Vlan not getting access to internet
-
Hello,
I currently configured PFSense setup as a DHCP server for multiple vlans. On my Cisco switch I have the 'inside' interface set to vlan 10 (management) and my devices vlan 5. For some reason, the only way I can get out is if my device is on the same vlan 10 network as the inside interface being used for PFSense.
I've tried putting the interface as a a trunk instead of vlan 10, which didn't work. Do i need to do any type of natting in order to get other vlans access to the internet?Currently i have a VM running proxmox connected to 1 nic on vlan 10 for management. a separate pcie card for wan/lan access for PFSense.
Thank you in advance.
-
@tyler-0 How many vlans?
What is an "inside interface"?
If you have these vlans configured on pfSense, you will need a trunk port with each vlan tagged on it to get them to your switch. -
@jarhead I have a PCIE Nic card installed on my server, one is a wan port one is another port connected to my Cisco switch. i am considering that the inside interface. it's irrelevant, i was just giving context.
That port on the switch is a trunk port, it is allowing all vlans, i have like 6.
I have PFSense configured on my management, vlan 10 network. The only way i can get to the internet is if my computer is plugged into a switch port tagged on teh management vlan. all my other vlans are unable to get to the internet. For example, my vlan 5 for wired personal devices, it is getting correct DHCP IP From PFSense, but it is unable to access the Internet. -
@tyler-0 Firewall rules?
Are you allowing the vlans internet access?
Post pics of the config's. -
@jarhead Here is some pics -
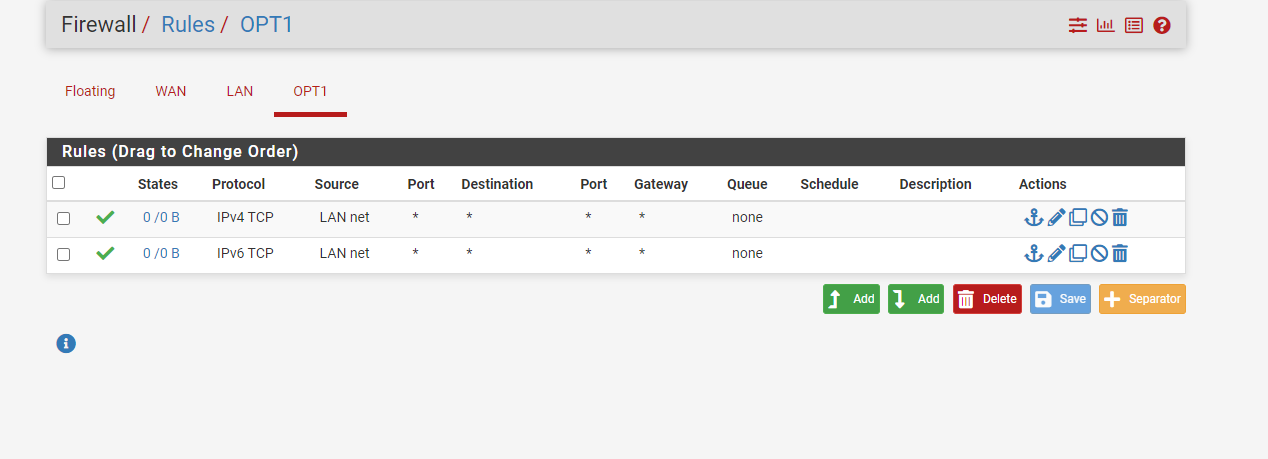
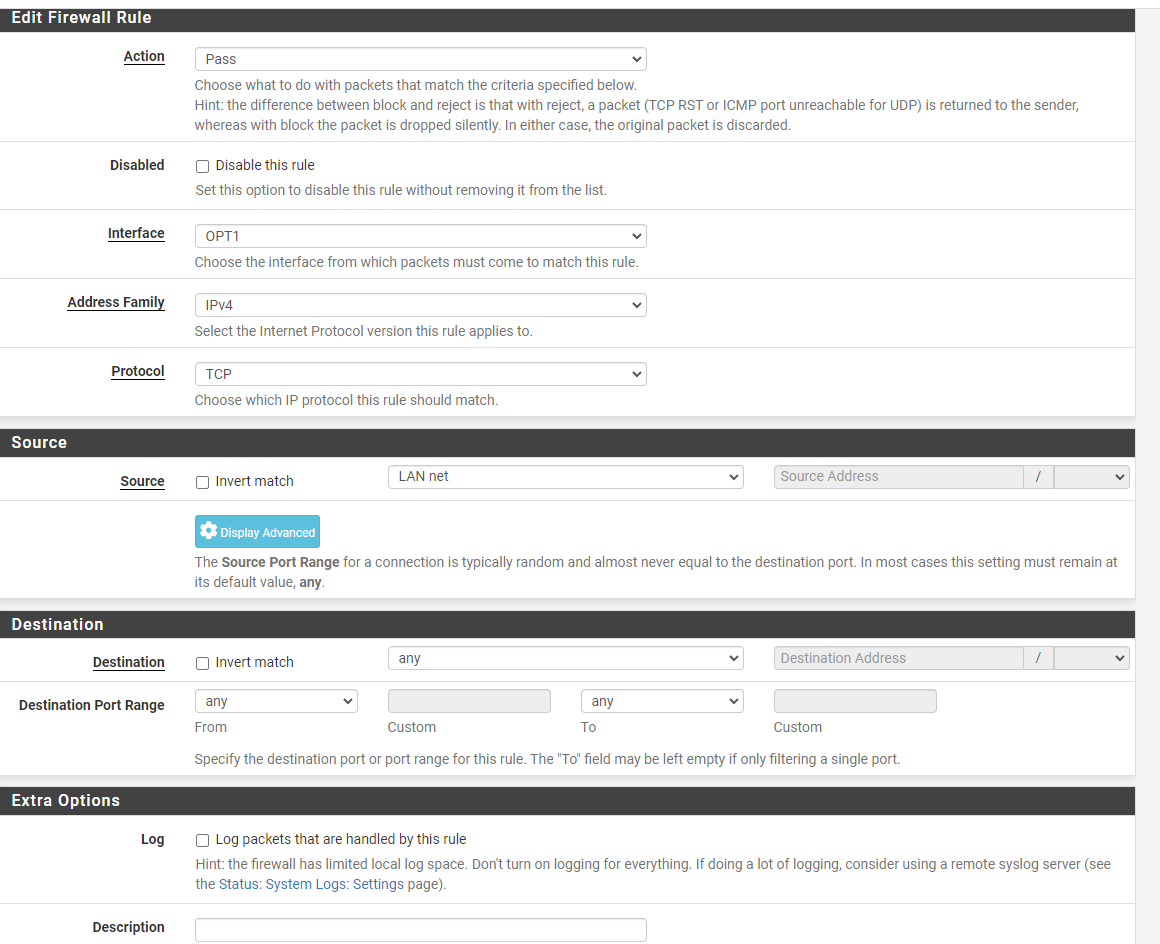
-
@tyler-0 What traffic isn't passing?
DNS? Pings?Those are UDP and ICMP respectively.
You are only passing TCP at this point -- so you can load http and https but you can't convert yahoo.com to 98.137.11.164
-
@tyler-0
Also "LAN net" as source on OPT interface doesn't make any sense. The incoming connections should only come from "OPT1 net" here. -
@viragomann Good catch. All they're allowing is TCP from the LAN net to hit OPT but not anything from OPT to go out.
-
@tyler-0
Besides the already mentioned ruleset (wrong interface)...
Correct me when I'm wrong (and I probably am), but when you configure all vlans on your switch and none on pfsense, how could pfsense do any routing?
So you set pfsense in your management vlan10, your devices behind your switch only reach internet when being in vlan10 as well...
Have you checked your switch's L3 config? Does it allow for other VLANs to reach pfsense in VLAN10 at all? -
@the-other I never assume the switch is L3, or that it's configured to route traffic if it is.
If we're talking about putting VLANs on a NIC in pfSense then it's most likely the switch either isn't L3 or isn't being used to route.
-
@rcoleman-netgate
Hmm, I was just assuming, because the screenshot only shows WAN, LAN and OPT1...
Thats why I mentioned that idea...
As stated: probably wrong
;) -
@the-other @rcoleman-netgate
Thank you both for the responses! I'm a noob when it comes to networking, more of a noob when it comes to firewalls and rules lol.So heres what i've changed and decided I want to accomplish. Ultimately, I would like to do L3 on the switch, but after reading more on different posts, it seemed easiest just to let PFSense do DHCP Instead of the switch.
Instead of Vlan 10 being the lan IP, I changed it to vlan 50.
Heres ideally what I want to accomplish. This is what I had setup previously with my Cisco ASA. But I ditched the ASA, sort of, it's still in my rack, but I wanted to try PFSense lol.
What I had setup before and what I would like to do, just unsure how to achieve it properly.
ASA Config -
Inside Interface Vlan 50 192.168.50.1
Outside DHCPSwitch Config -
Switch Port 24 connected to the ASA (inside) tagged with Vlan 50. Vlan 50 IP On the switch was 192.168.50.2. I then had a static route 0.0.0.0 0.0.0.0 192.168.50.1 to the inside interface of the ASA.
My Cisco Switch was set to Layer 3 on all Vlans. Management 10, Wired Devices, 5, IoT 6, Guest 7.
I've since moved to meraki access points and am letting Meraki do DHCP for the guest network, so really I only need 3 vlan. 10 (mgt) 5 (wired) 6 (IoT).I realized I had it all wrong when I set PFSense to be 192.168.10.10. I don't want PFsense to sit on the mgt Vlan, i feel like that's wrong..?
Let me know how I can best and easiest do this. If i need to scratch DHCP via L3 on the switch, I can set it up via PFSense. Would I then still need to put an IP on the vlan on the switch side if I choose for PFSense to do DHCP?
-
@tyler-0 said in Vlan not getting access to internet:
@the-other @rcoleman-netgate
Thank you both for the responses! I'm a noob when it comes to networking, more of a noob when it comes to firewalls and rules lol.So heres what i've changed and decided I want to accomplish. Ultimately, I would like to do L3 on the switch, but after reading more on different posts, it seemed easiest just to let PFSense do DHCP Instead of the switch.
Instead of Vlan 10 being the lan IP, I changed it to vlan 50.
Heres ideally what I want to accomplish. This is what I had setup previously with my Cisco ASA. But I ditched the ASA, sort of, it's still in my rack, but I wanted to try PFSense lol.
What I had setup before and what I would like to do, just unsure how to achieve it properly.
ASA Config -
Inside Interface Vlan 50 192.168.50.1
Outside DHCPSwitch Config -
Switch Port 24 connected to the ASA (inside) tagged with Vlan 50. Vlan 50 IP On the switch was 192.168.50.2. I then had a static route 0.0.0.0 0.0.0.0 192.168.50.1 to the inside interface of the ASA.
My Cisco Switch was set to Layer 3 on all Vlans. Management 10, Wired Devices, 5, IoT 6, Guest 7.
I've since moved to meraki access points and am letting Meraki do DHCP for the guest network, so really I only need 3 vlan. 10 (mgt) 5 (wired) 6 (IoT).I realized I had it all wrong when I set PFSense to be 192.168.10.10. I don't want PFsense to sit on the mgt Vlan, i feel like that's wrong..?
Let me know how I can best and easiest do this. If i need to scratch DHCP via L3 on the switch, I can set it up via PFSense. Would I then still need to put an IP on the vlan on the switch side if I choose for PFSense to do DHCP?
I believe we're good now actually.
I made PFSense Lan 192.168.50.1, my switch I created vlan 50 and gave it IP 50.2. I then fixed vlan 5 correctly to what was stated, I can now access the internet on the vlan 5 for wired devices. I've got ProxMox itself on vlan 10 for management. The only issue i'm having now is vlans seeing each other. For example my PC is sitting on vlan 5, but unable to ping the gateway 192.168.10.1 for vlan 10, therefore I cannot get to my proxmox server on that Vlan. It's going to take me a bit to tinker with the rules to figure it out. I also don't want my management vlan to have access to the Internet. I assume that's the point of the 'lan net' rule. I plan to create a DMZ Network for my VM's to sit on that need Internet access.