Cant ping Lan <-> Opt 1 ?
-
Followed Tom Lawrences guide from scratch to setup a fresh pfSense.
Lan is 192.168.25/24
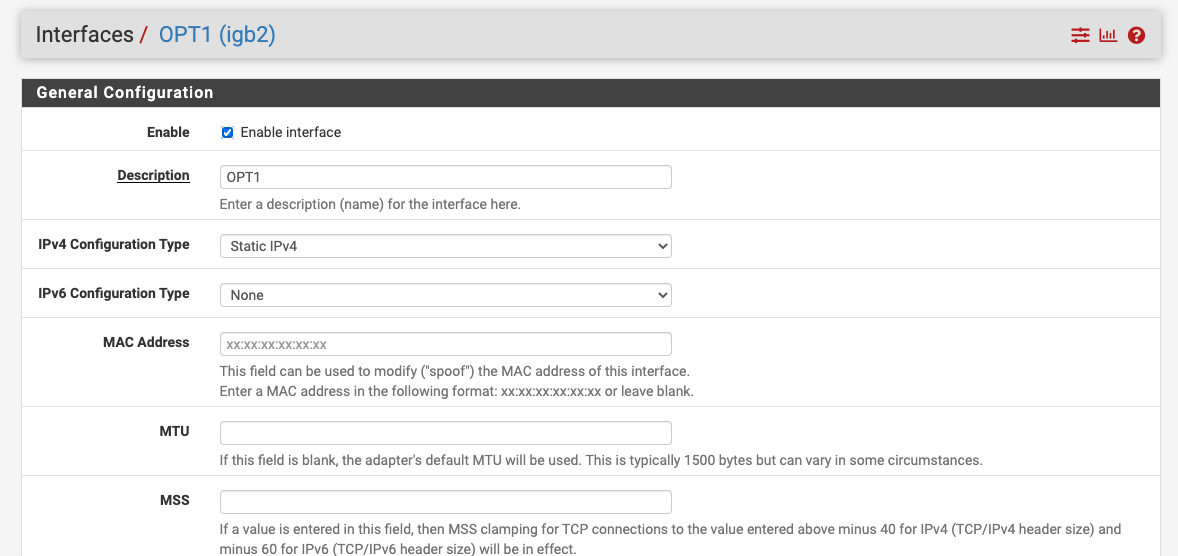
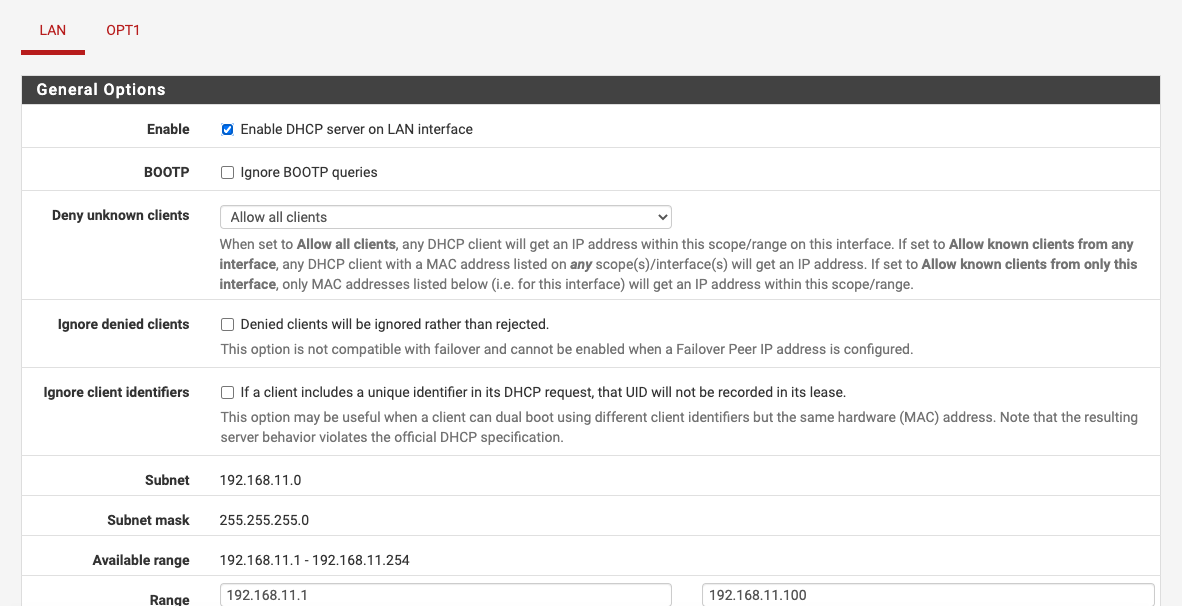
Opt1 is 192.168.50/24Interfaces are enabled, DHCP is set, and both have any protocol, any source, any destination.
I am able to connect to the internet but not able to ping Lan from Opt1.
Also not able to do reverse, ping Opt1 from Lan.
I get an error about routes and ICMP and the ping fails...
I have installed 3 times, double checked everything, rebooted swapped wires. I am at a loss.
Where am I going wrong here/why can I not ping ?
-
@srytryagn Post pictures.
-
@jarhead Of what, what would help?
-
@jarhead Is there something that needs to be done in windows/ubuntu/mac for a gateway to be able to ping across lans and Opt 1 ?
-
@srytryagn
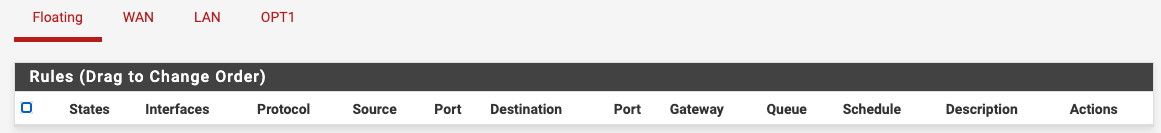
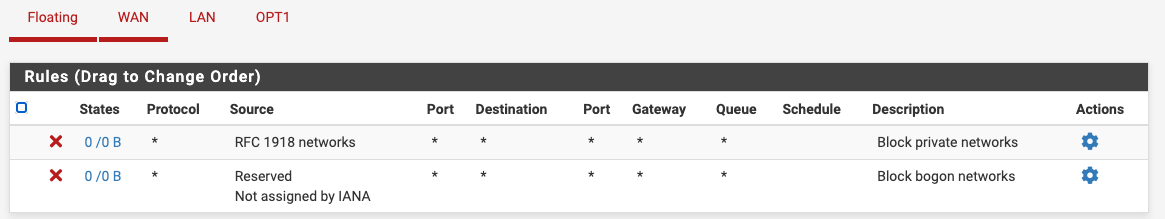
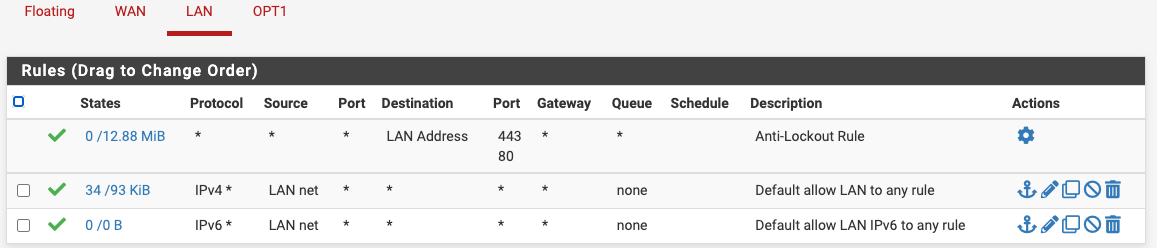
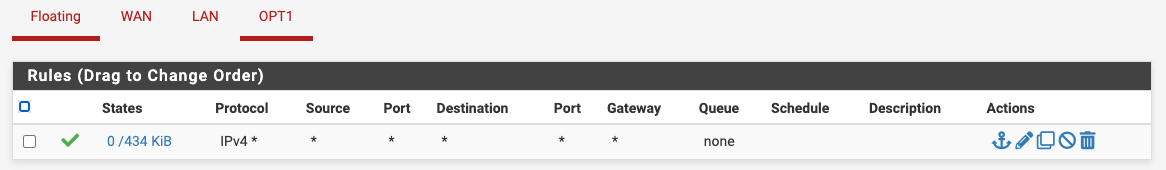
Pics of your firewall rules for both interfaces.
Saying you followed someone's guide doesn't mean it's correct and if you really have the rules right, there's no reason you couldn't access each subnet from the other. -
@srytryagn said in Cant ping Lan <-> Opt 1 ?:
I get an error about routes and ICMP and the ping fails..
What is this exact error?
Here is the thing out of the box the lan rules are any any.
You would be able to talk to any other network you brought up on pfsense.. No matter what the rules are on that other interface because the state created when your allowed there from lan would allow the reverse traffic.
Common mistakes users make.
They are policy routing out their lan - ie forcing traffic say out a gateway or wan interface. If your going to policy route, you need a rule above where you send traffic out a gateway that allows access to your other networks.
Rules on lan have been altered from the any and are not correct to allow what your wanting, floating rule was put in place for example. User enabled block rfc1918 on lan interface for example. Or any any rule set to say tcp only so no ping wouldn't work.
Device in other network is not using pfsense as their gateway.
Device in other network is running a host based firewall that prevents the access even though pfsense allowed it.
And one that has been coming up a few times recently - mask has been set on client and its wrong, where the other network trying to talk to or respond too to the device is local, and therefore never sends the traffic to pfsense to be routed.
Another common mistake, user running a vpn on the client, which is forcing traffic out the clients vpn connection, which no doesn't have access to your other networks.
I could go on and on with all the possible mistakes that are made ;) But here is the thing, out of the box lan would be able to talk to any other network you create on pfsense. There are no special routes to create, there are no special settings needed.. There are no rules even needed to be created on the other network interface.
But would love to see this route error your seeing.. Do you have any rules on floating? Could you post the rules you have on lan.
-
-
-
@johnpoz said in Cant ping Lan <-> Opt 1 ?:
@srytryagn said in Cant ping Lan <-> Opt 1 ?:
I get an error about routes and ICMP and the ping fails..
What is this exact error?
Here is the thing out of the box the lan rules are any any.
You would be able to talk to any other network you brought up on pfsense.. No matter what the rules are on that other interface because the state created when your allowed there from lan would allow the reverse traffic.
Common mistakes users make.
They are policy routing out their lan - ie forcing traffic say out a gateway or wan interface. If your going to policy route, you need a rule above where you send traffic out a gateway that allows access to your other networks.
Rules on lan have been altered from the any and are not correct to allow what your wanting, floating rule was put in place for example. User enabled block rfc1918 on lan interface for example. Or any any rule set to say tcp only so no ping wouldn't work.
Device in other network is not using pfsense as their gateway.
Device in other network is running a host based firewall that prevents the access even though pfsense allowed it.
And one that has been coming up a few times recently - mask has been set on client and its wrong, where the other network trying to talk to or respond too to the device is local, and therefore never sends the traffic to pfsense to be routed.
Another common mistake, user running a vpn on the client, which is forcing traffic out the clients vpn connection, which no doesn't have access to your other networks.
I could go on and on with all the possible mistakes that are made ;) But here is the thing, out of the box lan would be able to talk to any other network you create on pfsense. There are no special routes to create, there are no special settings needed.. There are no rules even needed to be created on the other network interface.
But would love to see this route error your seeing.. Do you have any rules on floating? Could you post the rules you have on lan...
Posted pics above, if there is anything else please let me know as I cant seem to find the source of the error. It has been driving me nuts in fact.
-They are policy routing out their lan - ie forcing traffic say out a gateway or wan interface. If your going to policy route, you need a rule above where you send traffic out a gateway that allows access to your other networks.
{How do I see if I am making this mistake ?}-Device in other network is not using pfsense as their gateway.
{How do you check this on Mac windows linux/Ubuntu?}-And one that has been coming up a few times recently - mask has been set on client and its wrong, where the other network trying to talk to or respond too to the device is local, and therefore never sends the traffic to pfsense to be routed.
{Now this I really dont get, how is this troubleshot ?} -
Ok on your lan devie ping 192.168.22.1
Can you do that
Your not policy routing, you have no gateway set on your lan.
You can verify view your routes on your box with netstat -r
If your client is getting IP from dhcp you should be fine because dhcp will not let you create overlapping networks. But you can view a clients mask with ipconfig /all on windows or linux/mac with ifconfig
-
@johnpoz said in Cant ping Lan <-> Opt 1 ?:
Ok on your lan devie ping 192.168.22.1
Can you do that
Your not policy routing, you have no gateway set on your lan.
You can verify view your routes on your box with netstat -r
If your client is getting IP from dhcp you should be fine because dhcp will not let you create overlapping networks. But you can view a clients mask with ipconfig /all on windows or linux/mac with ifconfig
Sounds like I am not following the steps correctly for initial setup; gateway setup or policy routing was not something I saw in tutorials or am familiar with.
In my setup I used the wizard, then:
- add interface for Lan + Opt1 and assign static IPv4
- Add firewall "any" rules
- DCHP server set ranges
Is there a step I am missing required to setup or configure gateways?
Or is it a setting on the client side that is amiss?
-
Just out of curiosity;
What are you pinging on the other interface ?
Could it be the pinged device has a firewall on itself which denies pings from unknown subnets ?
-
Mac tried (192.168.22.22) tried to ping Windows:
192.168.11.11
192.168.22.22Disabled all firewall settings temporarily for testing.
Ping fails.
-
@srytryagn can you please do as I ask this simple on
On your pc on your lan ping 192.168.22.1
-
ping 192.168.22.1 (from PC with IP 192.168.11.11)
PING 192.168.22.1 (192.168.22.1): 56 data bytes
64 bytes from 192.168.22.1: icmp_seq=0 ttl=64 time=0.243 ms
64 bytes from 192.168.22.1: icmp_seq=1 ttl=64 time=0.403 ms
64 bytes from 192.168.22.1: icmp_seq=2 ttl=64 time=0.435 msWorks.
But ping 192.168.22.22 (from PC with IP 192.168.11.11)
fails...
ping 192.168.22.22
PING 192.168.22.22 (192.168.22.22): 56 data bytes
Request timeout for icmp_seq 0
Request timeout for icmp_seq 1
Request timeout for icmp_seq 2
Request timeout for icmp_seq 3 -
@srytryagn said in Cant ping Lan <-> Opt 1 ?:
But ping 192.168.22.22 (from PC with IP 192.168.11.11)
And again - there are many reasons that could be, most likely host firewall on the 192.168.22.22 machine. Or wrong gateway or etc. etc..
To prove that to yourself, get a constant ping going from your lan device, this 192.168.11.11 to some IP on your opt network 192.168.22.22 for example
ping 192.168.22.22 -t on a windows machine
Now sniff via packet capture under the diagnostic menu on pfsense, on your opt interface.. You see the pings going out, but no response.
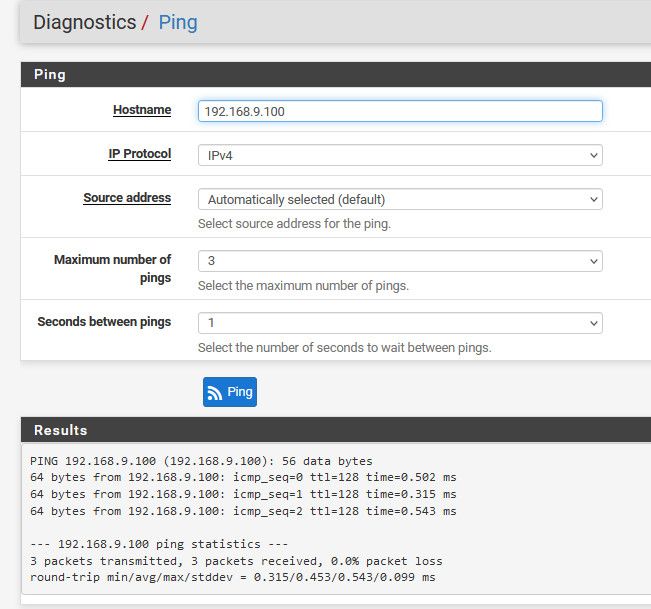
edit: here you go, example from box (192.168.2.12) in one of my vlans I can ping a box in my lan.
PING 192.168.9.100 (192.168.9.100) 56(84) bytes of data. 64 bytes from 192.168.9.100: icmp_seq=1 ttl=127 time=1.09 ms 64 bytes from 192.168.9.100: icmp_seq=2 ttl=127 time=0.795 msI then set firewall on that 192.168.9.100 box
ping 192.168.9.100 PING 192.168.9.100 (192.168.9.100) 56(84) bytes of data. ^C --- 192.168.9.100 ping statistics --- 8 packets transmitted, 0 received, 100% packet loss, time 7165msIf I sniff on the lan interface while pinging from the vlan device.. You can see pfsense sending on the traffic

The problem is not pfsense routing or allowing the traffic - its just that the device is not answering..
Even with the firewall on the host, pfsense can ping it - because pfsense is pining from an IP on that lan interface (192.168.9.253) Which the host firewall allows ping from its own local network, but not from a remote network (192.168.2.12) in my example.
-
Had to set gateways on client side, still did not work.
Then I rebooted.
And it works :( :)
-
@srytryagn said in Cant ping Lan <-> Opt 1 ?:
Had to set gateways on client side
And why would you have had to do that? Your dhcp would auto hand that out.. Nowhere in your posts did you say your client was not using dhcp..
How would the devices have gotten internet through pfsense if they were not using pfsense as their gateway? Was internet not working on these devices? You made no mention of that either.
You stated
I am able to connect to the internet
That is to be assumed your opt had internet as well, if it did not you should of mentioned that, etc.
-
@johnpoz said in Cant ping Lan <-> Opt 1 ?:
@srytryagn said in Cant ping Lan <-> Opt 1 ?:
Had to set gateways on client side
And why would you have had to do that? Your dhcp would auto hand that out.. Nowhere in your posts did you say your client was not using dhcp..
How would the devices have gotten internet through pfsense if they were not using pfsense as their gateway? Was internet not working on these devices? You made no mention of that either.
You stated
I am able to connect to the internet
That is to be assumed your opt had internet as well, if it did not you should of mentioned that, etc.
The internet was working.
DHCP was set to auto, pings were not working.After setting to manual on clients and explicitly making the ".1"s gateway and rebooting it worked all of a sudden.
This was a huge time suck, wish I had made a mistake I could learn something from.
-
@srytryagn said in Cant ping Lan <-> Opt 1 ?:
The internet was working.
Well that just not really possible, if your gateway wasn't working - how would clients have gotten internet?
The gateway is the same for internet as it is for other networks attached to pfsense, etc.
What makes more sense is your rebooting of the client fixed whatever your firewall setting was on the host, etc.
If the gateway was not set on your client - there is no way it could of gotten internet through pfsense.