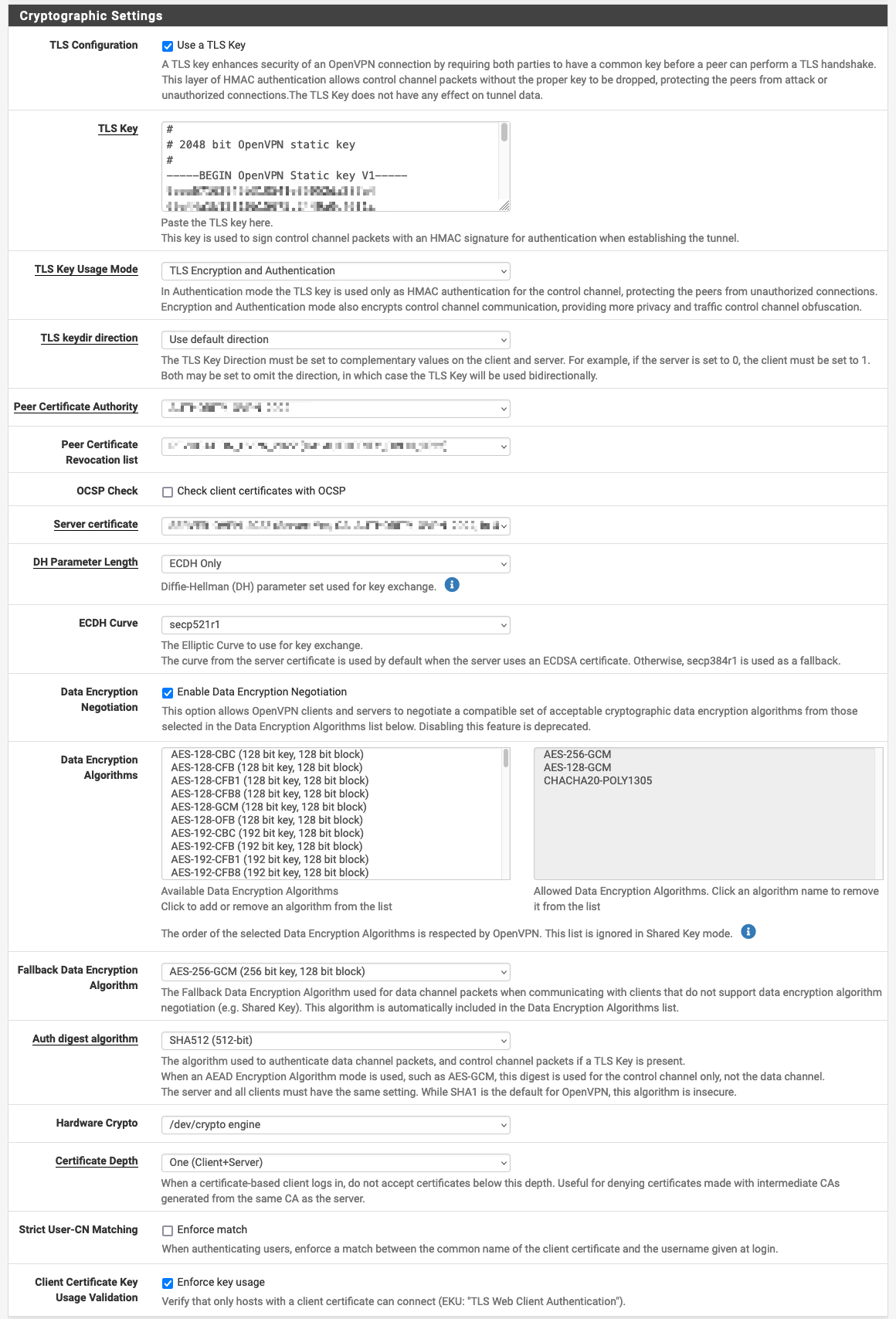
My pfSense Encryption settings are configured as follows (I used AES-256-GCM as fallback as well to prevent downgrading to a weaker encryption as I am the only user of the VPN):
Finally the OpenVPN config file for my iOS client is as follows (certificates part removed):
persist-tun persist-key data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 data-ciphers-fallback AES-256-GCM auth SHA512 tls-client client remote my.site.com 1194 udp4 setenv opt block-outside-dns lport 0 verify-x509-name "server" name auth-user-pass remote-cert-tls server explicit-exit-notifyWould anyone have any leads I could investigate? I am not really sure where to go from here:
- is this an issue with the iOS OpenVPN app not supporting stronger ciphers?
- did I make a config mistake anywhere?
I am quite reliant on my VPN setup but my old config is deprecated and I don't want to let it run as such with the older ciphers.
Any help or pointers would be greatly appreciated :)
-
Well after 3 days of numerous trials & errors, I finally managed to solve the issue by checking the iOS client settings and unticking the "AES-CBC Cipher Algorithm" option which apparently can break the VPN connection.
So there you go, I am leaving my solution here in case anyone else stumbles on a similar problem one day.
-
@mcding Hello, thank you for providing an answer. I just ran into that problem I do not seem to find the setting you indicate in your answer. Which ios client are you using? is it the openvopn client? I am using version 3.3.2 (5086) Under settings I see VPN protocol, cnnection timeot, batery saver, seamless tunnel, connect vi, captive portal detection, confirmation dialogs, theme, crash reporting and under advanced settings: minimun TLS version (profile default) ipv6 and allow compression (insecure) , DNS fallback, and layer 2 reachability. Any idea where I can find the setting you indicate?
-
@alfaro hey, i checked my iOS client settings and indeed, I couldn’t see the option anymore.
So I checked the iOS OpenVPN version history here:
iOS OpenVPN release notes and saw that they removed that option in the latest 3.3.0 release from July 19.
Second line: Removed the “force AES-CBC cipher” legacy compatibility option.I am still connecting without any issues though.