Help setting up the internal switch!
-
So I'd better start by telling the truth... I am a noob when it comes to networking and formost configuring firewalls.
It was no coincidence that I choose Unifi for my home network years back.
But for some reason I really fell in love with pfSense, I really liked the gui and how it worked.
So much so that I decided to support the open source project, and bougth a Netgate SG2100.
At first I set it up as simple as possible and very much like my setup before.So I got an idea to rebuild my network, easy you say, if you know how pfSense function with hardware.
I do not. And I have a family, that is in dire need of internet every waking second of the day.
Thus redoing my network has to be done without any interruptions. If I were to do it while I am awake. :)If you'd like I can show the current setup, but it is crazy simple.
I have not activated the switch. I have three VLANs, client, server and guest. The simplest firewall rules possible for this to work.So what do I want now?
I want to use the built in switch.
First port should have internet and two VLANs, clients and guest network, it should be able to reach second port, where I will have the server LAN/VLAN.
What Id would like to add is an port as DMZ.I can share my current config if you'd like.
What I am asking for a ready config for me to copy paste pretty much.
I know it is a a lot and I should RTFM.
But Firewalls is not my area of expertise and it will probably never be.
With 4 kids and a 100% day job, the time I have to read and learn is to say the least very limited.
I have tried to watch and read different things but my brain refuses to learn this.
I would be prepared to to pay for an hour (I guess it takes less...) to help me with this. -
So currently you have an external switch with the 3 VLANs on it?
And you have the VLANs configured in pfSense but just not using the switch?
Or the VLANs are what you want to go to and you just have a single subnet right now?
Steve
-
@stephenw10 The first. All vlans is configured in pfSense. And not using the switch.
-
@swemattias Have you looked at the documentation on the switch?
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/switch-overview.html
-
@rcoleman-netgate I have, more than once. It is good. But for some reason my brain isn’t capable of grasping how to do it. I have tried to many times if you ask my family.
-
Ok so you are just passing through all three to an external switch currently?
You can certainly do whatever you need to here.
Access between VLANs or from VLANs to the internet is controlled entirely by the firewall rules. The switch doesn't know or care about anything at layer 3, routing traffic. So nothing should change there if you already have the VLANs configured.
You just just need to decide which VLANs you want to have available at which ports and whether that should be tagged (to trunk to an external managed switch) or unatgged so you can connect hosts or unmanaged switches directly.
Are the three VLANs you have in addition to the main LAN? Just for clarity what VLAN IDs are you using?
Steve
-
@swemattias Perhaps these images will help. This is the 7100 but the principles are the same (But you have 1 LAGG so they're port "0", not 9/10 like the 7100's is).
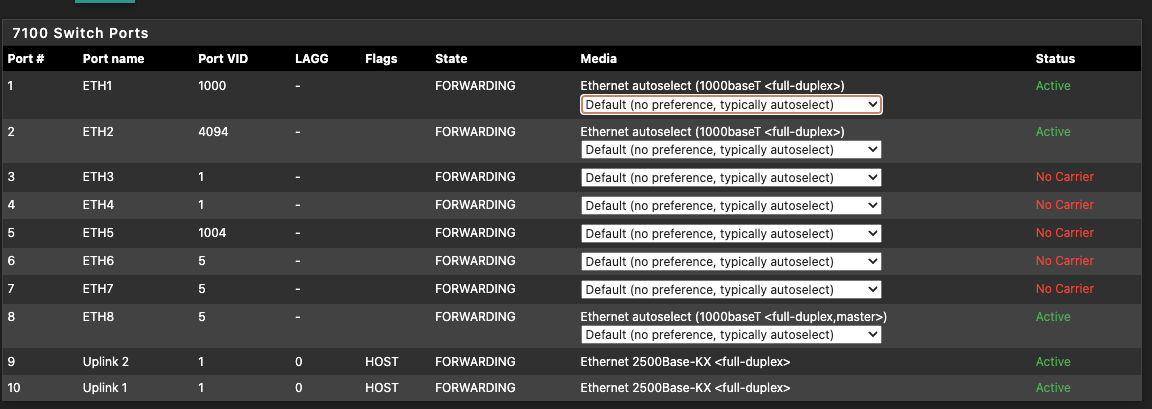
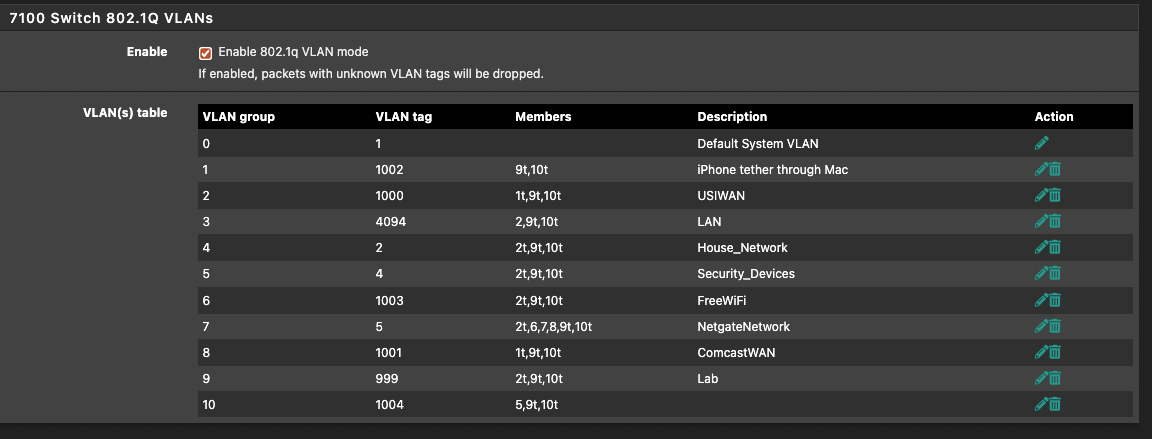
-
@stephenw10 Yes I am.
Access: That sounds good!
Where I want my VLANs I already know and they are "sepereted" physically. Port 0 and 1.
VLAN 10 (Server), 20 (client), 200 (Guest)
Port 0: 20 and 200.
Port 1: 10 -
@rcoleman-netgate Thank you!
Here is where I have the hardest the 802.10 VLANs.
Tags and members. I have read about it 100 times still cant figure out how to set it up. -
Are you looking to remove the external switch from the setup?
If not which port is that connected to now and will it remain there and with all the VLAN passed to it?
Steve
-
@stephenw10 nothing is changing behind the firewall, LAN 1 has a switch connected to it, as do LAN 2.
That will not change. -
@rcoleman-netgate
Here is my current setup, not hard to guess...
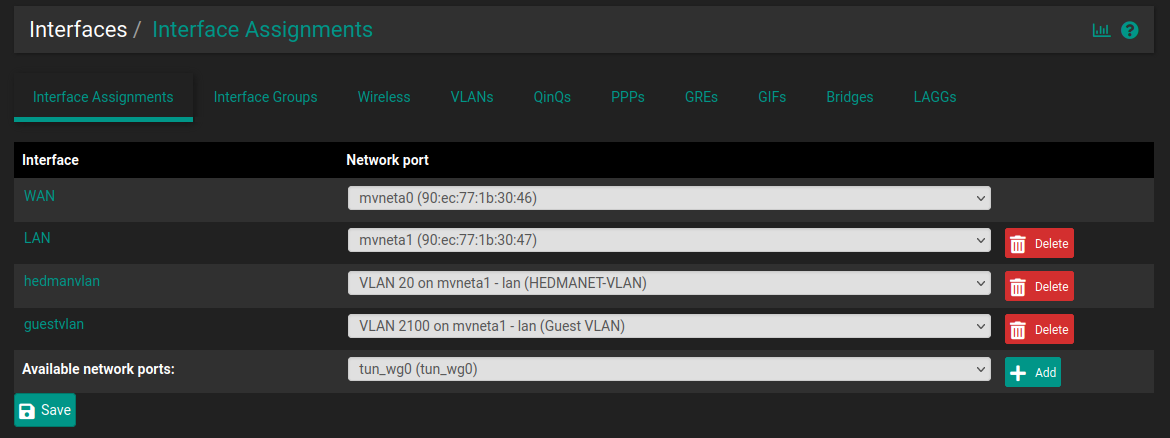
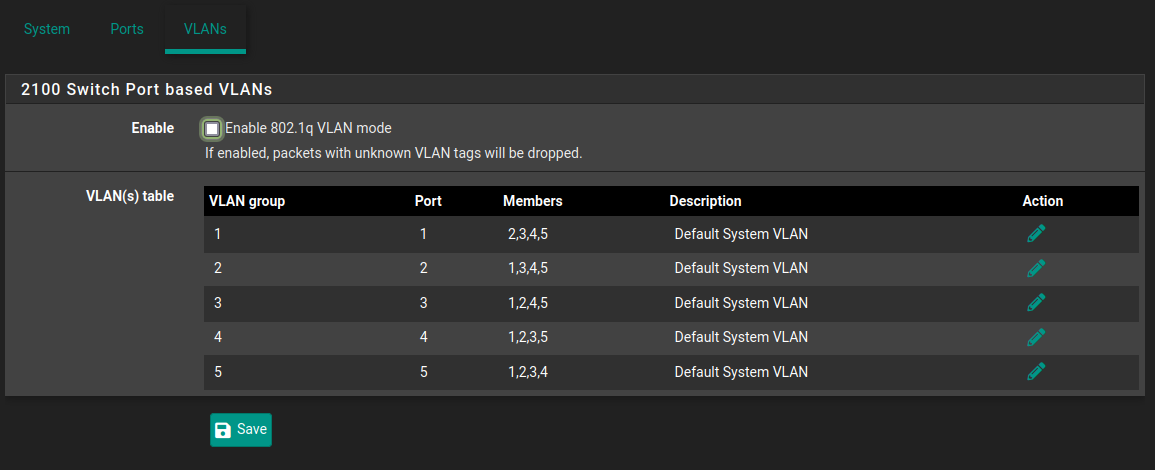
-
Ok, so there are some conflicting details here. You currently have LAN as untagged and then two VLANs on that; 20 and 2100. But above you are asking about VLANs 10, 20 and 200?
Also you refer to port 0 and 1 above but the 2100 has 4 LAN ports labelled LAN1-4. Those are the switch ports 1-4, port 5 is the internal port that links to mvneta1.
So you have two switches connected to LAN1 and LAN2 currently. Do you need all the VLANs to be available at both switches?
I was assuming you have configured those switches for the existing VLANs but perhaps you are just configuring VLANs on the clients directly?
Steve
-
@stephenw10 I know I have mixed up the ports number earlier.
And my VLAN numbers... as well. ashamedTo be crystal clear:
I want a base LAN 10.1.1.0/24 (If needed... a rest from my Unifi router setup)
Server VLAN 11 10.11.1.0/24
Client VLAN 22 10.22.1.0/24
Guest VLAN 172 172.16.1.0/24
DMZ LAN? VLAN? Suggestion pls.All should have internet.
11 and 22 should have to restrictions between them.
172 should only have internet, nothing else.LAN1 VLAN 1, 22 and 172
LAN2 VLAN 1, 11PS. I have never been able to create VLAN 100, it just doesn't work with that VLAN. I used to have client VLAN 100 with 10.100.1.0/24. But had to change due to this (bug?). DS.
-
Hmm, there's no reason VLAN 100 shouldn't work. I have seen others use that many times, 100, 200, 300 etc is quite a common numbering scheme.
Ok, so currently the switch is in port VLAN mode which means it just passes all traffic to all ports so VLANs 20 and 2100 are available everywhere. Which mean your two switches could be using them. Are they both configured to use those VLANs? You would have to reconfigure them to use these new VLANs if so. Assuming you need them.
Steve
-
@stephenw10 Yes the switch is today in port VLAN mode and all VLANs are available on all ports.
So what I want to do is to send VLANs 1,22 and 172 via port LAN1.
And VLANs 11 LAN2.
And DMZ on LAN3 (I discovered that I had forgot it in an earlier post). -
 J jimp moved this topic from General pfSense Questions on
J jimp moved this topic from General pfSense Questions on
-
Ok, so to do that you will need:
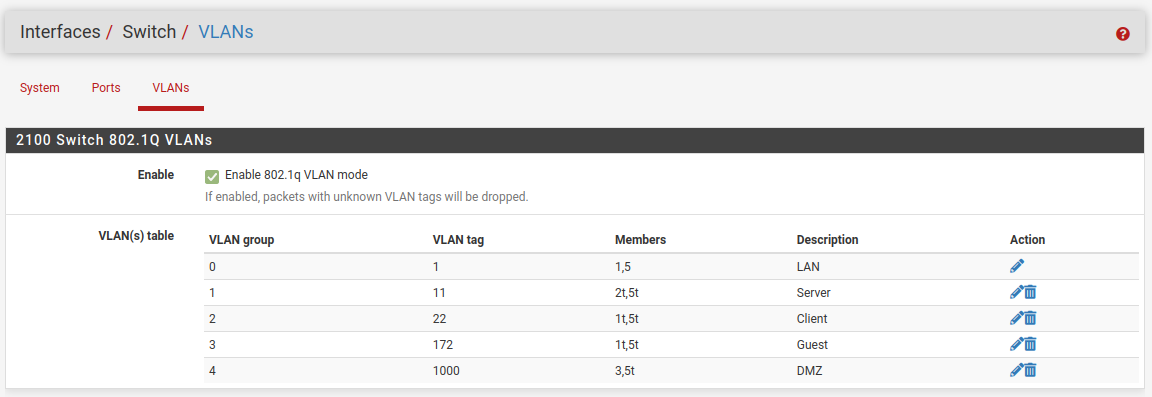
I choose VLAN 1000 to use for DMZ but you could use anything there. Since that's untagged on port 3 you also need to set:
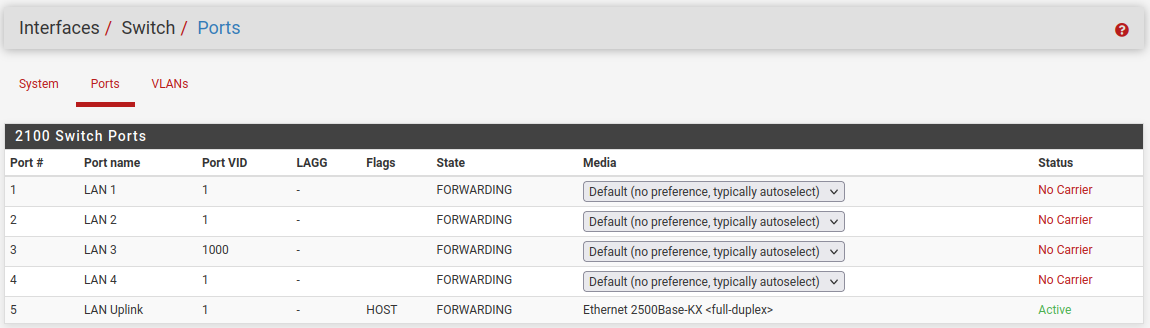
Port 4 is unused in that setup.
Those VLANs are tagged out of ports 1 and 2 so the switches connected to them will need to be configured for that. It sounds like they already are though.
Steve
-
@stephenw10 Thank you! :)
A question though.... on the VLAN(s) table part.
Thee two panels are the ones that I just cant grasp.
Ports 1-5 is physically LAN1-4 and 5 as uplink. That is the easy part.Now over to the strange part... VLANs.
VLAN Group 0, is that LAN1 (1) and LAN1 and LAN-Uplink (LAN5) as members?
And the group 1, is VLAN11 and LAN2, LAN5, that means that VLAN 11 should be on port 2 and 5, that is also the internet "connection" between them?Am I getting this right?
-
Yes. The VLAN group number is just the number in the list, the order there is of no significance.
So, yes, group 0, which is VLAN ID 1 (packets tagged as VLAN1) has member ports 1 and 5. Both are untagged.
That means that if the switch has has a packet that is tagged 1 it can will send it out of ports 1 and 5 and it will untag it as it leave the port.
VLAN1 is special. Most switches use this as the default internal tag and you should not not use VLAN1 externally if you can possibly avoid it:
https://docs.netgate.com/pfsense/en/latest/vlan/security.html#using-the-default-vlan1On the ports tab you will see that all ports except 3 are set to use 1 as the Port VLAN ID. That means that untagged traffic arriving at that port from outside the switch is tagged as 1 as it enters. Inside the switch all packets are tagged with something in 802.1q mode.
Thus if you ping something on the LAN subnet from pfSense itself a packet leaves the LAN interface untagged since that isn't a VLAN (mvneta1). It enters the switch via port 5 which is internally connected directly with mvneta1. It's untagged so the switch applies the PVID and tags it 1. The switch then sees the only other port that is a member of VLAN1 is port so it sends it out of port 1. Because it's an untagged member it strips the tag as it leaves the port so the packet arrives at whatever is connected to port 1 as untagged.
For group 1, VLAN11, both member ports are tagged. That means the switch will send packet out of those ports without stripping the tags. It also means it will accept packets arriving on those ports that at tagged VLAN11.
Since there are no untagged members of VLAN11 we do not have to set a PVID. We are only dealing tagged traffic.For group 4, VLAN1000 DMZ, we have tagged and untagged members. Traffic arrives on the port 5 tagged, from a pfSense VLAN interface, and is send out of port 3 with the tags stripped. That means you can connect a client directly to port 3 and it doesn't have to know anything about the VLAN. But in order for replies to work we have to set the PVID on port 3 as 1000. That way the untagged replies from a client will be tagged only VLAN 1000 and correctly send back to the VLAN1000 interface in pfSense.
Steve
-
@stephenw10 Thank you once again, one more drop to finally break the wall...
It this tagged non-tagged traffic that messes this up for me.
I will need to read you post a few times before I can say if it helped me or not.One question though VLAN1, I am not gonna use it in any way, but also I do not need to care about it? Setting up a DHCP and what not for it?