Bleedover of services
-
I am in the process of securing a machine and am running into an issue where
I am getting bleedover for lack of a better term.For example I run nmap on a different network, against a machine that I only want to have 80 and 443 available on I still see ssh as a open port as well as 8081 and 8443 (I am running PFBlockerNG). When I go to those open ports I end up on the firewall itself which I do not want.
I am running
2.6.0-RELEASE (amd64)
built on Mon Jan 31 19:57:53 UTC 2022
FreeBSD 12.3-STABLEI have also tried putting in a Block rule on the WAN interface to block all traffic to port 22 TCP with a source of any and a destination of any on port 22.
The only way I can stop ssh from showing as an open port is to disable it on the firewall itself but then I cannot ssh to it from the local network.
Suggestions?
-
@criley where are you running nmap from exactly.. Out of the box unsolicited inbound to wan is deny.
But if your scanning your wan IP from lan with any any rule it would be allowed.
Where exactly are you scanning from to where, and where do you have firewall rules setup? Traffic is evaluated as it enters an interface from the network its attached too.
-
@johnpoz That is why I am so confused. I checked and I do not have a deny all rule on the Wan side, I do have the Block private networks rule, the Block bogon networks, then a rule to allow ICMP and then I start with individual port openings where I open FTP, HTTP, HTTPS, etc.
This firewall has been running for years and I am just wondering if there is a rule that was dropped over that period or was lost in a upgrade.
I am running all of my scans from a entirely different network that should not have any elevated privileges.
Any assistance is greatly appreciated as I got bosses breathing down my neck.
-
@criley LAN has "allow to all" rules by default. All other interfaces have no rules, so the default deny rule applies and all traffic gets dropped unless allowed.
Do you have any WAN rules or NAT rules allowing ports 8081 or 8443?
In pfBlocker DNSBL settings do you have "Web Server Interface" set to WAN?
You can view active rules: https://docs.netgate.com/pfsense/en/latest/firewall/pf-ruleset.html
-
@criley do you have any rules in floating? Can you post up your wan rules..
As mentioned the default is deny, it is not shown.. If there is no allow rule on wan, or in floating then unsolicited traffic is denied by default.
-
@johnpoz I am not sure how to post just the WAN rules so I zipped up and attached both the firewall and nat rules. I appreciate you taking a look and hopefully pointing me into the right direction.
-
@criley said in Bleedover of services:
I am not sure how to post just the WAN rules
simple screen shot
-
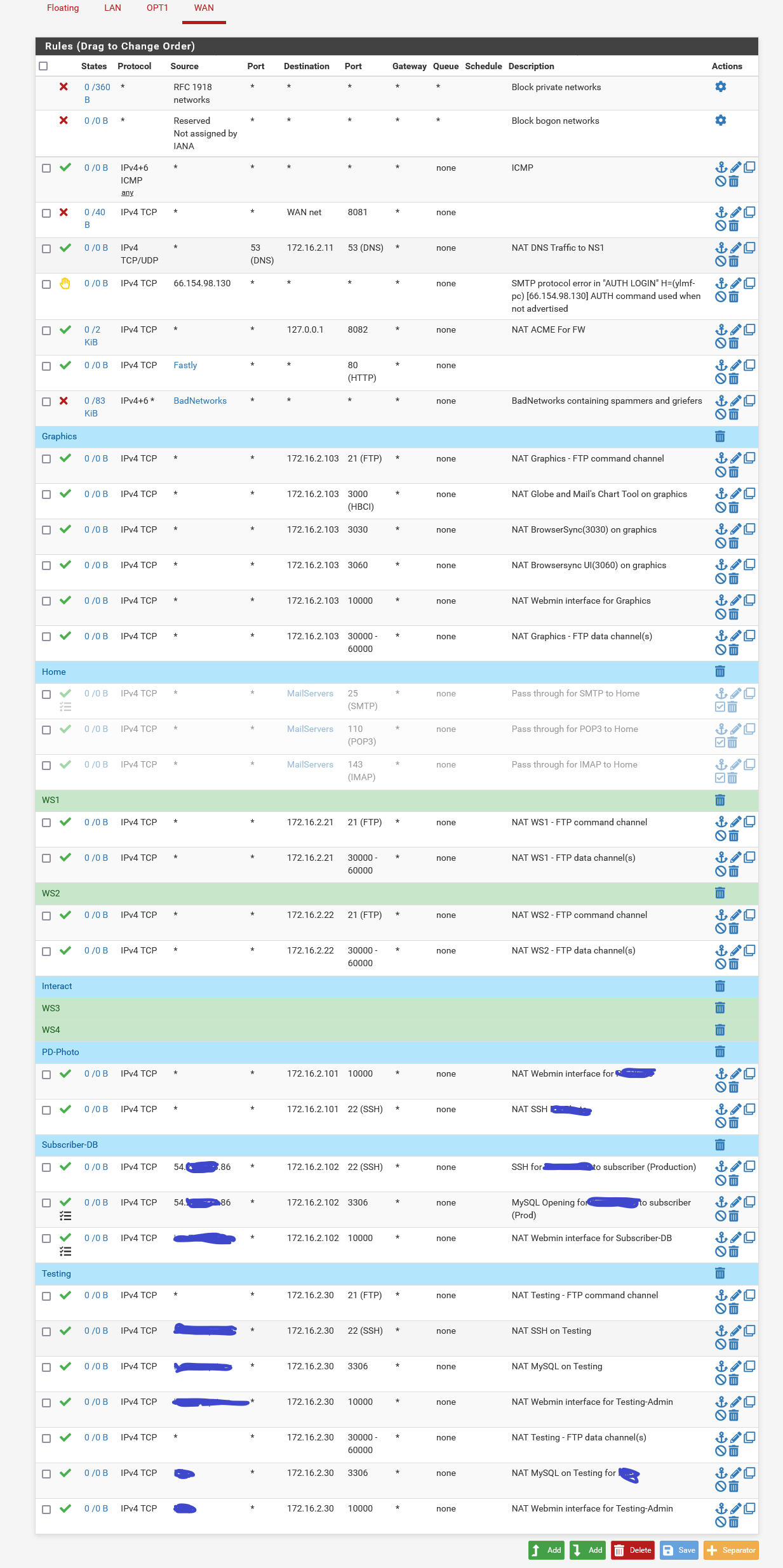
@johnpoz Here we go....
-
@criley do you have anything floating tab..
-
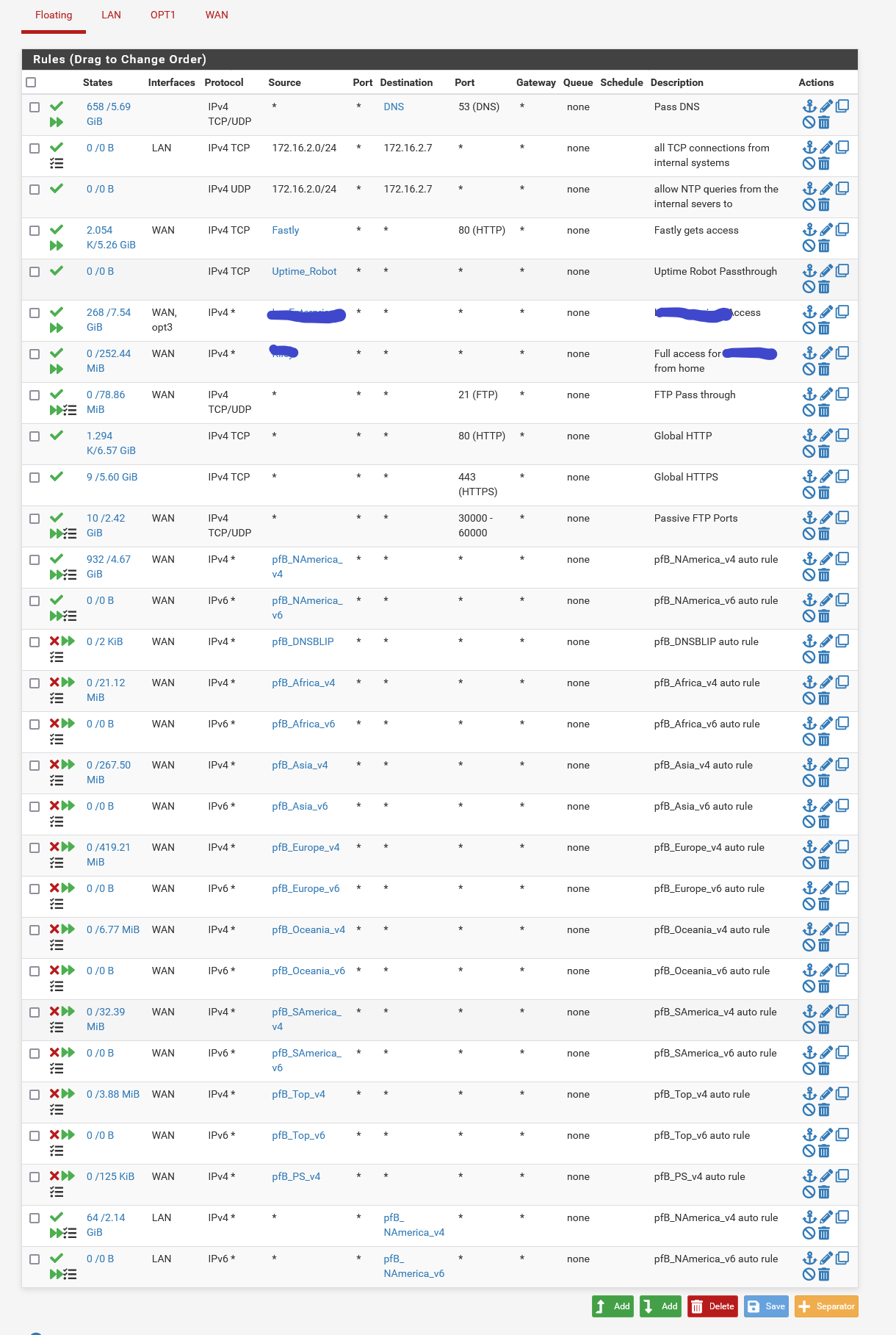
@johnpoz Here you go
-
@criley well you got any any rule from anything NA
And what are those rules 80 and 443 that don't show any interface? Pretty sure those would allow on any interface.. From looking at the rule in the zip you sent.
pass inet proto tcp from any to any port = http flags S/SA keep state label "USER_RULE: Global HTTP" ridentifier 1472233311 -
@johnpoz Those two rules that you pointed out were put their by pfBlockerNG. I have disabled them and will retest.
-
@criley well your using pfblocker wrong then ;) It only does what you tell it to do.. But a floating quick rule would be evaluated before any rules on your wan interface.
-
@johnpoz I went ahead and disabled both of those as well as the global http that you mentioned and I am still able to see ssh as well as the 8081 and 8443 both of which are from PFBlocker. Like I said the thing that really makes me crazy is why ssh still shows and when I try to ssh to the servers ip it drops me at the firewall ssh prompt.
-
@criley Did you have open states?
https://docs.netgate.com/pfsense/en/latest/troubleshooting/firewall.html#new-rules-are-not-appliedWhat are the NAT rules for port 22?
pfBlocker blocks are generally added to LAN (outbound) or WAN (inbound) and not floating rules which can appear unpredictable to those not familiar with them.
https://docs.netgate.com/pfsense/en/latest/nat/process-order.html#floating-rules-notes
https://docs.netgate.com/pfsense/en/latest/firewall/floating-rules.html