pfSense on HyperV = Massive problems
-
So, im trying to run pfSense on HyperV and I just cannot get it right. My setup is a Wireless 4G router connected to pfSense and setup as a upstream gateway.
My issue is massive latency in almost everything, Failed DNS resolution on SOME hostnames but not all., some clients do not receive DHCP offers at all. Very weird behavior.
I have 2 virtual switches setup, 1 for LAN and 1 for WAN.
This leaves me with 4 interfaces, LAN WAN and VirtualLAN and VirtaulWAN.Ive disabled the IPv4 and IPv6 properties on all except for the WAN and LAN interface connected to my router, as my upstream gateway. So basically both virtual interfaces have noth IPv4 and IPv6 disabled so they are not clients on the network.
On the LAN interface I have enabled IPv4 only and given a static IP for remote access into the VM host.I then setup the PfSense LAN interface with the VirtualLAN and give a static ip of say 192.168.1.1 and WAN interface with static ip of say 192.168.10.2 and the upstream gateway is sitting at 192.168.10.1.
Is this the correct way to set this up? Im trying to avoid having double ups of clients on the network for each interface. Does disabling the IPv4 and IPv6 properties still just pass traffic through?
Thanks for the help!
-
-
 S stephenw10 moved this topic from General pfSense Questions on
S stephenw10 moved this topic from General pfSense Questions on
-
@bob-dig thanks for the information. This will come in handy if I have any issues.
What i'm really struggling with is getting the interfaces setup correctly. Im following this guide.
https://docs.netgate.com/pfsense/en/latest/recipes/virtualize-hyper-v.html
However, when I setup the LAN interface as a "internal network" I cannot ping or reach my pfSense login page.
I have created 2 Virtual Switches just as shown in the guide.
WAN - with the WAN interface selected and setup as a "External Network" and have disabled Allow management operating system to share this network adapter as I have a dedicated NIC for WAN.
LAN - created the LAN interface and just selected "Internal Network".
Assigned both interfaces to the VM and assigned them correct, WAN gets DHCP, and I set a static IP on the LAN interface in the same subnet as my LAN, and also as the physical LAN interface on the host, yet still I cannot ping or reach the pfSense web page.
Could someone advise me on the CORRECT way to setup these interfaces on HyperV. I would like to do it once and once only and get it right.
Thanks in advance.
-
@deanfourie Internal is correct if you sit in front of this physical machine. You also can use external if you connect this interface to a physical switch.
-
@deanfourie said in pfSense on HyperV = Massive problems:
and I set a static IP on the LAN interface in the same subnet as my LAN, and also as the physical LAN interface on the host,
What do you mean by that? pfSense should be the router in my mind.
So you want pfSense to be only a virtual firewall for another vm?
-
@bob-dig Ok I think I get you.
if I understand correctly, Internal and Private are just the HOST machine internal communication. When selecting internal or private, traffic will not leave the HOST at all?
This needs to also be setup as a external interface for LAN traffic to exit the LAN interface out to the physical LAN switches and infrastructure?
Thanks
-
-
@deanfourie Please don't assume but tell exactly what your setup is, how many routers, how many switches and hosts etc. and what you want to achieve. Will make answering much easier. Maybe make a diagram.
-
@bob-dig Sure, let me do the best I can here
4GWireless Router WAN Incoming *Upstream Gateway" >>
pfSense WAN Interface /30 Network>>
pfSense LAN Interface /27 Network >>
Cisco 48 Port PoE Switch >>
Wifi AP >>
CLIENTsPretty basic, just a home setup. Hope that makes sense.
-
@deanfourie Ok, make another external vSwitch for pfSense LAN and connect it to the Cisco Switch. You also can use this connection for the VMhost (shared) or use another physical NIC (if you have) to the Cisco switch for that, that is up to you.
VLANs come on top of this if you have...
-
@bob-dig yup thanks have done that. But speeds seem super slow and connection is intermittent.
-
@deanfourie Then #2.
-
@bob-dig yup ok cheers. Thank you
-
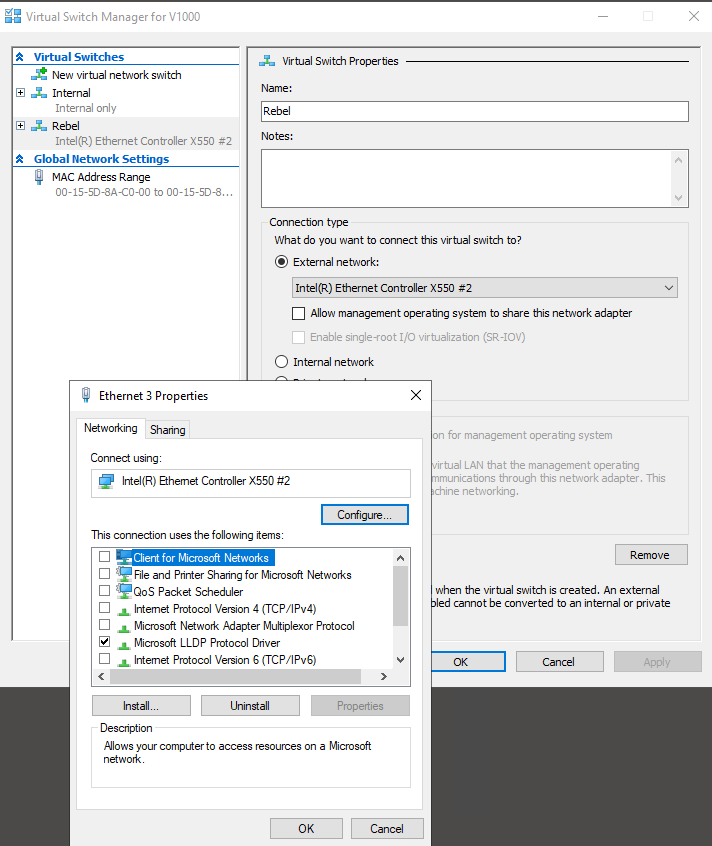
@deanfourie I have another question regarding the NIC configuration in windows.
Lets take for example my WAN interface. I have the ability to DISABLE IPv4 on this interface. If I disable the IPv4 and IPv6 option on this interface, it basically disables everything on the interface except the Microsoft Hyper-V Interface.
This still allows pfSense to send and receive traffic on this interface, however windows just simply doesn't see it.
What are the disadvantages or advantages to doing this? And how does this still allow traffic to pass through. Its like it just become some kind of transparent bridge interface the just allows traffic to flow through it.
Im not gonna lie, I like it, as I can manage which interfaces actually are sitting on what networks on the HOST. This way I can configure my HOST Hyper-V LAN interface for traffic and have the traffic also router through pfSense and I dont have a pointless client sitting on the WAN network.
Hope that makes sense.
Any ideas?
Thanks
-
@deanfourie said in pfSense on HyperV = Massive problems:
Lets take for example my WAN interface. I have the ability to DISABLE IPv4 on this interface.
No, you wouldn't share this with the host to begin with so no need to disable anything.
It will look like this on the host, don't mess with it.