unable to connect vlan to vlan?
-
@johnpoz
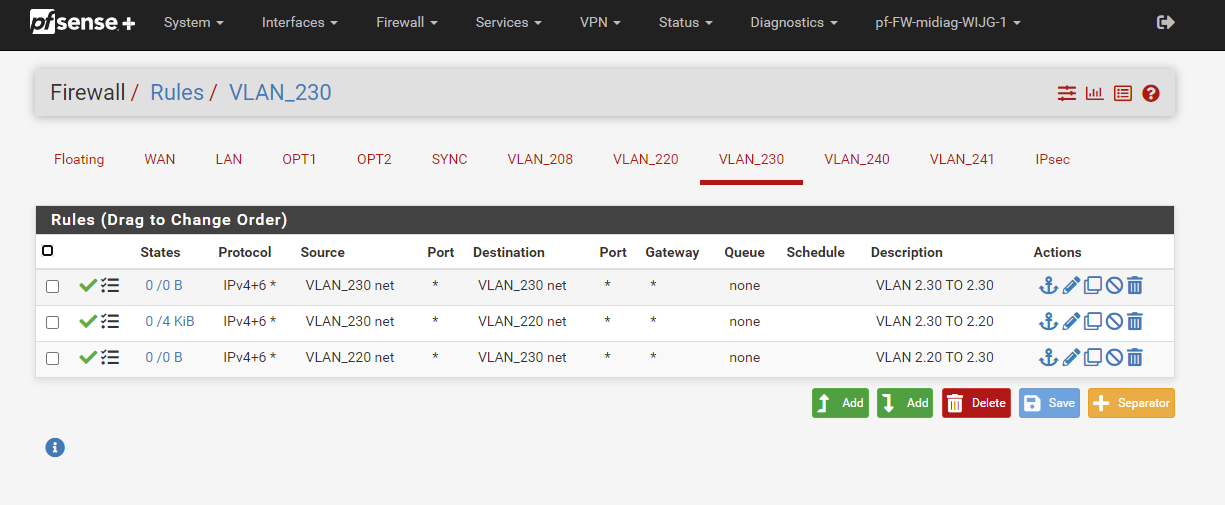
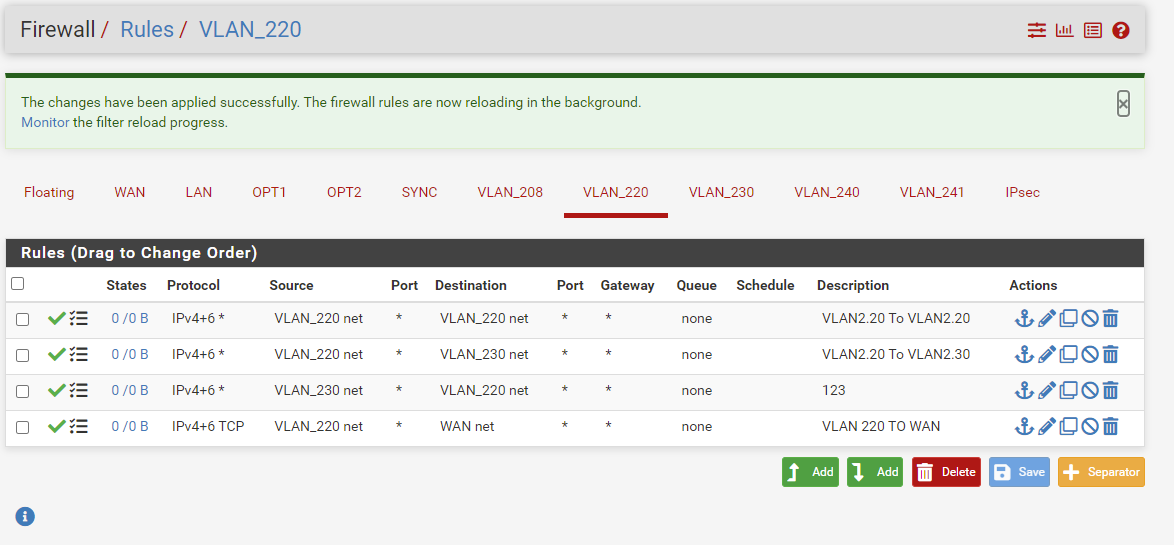
So this should be the correct order then?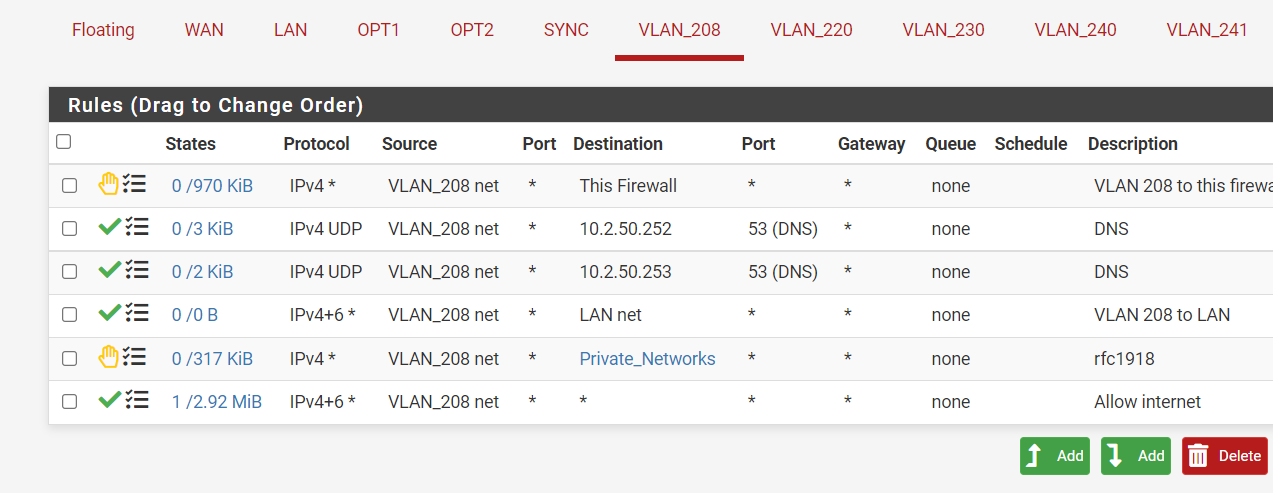
-
Yeah those would work for allowing devices on 208 net to talk to those 10.2 Ips, as long as those are not IPs of pfsense since your blocking "this firewall" first.
If those are name servers - you prob want those rules to be udp/tcp.. In some instances dns can and does use tcp..
-
@johnpoz
The 10.2.50.252 is the VIP of the pfsense, the 50.253 and 10.2.8.253 are the DNS servers the pfsense uses when I do a ipconfig on the laptop.I changed a little:
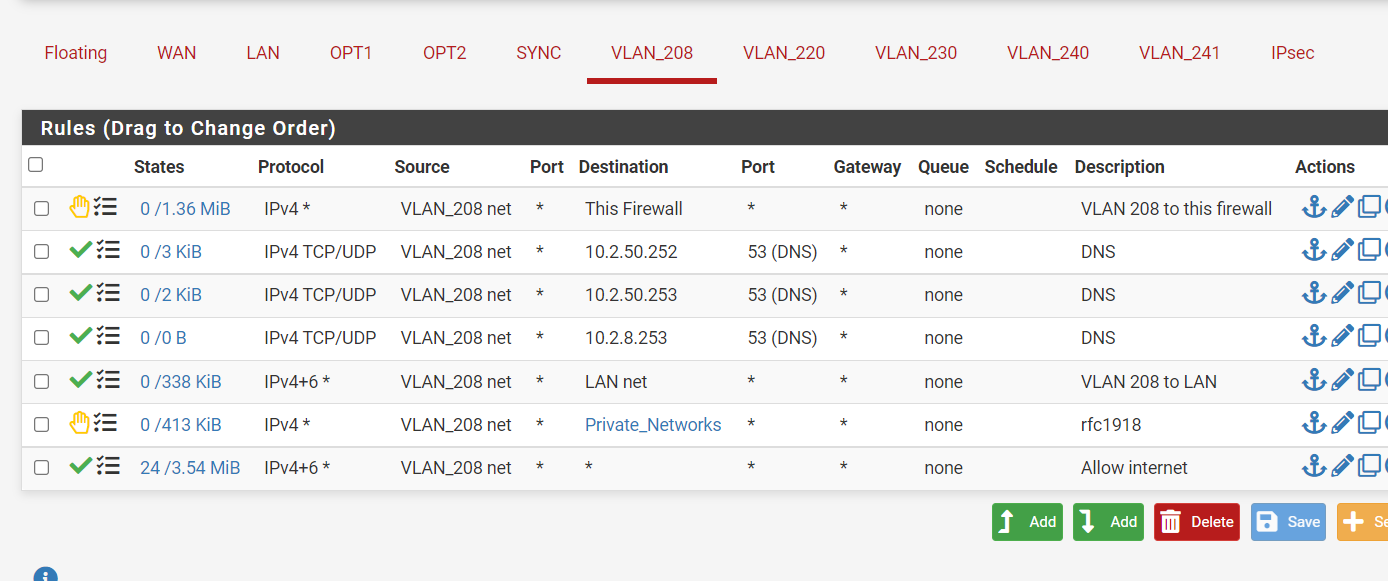
But this 208 is used by an SSID on the wifi. If I connect to that SSID , I cannot access the internet?
-
Guess my order was wrong.
did :
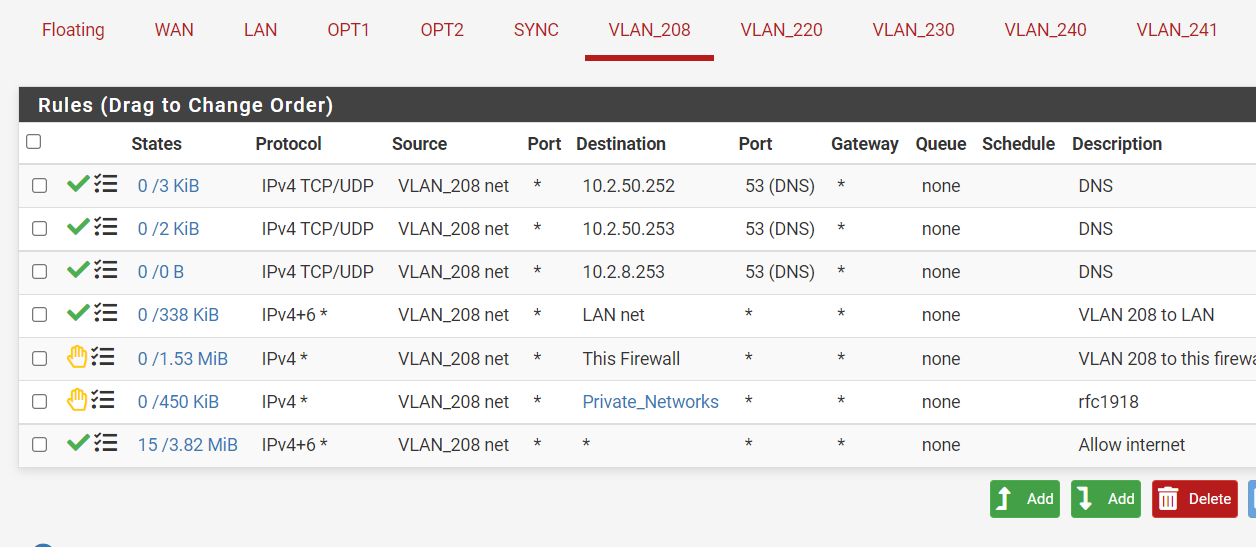
And now it seems to be better for the internet. But now I CAN access the firewall gui and that I don't want? :(
-
@nick-loenders so what are those IPs 10.2.x are those pfsense IPs? Either way if you want to block access to gui of pfsense on its IPs
Create a rule at top that blocks access to the webgui ports (say 80 and 443) to "this firwall"
-
I do my best :) But it won't block.
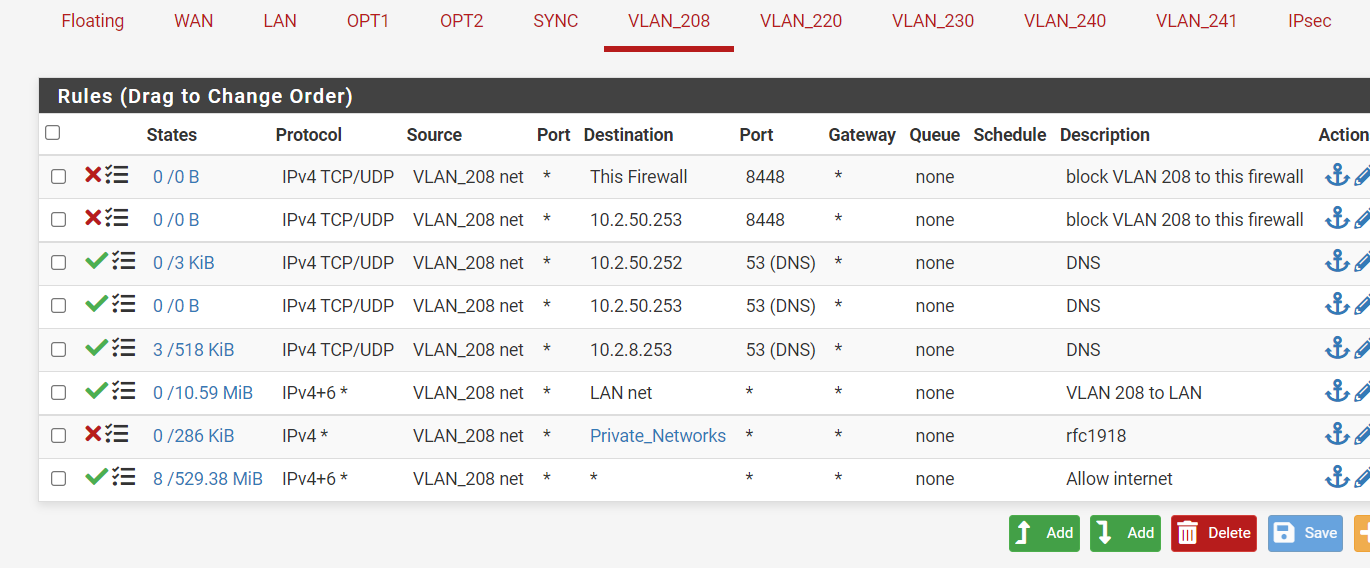
Off course the LAN net is the 10.2.50.0/24 as well, problem in there ?
Private_Networks is:
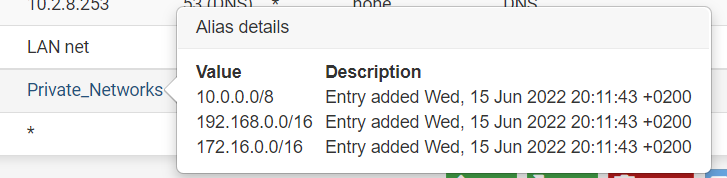
VLAN 208 has ip's 10.2.8.0/24
-
@nick-loenders you need to check states.
If something is allowed, and you connected to it. A state would be created allowing that traffic. If you then put in a block to that thing. Until the state goes away it would still be allowed, states are evaluated before rules.
So you need to either wait til the state expires, or you kill it via the state table in diagnostic menu.
Also when troubleshooting firewall rules, make sure you don't have something in the floating tab that would allow it.
It goes states
floating rules
interface rulesSo even if you create a block in the interface, if you have some quick rule set in floating that allows it, it would be allowed no matter what rules you put on the actual interface.
edit: BTW 172.16 is a /12 mask not a /16... The 172 space is 172.16-31
-
@johnpoz the states thing probably did it yesterday.
I'll have to change the subnet yes. Good remark :)