Subnetting
-
@johnpoz Well, I have some machines on the LAN-side with private IP.. mostly they are public, but still...
I also have 1-1 NAT rule at the end that says external IP XX.1->XX.0/24. Without this, most of the network goes down. Seems like I must have it.
I tried defining a /28 on a server on the network now and as soon as I added an VIP in pfSense on the LAN-interface, it worked and server got internet! If I removed the VIP, the server didn't get internet access. Supplying the .1 as gw as I have on all other machines didn't work either. Of course, it isn't any more secure, but I guess this is how I can start without disrupting the /24.
-
@fireix said in Subnetting:
I have some machines on the LAN-side with private IP.
well those would go in their own network or vlan.
-
@fireix said in Subnetting:
I have some machines on the LAN-side with private IP.. mostly they are public, but still...
Then configure routing and firewall accordingly. For example, if you create additional subnets, you need to create rules to allow them access to the Internet. For security, NAT does nothing that a properly configured firewall doesn't.
-
@jknott This is my relative simple setup. I struggle to understand how I can do this any different.
I borrowed the public static IPs of Google to illustrate my public IP-addresses. As you see, I also have some private IP (192.168.0.X) networks.
If I remove that last line of the 1-1 NAT, all traffic to my public IPs at 142.250.74.X stops (except 142.250.74.163 of course). Even if I have the firewall rule that says it should be allowed in. Similar, if I remove the WAN *->142.250.74.12 ALLOW-ALL rule and keep 1-1 NAT, the inbound traffic stops.
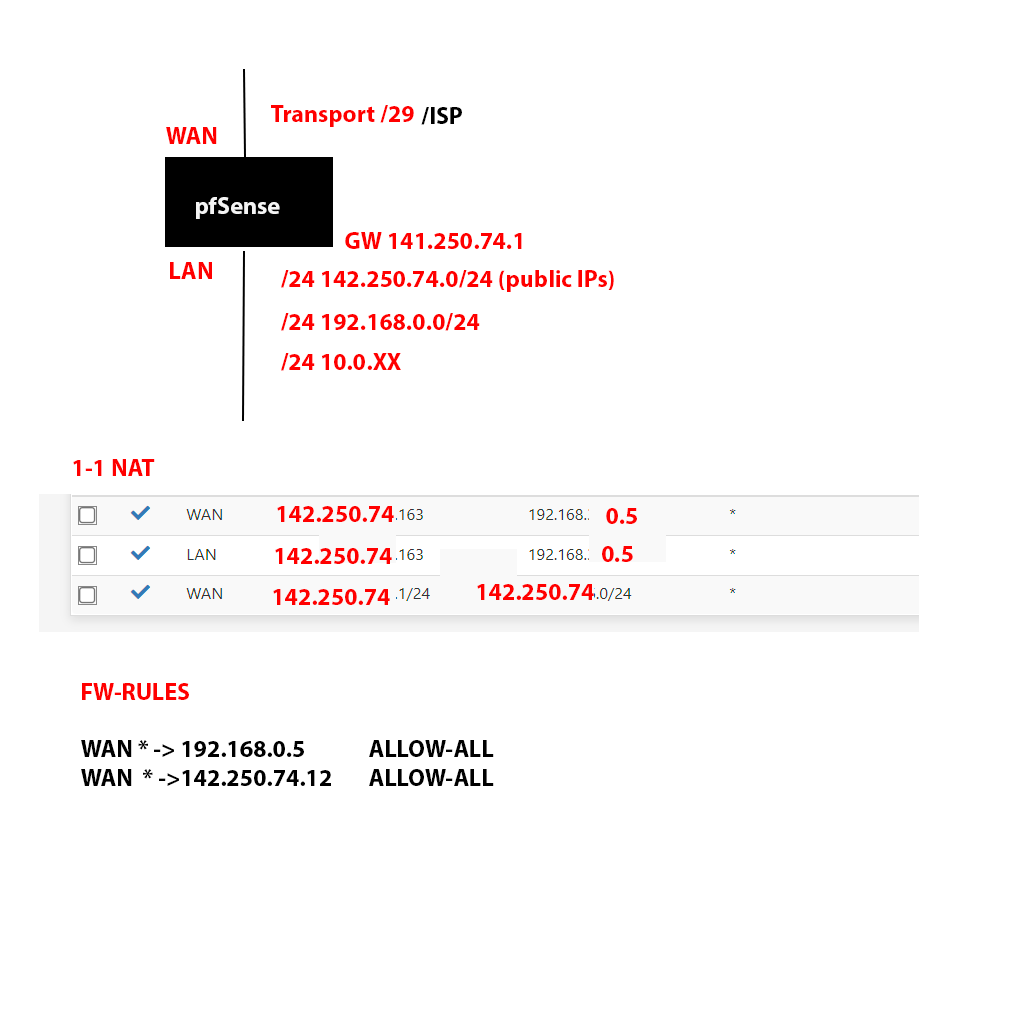
So what you say, is there a way to avoid using NAT in this case? Note that I have public IPs on my LAN-side because of mostly webservers/cpanel-servers and other software that requires binding to public IPs. There are some exceptions, that's why I have maybe 15 rules in 1-1 NAT (I only posted two examples).
-
[Note: The OP's lack of any context forces my comment to be high level and generic. Were details included, the entire approach might be suspect, and more useful info offered.]
@fireix Where to start...
OK, which device are you using, or at a minimum, how many Ethernet jacks dos your pfsense device have on it?
You should have a dedicated jack (physical LAN for your inbound Internet traffic. Think of it like a DMZ network-one which would never mix traffic (on any layer) with the trusted networks.
At a high level, your WAN interface should expose or advertise the publicly routed addresses-not a network behind the public one(s). You use routing to then direct that traffic to the DMZ, even having specific IPs go to specific DMZ IPs.
I would make my DMZ (OPTx) LAN something like: 10.250.74.0/24 (using some of the public range to make it easier), and it would have hosts that would get traffic from the WAN interface, but routed. It is a fairly large setup that has a public /24, but let's say you you have hosts on it like:
142.250.74.1, .50, .100, .203, ...
I would then NOT make the DMZ lan reflect their same 4th octet, but group them based on functions. So maybe the first 2 in the list above are web servers, then I would make them:
WAN 140.250.74.1 = DMZ/OPTx 10.250.74.21
WAN 140.250.74.50 = DMZ/OPTx 10.250.74.22
[...keeping the web servers in the 20s]FTP servers in the 40s, etc. This makes life so much easier when you start accessing the DMZ from internal, and you don't have to re-do everything if your public IP range gets smaller, dual ISPs, etc. You don't want to tie things 1:1, but rather keep things isolated (numbering scheme-wise)
Personally, the LAN (trusted) network(s) should be on the LAN interface, and use rules to allow any of those hosts to access a DMZ host-being extremely specific-not just IP but port & protocol. You should deny all, then pinhole to/from the trusted LAN, as it is your highest priority.
As for your 2 LAN addresses, 10.0.XX is a /16 not a /24. Each 'octet' is 8 bits. Also I suggest you never, ever have an Allow All inbound-especially from the Interwebs. I won't go into all the reasons why it's Bad(TM) here, just believe me. Pin-holes will save your hide.
I suggest you VLAN all your internal networks, and don't put hosts on the 'hard' LAN (address of the physical LAN port).
You will find situations where this or that group needs fine-tuned access, and this is far easier to do/manage/maintain in VLANs than one LAN segment or overlapping LANs on a singe interface.Just a comment, but it looks like you aim to use the same LAN network address(es) on different LAN segments. If so, this will not work, and is a Bad(TM) idea. Every physical, logical, and virtual lan segment needs to be unique.
This is just a high level feedback of what you posted.
For getting started with networking similar to what you describe, but books. But if you'd rather read about pfsense on the Interwebs, start here:
https://docs.netgate.com/pfsense/en/latest/recipes/example-basic-configuration.html
https://docs.netgate.com/pfsense/en/latest/vlan/index.html
etc.If you have managed switches, you will want to configure them for VLANs to match the firewall, or Weird(TM) things will happen. Just do port assignments for now (Port X = VLAN Y), and get fancy later.
More context = less wasting your/everyone's time. :-)
-
@bogusexception Thanks for your thougths, it is a pretty big job to change all this after so many years with the current setup.. at least it shows that the thing I want to do is harder than I knew :) I have run transparent fw for 10 years or so and this current setup/network (this kind of setup was suggested by a forum thread here for about 2-3 years where they suggested to use a transport network on the WAN side to be able to use the fw in a more "normal" fashion, since transparent wasn't 100% supported on pfSense - even if it worked).
"Allow All" was just easy for me to write to show the principle. In reality, there are port 80, 443, 22 etc. I would never do allow all on any IP of course. That would render the fw useless ;) I have 500 rules or so, some just for one port..
The 10.0.XX was a typo, I ment 10.0.0.0 (so a /24).
With regards to your setup: Most of the servers have dual purpose and it is one customer per server: Often one of their FTP server also includes a web-server and maybe even email or VPN.. or special applications. So your grouping based on functions would be a bit tricky. They are totally different type of servers, it is not like they have a small dedicated role each. I have grouped ports and function as best as possible in fw rules, but often not that many common setups. So if I was to do port forwarding, it would be massive(!) work.
The setup I have now looks pretty much the default you get at a data center and since 99,9% of the servers are public on many ports, it was just easier to use their public IP. Remember I had transparent fw (using Fortigate first 8 years) and then it was extremly easy to manage. People saying NAT was a bit slower also, so it worked just fine. But the Fortigate had expensive licenses..
Note that since it is mostly public servers, each server is like a isolated box with their own integrated fw. So network traffic between them isn't really a big deal, since you assume they are all available on the internet and should handle the noise. Having a fw gives just a bit better security/control.
-
@fireix said in Subnetting:
This is my relative simple setup. I struggle to understand how I can do this any different.
First off, as mentioned, there's no need for NAT. You have a /29 transit network. This is how your /24 is routed to you. In pfSense, you can split that /24 into smaller networks to be assigned to an interface or VLAN. For example, you could split it into 2 /25s or a /25 and a couple of /26s. etc., according to your needs. This is basic routing. Nothing fancy about it. In comparison, on IPv6, I have a /56 prefix from my ISP. That gives me 256 /64s. I assign one to my main LAN, my guest WiFi VLAN and a test LAN. I also use one for my VPN, even though I only have one user on it.
-
@jknott I see :) But why does the traffic (to any IP on the 142.250.74.X) stop once I remove the last 1-1 NAT (in the picture)? The traffic still flows to the 142.250.74.163 further up in the NAT-rules, but the rest stops.
I must have done a mistake somewhere, but no idea where to look for it. Perhaps the 1-1 NAT kind of "cover-up" my mistake and that is why it works when I just do NAT-for everything.
OR is it that I have to disable NAT-totally, if not, it will only work in "normal" mode if ALL is nat'ed? All or nothing? The only reason I use NAT at all is that a few PCs with private IP needs a public IP front. If it was my PC, I could just added the public ip to those PC as 2nd IP.
-
@jknott I only have like 4 physical interfaces on this Supermicro-box (and two of them used for LAN LACP-lag against two managed stacked switches), so I guess VLAN is the only way to go in my case. That is for sure next. Haven't got it working on my dlink switches so far, but i guess one thing at a time..
-
@fireix said in Subnetting:
I must have done a mistake somewhere, but no idea where to look for it. Perhaps the 1-1 NAT kind of "cover-up" my mistake and that is why it works when I just do NAT-for everything.
Sometimes, the best thing to do is start from scratch. Your first mistake was using NAT when you don't need it. Determine your subnet needs and take it from there.
And yes, you use VLANs where appropriate or if you don't have enough physical ports. In my network, I use a VLAN for guest WiFi. Beyond that, I have no need for VLANs, at least not at the moment. If you use VLANs because you don't have enough ports, you use a managed switch to separate the VLAN(s) from native.
-
@jknott Ok, so you are saying that I have to either use NAT for all - or not at all? Just want to be sure what you are telling me :) Since I for now at least need NAT, I need to have that 1-1 NAT rule for all public IPs, correct?
-
You don't need NAT. It was created to get around the IPv4 address shortage and with a /24, you likely have more than enough addresses.