Pfsense and l3 switch and dmz
-
Hello everyone, I need some help with my home network design.
I have a netgate sg5100 as my main router and firewall, a cisco sg500 as my switch, and a Netgear R7800 as ap.
Here is my home network topology:- GUEST, CAM, IOT, DMZ vlans defined in pfsense;
- VM, VPN, CLRNET vlans defined in sg500;
Everything seems ok, except i can not access dmz from sg500 defined vlans, but i can access dmz from outside via wireguard vpn.
Thanks you in advance!
Here is my home network topology
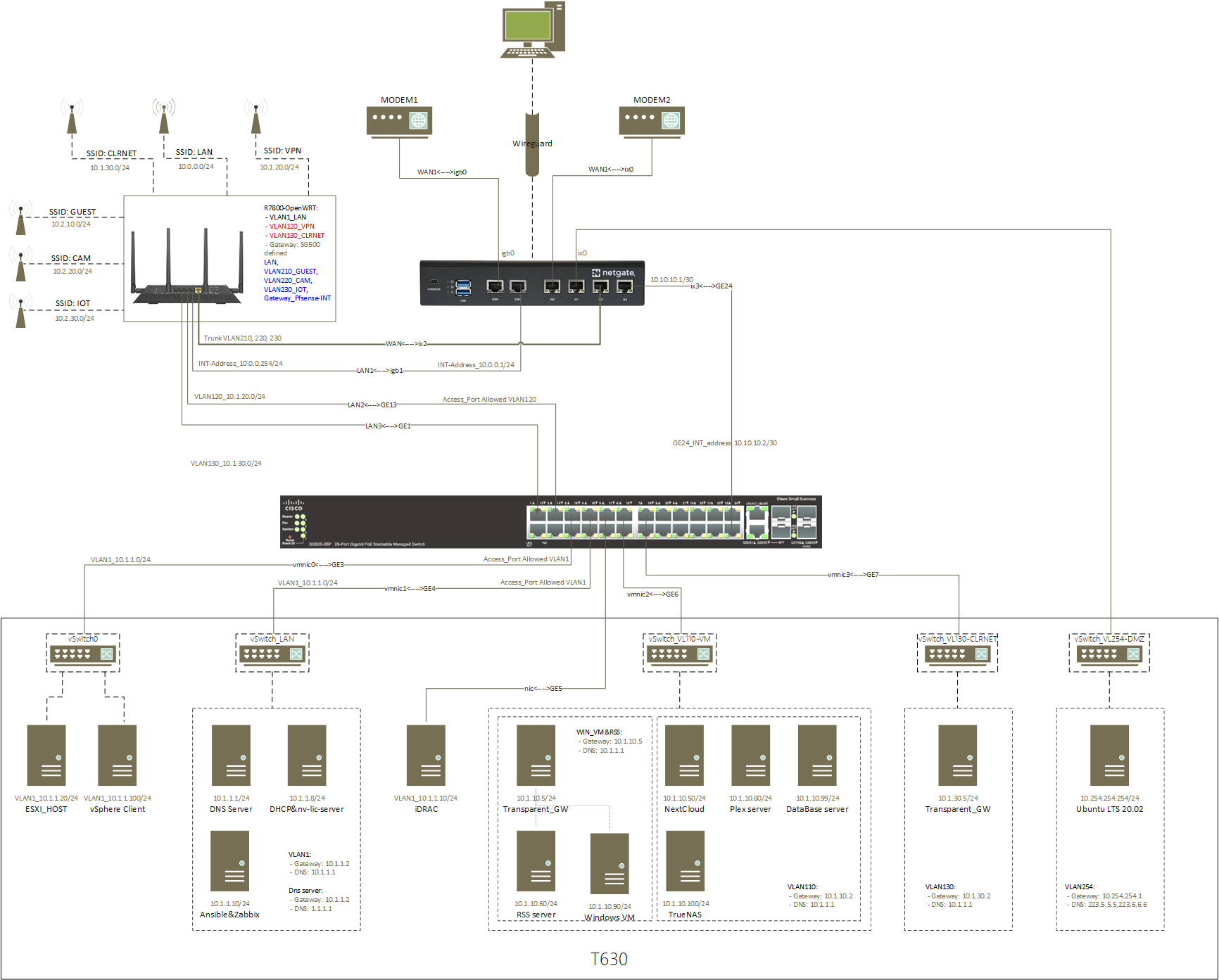
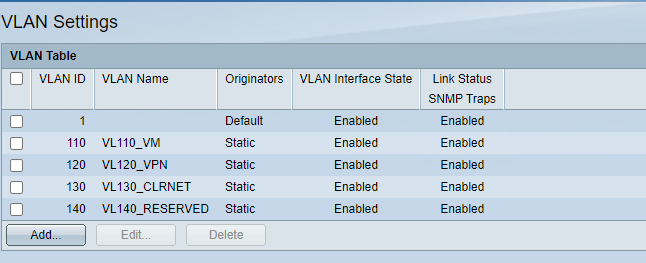
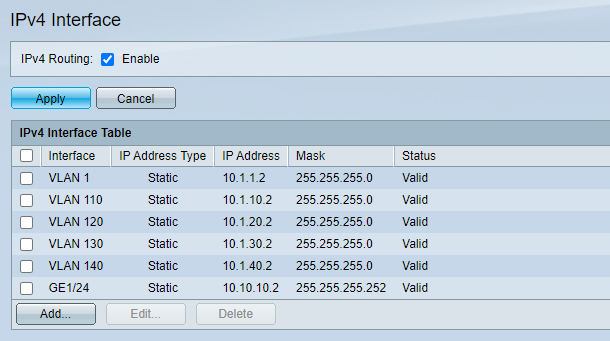
SG500 settings
R7800 settings
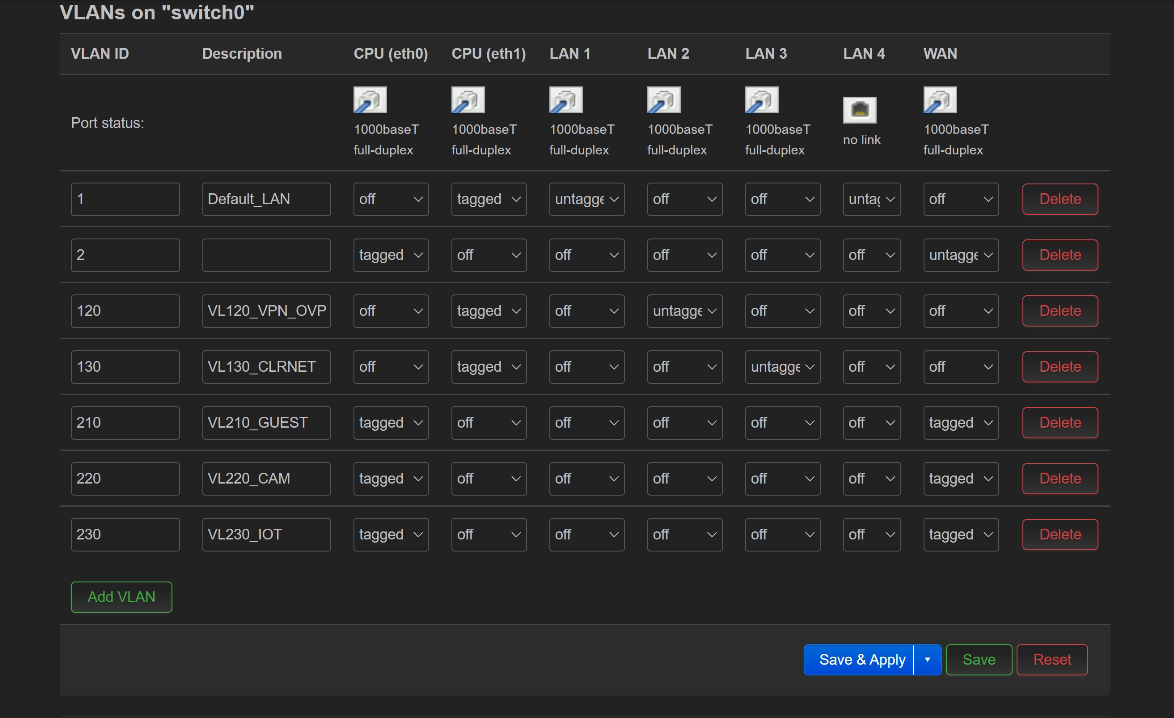
-
@chinchun Here is my pfsense settings
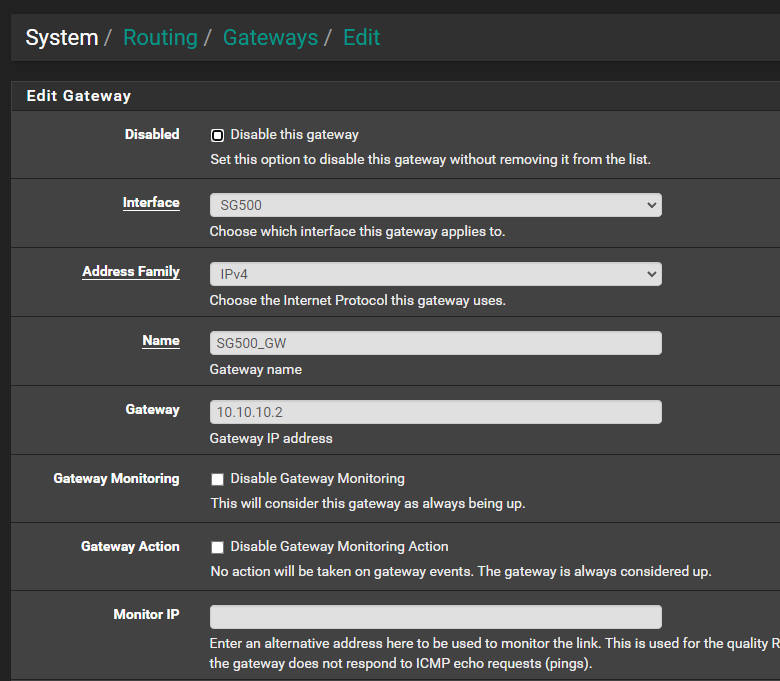
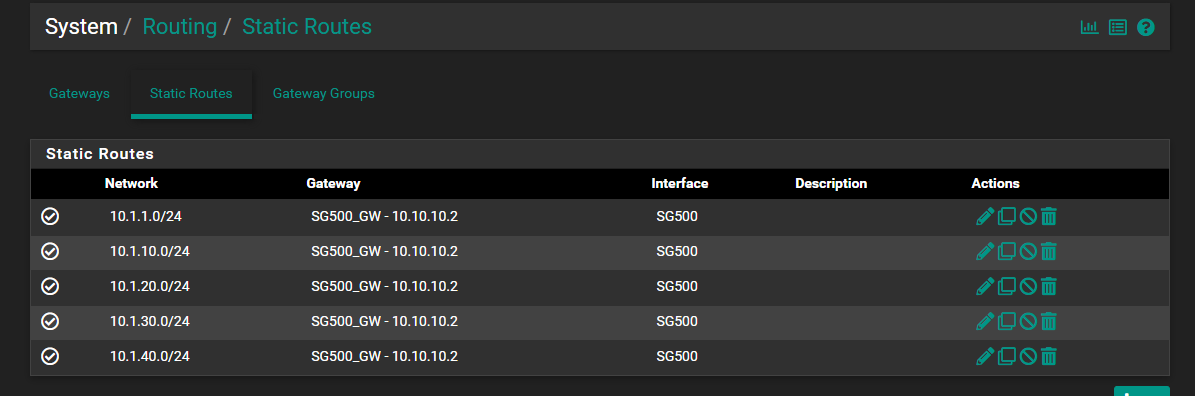
-
@chinchun I can ping the gateway of dmz(10.254.254.1, defined in pfsene) from my SG500 defined vlans, howerver i can not ping the host(10.254.254.254)
-
Is the host at 10.254.254.254 configured to allow access from outside it's own subnet?
Does it have a route back to the VLAN hosts to be able to reply?
If those hosts can ping 10.254.254.1 then pfSense is almost certainly sending the traffic towards 10.254.254.254 but it is refusing or is unable to reply.
Steve
-
@stephenw10 Thx for the apply.
- It does
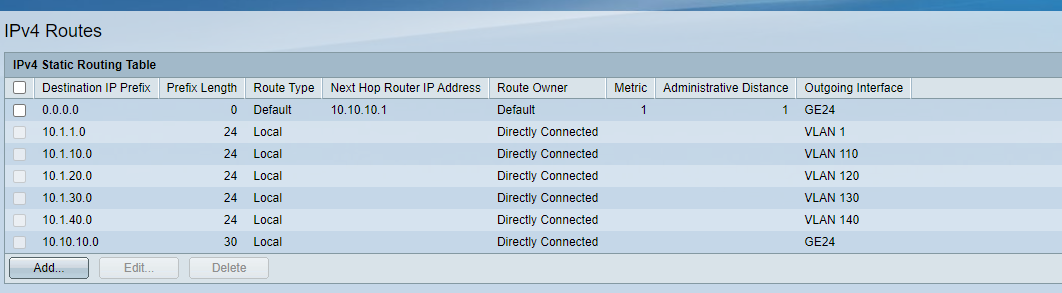
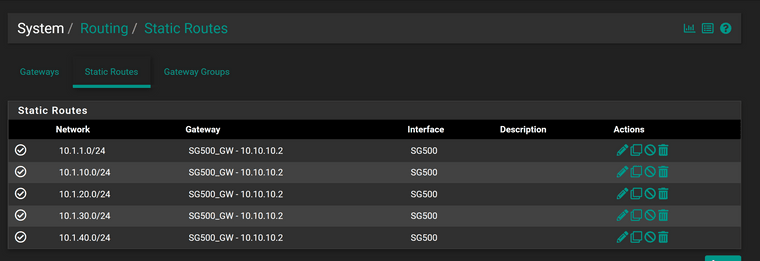
- I am not sure how can I do that, pfsense does not have a stastic route to switch defined vlans, I can not add it, because pfsense keep remaind me with the "This network conflicts with address configured on interface VL254_DMZ" error. And I does not define the vlan254_dmz in switch, but I think that traffic from switch defined vlans hosts(eg. 10.1.10.10) to 10.254.254.0/24 will go to pfsense via 10.10.10.2/30 anyway right?
- No, those hosts can not ping 10.254.254.1.
Let's keep it simple, basically now my problem is I can not access 10.254.254.254 or 10.254.254.1 from 10.1.10.10.
Here is my firewall rules for dmz
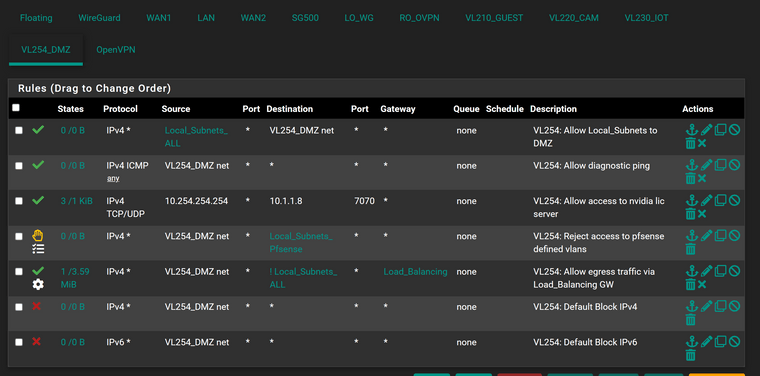
-
@stephenw10 And here is the aliases
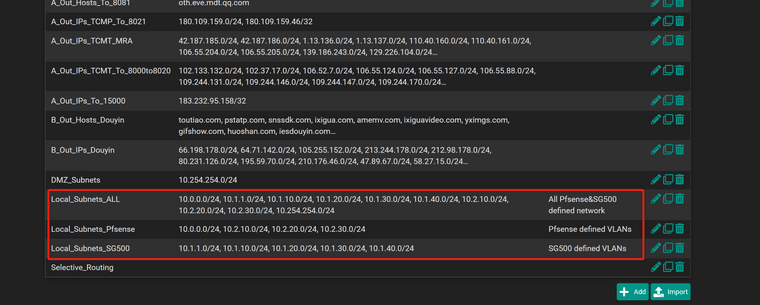
-
@stephenw10 And here is the updated topology
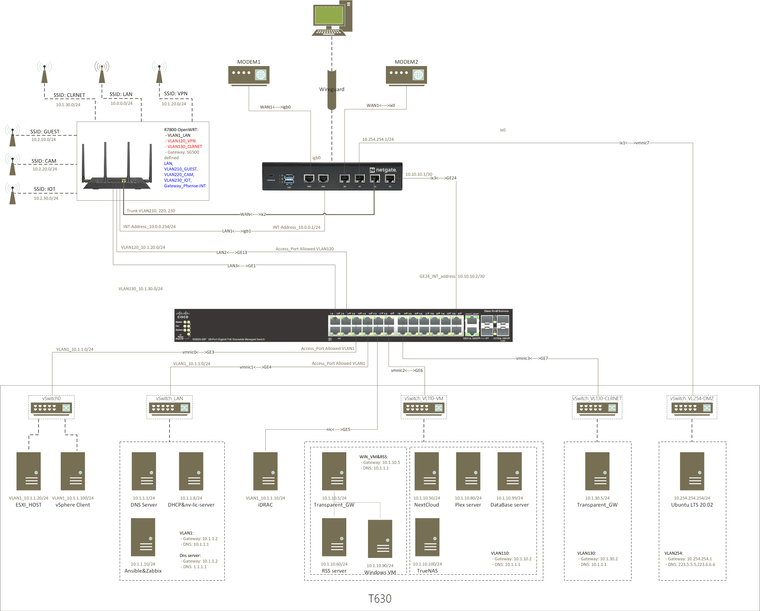
-
@chinchun said in Pfsense and l3 switch and dmz:
now my problem is I can not access 10.254.254.254 or 10.254.254.1 from 10.1.10.10.
Ok, that's different to earlier then when you said you could ping 10.254.254.1 but not 10.254.254.254. Is that correct?
The DMZ firewall rules make no difference to this traffic. Those connections are filtered by the VLAN 110 (VM?) rules. Can we see a screenshot of those?
Start a ping from 10.1.10.10 to 10.254.254.254 then check the state table in pfSense (Diag > States). Filter by 10.254.254.254. You should see two ICMP states. One incoming on VLAN110 and one outgoing on DMZ.
Steve
-
@chinchun late to the game here, but your drawing is a bit noisy.. A logical drawing would be much easier and faster to take in.
For example really don't care what devices are in vlans - that some ubuntu lts 20 is in vlan whatever, or what vlan your plex server is in, etc.
while this might be great for you.. In troubleshooting routing - all that is needed is logical diagram.
What specific network is your transit network? And is your R7800 routing? You have 2 gateways setup on it? one to the sg500 and another to pfsense?
Why are you complicating it with all the L3 stuff, why not just do layer 2 on your AP and SG500 and let pfsense handle all the routing?
-
@stephenw10
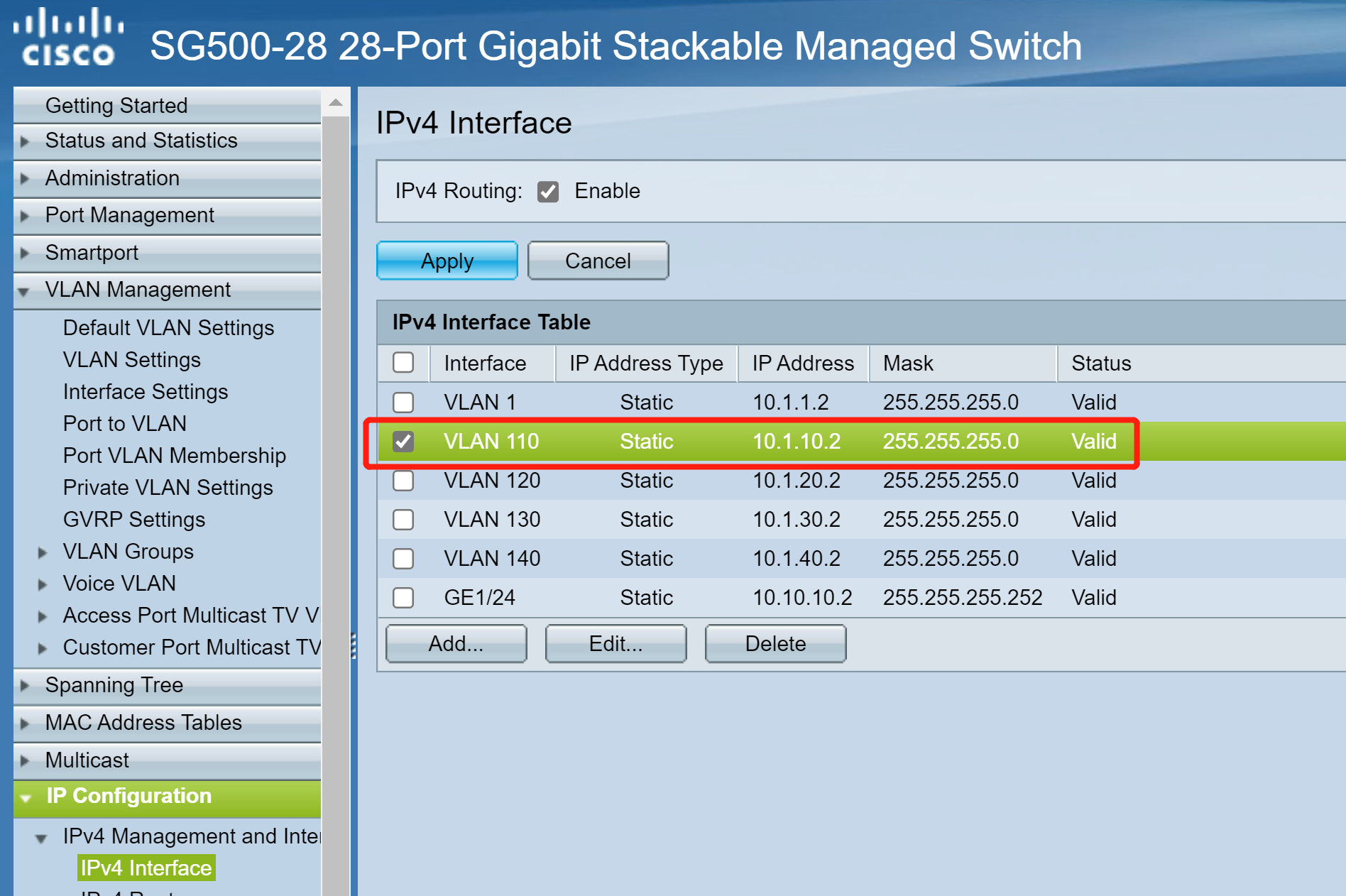
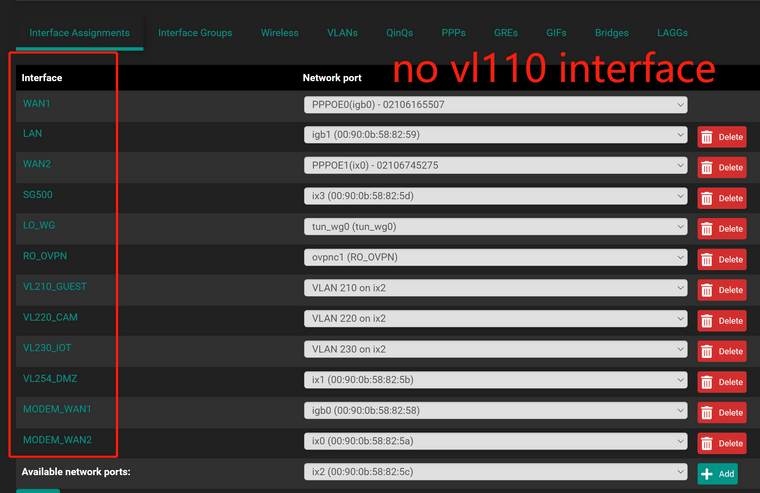
Let me make something clear first,- vlan 110 is defined in my switch sg500, vlan interface is 10.1.10.2, it does not have an interface in pfsense;
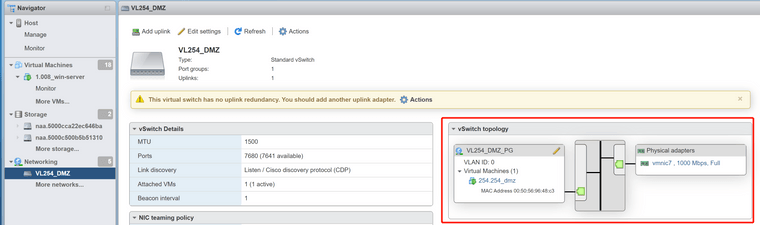
- dmz is directly connected to one of the sg5100 firewall (ix2); interface address is 10.254.254.1, 10.254.254.254 is an vm,
And for your questions:
- When I say I can ping 10.254.254.1, that is form outside of my home network using wireguard vpn connected to pfsense;
- 10.1.10.10 indeed is an vm; gateway is 10.1.10.2 (switch vlan110's interface address)
- I did what you said, but I can not see any states in pfsense, so I guess traffic form 10.1.10.10 does not reach pfsense?
Here is a simple topology, and my switch, ESXI, pfsense related settings, hope is helps.
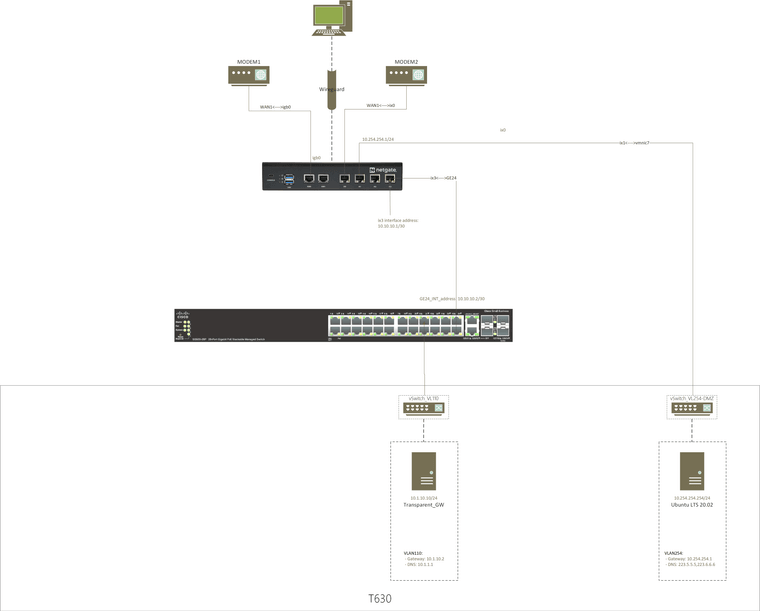
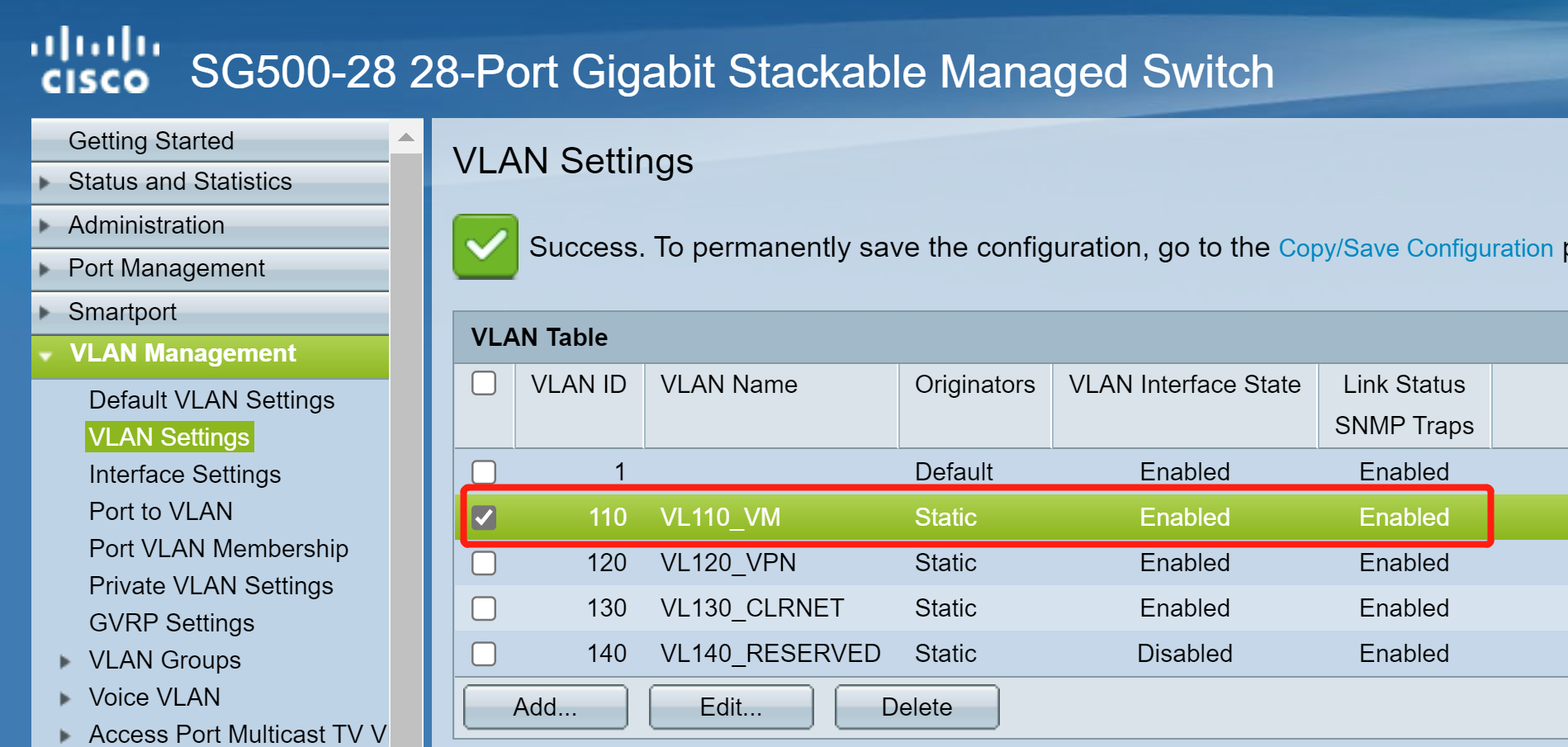
Because my mother language is not english, I am not sure if I understand you perfectly, and made myself clear, if there is any misunderstandings, please point it out to me. Many thanks!
-
@johnpoz
Sorry for the mess, and for your questions:- transit network is 10.10.10.0/30;
- R7800 does not do routing, just act as ap, and it only have one gateway which is pfsense's lan address
- I did try to let pfsense handle all the routing (which is working perfactly), but sg5100 only have gigabit ethernet ports, so I want the sg500 handle all the inter vlan routing instead;
Basicly I have two set of vlans, one is vlan 1xx, the other is vlan 2xx, vlan 1xx need linespeed inter vlan routing, so I defined them with my l3 switch, vlan 2xx don't need inter vlan routing, so I defined them in pfsense for better control.
-
@chinchun said in Pfsense and l3 switch and dmz:
10.1.10.10 indeed is an vm; gateway is 10.1.10.2 (switch vlan110's interface address)
I did what you said, but I can not see any states in pfsense, so I guess traffic form 10.1.10.10 does not reach pfsense?
What are the rules on 10.10.10.1 (ix3) interface in pfsense. If your going to want your downstream networks to go to other networks on attached to pfsense, or the internet - rules would have to be setup on this interface to allow that.
If you do not have a rule to allow the traffic from say 10.1.10.10 then no a state would never be created.
-
@johnpoz
Here it is
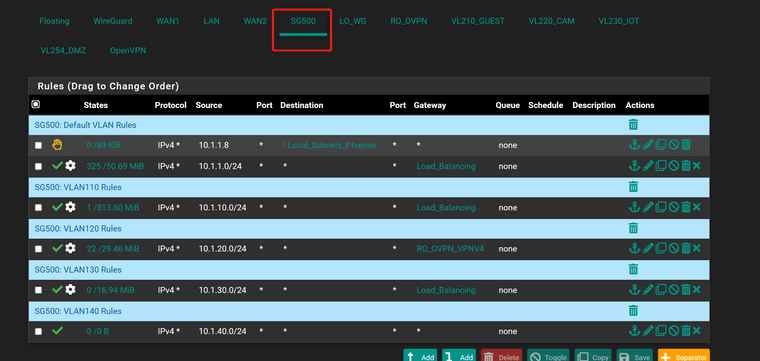
-
@johnpoz
Don't know if I did it the right way. -
@chinchun Your throwing the traffic from your downstream networks into a gateway, your LoadBalance.
Yeah that is policy routing, if you want these downstream networks to go to another network(s) off of pfsense you would have to allow for that in the rules.. I doubt your gateway your forcing the traffic to can get there ;)
https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
-
OK, you need a rule on SG500 to allow traffic from 10.1.10.1/24 to DMZ without a gateway set.
Otherwise that traffic is forced via the load-balance gateway group and cannot reach the DMZ.See: https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#bypassing-policy-routing
Steve
Edit: Snap!

-
@stephenw10 beat you too it Steve ;) hehehe -- jinx, you owe me a beer!
-
@johnpoz
Thanks for the apply!
I will read it first then try it out. Not an expert of pfsense, just an architect who love these things, still learning
-
@stephenw10
And many thanks to you too, bro!
Almost 3 am here, night! -
@chinchun here to help, you seem to have a pretty nice network setup..
And I wouldn't mind having a sg500, I have some sg300s
I don't do any routing on mine (other than lab for helping here if needed) mine are in L3 mode but only use L2 on them.
My sg300 is getting a bit long in the tooth, and is eol here next year I think.. I have my eye out for replacement.. Love to have something that has multiple gig interfaces 1/2.5/5/10 in the 24 port range.. And at a great price hehehe..
The cisco smb line with 24ports some with poe, and with multigig would be sweet! But this unicorn switch is not on the market that I can find - at least not at the price willing to pay..