Captive Portal breaks policy routing for bypassed MAC addresses after upgrade to 22.05 [fixed]
-
We also have a Problem since Update. The Problem is that the Login Page dont appear. Any one else have this Problem?
-
@opit-gmbh said in Captive Portal broken after upgrade to 22.05:
The Problem is that the Login Page dont appear. Any one else have this Problem?
You've read the entire thread, have you ?
I didn't saw someone saying that the login page doesn't appear.
So whatever you issue is, it isn't "dummynet: bad switch 21!" or "bug 13290" or bug "https://redmine.pfsense.org/issues/13323".For what it's worth : I'm using 22.05 and the captive portal. Authentication is handled by FreeRadius, the pfSense package. https login is enabled. No other fancy stuff.
It works.I did saw these "dummynet: bad switch 21!" in the logs, - the portal functionality was doing fine - so I added the patch https://redmine.pfsense.org/issues/13323 and that took care of things.
-
Any idea what can cause my problem or how to debug it?
-
@bitrot How did you apply the patch? Did you go into System >> Patches >> Add New Patch... then upload the .patch file from Bug #13323
-
If you use the captive portal, you should bookmark this page.
Troubleshooting Captive Portal. -
@bobcat05 Yeah, System >> Patches >> Add new patch and then use the URL/Commit ID for the patch to upload it. (https://github.com/pfsense/pfsense/commit/add6447b9dc801144141bb24f8c264e03a0e7cae)
This fixes the Captive Portal policy routing issue. I don't think this fixes the dummynet message. I haven't tested for that. There's a separate bug report for that. https://redmine.pfsense.org/issues/13290#change-61935
-
@gertjan yeah i know this site. but all worked perfectly before i upgraded to 22.0.5. We have multiple Netgate's running with mostly the same config. The Problem with the not upcoming Captive Portal is just on some of them, not on all! So i don't know what can cause this problem. Maybe some have a tipp where i can have a look.
An all our Netgate's we have running: pfBlockerNG und Snort (not in blocking mode) -
@opit-gmbh said in Captive Portal broken after upgrade to 22.05:
The Problem with the not upcoming Captive Portal is just on some of them, not on all!
Then you have the solution already available.
On two pfSense sites, only the settings and surrounding hardware are different.
pfSense on two systems is always identical.
So, compare the settings of a working and non working site.
Most often, its a broken DNS. -
@bobcat05 Is there an easy way to revert back too 22.01?
-
@backlash619 unfortunately not... You have to open up a support ticket requesting access to the version of firmware you want. Then, they send you an image file that you have to write it to a USB stick and completely reinstall pfsense using the console port on the device.
-
@bobcat05 said in Captive Portal broken after upgrade to 22.05:
@backlash619 unfortunately not... You have to open up a support ticket requesting access to the version of firmware you want. Then, they send you an image file that you have to write it to a USB stick and completely reinstall pfsense using the console port on the device.
a) there are reinstall instructions for each model, e.g.
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/reinstall-pfsense.html
(if not Netgate hardware, per other posts one installs 2.6 and re-upgrades to Plus)b) going forward, ZFS and Boot Environments should make rolling back easier. See the Netgate video linked from https://www.netgate.com/blog/pfsense-plus-software-version-22.05-now-available
-
@backlash619 @bobcat05 @steveits The procedure for a re-install is the same as for a downgrade. I did such a re-install after upgrading to 22.05 just recently exactly because I wanted ZFS Boot Environments capability going forward. The re-install/downgrade process is a lot less difficult than some people make it out to be. Even creating a ticket with support for a firmware download isn't a big deal. They responded to my request with a download link within minutes.
-
I also have the issue on 22.05. A captive portal user can blow past the firewall rules and get access to another secured LAN on the same router, etc. Luckily this is testing on a backup router and this didn't happen in production!
-
@turntheterribletank Did you try the patch?
-
@turntheterribletank Mine can even authenticate to radius... does the patch resolve this?
-
@backlash619 I don't know if the patch fixes your issue. Not sure if what you're facing is related. I don't use RADIUS authentication on my Captive Portal, so I'm not able to answer that. It's simple enough to apply the patch to test it out though. You can always disable the patch afterward if it doesn't solve your issue although I would apply it anyway because it does fix a problem.
-
This is a backup router, so I'm interested in a fixed release and not necessarily looking to patch. No issues with radius, etc. That's all fine.
Production and backup are both 7100 1u. The ability to roll these back will be nice. -
@turntheterribletank I have no issue applying an official patch that will go into the next official release, so I can have an important fix today. But you do you :)
-
@bitrot Yep. We won't be updating to 22.05 and patching. We'll wait.
-
@bitrot Sorry..
the patch file 13323.patch is different from patch https://github.com/pfsense/pfsense/commit/add6447b9dc801144141bb24f8c264e03a0e7cae
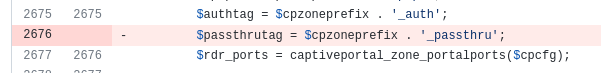
and in the patch file:

Luca