pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue
-
The native (parent) NIC. We need to see the tagged traffic in the pcap and capturing on the VLAN removes that.
Using
tcpdump -e -i ix2 vlanwill show only VLAN tagged traffic which will make things easier to read. -
Hmm, so that clarifies what we saw before. The only incoming traffic is strangely double tagged.
But that does prove we can see incoming tagged traffic. Which implies nothing else is sending VLAN 20 tagged replies.
Do devices at .58 and .60 actually exist? Can you check for the incoming ARP requests there?
There has been some driver changes in ix including that specific fix for VLAN0 traffic but that was before 22.01 not between that and 22.05....
-
@stephenw10 said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
Hmm, so that clarifies what we saw before. The only incoming traffic is strangely double tagged.
But that does prove we can see incoming tagged traffic. Which implies nothing else is sending VLAN 20 tagged replies.
Do devices at .58 and .60 actually exist? Can you check for the incoming ARP requests there?
There has been some driver changes in ix including that specific fix for VLAN0 traffic but that was before 22.01 not between that and 22.05....
This is what I have on DHCP leases screen:
They exist but they are offline
Only IOT devices are on these VLANS, most of them are Wireless, the only one wired is 192.168.10.58 and connected to a specific port.
The last pfSense that worked(besides 22.01), to have timeline, was pfSense-CE-memstick-2.7.0-DEVELOPMENT-amd64-20220314-1916. After that all snapshots behaved like it is now.
-
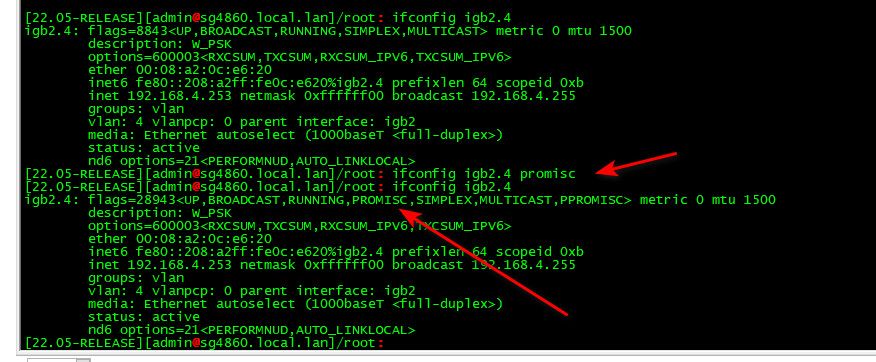
@stephenw10 Can we try something else...I don't try to be smart or anything, but how do I set those 2 VLANS to have PROMISC tag? I know it works for you. But maybe we can try
-
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
VLANS to have PROMISC tag?
just set it with ifconfig
here
-
@johnpoz
Yep figured it out from here https://www.freebsd.org/cgi/man.cgi?ifconfigAs you said, it does not work but I had to try. Don't get my wrong, thank you both for what you did until now. I'm just desperate. :)
I'm open to ideas, if you still have any.
Would it be useful to compare with a dump from 22.01, to see how vlans are handled there in my case? Should I revert back for now? Or should we try something else?
-
I would get a laptop on an access port on one of those VLANs so you can see what's happening at that end.
It's possible something got fixed and that has broken your setup because the double tagged traffic is now dropped as expected.
We don't see double tagged ARP replies from those devices though so it's unclear if they ever see the requests.What is handling the VLANs in between? How is it configured?
Steve
-
@nrgia if I had to "guess" something changed in the driver with that 0 tag.. that is a "guess".. @stephenw10 might have some other stuff to try/look at.
-
We know that something did change: https://github.com/pfsense/FreeBSD-src/commit/9c762cc125c0c2dae9fbf49cc526bb97c14b54a4
Hence my suggestion that it could be the VLAN0 tags were being incorrectly passed in 22.01 and before that 'fix'.
There shouldn't be any VLAN0 tagging happening here though.
-
@stephenw10
A Netgear switch....could it be that for some switches that VLAN 1 to be untagged, and for others VLAN0. Could it be that pfsense 22.01 had VLAN1 for untagged and now pfsense 22.05 have VLAN 0 for untagged ? Or I speak nonsense ? -
Anything is possible! You should never use VLAN1 (or 0 IMO) because some switches do weird things with that.
That double tagged traffic looks wrong and it's hard to see how pfSense could be causing it.Can we see the switch config? Does it have any QinQ or Priority tagging options?
I would have to guess that something in incorrectly applying priority tags to already VLAN tagged traffic.
-
@stephenw10 isn't there a whole other thread going on for quite some time about vlan 0? I have just stayed out of that one - no experience ever using a vlan 0.
But vlan 1 should pretty much never be tagged. That is just the default vlan ID uses use for their default untagged default network.
But yeah that double tag thing doesn't look right to me.
edit: Just me and my ocd I think - but why would you tag 192.168.10 with an ID of 20 and 192.168.20 with 30?, wouldn't 10 be better ;) just so you know hey 192.168.10 - that is vlan 10, I do that with my vlan 4 and 6, they are 192.168.4 and 192.168.6 networks ;)
-
@stephenw10
You can, sure, my native VLAN is untagged with vlan 1 on the switch. It worked before so I did not bother. -
@johnpoz said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
@stephenw10 isn't there a whole other thread going on for quite some time about vlan 0? I have just stayed out of that one - no experience ever using a vlan 0.
But vlan 1 should pretty much never be tagged. That is just the default vlan ID uses use for their default untagged default network.
But yeah that double tag thing doesn't look right to me.
edit: Just me and my ocd I think - but why would you tag 192.168.10 with an ID of 20, wouldn't 10 be better ;) just so you know hey 192.168.10 - that is vlan 10, I do that with my vlan 4 and 6, they are 192.168.4 and 192.168.6 networks ;)
Watched Tom Lawrence once, and he tagged them that way :) If it matters I can rename them, if you think it matters
VLAN 1 is not tagged in my case. It's only in the switch. All the ports on Group VLAN 1 are untagged.
-
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
if you think it matters
no doesn't matter - just odd, it is common practice to use an ID that somehow relates to the IP range is all.. But the vlan ID has zero to do with the IP space used on the vlan..
-
@johnpoz I will rename them, I know it's not logic to follow when debugging.
On your primary switch what do you have for native 1 or 0 ? -
Can we see the other VLAN config tabs? What is that switch? What firmware version?
But I would still get a laptop on to it and take some pcaps there to see what's happening.
Steve
-
@nrgia said in pfSense 22.05 breaks VLANS, restoring pfSense 22.01 fixes the issue:
primary switch what do you have for native 1 or 0 ?
My default is 9 ;) common practice to move away from 1 in the enterprise. Have never seen 0 to be honest.. Its more of a special use ID, have never ever seen 0 used on a switch as the default vlan. Every switch that I can remember has always been 1 as the default vlan.
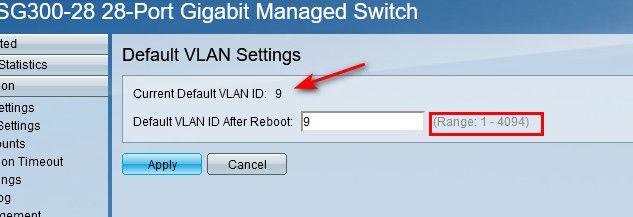
Notice - doesn't allow you to set 0, its 1-4094
-
@stephenw10
The Model is GS116Ev2 firmware version 2.6.0.48VLAN1
https://imgur.com/Js7iYjcVLAN20
https://imgur.com/keYmhMBVLAN30
https://imgur.com/gW0qBhc -
@nrgia why do you not have any untagged ports in your 10 or 20 vlans? Do you have no devices actually plugged into this switch on those vlans, and only other switches or AP?