I can ping between two hosts from different VLANs
-
Hi, I have several VLANs created. I'm testing step by step the settings and I noticed that I can't connect from one host in VLAN 50 (192.168.50.4) to another host in VLAN 10 (192.168.10.6). But already, for example, there is no problem to send a ping from that host in VLAN 50 to another host in VLAN 10 (e.g. 192.168.10.3). There is also no problem to send a ping from this host 192.168.10.3 to 192.168.10.6.
On the switch side (Mikrotik) 802.1x is configured and on pfSense I have freeRADIUS which assigns VLANs to hosts based on certificates.
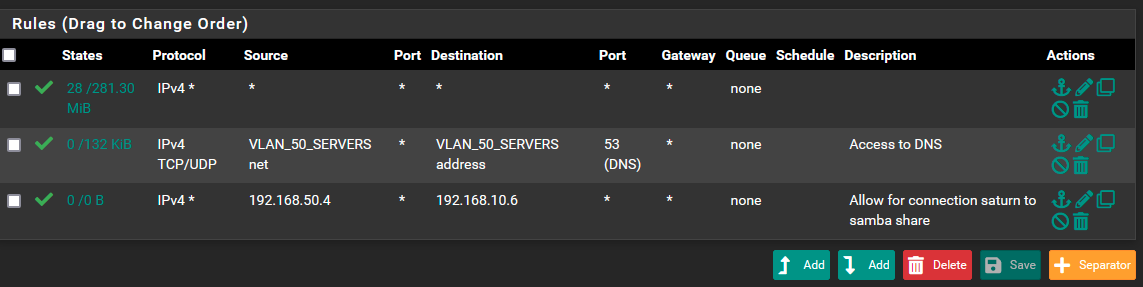
My rules for VLAN 50 look like the following. The one at the top is my act of desperation, which so far doesn't help either.
Please help. I don't know how to troubleshoot it.
-
@dansci Maybe kill the states before further testing or it is a host-firewall problem or the switch or you have rules on floating or created groups with other rules.
-
@bob-dig thanks for quick response
-
states cleaned - it didn't help
-
host firewall is not set
-
switch is not blocking anything
-
I don't have rules on floating
-
and I didn't created any group for other rules, everything for that interface is in that interface.
-
-
@dansci did you check the mask on this host 10.6? If the mask is say /16 it would think that 50.4 is in its same network and would not send the response back to pfsense.
I would sniff on your vlan10 interface while you have a constant ping to 10.6 from 50.4
If you see pfsense send the ping on, and you get no response then something on that host, firewall, wrong mask, pfsense not its gateway, etc.
You say you can ping other things in the 10 vlan from 50.. So that really screams something on that host you can't ping
-
@johnpoz for now I sniffed with Packet Capture in the pfSense.
Interface: VLAN10, IPv4 only, ICMP, host address: 192.168.10.6This is the result:
13:45:51.487384 IP (tos 0x0, ttl 63, id 17827, offset 0, flags [DF], proto ICMP (1), length 84) 192.168.50.4 > 192.168.10.6: ICMP echo request, id 15540, seq 141, length 64 13:45:52.511093 IP (tos 0x0, ttl 63, id 17866, offset 0, flags [DF], proto ICMP (1), length 84) 192.168.50.4 > 192.168.10.6: ICMP echo request, id 15540, seq 142, length 64 13:45:53.512045 IP (tos 0x0, ttl 63, id 18049, offset 0, flags [DF], proto ICMP (1), length 84) 192.168.50.4 > 192.168.10.6: ICMP echo request, id 15540, seq 143, length 64 13:45:54.526467 IP (tos 0x0, ttl 63, id 18282, offset 0, flags [DF], proto ICMP (1), length 84) 192.168.50.4 > 192.168.10.6: ICMP echo request, id 15540, seq 144, length 64 13:45:55.550161 IP (tos 0x0, ttl 63, id 18308, offset 0, flags [DF], proto ICMP (1), length 84) 192.168.50.4 > 192.168.10.6: ICMP echo request, id 15540, seq 145, length 64So it seems that the host 10.6 is not answering.
-
@dansci said in I can ping between two hosts from different VLANs:
So it seems that the host 10.6 is not answering.
Exactly - that was pretty obvious from what you said was happening, but the sniff gives you validation that pfsense is sending on the traffic.
I would check the mask on the 10.6 box, did you set that IP and mask by hand? This has come up a few times recently to be honest. If setting a static IP on the box to a /16 vs /24 would for sure give you the exact symptoms your seeing.
If not then that - then firewall or security software on this 10.6 box is the most likely problem - if this box has working internet access through pfsense.
But from the sniff you can see the ping is being sent to the 10.6 box - it just isn't answering.
-
@johnpoz 10.6 downloads the configuration via DHCP. The mask is correct, 24.
I tried to run Wireshark on this 10.6, but for some reason after running packet capture it crashes and I can't manage it.However, it turned out that this host has a non-stop VPN connection running to an external network. While in the previous configuration of my network, where both hosts were in one subnet (without VLAN) (50.4 and 10.6 were in 192.168.0.0/24) then there was no problem with connecting between them. Now that maybe this OpenVPN on 10.6 is causing 50.4 to not be able to get along with it. I need to verify that, but if that turns out to be the case then I'll have to work around the problem somehow.
-
@dansci said in I can ping between two hosts from different VLANs:
@johnpoz 10.6 downloads the configuration via DHCP. The mask is correct, 24.
I tried to run Wireshark on this 10.6, but for some reason after running packet capture it crashes and I can't manage it.However, it turned out that this host has a non-stop VPN connection running to an external network. While in the previous configuration of my network, where both hosts were in one subnet (without VLAN) (50.4 and 10.6 were in 192.168.0.0/24) then there was no problem with connecting between them. Now that maybe this OpenVPN on 10.6 is causing 50.4 to not be able to get along with it. I need to verify that, but if that turns out to be the case then I'll have to work around the problem somehow.
Depending on exactly which type of VPN client is configured and running on this 10.6 host, it very well could be the default route for this host has been changed by the VPN package to be a gateway at the far-end of the VPN tunnel. If true, then the host is replying via that gateway, and that gateway likely has no idea how to route a reply to your source IP (especially if your source IP is in RFC1918 space).
-
@bmeeks Here my knowledge is limited. How can I check which gateway has priority in such a situation, the one from the local connection or the one from the VPN tunnel?
If it turns out that the one from the VPN then can I somehow indicate in the VPN client to look for this host elsewhere?
The client is OpenVPN.
-
I got permission to disable this VPN temporarily, but this did not help. The ping is not coming back.
PS. sorry for the mistake in the title. Of course it should be that I can't :)
-
@dansci said in I can ping between two hosts from different VLANs:
@bmeeks Here my knowledge is limited. How can I check which gateway has priority in such a situation, the one from the local connection or the one from the VPN tunnel?
If it turns out that the one from the VPN then can I somehow indicate in the VPN client to look for this host elsewhere?
The client is OpenVPN.
Typically, on a client, there is only a single gateway configured and that one is considered the "default" one where all traffic not bound for the local subnet is sent. So for a host on a 10.x.x.6 network (assuming subnet is properly set), it hand off any traffic destined for a network outside of that subnet to the gateway.
Many users have posted here on the Netgate forums with traffic routing problems caused by installing VPN clients according to instructions from the VPN provider. Invariably those instructions call for turning on a setting that pulls the default route from the VPN provider instead of using the route provided by say DHCP on the host (or firewall).
I don't currently have an active VPN client on a host I can check, so I am unable to describe for you where to check the gateway configuration.
The online docs for OpenVPN are available, but require quite a bit of networking skill to navigate and understand. Here is one example: https://openvpn.net/vpn-server-resources/site-to-site-routing-explained-in-detail/.
-
@dansci said in I can ping between two hosts from different VLANs:
I got permission to disable this VPN temporarily, but this did not help. The ping is not coming back.
PS. sorry for the mistake in the title. Of course it should be that I can't :)
Disabling the VPN does not necessarily mean the route was changed.
Is the VPN connection a dedicated site-to-site one, or is it being used as some sort of "privacy protection" thing for routine browsing and is terminating with some commercial VPN provider?
What kind of host is this 10.6 device? Is it a Windows box, a Linux box, or what? Can you check its gateway setting?
This topic thread from the OpenVPN forum may also help: https://forums.openvpn.net/viewtopic.php?t=27689.
As someone mentioned earlier in this thread, have you verified whether the 10.6 host has its own internal firewall running or not? Windows clients these days do in fact run a host firewall by default. Ditto for most Linux type hosts as well. The Windows firewall can be particularly tricky because it will by default sometimes allow traffic from the local network but will block traffic from external networks (meaning not on the same subnet).
-
This post is deleted! -
@bmeeks 10.6 is Windows. And it was actually a Windows firewall, .... sorry, earlier I thought it acutely let such things go.
And just answering anyway, the VPN is supposed to allow connection to this computer from outside to its shared folder.
And the routing table on this Windows looks like the lowest metric is the gateway from pfSense - 10. Where the VPN is is 20.
Tabela tras IPv4 =========================================================================== Aktywne trasy: Miejsce docelowe w sieci Maska sieci Brama Interfejs Metryka 0.0.0.0 0.0.0.0 192.168.10.1 192.168.10.6 10 127.0.0.0 255.0.0.0 On-link 127.0.0.1 306 127.0.0.1 255.255.255.255 On-link 127.0.0.1 306 127.255.255.255 255.255.255.255 On-link 127.0.0.1 306 192.168.0.0 255.255.252.0 192.168.24.1 192.168.24.122 20 192.168.10.0 255.255.255.0 On-link 192.168.10.6 266 192.168.10.6 255.255.255.255 On-link 192.168.10.6 266 192.168.10.255 255.255.255.255 On-link 192.168.10.6 266 192.168.24.0 255.255.255.0 On-link 192.168.24.122 276 192.168.24.122 255.255.255.255 On-link 192.168.24.122 276 192.168.24.255 255.255.255.255 On-link 192.168.24.122 276 192.168.100.0 255.255.255.0 192.168.24.1 192.168.24.122 20 192.168.252.0 255.255.255.0 192.168.24.1 192.168.24.122 20 224.0.0.0 240.0.0.0 On-link 127.0.0.1 306 224.0.0.0 240.0.0.0 On-link 192.168.10.6 266 224.0.0.0 240.0.0.0 On-link 192.168.24.122 276 255.255.255.255 255.255.255.255 On-link 127.0.0.1 306 255.255.255.255 255.255.255.255 On-link 192.168.10.6 266 255.255.255.255 255.255.255.255 On-link 192.168.24.122 276 ===========================================================================Anyway, I tried to quickly add a rule to the Windows firewall, but it didn't work. I need to read up on how to do it to unblock 50.4.
-
@dansci said in I can ping between two hosts from different VLANs:
I need to read up on how to do it to unblock 50.4.
I personally don't run local windows firewall.. I have no hosts locally on my network that I would consider hostile.. And I don't run any services that I would block specific hosts on the same network from accessing, etc. My box is on its own segment, shit I don't actually trust is on different vlans, and pfsense prevents them from talking to my PC etc. So the local firewall wouldn't be worth managing.. And just causes problems ;)
Not saying you should do that - just saying it is an option if your having issues configuring it. At least for your own validation that is the problem..
Host firewalls do have valid use cases, but they also can just be pita if they wouldn't do any good anyway.. You have to evaluate for yourself if makes sense to run a host firewall or not for your environment.
-